Snort is showing IPs that I don't own
-
I woke up today and saw my pfsense alerts with that listed below and I'm trying to figure out what is going on.
The 80.x is not in my public range, so I'm trying to track down what exactly this might be?Forgot to mention, Snort is only listening on the LAN side -
Any information would be great.
Thanks!4/26/2020 3 Generic Protocol Command Decode 80.24.39.249 60.111.0.0 123:08:00 (spp_frag3) Fragmentation overlap 8:54:22
4/26/2020 3 Generic Protocol Command Decode 80.24.39.249 40.47.0.0 123:08:00 (spp_frag3) Fragmentation overlap 8:54:21
4/26/2020 3 Generic Protocol Command Decode 80.24.39.249 233.186.0.0 123:08:00 (spp_frag3) Fragmentation overlap 8:54:18
4/26/2020 3 Generic Protocol Command Decode 80.24.39.249 233.186.0.0 123:03:00 (spp_frag3) Short fragment, possible DoS attempt 8:54:18
4/26/2020 3 Generic Protocol Command Decode 80.24.39.249 233.186.0.0 123:03:00 (spp_frag3) Short fragment, possible DoS attempt 8:54:18
4/26/2020 3 Generic Protocol Command Decode 80.24.39.249 239.126.0.0 123:08:00 (spp_frag3) Fragmentation overlap 8:54:14
4/26/2020 3 Generic Protocol Command Decode 80.24.39.249 182.11.0.0 123:03:00 (spp_frag3) Short fragment, possible DoS attempt 8:54:11
4/26/2020 3 Generic Protocol Command Decode 80.24.39.249 70.15.0.0 123:03:00 (spp_frag3) Short fragment, possible DoS attempt 8:54:01
4/26/2020 3 Generic Protocol Command Decode 80.24.39.249 202.187.0.0 123:08:00 (spp_frag3) Fragmentation overlap 8:54:00
4/26/2020 3 Generic Protocol Command Decode 80.24.39.249 41.13.0.0 123:08:00 (spp_frag3) Fragmentation overlap 8:53:57
4/26/2020 3 Generic Protocol Command Decode 80.24.39.249 41.13.0.0 123:03:00 (spp_frag3) Short fragment, possible DoS attempt 8:53:57 -
@nullvalue said in Snort is showing IPs that I don't own:
233.186.0.0
That one and the 239.126 are multicast..
Its not uncommon for ISP to run multiple layer 3 on the same layer 2 network..
And the others also seem to be some sort of broadcast address notice the ending in 0.0
Bring it up to your ISP - I would "guess" some sort of misconfig on their end.
-
@johnpoz
Thank you, that would make a little sense, but I'm wondering if I'm pointing snort to the internal interface, how I would be able to catch these alerts? Usually when I see alerts I can trace it back down to some program on some computer on my network, but this seems to be on the outside, unless I'm reading it incorrectly, or I have something misconfigured? (which I'm suspecting). -
https://forum.netgate.com/post/831808
-
@Derelict
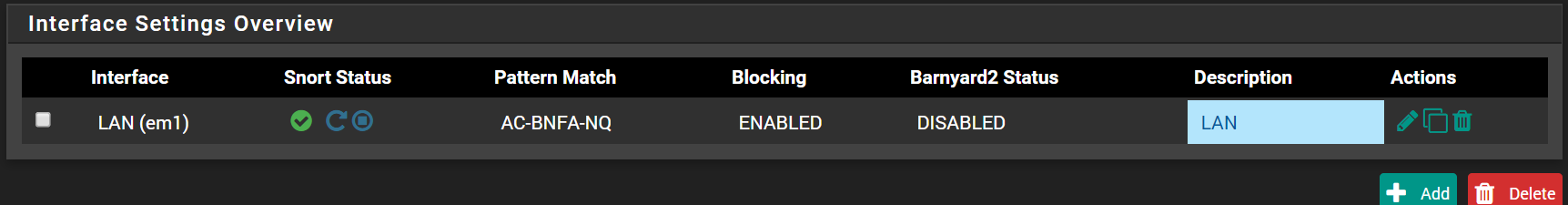
I have only the LAN (internal, I have no dmz and everything sits behind pfsense) enabled for Snort, which why I was confused about the alerts which references sources to be external IPs, or perhaps I'm reading it incorrectly? From my understanding, it should be an internal to -> external or external <--- internal.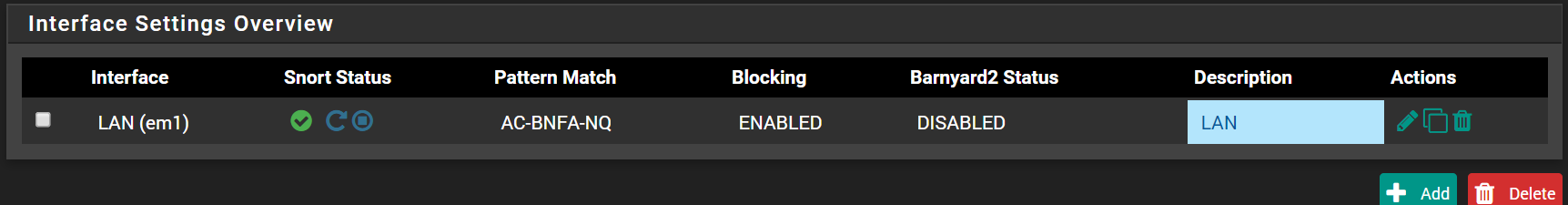
-
So just to be sure you are showing us the correct logs, did you copy the alerts show above from your LAN? You should go to ALERTS and then select LAN in the Interface drop-down selector. That will show alerts from the LAN. The default choice on that tab is the WAN.
If these alerts are from your WAN side, then it is likely something going on from your ISP's side.
If these alerts are from your LAN, and that source IP of 80.24.39.249 is not in your LAN, then I would start looking for a misconfigured device in your LAN. Snort will put the interface it runs on in promiscuous mode. That means the interface will sample and copy all traffic flowing on the wire. The most obvious source of "wrong IP" traffic on your LAN would be a misconfigured device on the LAN. Could also be a multi-homed (multiple NIC interface) host where one of the ports has an incorrect IP address setup.
The next thing to check, although I would expect this to be much less common and also to generate other serious issues, is a cross-connection between your LAN and some other network.
-
Are these guys your ISP ?
AS details for 80.24.39.249 :-
route: 80.24.0.0/16
descr: RIMA (Red IP Multi Acceso)
origin: AS3352
mnt-by: MAINT-AS3352
created: 2005-07-21T12:32:14Z
last-modified: 2009-08-19T06:59:24Z
source: RIPE
remarks: ****************************
remarks: * THIS OBJECT IS MODIFIED
remarks: * Please note that all data that is generally regarded as personal
remarks: * data has been removed from this object.
remarks: * To view the original object, please query the RIPE Database at:
remarks: * http://www.ripe.net/whois
remarks: ****************************Monday, 27 April 2020 at 15:26:06 British Summer Time