Port 0 seems to sneak by firewall logging.
-
I have a lot of these logs in my firewall log.
Last rule is a rule that blocks everything on my WAN interface without logging. I made this so I could easily enable the log when troubleshooting but otherwise won't be bothered by everyone probing the firewall.But these still show up:
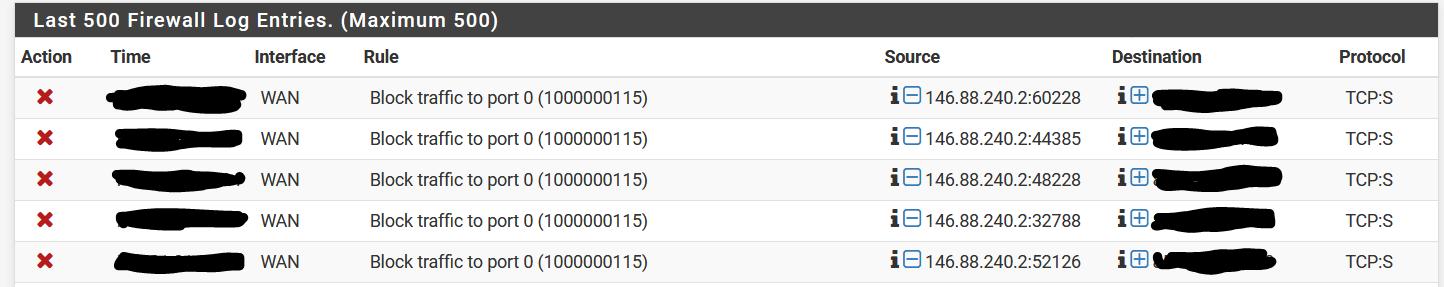
I tried to search for traffic to port 0 but I couldn't find much.
Why do I see these when I block everything without logging?
Also tried to put in a rule that would block port 0 specifically, but that is impossible.
-
Because it is an automatic rule quite high in the rule set.
Look at
/tmp/rules.debugin that case.Looks like the firewall just doing its job.
-
@Derelict said in Port 0 seems to sneak by firewall logging.:
Because it is an automatic rule quite high in the rule set.
Look at
/tmp/rules.debugin that case.Looks like the firewall just doing its job.
Thanks, I found it. It's this one:
block log quick inet proto { tcp, udp } from any to any port = 0 tracker 1000000115 label "Block traffic to port 0"Is this hard coded into the source code or is there someway to change these automatic rules?
-
Not really. There isn't any reason to want to not block traffic to or from port 0.
You can disable logging of the blocks here:
Status > System Logs, Settings, Log packets matched from the default pass rules put in the ruleset
But I'm not sure why you would want to.
-
@Derelict said in Port 0 seems to sneak by firewall logging.:
Not really. There isn't any reason to want to block traffic to or from port 0.
You can disable logging of the blocks here:
Status > System Logs, Settings, Log packets matched from the default pass rules put in the ruleset
But I'm not sure why you would want to.
Thanks @Derelict.
Well, the WAN interface is probed constantly so I don't want to log that. I want to log the blocks on the other interfaces though.
But I'll do it the other way around. I remove all logging by default block rules and put in a last rule for logging where I want to log.
-
-
@JKnott said in Port 0 seems to sneak by firewall logging.:
Why are you hiding the time?
hehehe great question - inquiring minds need to know! ;)

-
@JKnott said in Port 0 seems to sneak by firewall logging.:
????
Why are you hiding the time?
So you wanna know why I hid the time but you haven't asked why I didn't hide the source IP and what the source IP is?
The plot thickens...
-
Know exactly what it is ;)
www.arbor-observatory.com.
Its their netscout scanner.. Is a given you would hide your dest IP.. As to why not hide the source - because its not your, and doesn't give away any sort of info.. So makes sense to not block it.
What doesn't really make a lot of sense is blocking the time - unless you think we could look into their logs at that exact time and see who they were scanning ;) hehehe Which I would bet would be thousands and thousands of IP at that exact same second ;)
-
@johnpoz said in Port 0 seems to sneak by firewall logging.:
What doesn't really make a lot of sense is blocking the time - unless you think we could look into their logs at that exact time and see who they were scanning ;) hehehe
The power of The Moderator and Inquiring Minds shall not be underestimated
