OpenVPN no authenticated log generated
-
I don't know how this file is used, in what context, etc.
@tienpro113396 said in OpenVPN no authenticated log generated:
openvpn.attributes.sh
-
@tienpro113396
Sorry, I don't know why it would have stopped logging but I think using logger is possibly a better way to do this.Forgot to mention that there are functions available to format the numbers but that wasn't so important to me.
-
@Gertjan Yes I need to logging users disconnect time, I do a research and know that I can edit that file to get the disconnected log in openvpn.log file. In 5 days I have both authenticated and disconnected log and boom only disconnected log appear there. No more authenticated log
-
Put on the second line in your script file openvpn.attributes.sh these commands :
/usr/bin/logger "test"
/usr/bin/logger $script_typealso, type
logger "test"at the command line (console or SSH access - no GUI) and have a look at the main System log ^^
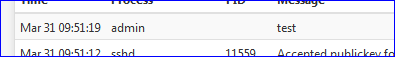
Now, test.
When this file gets used, it will log. -
@Gertjan great tips. And I dont have "test" on StatusSystem\Logs\OpenVPN :((
Change to that, right?if [ "$script_type" = "client-connect" ]; then if [ -f /tmp/$common_name ]; then /usr/bin/logger "test" /usr/bin/logger $script_type /bin/cat /tmp/$common_name > $1 /bin/rm /tmp/$common_name /bin/echo "$(date +'%b %d %H:%M:%S') pfSense2 openvpn: user '${common_name}' authenticated" >> /var/log/openvpn.log /bin/echo "$(date +'%b %d %H:%M:%S') pfSense2 openvpn: user '${common_name}' authenticated" >> /home/tien.tran/testlog.log fi elif [ "$script_type" = "client-disconnect" ]; then command="/sbin/pfctl -a 'openvpn/$common_name' -F rules" eval $command /sbin/pfctl -k $ifconfig_pool_remote_ip /sbin/pfctl -K $ifconfig_pool_remote_ip /bin/echo "$(date +'%b %d %H:%M:%S') pfSense2 openvpn: user '${common_name}' disconnected" >> /var/log/openvpn.log fi exit 0 -
There was also "explicit-exit-notify" and automatic timeouts.
You can see some discussion in Redmine: issue 9085
-
@tienpro113396 said in OpenVPN no authenticated log generated:
And I dont have "test" on StatusSystem\Logs\OpenVPN :((
That's right.
the "logger" command will log in the System log (as said above). -
... and Redmine 9108
-
That redmine ticket was closed because .... the (your) issue isn't an issue ;)
-
@biggsy I added "explicit-exit-notify 3" before and got some error so I delete it :v
-
@Gertjan Thanks! I see that log.I will check more about that
-
True - but there was some discussion that others might find interesting or useful.
-
hey all
does it really make sense to do scripting in core pfS files ?
i dont think so.
if you want to receive emails when vpn-clients log in or out
use the method described in this posthttps://forum.netgate.com/topic/151351/email-notification-openvpn-client-connect-common-name/26
as far as some others are concerned if you read the post from top to bottom
you can use a nice working tooltruely mentioned
as @Gertjan mentioned you or someone can aff logger to the script to get more information into the logthe main question still remains
does it really make sense to do scripting in core pfS files ? -
@noplan said:
does it really make sense to do scripting in core pfS files ?
No, it's not ideal to modify the core files. However, did you see the note in 9085 about conflicting scripts?
Putting client-connect and client-disconnect entries in Custom options caused /usr/local/sbin/openvpn.attributes.sh to be overridden. (I wonder if users of the solution in the other topic are seeing that.)
As openvpn.attributes.sh appears to be cleaning up pf table entries on client-disconnect, it didn't seem wise to override it. Adding the two logger lines to it seemed to be the safer, if not the cleanest, way.
-
@Gertjan
how can they (.sh scripts) can make me coffee .... /me pretty interested ;)
but for real dyin from coffee overdose not the best way to leave this world ... -
help me out, still early mornin here,
i get the concern at client-connect (point taken)
i dont get it at client-disconnectso addin the logger lines to the scripts (connect and disconnect) will be a task for today.
i'll keep u posted on this one.
-
@noplan said in OpenVPN no authenticated log generated:
how can they (.sh scripts) can make me coffee .... /me pretty interested ;)
Scripts build cars, fly planes and launch nukes.
And coffee should be a problem ? -
@noplan said in OpenVPN no authenticated log generated:
help me out, still early mornin here,
i get the concern at client-connect (point taken)
i dont get it at client-disconnectI'm just saying that the solution offered in the other topic (using user-written client-connect and client-disconnect scripts in Custom options) will conflict with and prevent the openvpn.attributes.sh script from running.
Because openvpn.attributes.sh uses pfctl to kill state entries when a client disconnects, I think it's better to just add in the logger calls and let the rest of the script do its thing.
By modifying openvpn.attributes.sh, though, you are changing one of the core pfSense files.
-
These lines :
...
client-connect /usr/local/sbin/openvpn.attributes.sh
client-disconnect /usr/local/sbin/openvpn.attributes.sh
...
are placed into the openvpn server config file when one of these LAST two options are chosen (User Auth ...) :Each pfSense OpenVPN server instance has a config file here : /var/etc/openvpn/.....
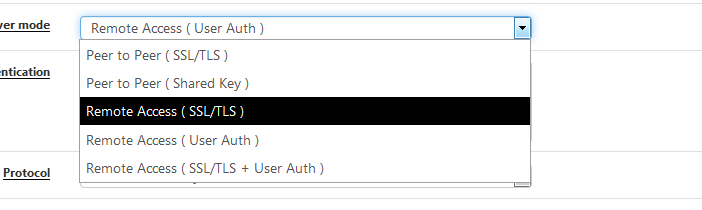
So, when User names and passwords are used, "/usr/local/sbin/openvpn.attributes.sh" is used with the client-connect and client-disconnect commands.
In that case, adding client-connect and client-disconnect commands in the "Custom options" box has consequences and or side effects. Which ones ? Dono, up to you to find out.
So, when you want to use client-connect and client-disconnect commands (with your own scripts) in the Custom options box, you should not chose to use User/password auth, just SSL/TLS.
Btw : had to look up in the manual, the one that explains it all ;)
-
Thanks for that @Gertjan. By "the manual" I assume you mean the code.
I've only ever used the last two options and didn't realize that openvpn.attributes.sh wasn't used in the top three.
Hmmm...
I think I can see why it wouldn't apply to Peer to Peer but I'm now wondering why it wouldn't apply to Remote Access (SSL/TLS)Got it!