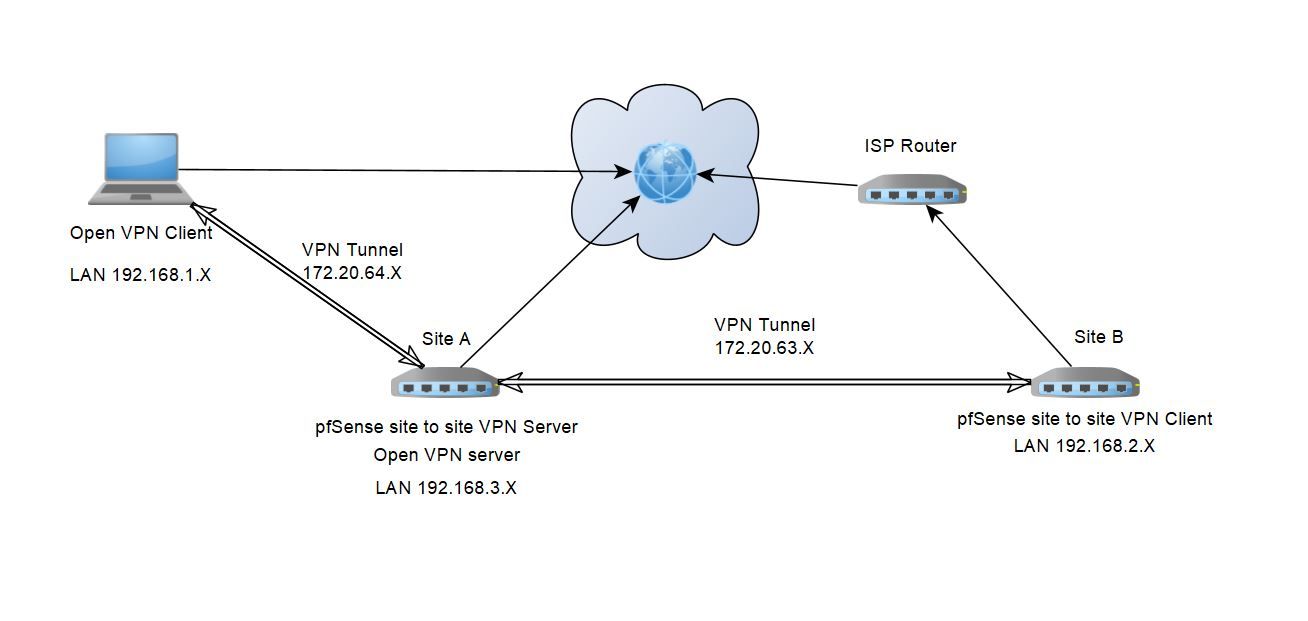
Unable to access Site B through Site to Site VPN when remote connected to Site A.
-
You have also to tell the pfSense on site B the route to the access servers tunnel network.
To do so open the OpenVPN settings on site B and add the access servers tunnel network to the "Remote Networks". -
@MWZotti
On the OpenVPN server page, there's a setting Redirect IPv4 Gateway, which forces all traffic through the VPN. If that is set, you should be able to reach B. If it isn't, you'll need a route to do that and also return.
-
I am heading out there this evening and will give that a try. Would this be the 172.20.64.0/24? Since site B is a client would I be doing this at VPN/OpenVPN/Servers and modifying the client?
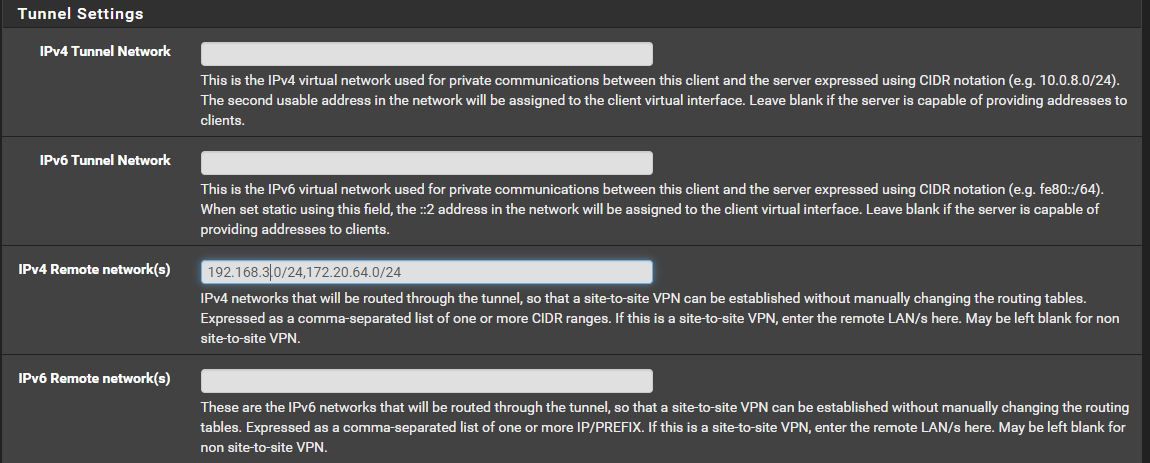
-
@MWZotti
Yes, looks fine. -
@viragomann Thank you. I will let you know how it turns out.
-
@viragomann That worked great. Thank you.
Is this also supposed to help with the port forwarding Site B through the VPN to Site A so they can be accessed or are there other rules I will need to apply?
-
@MWZotti
When forwarding pakets through the VPN to site A, it's necessary to assign an interface to the OpenVPN instance, at least on A, but I suggest to so that on both sites.
Go to Interfaces > Assign, select the respective OpenVPN instance (eg. ovpnc1, ovpns2) and hit Add. Open the new interface and enable it. Enter also an appropriate description.Consider that after adding the interface no traffic may flow across the VPN. You may have to assign firewall rules to the new interface to allow the traffic.
-
@viragomann I was able to get it working. I referenced a different thread and had to read it about 100 times to comprehend what was happening. I think I have everything set correctly and am able to port forward over the tunnel. However I don't know if one of the rules I setup really has any validity.
Link used for reference:
https://forum.netgate.com/topic/74534/a-definitive-example-driven-openvpn-reference-threadSite B I changed the open VPN rules to the following:
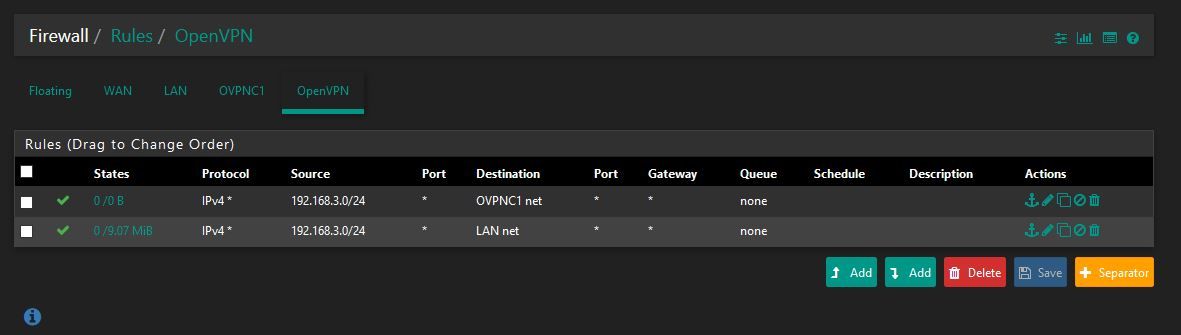
And changed the OVPNC1 firewall rule to pass any traffic.
I don't know if the rule I have set for source on OpenVPN tab for 192.168.3.0/24 actually does anything? Like I said I had a hard time following the guide in that thread, but was able to port forwarding through the tunnel from site B to site A to work. -
@izak01 All traffic appears to be flowing at this time. I can reach both devices while VPN'd into Site A. Devices at Site A can Ping and access site B. Devices at site B can do the same to site A. And ports are forwarded at site A that reach and display info from site B.
Is there something I am missing?
-
@MWZotti
Congratulations!
However, the first rule of the shown tab is useless. It allows access from LAN in site A to the OpenVPN tunnel (transit) network. There is no need to for that.
As you can see in the States column, no packet hit that rule.For your info: "OpenVPN" is an interface group including any OpenVPN instance (servers and clients) you are running on that machine. So it includes OVPNC1 as well.
Rules on an interface group have a higher prio than a rule on a member tab. -
@viragomann Thank you again. I will remove the first rule since it is not needed.
-
I must say using these SG-1100's and pfSense was way easier than when I tried to do it using another vendors firewalls. Thank you again community for your help.