The firewall appears to be blocking outgoing text messages from my phone ...
-
Yes, you configure the mirror port so that it copies the traffic from the AP to the computer running Wireshark. You can set up filters to narrow down the captures. for example, you could have something like ether host <MAC address> and port 53. This will capture all DNS packets to/from the phone's MAC address, whether IPv4 or IPv6.
You could probably do the same with the pfSense Packet Capture, but I find Wireshark is better to work with.
-
Wireshark is awful. The Samsung Note9 IPv6 ends in 75a0, here is a capture while a wifi call was received (successfully) by Note9.
No. Time Source Destination Protocol Length Info 10262 4.084411 2601:646:8c03:52a0:e0b9:xxxx:xxxx:75a0 2601:646:8c03:52a0:225:90ff:febb:bf0c DNS 104 Standard query 0x9e25 AAAA settings.crashlytics.com 10265 4.101972 2601:646:8c03:52a0:225:90ff:febb:bf0c 2601:646:8c03:52a0:e0b9:xxxx:xxxx:75a0 DNS 167 Standard query response 0x9e25 AAAA settings.crashlytics.com CNAME crashlytics.l.google.com AAAA 2607:f8b0:4005:809::2003 10267 4.105301 2601:646:8c03:52a0:e0b9:xxxx:xxxx:75a0 2601:646:8c03:52a0:225:90ff:febb:bf0c DNS 104 Standard query 0x8ebc A settings.crashlytics.com 10277 4.118522 2601:646:8c03:52a0:225:90ff:febb:bf0c 2601:646:8c03:52a0:e0b9:xxxx:xxxx:75a0 DNS 155 Standard query response 0x8ebc A settings.crashlytics.com CNAME crashlytics.l.google.com A 172.217.6.35 11872 4.618443 2601:646:8c03:52a0:e0b9:xxxx:xxxx:75a0 2601:646:8c03:52a0:225:90ff:febb:bf0c DNS 97 Standard query 0xc948 AAAA e.crashlytics.com 11943 4.636643 2601:646:8c03:52a0:225:90ff:febb:bf0c 2601:646:8c03:52a0:e0b9:xxxx:xxxx:75a0 DNS 273 Standard query response 0xc948 AAAA e.crashlytics.com CNAME events-endpoint-i-1172912053.us-east-1.elb.amazonaws.com SOA ns-1119.awsdns-11.org 11983 4.641550 2601:646:8c03:52a0:e0b9:xxxx:xxxx:75a0 2601:646:8c03:52a0:225:90ff:febb:bf0c DNS 97 Standard query 0x526e A e.crashlytics.com 12011 4.658921 2601:646:8c03:52a0:225:90ff:febb:bf0c 2601:646:8c03:52a0:e0b9:xxxx:xxxx:75a0 DNS 292 Standard query response 0x526e A e.crashlytics.com CNAME events-endpoint-i-1172912053.us-east-1.elb.amazonaws.com A 54.227.236.206 A 54.235.102.234 A 54.235.130.173 A 54.235.139.111 A 54.235.145.134 A 54.235.153.229 A 54.225.77.36 A 54.225.80.137 12454 4.789122 2601:646:8c03:52a0:e0b9:xxxx:xxxx:75a0 2601:646:8c03:52a0:225:90ff:febb:bf0c DNS 104 Standard query 0xaf22 AAAA analytics.localytics.com 12457 4.806773 2601:646:8c03:52a0:225:90ff:febb:bf0c 2601:646:8c03:52a0:e0b9:xxxx:xxxx:75a0 DNS 225 Standard query response 0xaf22 AAAA analytics.localytics.com CNAME queuer-prod-elb.53.localytics.com SOA ns-1150.awsdns-15.org 12458 4.811377 2601:646:8c03:52a0:e0b9:xxxx:xxxx:75a0 2601:646:8c03:52a0:225:90ff:febb:bf0c DNS 104 Standard query 0x788e A analytics.localytics.com 12485 4.853485 2601:646:8c03:52a0:225:90ff:febb:bf0c 2601:646:8c03:52a0:e0b9:xxxx:xxxx:75a0 DNS 265 Standard query response 0x788e A analytics.localytics.com CNAME queuer-prod-elb.53.localytics.com A 52.204.176.87 A 52.204.205.76 A 34.232.55.250 A 34.234.107.175 A 34.234.135.110 A 34.239.78.187 A 52.71.187.57 A 52.72.139.236 31900 18.065314 2601:646:8c03:52a0:e0b9:xxxx:xxxx:75a0 2601:646:8c03:52a0:225:90ff:febb:bf0c DNS 105 Standard query 0xe763 AAAA lh3.googleusercontent.com 31901 18.080418 2601:646:8c03:52a0:225:90ff:febb:bf0c 2601:646:8c03:52a0:e0b9:xxxx:xxxx:75a0 DNS 162 Standard query response 0xe763 AAAA lh3.googleusercontent.com CNAME googlehosted.l.googleusercontent.com AAAA 2607:f8b0:4005:807::2001 31903 18.083509 2601:646:8c03:52a0:e0b9:xxxx:xxxx:75a0 2601:646:8c03:52a0:225:90ff:febb:bf0c DNS 105 Standard query 0xf396 A lh3.googleusercontent.com 31905 18.083534 2601:646:8c03:52a0:225:90ff:febb:bf0c 2601:646:8c03:52a0:e0b9:xxxx:xxxx:75a0 DNS 171 Standard query response 0xf396 A lh3.googleusercontent.com CNAME googlehosted.l.googleusercontent.com A 172.217.6.65 -
Wireshark is a very useful tool. However, as it is fairly complex, there is a bit of a learning curve. However, that crashlytics serverr is actually Google.
I just see DNS query response pairs. Are there any failures there?
-
@JKnott said in The firewall appears to be blocking outgoing text messages from my phone ...:
I just see DNS query response pairs. Are there any failures there?
I guess not, will have to wait for it to fail and the spend an hour muddling through wireshark.
-
i just recently posted in 'wifi calling being blocked?' here's a copy paste of my response and how i got not only wifi calling, but all sms, mms as well. hope this helps
edit additional: i believe this would also affect the carrier's video calling feature as well, the baked into android phone app not like google duo or hangouts etc etc.:"ok yea this is almost a year later however:
had this issue - 2.4.5RC packages installed or not didn't matter, wifi calling and MMS would not work
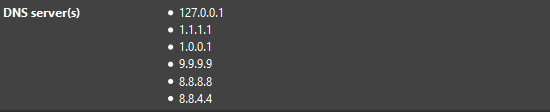
was using solely cloudflare dns. yes dnssec ssl/tls
added google and quad9 dnssec tls/ssl
(i dont think enabling the checkbox for dnssec or all of the other dnssec extras matter as i had the issue before setting it up as well)
success
for me, the problem is the mobile carrier proxy being an RFC 1918 address, pfsense allows this out from what i could tell, even with the rfc 1918 and bogon blocking enabled on the wan not lan (as expected), but i suspect cloudflare might also have these blocked in such a way - which could explain why the return trip would timeout (see next).
for the return trip, it did not return from their internal proxy but rather their external facing 'exit point' (i verified this by running traceroute from my phone while on cell service with hetools to my wan ip address)
added their hostnames to whitelist to be safe.
if i should post this new elsewhere or something, would someone kindly let me know? thanks"
-
@sparkyMcpenguin thanks for sharing. I also had Cloudflare as the sole DNS lookup, but have now added DNSwatch and Quad9. I don't think I'm set up for DNSsec, not sure where that is in pfSense. Will report back if the problem goes away. It is hit or miss so could take a few days.
-
@lifespeed what I did after changing settings was just reload unbound, pfblockerng, dnsbl, and snort. No need to restart or wait too long. Cron update as well is what I did. Hope it works!
Edit additional: I checked my phone APN settings, added their "mmsc" and "proxy" to the whitelist in dnsbl, host name and IP (excessive, but this was only added AFTER verifying it working adding additional DNS servers)
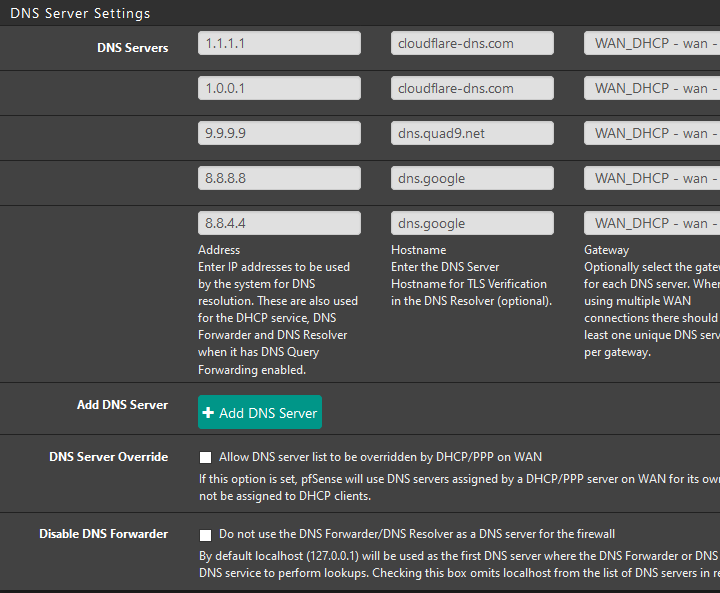
Also, I do not "allow upstream DNS" the forwarding setting. pfsense first, then cloudflare, quad9, Google
Edit: Last "also" I have a feeling the Google DNS is what really did it, at least for me, you know cause android, and I'm sure iPhone works too cause they mostly use Google DNS as well from what I remember
-
@lifespeed as for dnssec uh general setup under system and then the DNS resolver or forwarder had another checkbox I think. Check out dnsprivacy.org
-
@sparkyMcpenguin said in The firewall appears to be blocking outgoing text messages from my phone ...:
Edit: Last "also" I have a feeling the Google DNS is what really did it, at least for me, you know cause android, and I'm sure iPhone works too cause they mostly use Google DNS as well from what I remember
I had avoided the Gogle Empire, but I'll add it to the end of the list.
-
@lifespeed
i tried too, but that's why i went from just the 1, to 3 for lack of a better term "a RAID 50 DNS connection" raid 5 cause 3 dns make it 50 because dnssec.if someone takes over all three and screws up my pfsense, there's far bigger problems
 edit: maybe 60, cause technically i have 5, the two backups for cloudflare and google included. i only have the 'secure' quad9 i didn't want to use the 'insecure' secure one lol
edit: maybe 60, cause technically i have 5, the two backups for cloudflare and google included. i only have the 'secure' quad9 i didn't want to use the 'insecure' secure one lol -
@lifespeed
side note: using cloudflare dns (without adding TLS hostname) will use the DoH standard as per the explanation on their site. i believe google does as well. i dont remember about quad9, but from my understanding of the pfsense documentation, if you enter the TLS hostname, it will use both depending on whatever situation or browser being used. as for the 'insecure' secure quad9, that just means it doesn't have their complimentary 'we have ad blocker and ips/ids stuff too guys let us play..." hehedit let me make this easier:
widget:
general setup:
current base system:
the way i have this set up, and with my knowledge of networking (need to renew my Network+ or just.. not.. ripcomptia) i understand it to work this way with a clean slate and no dns cached entries:
if 127.x.x.x doesn't have record, query dns server list. because i don't 'allow override' ISP can't give me the DNS result cause it's technically blocked (or at least just dropped at the adapter level?) edit: or actually not even seen by them duh
oh this reminds me i have ASN set to one hour, not 24 hours...
sorry for the here and there edits i keep reminding myself of something
"Enable DNSSEC Support" checkbox in DNS resolver settings: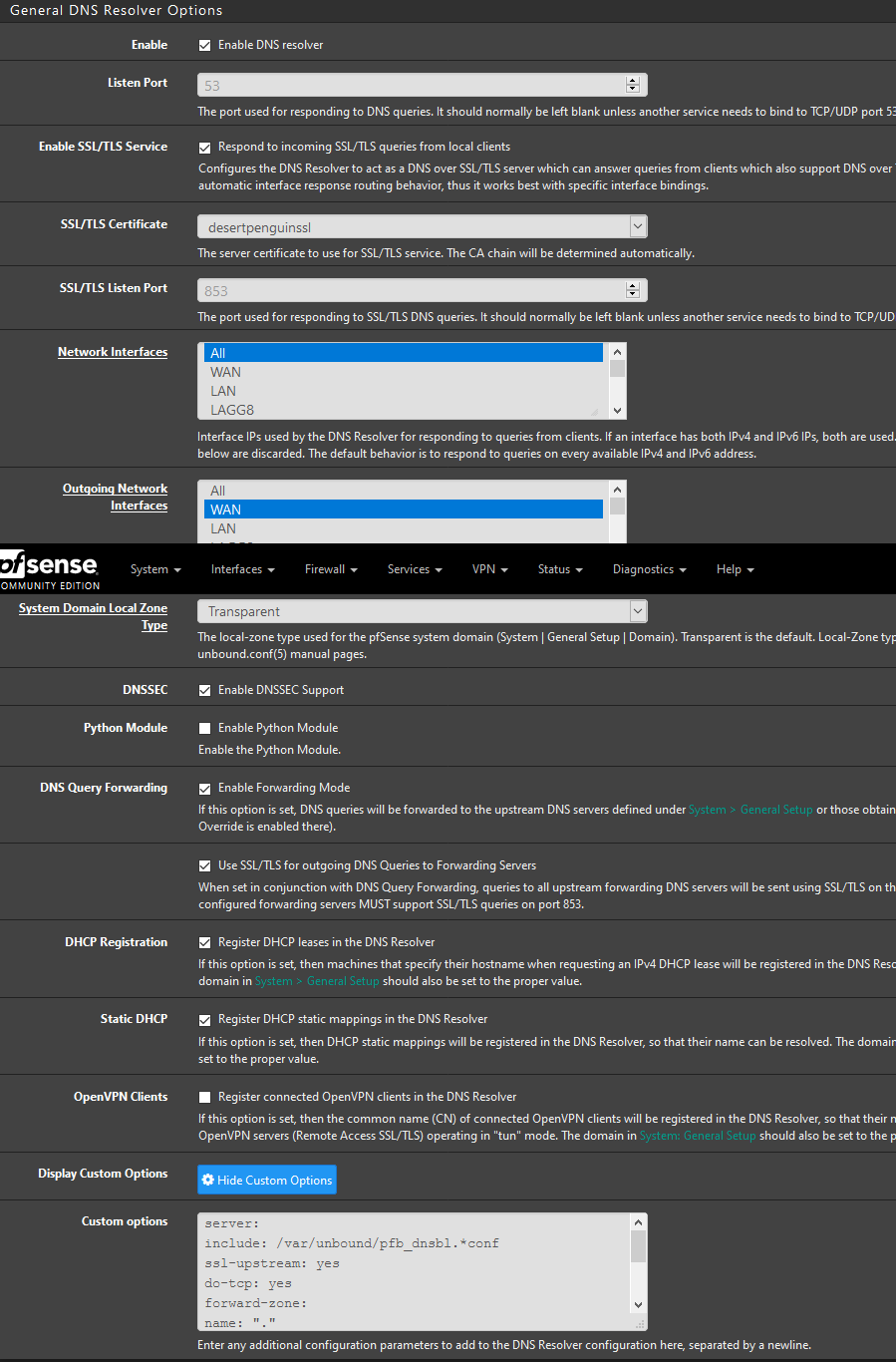
custom options (2 part cause of scroll bar):
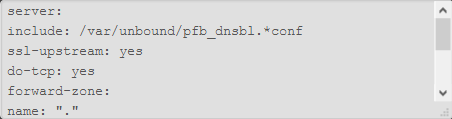
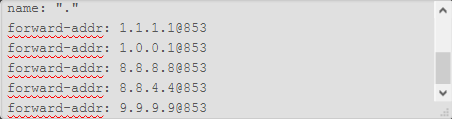
-
Adding DNSwatch, Quad9 and Google DNS servers did not fix the problem. I don't have hostnames entered for the DNS servers as you have shown. Also it looks like you just updated pfSense to 2.4.5? I think I'm on the previous rev of pfSense, 2.4.4. Also I don't have DNSsec set up, is a self-signed certificate adequate? Will try again tonight.
-
@lifespeed said in The firewall appears to be blocking outgoing text messages from my phone ...:
Adding DNSwatch, Quad9 and Google DNS servers did not fix the problem. I don't have hostnames entered for the DNS servers as you have shown. Also it looks like you just updated pfSense to 2.4.5? I think I'm on the previous rev of pfSense, 2.4.4. Also I don't have DNSsec set up, is a self-signed certificate adequate? Will try again tonight.
self signed yes i think. i just wanted the 8 dollar domain and ddos and whois protection from namecheap lol
-
@sparkyMcpenguin said in The firewall appears to be blocking outgoing text messages from my phone ...:
@lifespeed said in The firewall appears to be blocking outgoing text messages from my phone ...:
Adding DNSwatch, Quad9 and Google DNS servers did not fix the problem. I don't have hostnames entered for the DNS servers as you have shown. Also it looks like you just updated pfSense to 2.4.5? I think I'm on the previous rev of pfSense, 2.4.4. Also I don't have DNSsec set up, is a self-signed certificate adequate? Will try again tonight.
self signed yes i think. i just wanted the 8 dollar domain and ddos and whois protection from namecheap lol
this 8 dollar domain also was just for name resolution (ya i could've acme but eh)
technically i didn't need it for these purposes, i was just preparing for later on when i added openvpn, so that name resolution could be supplemental on my DDNS (residential IP)
-
@lifespeed said in The firewall appears to be blocking outgoing text messages from my phone ...:
Adding DNSwatch, Quad9 and Google DNS servers did not fix the problem. I don't have hostnames entered for the DNS servers as you have shown. Also it looks like you just updated pfSense to 2.4.5? I think I'm on the previous rev of pfSense, 2.4.4. Also I don't have DNSsec set up, is a self-signed certificate adequate? Will try again tonight.
for dnssec all this stuff i watch Lawrence Tech Systems on youtube. wonderful guy. such an easy setup process, link:
"Setting up DNS Over TLS & DNSSEC With pfsense"
i followed this and had no issues. i went to dnsprivacy to obtain settings for other providers
-
@lifespeed said in The firewall appears to be blocking outgoing text messages from my phone ...:
Also it looks like you just updated pfSense to 2.4.5?
correct however all these dns settings i had entered into 2.4.4-3 before changing to RC branch
-
@sparkyMcpenguin said in The firewall appears to be blocking outgoing text messages from my phone ...:
@lifespeed
side note: using cloudflare dns (without adding TLS hostname) will use the DoH standard as per the explanation on their site. i believe google does as well. i dont remember about quad9, but from my understanding of the pfsense documentation, if you enter the TLS hostname, it will use both depending on whatever situation or browser being used. as for the 'insecure' secure quad9, that just means it doesn't have their complimentary 'we have ad blocker and ips/ids stuff too guys let us play..." hehSo it sounds like I left out a key step of entering the DNS server domain names? Or is TLS and DNSsec required as well? Just trying to figure out why I'm still not getting wifi calling and SMS on the Samsung phone.
-
@lifespeed said in The firewall appears to be blocking outgoing text messages from my phone ...:
@sparkyMcpenguin said in The firewall appears to be blocking outgoing text messages from my phone ...:
@lifespeed
side note: using cloudflare dns (without adding TLS hostname) will use the DoH standard as per the explanation on their site. i believe google does as well. i dont remember about quad9, but from my understanding of the pfsense documentation, if you enter the TLS hostname, it will use both depending on whatever situation or browser being used. as for the 'insecure' secure quad9, that just means it doesn't have their complimentary 'we have ad blocker and ips/ids stuff too guys let us play..." hehSo it sounds like I left out a key step of entering the DNS server domain names? Or is TLS and DNSsec required as well? Just trying to figure out why I'm still not getting wifi calling and SMS on the Samsung phone.
yes for DNSSEC those extra little 'server options' from what i understand in the video i linked, need to be set
"tls and dnssec required?" i 'think' so. entering in the info just in the server options and in general setup i believe without the dnssec support checkbox enabled, could explain broken dns routing.
it's possible you need to check your phone APN settings and add the host names of your carrier listed there into the DNSBL whitelist (i did this for my carrier - still after it working just added it for certainty - like in case a blocklist lists those addresses) i had a block list blocking google dns just last week (reported it to the list owner already). no issues since
-
@sparkyMcpenguin said in The firewall appears to be blocking outgoing text messages from my phone ...: possible you need to check your phone APN settings and add the host names of your carrier listed there into the DNSBL whitelist (i did this for my carrier - still after it working just added it for certainty - like in case a blocklist lists those addresses) i had a block list blocking google dns just last week (reported it to the list owner already). no issues since
Does pfSense enable any blocklists by default? I don't think I have enabled any. If it isn't obvious already, I am far from an expert on this router SW.
-
@lifespeed said in The firewall appears to be blocking outgoing text messages from my phone ...:
@sparkyMcpenguin said in The firewall appears to be blocking outgoing text messages from my phone ...: possible you need to check your phone APN settings and add the host names of your carrier listed there into the DNSBL whitelist (i did this for my carrier - still after it working just added it for certainty - like in case a blocklist lists those addresses) i had a block list blocking google dns just last week (reported it to the list owner already). no issues since
Does pfSense enable any blocklists by default? I don't think I have enabled any. If it isn't obvious already, I am far from an expert on this router SW.
as far as i know, no. but usually a cell phone carrier's proxy on mobile is set to an Internally Routeable IP Address (RFC 1918).
when i first started i had those blocks enabled. didn't work. turned it off, still didn't work. turned it back on, changed dns settings cleared cache reboot for safe measure, forgot about it for a couple days checked again and it was working just fine.
what i did (this is for ATT) was add their 'mmsc.x.x.x' and 'proxy.x.x.x' listed (hostname not ip as RFC 1918 is a private ip address not public, so the DNS lookup for that IP would fail as per my testing) (forgot to finish this thought:) added it to DNSBL whitelist
to verify all this i installed hetools onto my phone, on and off wifi did traceroute tests to the att proxy and my public facing wan ip
this gave me 'extra ip addresses' that i then added to the IP whitelist as yet another redundacy backup.
wifi calling also (for me) works over the openvpn i have set up (on wifi not cell service - obviously) with the android phone originally in question
i also have 'switch to mobile network when wifi connectivity..." turned on and off for testing. worked either way for me (depending on wifi interference as well.. too many walls in the way or if im outside, and wifi calling is still intermittent, but will reconnect when it gets a stronger signal)