Can I use one of my 6 physical network ports to be a vpn port?
-
Because your system is hosed ;)
https://docs.netgate.com/pfsense/en/latest/install/upgrade-troubleshooting.html
pkg-static clean -ay; pkg-static install -fy pkg pfSense-repo pfSense-upgrade -
perhaps you are right!
 this doesn't look good!
this doesn't look good!Shell Output - pkg-static clean -ay; pkg-static install -fy pkg pfSense-repo pfSense-upgrade
The following package files will be deleted:
/var/cache/pkg/sqlite3-3.22.0_1-3c0de3fc74.txz
/var/cache/pkg/iprange-1.0.3-65464f6717.txz
/var/cache/pkg/sqlite3-3.22.0_1.txz
/var/cache/pkg/pfSense-rc-2.4.3_1-abfbca5302.txz
/var/cache/pkg/pfSense-rc-2.4.3_1.txz
/var/cache/pkg/pfSense-kernel-pfSense-2.4.3_1-bde115e399.txz
/var/cache/pkg/pfSense-base-2.4.3_1-bd208e4cff.txz
/var/cache/pkg/pfSense-kernel-pfSense-2.4.3_1.txz
/var/cache/pkg/pfSense-default-config-2.4.3_1-01f7a2a04f.txz
/var/cache/pkg/pfSense-default-config-2.4.3_1.txz
/var/cache/pkg/pfSense-base-2.4.3_1.txz
/var/cache/pkg/libnghttp2-1.31.1.txz
/var/cache/pkg/pfSense-pkg-pfBlockerNG-devel-2.2.5_10.txz
/var/cache/pkg/perl5-5.24.4-89340f9371.txz
/var/cache/pkg/perl5-5.24.4.txz
/var/cache/pkg/libnghttp2-1.31.1-24a10b90b7.txz
/var/cache/pkg/pfSense-pkg-pfBlockerNG-2.1.4_8-d9071a3c1b.txz
/var/cache/pkg/lighttpd-1.4.48_1-26b547d114.txz
/var/cache/pkg/pfSense-pkg-pfBlockerNG-2.1.4_8.txz
/var/cache/pkg/lua52-5.2.4-34ceb7a41c.txz
/var/cache/pkg/lighttpd-1.4.48_1.txz
/var/cache/pkg/whois-5.2.17.txz
/var/cache/pkg/lua52-5.2.4.txz
/var/cache/pkg/whois-5.2.17-3e6f851a29.txz
/var/cache/pkg/GeoIP-1.6.11-3a55b74664.txz
/var/cache/pkg/pecl-intl-3.0.0_11.txz
/var/cache/pkg/GeoIP-1.6.11.txz
/var/cache/pkg/grepcidr-2.0-cec890eb71.txz
/var/cache/pkg/grepcidr-2.0.txz
/var/cache/pkg/aggregate-1.6_1-c1ea4bf1a7.txz
/var/cache/pkg/aggregate-1.6_1.txz
/var/cache/pkg/pecl-intl-3.0.0_11-7e63ad3a02.txz
/var/cache/pkg/icu-60.2_1,1-66aa5ec8d3.txz
/var/cache/pkg/iprange-1.0.3.txz
/var/cache/pkg/icu-60.2_1,1.txz
/var/cache/pkg/pfSense-pkg-pfBlockerNG-devel-2.2.5_10-5af9141812.txz
/var/cache/pkg/pfSense-repo-2.4.3_3-97fc8a3f69.txz
/var/cache/pkg/pfSense-repo-2.4.3_3.txz
/var/cache/pkg/pfSense-upgrade-0.52-239e1a78fc.txz
/var/cache/pkg/pfSense-upgrade-0.52.txz
/var/cache/pkg/pfSense-repo-2.4.3_4-c159ba5343.txz
/var/cache/pkg/pfSense-repo-2.4.3_4.txz
/var/cache/pkg/pfSense-upgrade-0.53-7baf5452be.txz
/var/cache/pkg/pfSense-upgrade-0.53.txz
The cleanup will free 78 MiB
Deleting files: .......... done
All done
Updating pfSense-core repository catalogue...
pfSense-core repository is up to date.
Updating pfSense repository catalogue...
pfSense repository is up to date.
All repositories are up to date.
The following 3 package(s) will be affected (of 0 checked):Installed packages to be UPGRADED:
pfSense-repo: 2.4.3_3 -> 2.4.3_4 [pfSense]
pfSense-upgrade: 0.52 -> 0.53 [pfSense]Installed packages to be REINSTALLED:
pkg-1.10.3_1 [pfSense]Number of packages to be upgraded: 2
Number of packages to be reinstalled: 13 MiB to be downloaded.
[1/3] Fetching pkg-1.10.3_1.txz: .......... done
[2/3] Fetching pfSense-repo-2.4.3_4.txz: . done
[3/3] Fetching pfSense-upgrade-0.53.txz: .. done
Checking integrity...Assertion failed: (strcmp(uid, p->uid) != 0), function pkg_conflicts_check_local_path, file pkg_jobs_conflicts.c, line 386.
Child process pid=52858 terminated abnormally: Abort trap -
I just pulled the trigger to 2.4.5.. And I really still have like hour of so more work to do... But I was pretty confident.. Had my media, and my backup (just in case)..
Took a bit longer than I thought - but I'm up on new 2.4.5... Have to check that all packages are working, etc.. But clearly the internet is working ;)
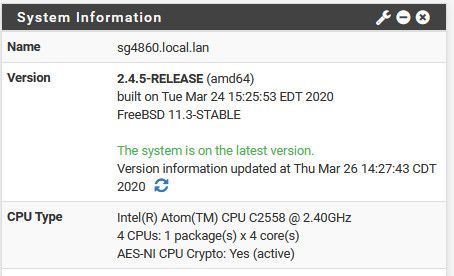
-
Glad it worked for you!

Mine is defo looking hozed!
Shell Output - pfSense-upgrade -d -c
Updating repositories metadata...
Updating pfSense-core repository catalogue...
pfSense-core repository is up to date.
Updating pfSense repository catalogue...
pfSense repository is up to date.
All repositories are up to date.
Upgrading pfSense-repo...
Updating pfSense-core repository catalogue...
pfSense-core repository is up to date.
Updating pfSense repository catalogue...
pfSense repository is up to date.
All repositories are up to date.
Checking integrity...Assertion failed: (strcmp(uid, p->uid) != 0), function pkg_conflicts_check_local_path, file pkg_jobs_conflicts.c, line 386.
Child process pid=10408 terminated abnormally: Abort trap -
Well do a clean install of 2.4.5 would be my suggestion... You can load in your backup config file..
-
-
So when you get back - just curious question.. Did you really think that 2.4.3_1 was current? That they hadn't updated in like 2 years.. And you were just ok with that?
-
@johnpoz said in Can I use one of my 6 physical network ports to be a vpn port?:
So when you get back - just curious question.. Did you really think that 2.4.3_1 was current? That they hadn't updated in like 2 years.. And you were just ok with that?
Hi, back!
Created a fresh VM but had a few issues with it not detecting my 4port nic (well it detected it but only used the 1st port) after alot of xml editing and tweaking it is working and now running on 2.4.5 :-)
To be honest with you, I rarely logged into the web admin of pfsense, only if I wanted to tweak or check something I would log in. I would always look to check for updates (I love an update!) and it would always say it was up to date in green so I just presumed it was updating itself and thought no more of it. It was only when you mentioned it I saw how old it was!
So, I am on 2.4.5 and still have this gateway down issue? the gateway must be up though as pia is active and running fine!
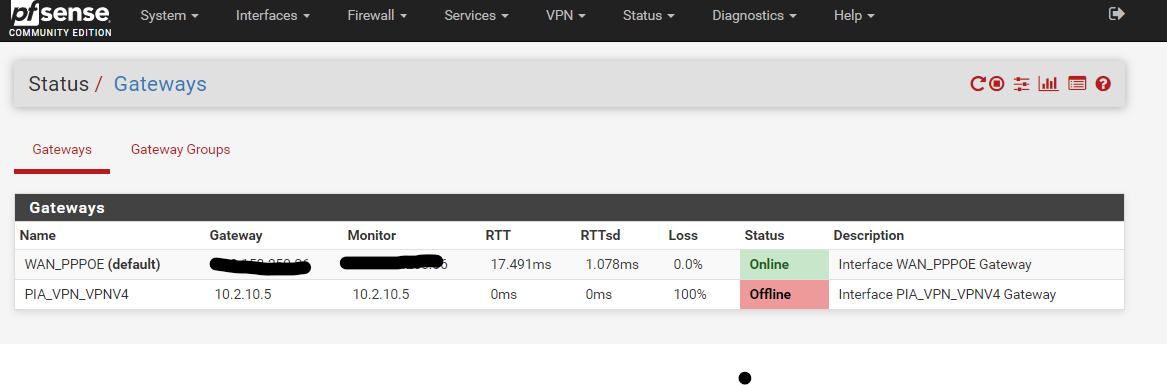
I also have dns leak and you made it quite clear that you did not approve of their method for resolving it not their killswitch method, would you mind pointing me in the way of the correct method? I have read about floating rules for a killswitch?
Many thanks :-)
-
How do you think you going to use normal wan and resolver not have a dns leak?
Did you hand your client on your vpn network a different dns? If you have him ask pfsense then yeah your going to show a "leak" But your resolving, your not forwarding.. So your not handing all your dns to anyway anyway..
that kill switch method they used was if you send ALL traffic to them! And if they down, then all traffic stops... That is not what your doing, your policy routing.. If you set gateway down rules don't
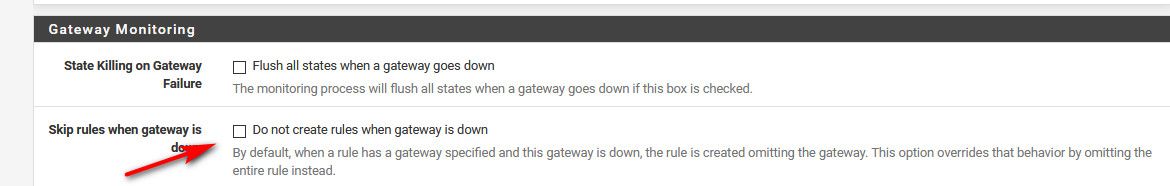
This is what normally would be your kill switch
But this is also what is prob preventing you from working... If your gateway is down, then you shouldn't have access.
Did you put any rules on your vpn interface you created?
Also when you say trouble recognizing your 4 port nic.. Your doing passthru of the nic to pfsense? Its easier to just let esxi do the nics, and give pfsense virtual nics. vmx3 or e1000
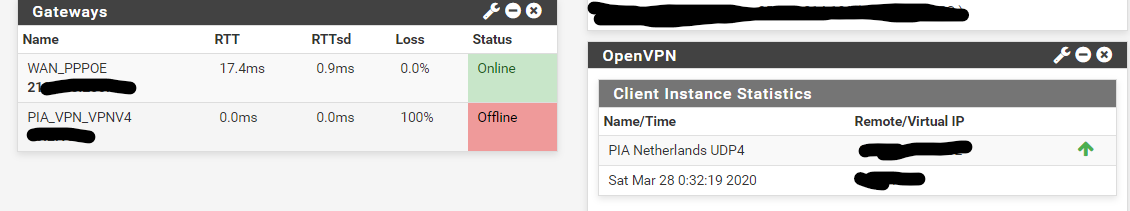
if you have no rules - then yeah you will show offline
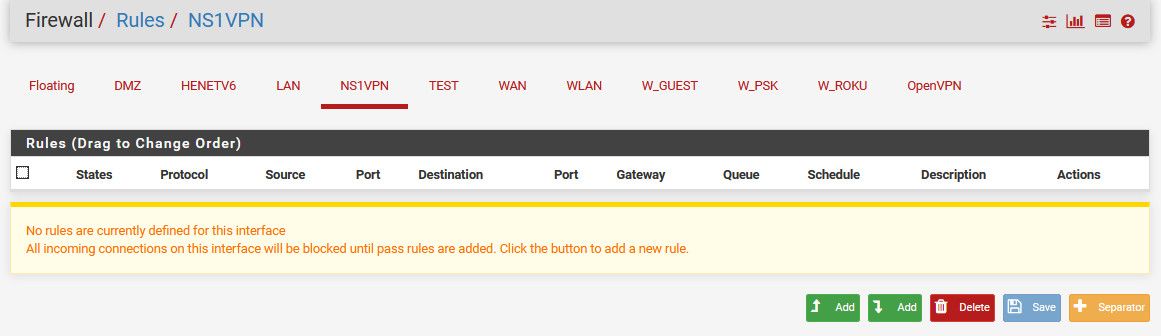
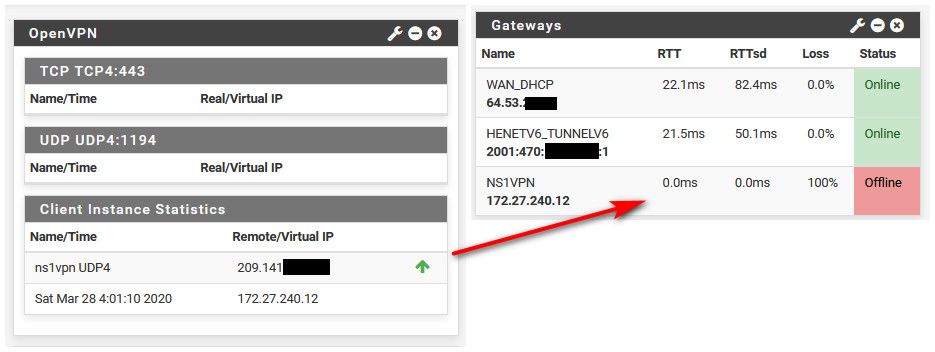
-
@johnpoz said in Can I use one of my 6 physical network ports to be a vpn port?:
How do you think you going to use normal wan and resolver not have a dns leak?
Did you hand your client on your vpn network a different dns? If you have him ask pfsense then yeah your going to show a "leak" But your resolving, your not forwarding.. So your not handing all your dns to anyway anyway..
Yes I have given the vpn network a different dns
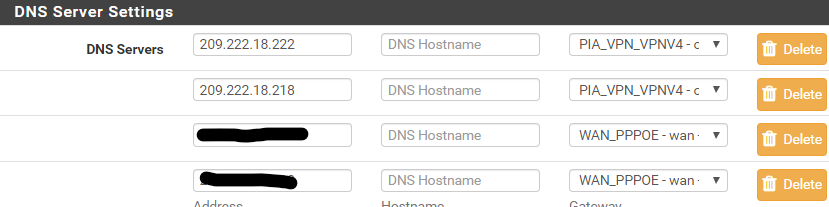
that kill switch method they used was if you send ALL traffic to them! And if they down, then all traffic stops... That is not what your doing, your policy routing.. If you set gateway down rules don't
This is what normally would be your kill switch

But this is also what is prob preventing you from working... If your gateway is down, then you shouldn't have access.
I Do have access even though my gateway is showing as offline, gateway monitoring is active but I cannot find that screenshot above on my system?
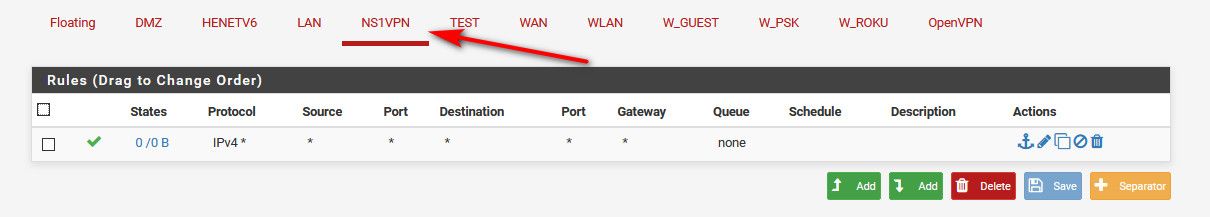
Did you put any rules on your vpn interface you created?

Yes I have this rule on my interface
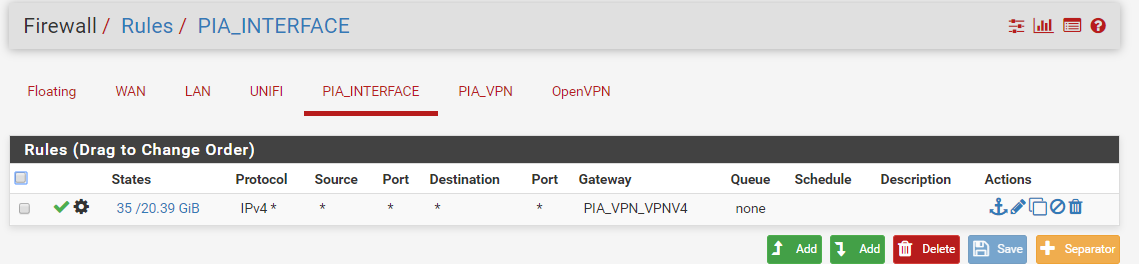
Also when you say trouble recognizing your 4 port nic.. Your doing passthru of the nic to pfsense? Its easier to just let esxi do the nics, and give pfsense virtual nics. vmx3 or e1000
The reason I was having issues was when setting up the VM, if I used the latest Q35-4.2 machine type I would only get 1 port of my 4 port nic so I reverted back to Q35-2.11 to get this working properly
if you have no rules - then yeah you will show offline
I do have this rule
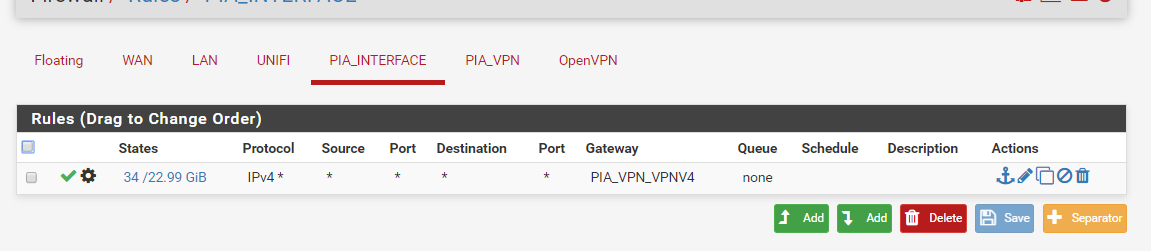
-
Why do you have a gateway set on your interface - to itself???
Where did it say to set a gateway on the interface you created for your vpn connection?
Which is which here?? You have the interface to your vpn... And then you have your own local network interface you created that you want to route out the vpn..
You need a rule on the interface that is vpn connection to allow monitoring to work..
What rules do you have on the PIA_VPN interface???
And NO is not how you would setup dns... All that says hey pfsense if your talking to those dns servers, use this gateway.. If your wanting client on this vpn connection your setting up to use those - then hand him those via dhcp!! Don't even let him ask pfsense..
if I used the latest Q35-4.2 machine type I would only get 1 port of my 4 port nic so I reverted back to Q35-2.11 to get this working properly
again that has ZERO to do with anything.. If you let the host handle the nics, and just give your VM virtual interfaces tied to virtual switches that esxi handles the connections too..
A vm doesn't know anything about how many ports on a nic.. It has a virtual interface, be it e1000 or vmx3 - so you are passing the hardware onto the VM... There is no point in doing this to be honest.. And now you prevent yourself from using those physical interfaces for any other VMs you might want to leverage, etc..
-
@johnpoz said in Can I use one of my 6 physical network ports to be a vpn port?:
Why do you have a gateway set on your interface - to itself???
Where are you seeing this?
As there is no guide for what I am trying to achieve I am finding information from you and information the web, it is obvious I am out of my depth, I am not denying that but what I am finding is advice from you is contradicting guides/information on the web so this is incredibly hard for me as I do not fully understand all the terminology nor the science behind everything, I find information that says do X and then it is shot down by you, the problem is I do not know any better I am just trying to get this interface working
Where did it say to set a gateway on the interface you created for your vpn connection?
As above, this would have been something I have found on the net.
Which is which here?? You have the interface to your vpn... And then you have your own local network interface you created that you want to route out the vpn..
PIA_INTERFACE is the physical interface and PIA_VPN was created automatically during the guide setup?
You need a rule on the interface that is vpn connection to allow monitoring to work..
Unfortunately when you say I need a rule, I have no idea what type of rule? this kind of advice although appreciated means little to me so I go and research and make my best assumption normally to find it is wrong :-(
What rules do you have on the PIA_VPN interface???
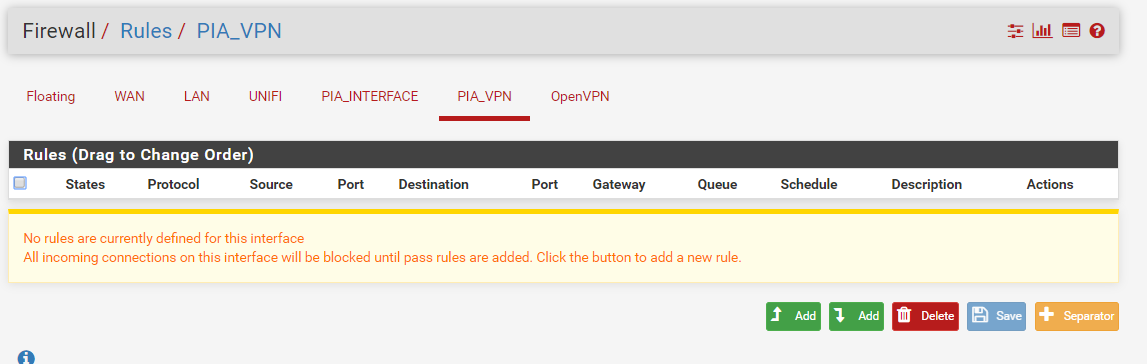
And NO is not how you would setup dns... All that says hey pfsense if your talking to those dns servers, use this gateway.. If your wanting client on this vpn connection your setting up to use those - then hand him those via dhcp!! Don't even let him ask pfsense..
if I used the latest Q35-4.2 machine type I would only get 1 port of my 4 port nic so I reverted back to Q35-2.11 to get this working properly
again that has ZERO to do with anything.. If you let the host handle the nics, and just give your VM virtual interfaces tied to virtual switches that esxi handles the connections too..
A vm doesn't know anything about how many ports on a nic.. It has a virtual interface, be it e1000 or vmx3 - so you are passing the hardware onto the VM... There is no point in doing this to be honest.. And now you prevent yourself from using those physical interfaces for any other VMs you might want to leverage, etc..
This turned out to be a common issue, when spaceinvader one made the video guide on how to install pfsense in 2018 he used Q35.211 as the machine type. That has since progressed to Q35-4.2 which results in pfsense only detecting one port of the four port nic. This has affected quite a few people I was not alone.
I have pfsense installed as a VM on unraid using a seperate HP Microserver. This is seperate to my main server and only runs pfsense, homeassistant and blue iris cctv, that is all it does.
Again, I really appreciate you trying to help me but and it must be tough for you but I assure I am trying as hard as I can to understand and progress. Thank you
-
So how are you going to ping.. You need a rule on that PIA_VPN interface - I showed you this already!!
Please do not reply like that - its makes it almost impossible to read... Just answer the question there is zero reason to quote every line of my post... It right above yours if I have to reread it to understand what your answering..
There is one thing to quote a specific item to point it out specifically - or if your 3 pages later in a thread..
But its becoming dreadful trying to read what your doing with you doing that.. Please stop!!
Put rules on your interface.. Does it now show that is up - there is really nothing your gong to be able to do if you don't get it to show that the gateway is up..
Q35-4.2 which results in pfsense only detecting one port of the four port nic
Again ZERO reason to do that - just let the VM host handle the hardware... The whole freaking point to running a VM.. There is ZERO reason to hand off direct hardware to just run pfsense... Are you saying when the VM is using e1000 or vmx3 virtual nics its not fast enough? You can not push enough pps?? That would be the only reason to do such a thing.
-
Thank you for your time, I will address this at a later date, it is just too beyond me. I have restored my backup to before I attempted this.
