pfSense BLOCKS this kind of traffic, or just monitors it?
-
Hi,
recently I checked the Suricata Alerts and I saw this :
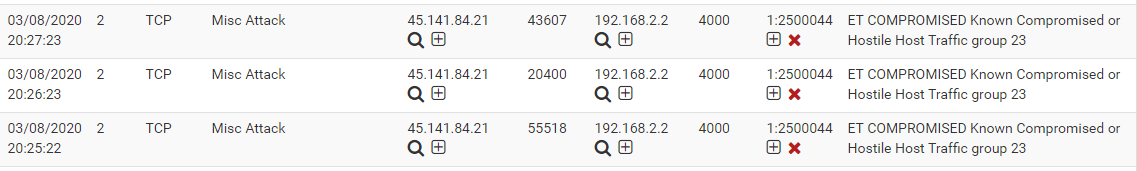
Does pfsense (and suricata) block this kind of traffic or just reporting it?
Thanks.
-
It depends on three things. First, is blocking enabled for Suricata on the configured interface? Second, is the enabled blocking mode set for Legacy Mode or Inline IPS Mode? Finally, if Inline IPS Mode blocking is enabled, are those rule actions being set to ALERT or to DROP or REJECT?
You would get better responses asking this question in the PACKAGES > IDS/IPS forum section of this message board. There are also 8 Sticky Posts with valuable info about the IDS/IPS packages available for pfSense posted here: https://forum.netgate.com/category/53/ids-ips.
When Legacy Mode blocking is enabled in either Suricata or Snort, then every single alert showing on the ALERTS tab will result in a block of the listed IP addresses unless that IP address is on a Pass List configured for the interface. The default Pass List will include all locally attached networks and then the WAN public IP. Block or no block decisions using Inline IPS Mode are controlled by the rule's action verb (typically either ALERT, DROP or REJECT).
-
@bmeeks The "block Offenders" setting was unchecked. So I changed it to "Legacy Mode" and also checked "Block On DROP Only".
But, the ET Compromise will not be blocked right?
-
First question I would ask is why do you have port 4000 forwarded to this 192.168.2.2 box? Are you playing diablo II?
Do you have Suricata in block mode? That is not pfsense - that is package addon... Out of the box pfsense would block all unsolicited inbound traffic... So the only way that traffic could be directed to 192.168.2.2 is if you opened it? Or 192.168.2.2 is your pfsense wan IP?
-
192.168.2.2 is a Windows Server inside my network. port 4000 is used for Remote Desktop. I now have Suricata in Legacy Block mode only for the WAN interface. (yes I know that Suricata is an add on)
-
@johnpoz said in pfSense BLOCKS this kind of traffic, or just monitors it?:
First question I would ask is why do you have port 4000 forwarded to this 192.168.2.2 box? Are you playing diablo II?
Do you have Suricata in block mode? That is not pfsense - that is package addon... Out of the box pfsense would block all unsolicited inbound traffic... So the only way that traffic could be directed to 192.168.2.2 is if you opened it? Or 192.168.2.2 is your pfsense wan IP?
If someone tries to enter credentials for Remote Desktop (trying to brake into the server) does pfsense block this IP? Does it figure that someone is trying to brake in? (via some pattern?)
-
@uxm re: Remote Desktop, presumably you meant to ask if Suricata will block the bad connection attempt (pfSense will block whatever ports aren't open). I believe there are rules for that yes, though I don't know which they are offhand. Just make sure they're enabled. I would also set an account lockout policy on the Windows computer...though note if they guess your username that could lock you out as well, for the time selected.
Also re: Suricata on WAN, it will inspect all packets hitting WAN, before blocked by the firewall. If you put in on LAN it will see many fewer packets, and also will get the IPs on the LAN that are generating (or targets of) the alerts. -
@uxm said in pfSense BLOCKS this kind of traffic, or just monitors it?:
192.168.2.2 is a Windows Server inside my network. port 4000 is used for Remote Desktop. I now have Suricata in Legacy Block mode only for the WAN interface. (yes I know that Suricata is an add on)
Use a VPN don't port forward RDP if you value your network.
https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2020-0609
-
@uxm said in pfSense BLOCKS this kind of traffic, or just monitors it?:
If someone tries to enter credentials for Remote Desktop (trying to brake into the server) does pfsense block this IP? Does it figure that someone is trying to brake in? (via some pattern?)
No - how and the F could it do that?? If your allowing RDP from the pubic internet your doing it wrong!! As mentioned VPN in..
Trying to change the port for security through obscurity is not security - as the saying goes!
-
@uxm said in pfSense BLOCKS this kind of traffic, or just monitors it?:
@bmeeks The "block Offenders" setting was unchecked. So I changed it to "Legacy Mode" and also checked "Block On DROP Only".
But, the ET Compromise will not be blocked right?
If you enabled the "Block on DROP Only" option and did not also use SID MGMT to set rules to DROP, then nothing will get blocked. It sounds like you are really new to using an IDS/IPS. I suggest you do some research on Google and learn how this technology works first.
Your questions about the IDS/IPS package and your other posts in this thread about security for RDP indicate you may be very new to network security. Your setup as you have currently described it is very much not as secure as it could and should be.
-
@bmeeks said in pfSense BLOCKS this kind of traffic, or just monitors it?:
@uxm said in pfSense BLOCKS this kind of traffic, or just monitors it?:
@bmeeks The "block Offenders" setting was unchecked. So I changed it to "Legacy Mode" and also checked "Block On DROP Only".
But, the ET Compromise will not be blocked right?
If you enabled the "Block on DROP Only" option and did not also use SID MGMT to set rules to DROP, then nothing will get blocked. It sounds like you are really new to using an IDS/IPS. I suggest you do some research on Google and learn how this technology works first.
Your questions about the IDS/IPS package and your other posts in this thread about security for RDP indicate you may be very new to network security. Your setup as you have currently described it is very much not as secure as it could and should be.
Yes, its a very new field for me. I try my best learning more (though I dont have so much time) Thanks @bmeeks
-
@uxm said in pfSense BLOCKS this kind of traffic, or just monitors it?:
@bmeeks said in pfSense BLOCKS this kind of traffic, or just monitors it?:
@uxm said in pfSense BLOCKS this kind of traffic, or just monitors it?:
@bmeeks The "block Offenders" setting was unchecked. So I changed it to "Legacy Mode" and also checked "Block On DROP Only".
But, the ET Compromise will not be blocked right?
If you enabled the "Block on DROP Only" option and did not also use SID MGMT to set rules to DROP, then nothing will get blocked. It sounds like you are really new to using an IDS/IPS. I suggest you do some research on Google and learn how this technology works first.
Your questions about the IDS/IPS package and your other posts in this thread about security for RDP indicate you may be very new to network security. Your setup as you have currently described it is very much not as secure as it could and should be.
Yes, its a very new field for me. I try my best learning more (though I dont have so much time) Thanks @bmeeks
Nothing wrong with being new to a field. All of us were also, at one time, new to this field. Spend some time searching for and browsing related links on Google to learn some more about the technolgoy.
The very first thing to learn about is what are VPNs (virtual private networks) and how they are used to enhance security for remote connectivity options such as Remote Desktop on Windows and other scenarios where you need remote access back into your LAN. You really, really need to be using a VPN for any kind of remote access from outside back into your local network (your LAN). Pretty much nothing else (such as obscure port forwards) is as secure as a VPN. pfSense gives you everything you need, out of the box, to configure a secure remote access setup.
Then read up on stateful inspection firewalls and how they operate. pfSense is a stateful inspection firewall. Then learn about the default-deny rule on the pfSense out-of-the-box WAN configuration and how that pretty much stops any unsolicited connectivity into your network. Only when you enable port forwards or otherwise monkey with that default deny rule do you open yourself up to external attack.
Only turn on the IDS/IPS package much later after you gain experience in this area. And even then, at first you should always run an IDS/IPS in detect-only mode for perhaps as long as a month to see what traffic patterns are "normal" for your network and to see which rules are being triggered. It is likely a number of triggered rules would actually be false positives and would need to be "tuned out" as you refined your IDS/IPS rule set. If you just install a tool such as Suricata or Snort and enable blocking immediately, you can expect to pretty much have all of your web browsing broken by false positive rules triggering.
-
@bmeeks said in pfSense BLOCKS this kind of traffic, or just monitors it?:
@uxm said in pfSense BLOCKS this kind of traffic, or just monitors it?:
@bmeeks said in pfSense BLOCKS this kind of traffic, or just monitors it?:
@uxm said in pfSense BLOCKS this kind of traffic, or just monitors it?:
@bmeeks The "block Offenders" setting was unchecked. So I changed it to "Legacy Mode" and also checked "Block On DROP Only".
But, the ET Compromise will not be blocked right?
If you enabled the "Block on DROP Only" option and did not also use SID MGMT to set rules to DROP, then nothing will get blocked. It sounds like you are really new to using an IDS/IPS. I suggest you do some research on Google and learn how this technology works first.
Your questions about the IDS/IPS package and your other posts in this thread about security for RDP indicate you may be very new to network security. Your setup as you have currently described it is very much not as secure as it could and should be.
Yes, its a very new field for me. I try my best learning more (though I dont have so much time) Thanks @bmeeks
Nothing wrong with being new to a field. All of us were also, at one time, new to this field. Spend some time searching for and browsing related links on Google to learn some more about the technolgoy.
The very first thing to learn about is what are VPNs (virtual private networks) and how they are used to enhance security for remote connectivity options such as Remote Desktop on Windows and other scenarios where you need remote access back into your LAN. You really, really need to be using a VPN for any kind of remote access from outside back into your local network (your LAN). Pretty much nothing else (such as obscure port forwards) is as secure as a VPN. pfSense gives you everything you need, out of the box, to configure a secure remote access setup.
Then read up on stateful inspection firewalls and how they operate. pfSense is a stateful inspection firewall. Then learn about the default-deny rule on the pfSense out-of-the-box WAN configuration and how that pretty much stops any unsolicited connectivity into your network. Only when you enable port forwards or otherwise monkey with that default deny rule do you open yourself up to external attack.
Only turn on the IDS/IPS package much later after you gain experience in this area. And even then, at first you should always run an IDS/IPS in detect-only mode for perhaps as long as a month to see what traffic patterns are "normal" for your network and to see which rules are being triggered. It is likely a number of triggered rules would actually be false positives and would need to be "tuned out" as you refined your IDS/IPS rule set. If you just install a tool such as Suricata or Snort and enable blocking immediately, you can expect to pretty much have all of your web browsing broken by false positve rules triggering.
I will follow your advices. Thank you so much. I really need to clear my viewing on that one.
Update : I have just setup my OpenVPN Server configuration and created my VPN user. Also exported the OpenVPN client for Android (my phone) and Windows (my work PC) and everything works super. Thanks! :)
PS : one problem though.. At work, I have two Internet Connections. The "production" connection (with ASA Firewall configured from the company that supports us) and one "off production, backup" internet connection. I use the "off production" connection. I connect but there are many disconnections/connections while I am connected... every 5-10 seconds..