Access servers on lan
-
Hi,
I've created OpenVPN server and clients can connect without problems.
But I miss some configuration so that clients can access other servers on the LAN interface subnet.
OpenVPN Server has LAN IP 192.168.135.223.
Tunnel network is 192.168.144.0/24
My first client get @ 192.168.144.2. So far, so good. Ofc pfsense has 192.168.144.1 on that subnet.
I can connect from clients to pfsense on 192.168.135.223. Once on pfsense I can connect to any servers on my lan. For example 192.168.135.93 and any other subnet too. For example xxx.214.182.129.
BUT on my clients I cant connect to 192.168.135.93 or any other servers on the pfsense LAN subnet. I can connect to xxx.214.182.129 without problems because it's not on the LAN network.From pfsense :
nc -vz xxx.214.182.129 22
Connection to xxx.214.182.129 22 port [tcp/ssh] succeeded!
nc -vz 192.168.135.93 22
Connection to 192.168.135.93 22 port [tcp/ssh] succeeded!From client :
nc -vz xxx.214.182.129 22
Connection to xxx.214.182.129 22 port [tcp/ssh] succeeded!
nc -vz 192.168.135.93 22
nc: connect to 192.168.135.93 port 22 (tcp) failed: Connection refusedThis is not a firewall block on 192.168.135.93. I dropped the firewall and it was the same.
So, what should I configure to access LAN servers from OpenVPN clients ?
-
Show your OpenVPN setting and Firewall Rules via screenshots.
-Rico
-
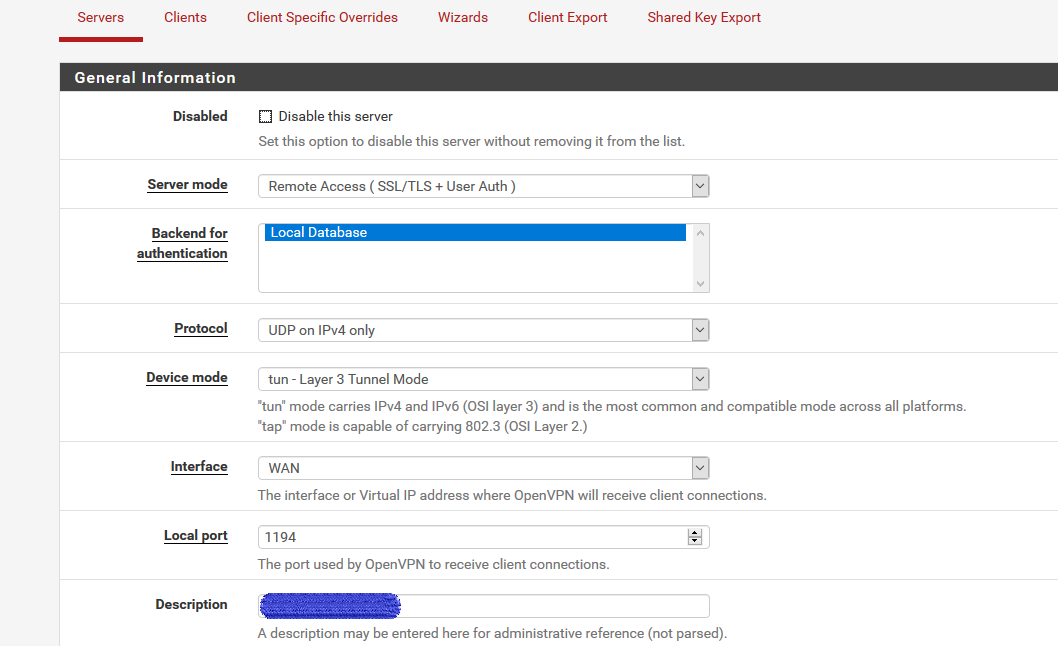
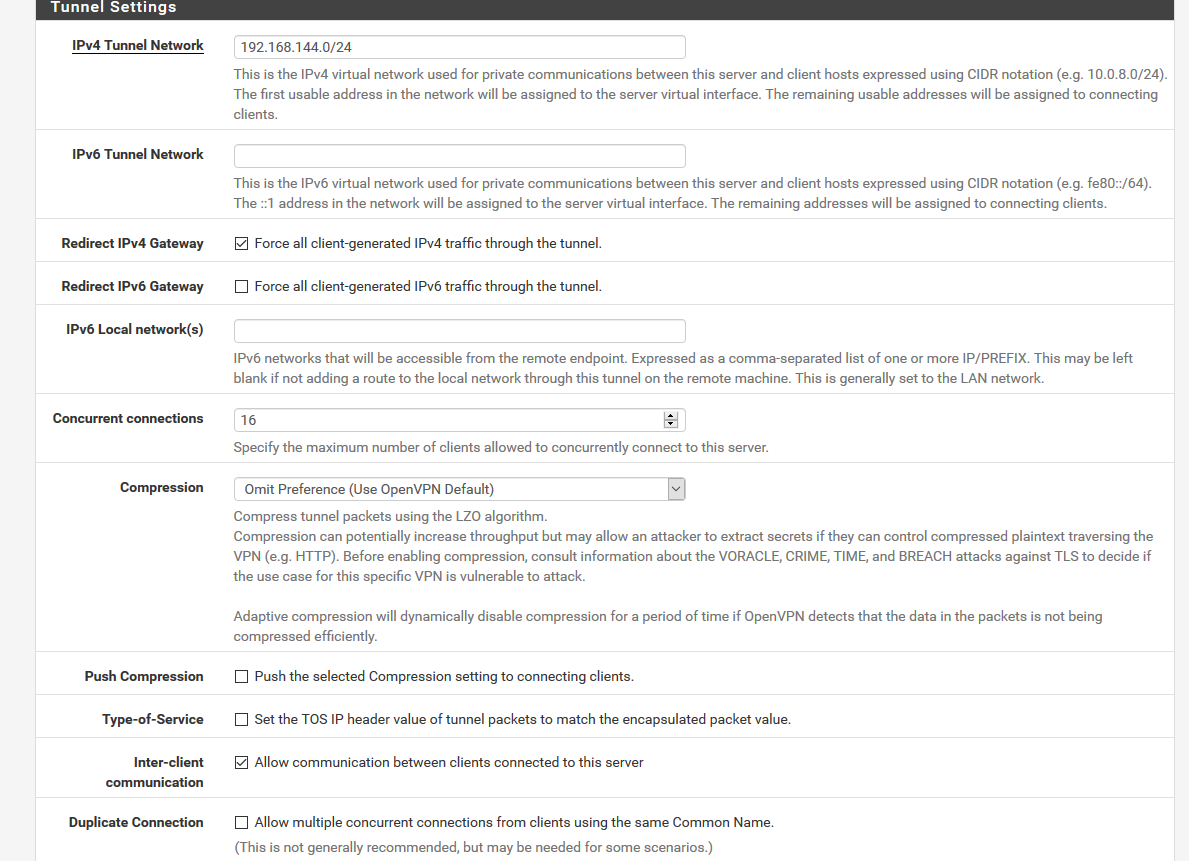
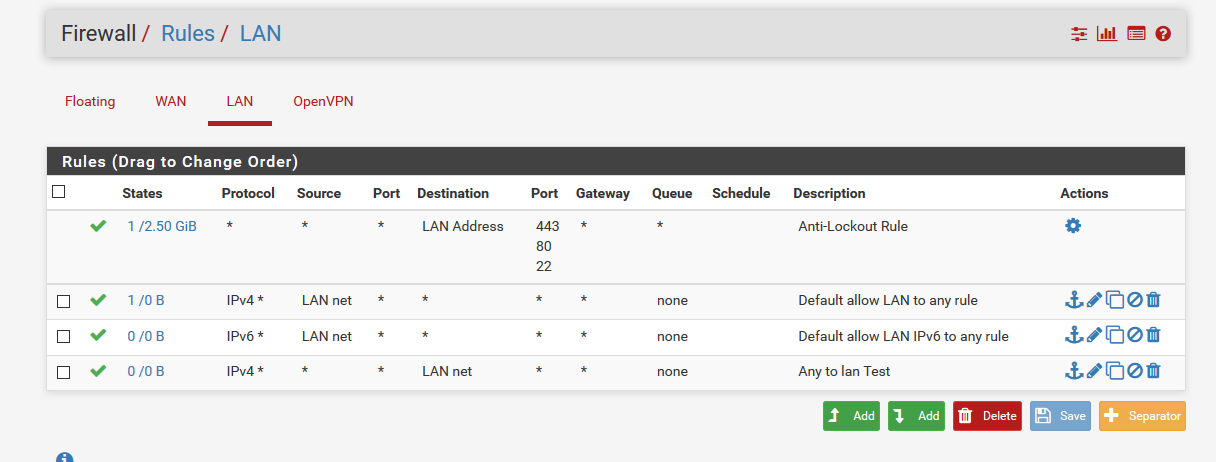
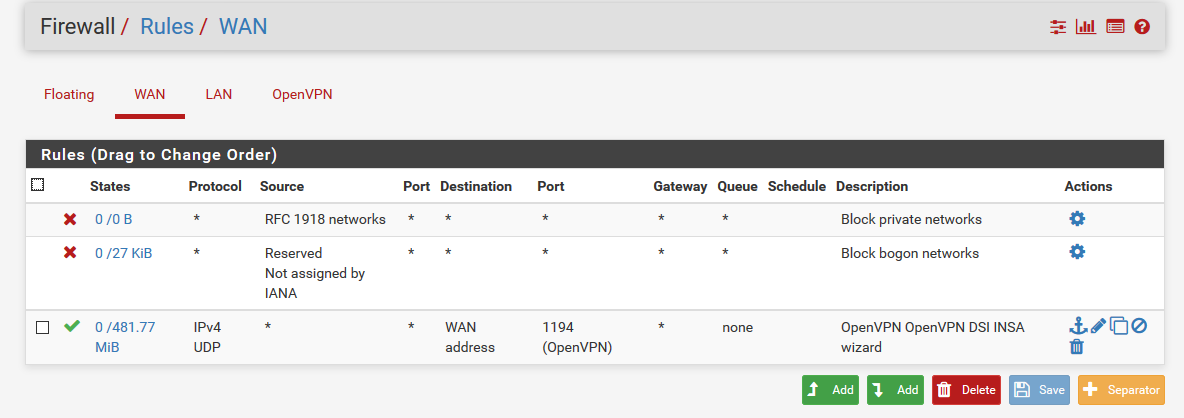
-
The Firewall "OpenVPN" tab matters most because your have problems with incoming traffic there, right?
-Rico
-
Just default on that tab :
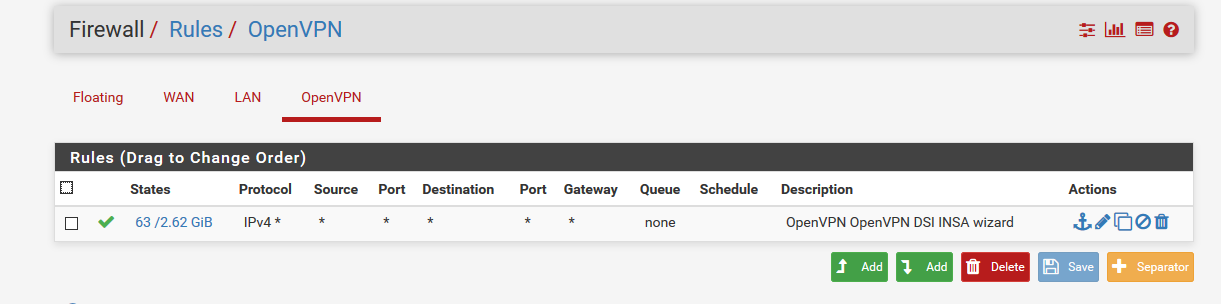
-
Are your clients using pfSense as gateway or are they pointing to any other router?
If you try to access Windows servers keep in mind that the Windows Firewall blocks any traffic outside of local/known subnets. Disable the Windows firewall for testing on the target side.-Rico
-
Well, clients are using pfSense as a gateway as far as I understand. I've checked "force all traffic through the tunnel" as you can see.
I have no problem with windows server at all. The settings seems correct for that part since the clients can access all windows servers and shares.
Maybe I should say that the pfSense only purpose is OpenVPN server so that outside clients can connect to the lan. No server from the lan use the pfSense server.
The only problem I have is to access servers on the same lan subnet that the LAN interface of the pfSense. I can't access 192.168.135.0/24 from the clients. Only from the pfSense server. And the pfSense server (.223) is not the gateway for this lan; the gateway is .1. -
Well your problem is Asymmetric Routing if you use different gateways. Your servers send traffic for 192.168.144.0/24 back to the other .1 gateway.
-Rico
-
solved ?
settings here ?
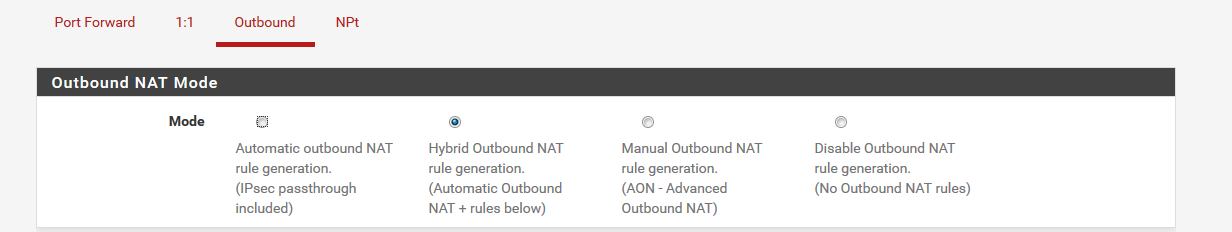
-
Outbound is set to Hybrid Outbound NAT already.
And yes, I guess the problem is asymetric routing since the pfSense box is not the gateway of that lan. Just a server that act as OpenVPN server.
How can I solve that ? -
Well, well, I found the solution by myself, with a little help from Rico.
The solution was to add, while not recommended, the gateway to the LAN interface.
So a Gateway was created in Routing/Gateways and assigned to LAN in Interfaces/LAN.
And that's it, now I can access all servers on the LAN subnet and all other subnets too.
Like :$ nc -vz 192.168.135.93 22
Connection to 192.168.135.93 22 port [tcp/ssh] succeeded!
$ nc -vz 192.168.135.5 443
Connection to 192.168.135.5 443 port [tcp/https] succeeded!
$ nc -vz xxx.214.182.129 443
Connection to xxx.214.182.129 443 port [tcp/https] succeeded!But I wonder how this pretty common situation is not already documented ??
-
@mururoa said in Access servers on lan:
But I wonder how this pretty common situation is not already documented ??
This is not common :
@mururoa said in Access servers on lan:
the pfSense box is not the gateway of that lan.
Common is : pfSense is the router/firewall/OpenVPN server of the LAN(s).