IPSec/IKEV2 not connecting with PSK on pfSense 2.5 dev release "AUTH_FAILED & CONNECTING => DESTROYING"
-
Are you sure they were using IKEv2 and PSK? IKEv2 mobile connections would be using EAP auth (EAP-MSCHAPv2, EAP-RADIUS, EAP-TLS), not PSK.
-
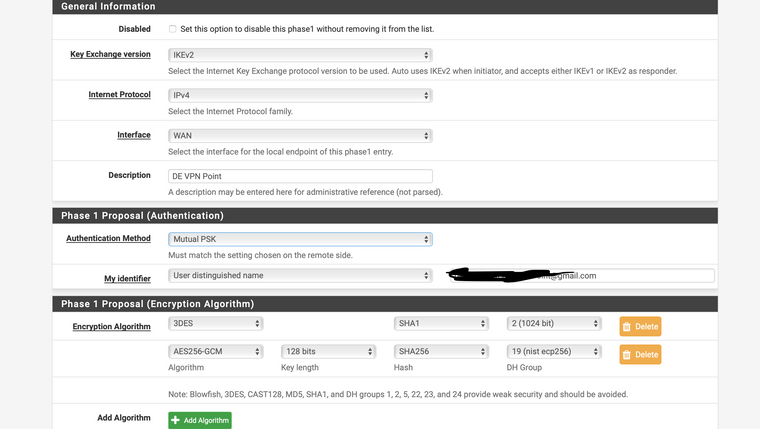
Yes I'm sure. I have IPSEC/ikev2 with Authentication Method Mutual PSK. It was worked on pfSense stable release 2.4.5 But after update to 2.5.0 dev not working. Also I tried clean install pfSense 2.5 with restoring IPSec config and firewall rules. All cases not successful for me.
-
-
What kind of clients? How are they configured?
I don't know of any IKEv2 clients, other than maybe strongSwan itself, which can use non-EAP auth with mobile IKEv2 setups.
-
VPN Clients is Mac OS and iOS users. VPN ikev2 configured in system settings. They are using just PSK key for authentication with out any certificates,non-EAP auth. It works fine on all systems. Maybe this problem related new Strongswan 5.8.4 version in pfSense 2.5 dev
-
@jimp Also in yesterday night I have tested auth with eap-MSChapv2 with cert in pfSense 2.5 dev - it works fine
-
Can you share some more specific details about the IKEv2+PSK Mobile config you had? Ideally, the IPsec section of config.xml would have everything I'd need to see, but it would contain some private info you could redact or change (like the PSK).
Failing that, the Mobile Clients tab settings, the Mobile P1 settings, and an example of how you configured a user account and client would be helpful.
-
@jimp Yes, sure. This is my IPsec config, I changed private info like psk & identifier. As I said early this configuration works fine current stable release of pfsense. Please see attached file
config-pfSense.localdomain-20200428041603.xml -
@jimp Did you have a time for reviewing it?
-
I think I have figured out the problem. I didn't try connecting a client but I configured a 2.4.x and 2.5.x setup with the same settings and the only thing that stood out is on 2.5.0, mobile user keys were being set as EAP in the IPsec daemon config (
/var/etc/ipsec/swanctl.conf) even when PSK was selected for the user.I opened a Redmine issue to track it here: https://redmine.pfsense.org/issues/10505
I committed a fix which should show up on that bug report in a few minutes. It's a small change, you can install the System Patches package and then create an entry for
2c9c2891678fc87dc40359726af81468a3570464to apply the fix once it shows up on the Redmine issue.After that, edit/save/apply on something in IPsec so the config will be rewritten, then try to connect again.
-
@jimp Many thanks! Your fix is working correctly!
Thanks for your support!