Filter logs showing traffic that doesn't make sense
-
I'm starting to get very confused about my ruleset. It looks like traffic is not matching rules that it should, or is logging weirdly. And now I wonder if I'm just not understanding some fundamentals.
Looking in this example at a specific LAN host (172.16.0.195) talking out to an internet host (172.104.93.253) - a daily Nessus scan. FYI my WAN address is 150.101.221.210, and the 10.20.22.216 is apparently my gateway (I'm on FTTN so I assume this comes from the ISP CPE).
In the logs I have 10's of thousands of passed outbound packets, all matching rule 55 on pppoe0. I've checked WAN and LAN rulesets and there is no 55, but on the command line I can see it.
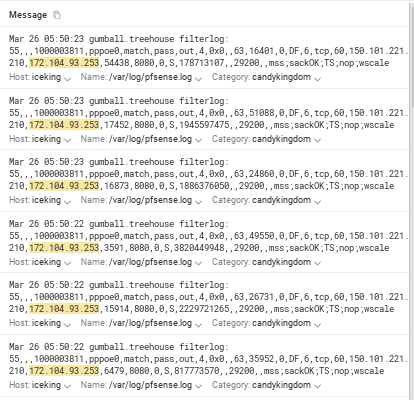
@55(1000003811) pass out log route-to (pppoe0 10.20.22.216) inet from 150.101.221.210 to ! 150.101.221.210 flags S/SA keep state allow-opts label "let out anything from firewall host itself"I've tried creating rules on both WAN and LAN to match and log (initially to not log was the intent but have turned on logging to see in any match), but these out logs are confusing.
If I look at IN logs, I do see the logs matching a rule on LAN. So that bit makes sense I guess, but these out logs confuse me a lot.
I wonder if it's because of the DF flag in this traffic? But if so, why? And why is the traffic logged with the WAN interface rather than only having the LAN address?
My ruleset looks like a mess now as I was trying all sorts of things out, but here are some screenshots.
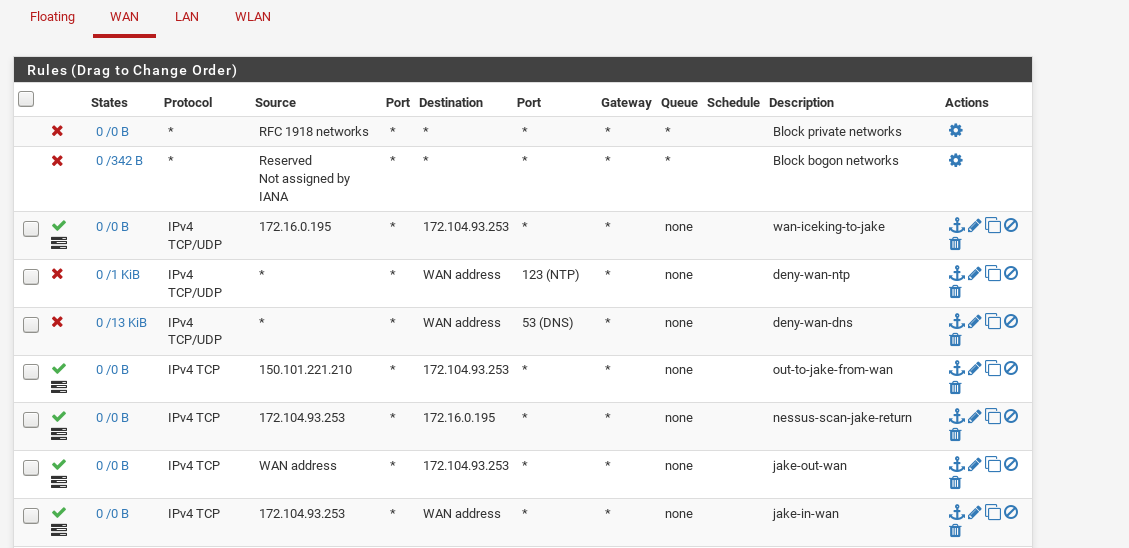
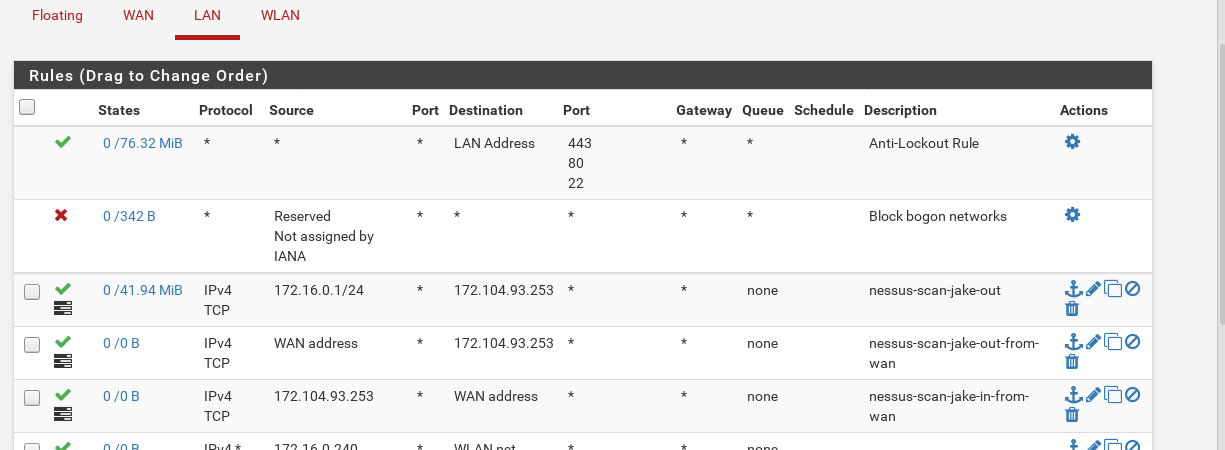
Would really appreciate some insight.
-
@55 is the id assigned to the rule
to get those rule numbers you need to run "pfctl -vvsr" from the shell or Diagnostics > Command.if you click the action icon on a log entry, it shows you the corresponding rule.
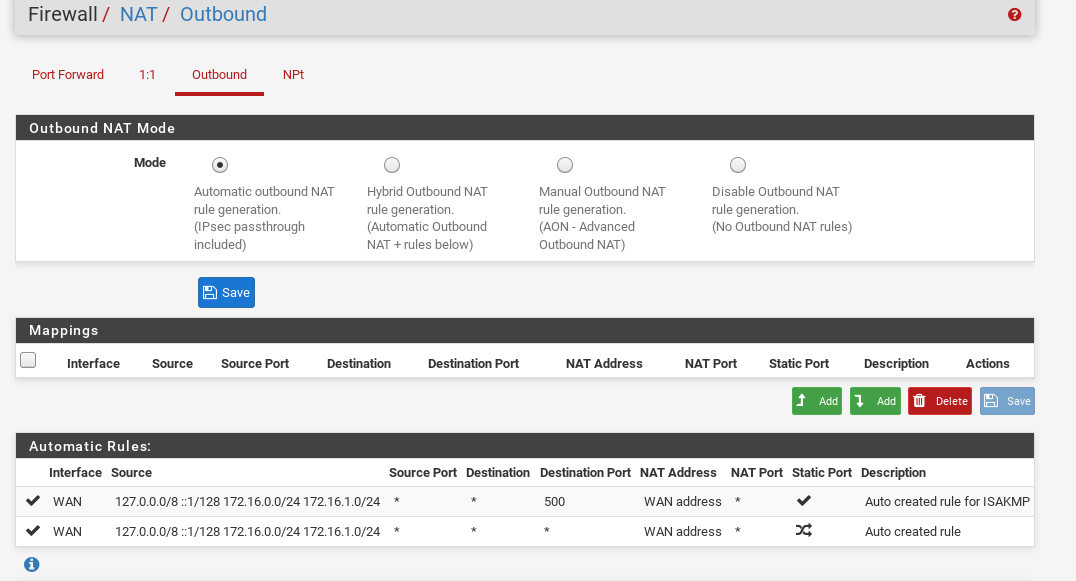
that said you have a rule with label "let out anything from firewall host itself" somewhere that match that traffic -
I'm pretty sure that rule 55 - "let out anything from firewall host itself" is a default rule, I see plenty of references to this rule on the forums and it looks like it's related to outbound NAT. Most likely the second of these:
Thinking about it again also, for the LAN rule that is matching, why does that get logged as IN, as isn't it OUT traffic? I understand it's IN from the LAN, but the traffic itself is heading to that internet host, so, that's confusing I suppose.
-
II worked it out. I had to add a Floating rule of Pass - src 'this firewall' - dst Internet Host IP - Quick - No Log.
That seems to make sense given NAT.
I understand things being matched as IN now also, all interface rules are IN.
Although I'm still a little confused as to how I can have that floating rule only match if the traffic originated from the one specific LAN port (or if that's even useful) - and it seems it's default to log on the default rule, which means you kinda get double logs if it already matches on interface specific rules.