OpenVPN Config with no internet
-
Hi guys,
I've configured a PFSense server in AWS to just use as a remote access VPN. So I just want all the users of my VPN to just go out to the internet all using the same public IP... no need for a a LAN.
Should be simple.... And I think I managed to configure everything... but after a user is connected to the VPN he doesn't have internet access...
I've checked and we have the NAT rule for the OpenVPN to the WAN interface.... and PFsense itself can connect to the internet... It's not just a DNS issue because I cannot even ping a server on the internet using IP....So what am I missing? Any tips?
Thanks a lot for all your help.
-
Post your server1.conf (/var/etc/openvpn). Post your NAT rules. Post the firewall rules on your OpenVPN tab.
-
First, thanks for trying to help.
Here are the configs:
cat /var/etc/openvpn/server1.conf:
dev ovpns1 verb 7 dev-type tun dev-node /dev/tun1 writepid /var/run/openvpn_server1.pid #user nobody #group nobody script-security 3 daemon keepalive 10 60 ping-timer-rem persist-tun persist-key proto udp4 cipher AES-128-CBC auth SHA256 up /usr/local/sbin/ovpn-linkup down /usr/local/sbin/ovpn-linkdown client-connect /usr/local/sbin/openvpn.attributes.sh client-disconnect /usr/local/sbin/openvpn.attributes.sh local 10.0.1.247 tls-server server 10.0.8.0 255.255.255.0 client-config-dir /var/etc/openvpn-csc/server1 username-as-common-name plugin /usr/local/lib/openvpn/plugins/openvpn-plugin-auth-script.so /usr/local/sbin/ovpn_auth_verify_async user TG9jYWwgRGF0YWJhc2U= false server1 1194 tls-verify "/usr/local/sbin/ovpn_auth_verify tls 'MySERVER' 1" lport 1194 management /var/etc/openvpn/server1.sock unix push "dhcp-option DNS 8.8.8.8" push "dhcp-option DNS 1.1.1.1" push "redirect-gateway def1" client-to-client ca /var/etc/openvpn/server1.ca cert /var/etc/openvpn/server1.cert key /var/etc/openvpn/server1.key dh /etc/dh-parameters.2048 tls-auth /var/etc/openvpn/server1.tls-auth 0 ncp-ciphers AES-128-GCM persist-remote-ip float topology subnetI saw that when I export a configuration, the OVPN file does not have the :
dhcp-option DNS 8.8.8.8
dhcp-option DNS 1.1.1.1
redirect-gateway def1Shouldn't it? But I've tried adding it and it also doesn't seem to work...
Open VPN Firewall Rules:
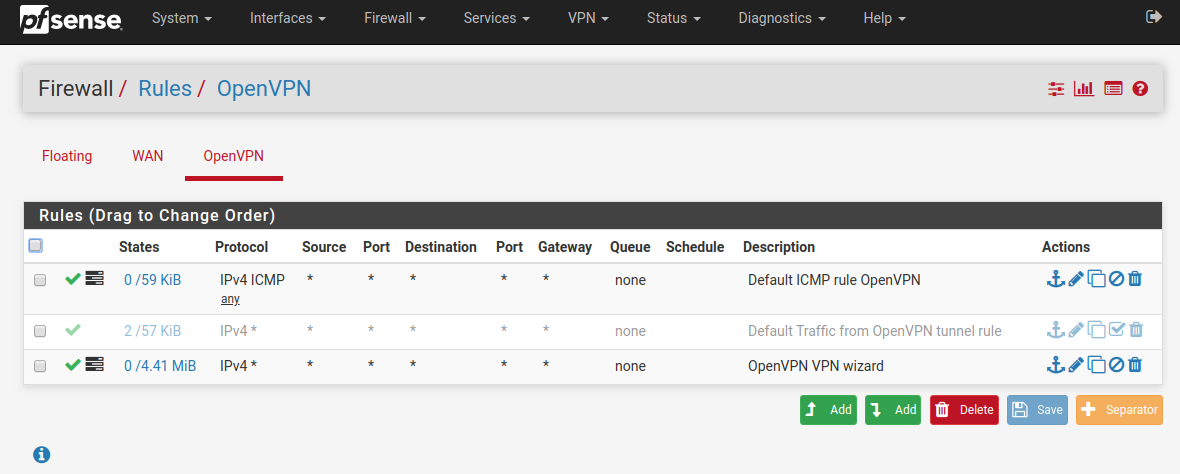
Firewall Nat Outbound Rules:
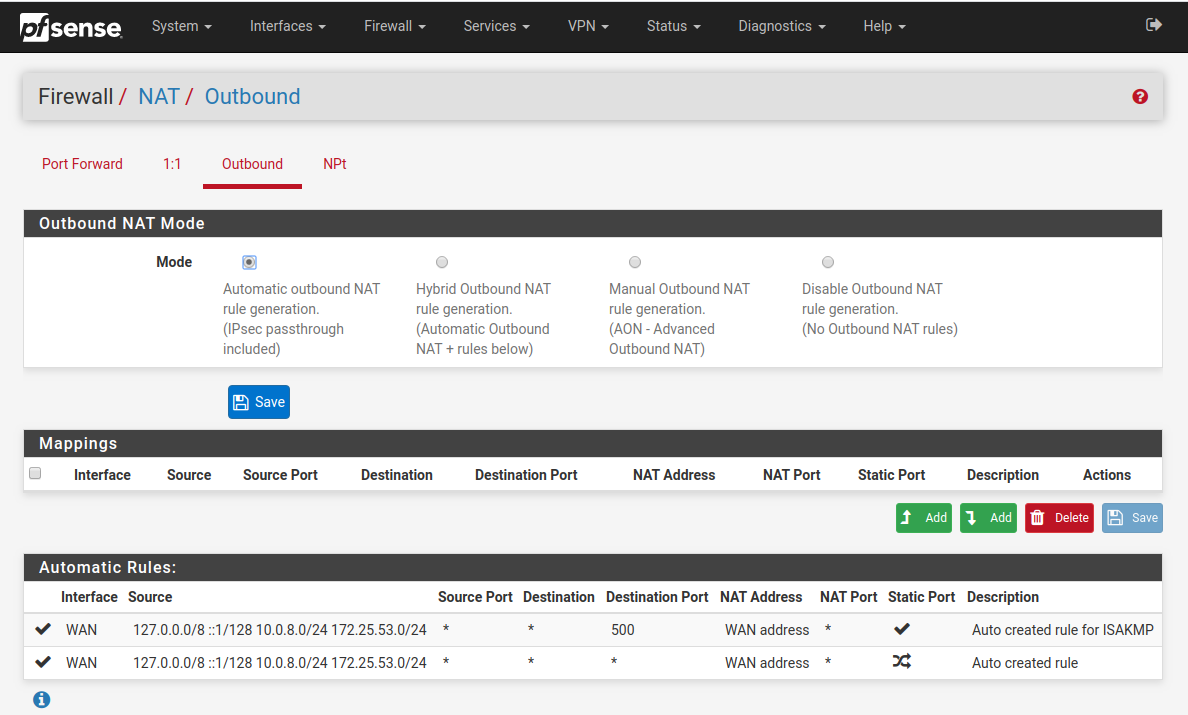
For the OpenVPN range, I put 10.0.8.0/24.
One thing that might be an issue (or not) is that, since I just want to use the VPN for remote access, not for LAN access, there is no LAN interface. The purpose is just for all users to connect here and go to the internet all with the same IP, so that we can then on some sites restrict it's access to just the VPN IP.
I really don't see anything wrong... We can create an user and connect to the VPN, but after connecting we just don't have internet. The VPN itself has internet through the WAN interface... we can do traceroutes, updates, etc...
Maybe something on AWS side (we disabled the source/destination check for the interface)...
Hope you can help.
Thanks again
-
According to the config, PFsense is double NAT'd and the WAN interface is sitting in the 10.x.x.x space. I would double check the netmask on the WAN interface and verify that there's no overlap in your tunnel network. Also, it's possible you may need to uncheck the "Block private networks and loopback addresses" and/or the "Block bogon networks" options on the WAN interface.
Are you creating a client cert during user creation? I've seen issues when the client cert doesn't get created. Although, this may depend on what authentication method you're using.
Do you have a Certificate Revocation list defined and selected in your config? I've seen issues in the past when a CRL isn't defined also.
Regarding your DNS export, according to the config, it's there:
push "dhcp-option DNS 8.8.8.8"
push "dhcp-option DNS 1.1.1.1"
push "redirect-gateway def1"On your OpenVPN tab, even though an any/any rule "should" work, I've been making these rules explicit as of late just to ensure that traffic is being matched correctly and sent down the correct interface. I.e.. you may want to define your tunnel network as the source address. Also, the rule you have for ICMP is redundant and can be removed.
As far as not having a LAN interface, considering your use case I wouldn't think that matters. However, I've never deployed it that way, so I'm not sure.
Not seeing anything glaring otherwise. I would review the client's routing table after they connect and then go thru the firewall logs while your're doing live testing. A useful troubleshooting app I'd recommend using is PingPlotter (https://www.pingplotter.com).
-
Hi @marvosa ,
thanks for the tips...
I changed the OpenVPN network to 192.168.70.0/24.... In the WLAN configs the option "Block private networks and loopback addresses" was already unchecked, bu I also unchecked the "Block bogon networks" option...The cert is getting created alright.... when I use the ovpn config file in the client the cert is there and the connection is made and established:
Enter Auth Password: ********* Thu Apr 30 17:53:46 2020 TCP/UDP: Preserving recently used remote address: [AF_INET]3.8.245.156:1194 Thu Apr 30 17:53:46 2020 UDPv4 link local (bound): [AF_INET][undef]:1194 Thu Apr 30 17:53:46 2020 UDPv4 link remote: [AF_INET]3.8.245.156:1194 Thu Apr 30 17:53:46 2020 WARNING: this configuration may cache passwords in memory -- use the auth-nocache option to prevent this Thu Apr 30 17:53:46 2020 [Aptoide] Peer Connection Initiated with [AF_INET]3.8.245.156:1194 Thu Apr 30 17:53:47 2020 TUN/TAP device tun0 opened Thu Apr 30 17:53:47 2020 do_ifconfig, tt->did_ifconfig_ipv6_setup=0 Thu Apr 30 17:53:47 2020 /sbin/ip link set dev tun0 up mtu 1500 Thu Apr 30 17:53:47 2020 /sbin/ip addr add dev tun0 192.168.70.2/24 broadcast 192.168.70.255 Thu Apr 30 17:53:47 2020 Initialization Sequence CompletedIt pings the main VPN interface ok:
ping 192.168.70.1 PING 192.168.70.1 (192.168.70.1) 56(84) bytes of data. 64 bytes from 192.168.70.1: icmp_seq=1 ttl=64 time=53.7 ms 64 bytes from 192.168.70.1: icmp_seq=2 ttl=64 time=50.4 ms 64 bytes from 192.168.70.1: icmp_seq=3 ttl=64 time=48.4 ms 64 bytes from 192.168.70.1: icmp_seq=4 ttl=64 time=50.6 ms 64 bytes from 192.168.70.1: icmp_seq=5 ttl=64 time=50.6 ms ^C --- 192.168.70.1 ping statistics --- 5 packets transmitted, 5 received, 0% packet loss, time 4006ms rtt min/avg/max/mdev = 48.492/50.808/53.776/1.716 msBut it cannot reach any other place...
On the Firewall logs I see this:
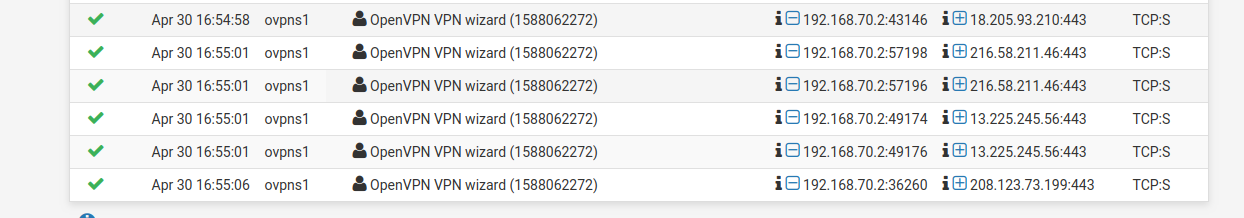
So it seems ok...
But still no internet...
Could it be something missing on the AWS VPC config? To allow internet... but pfsense should just use the wlan interface and that't it... should be transparent to AWS....
Any more ideas?!
-
There may very well be something that needs to be addressed in the AWS VPC settings, however, I am unfamiliar with the platform.
Short of a misconfig that I'm missing, an AWS VPC setting or something happening on the client-side, it's just troubleshooting at this point.
I PM'd you.