Trunking between a Cisco switch and Cisco router
-
Hi there,
I am new to pfSense but I am trying to connect a switch port in trunk mode with 4 VLANs to a router on stick through pfSense.
I am unable to find any documentation on how to form a trunk that carries VLAN tagging in pfSense. I have added a VLAN tag to pfSense interfaces respectively but there is no connection. From switch to pfSense or vice versa and pfSense to router or vice versa.
Could anyone give a hint on how this can be accomplished?
Thank you in advance!
-
Check the book:
https://docs.netgate.com/pfsense/en/latest/book/vlan/pfsense-vlan-configuration.html -
Much like the above link explains, you'd create your VLANs on the correct parent interface and then patch the parent interface to a switchport configured as a trunk. There's not much more too it.
If you're still having issues, we'll need more info. We'd need to see what you've done.
-
Hi,
Thank you for the answers and recommended book.
I have followed the instructions and tried different combinations but still doesn't work. I will expose the scenario.
I am using GNS3 to emulate the network. There is a switch with a Cisco image - vios_l2-adventerprisek9-m and the following configuration on the port connected to Proxmox VE server shown in the picture.
interface GigabitEthernet2/1
switchport trunk encapsulation dot1q
switchport mode trunk
media-type rj45
negotiation autointerface VLAN50
ip address 192.168.100.101 255.255.255.248(VLAN 50 has been created in the switch)
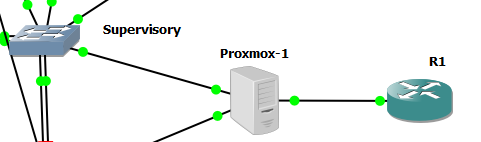
Then, Proxmox VE has a pfSense box inside. Proxmox interfaces are set to VLAN aware as its documentation suggests. I have also asked in Proxmox forums about this and that is their recommendation. In theory Proxmox only passes the traffic acting as a hub. (Firewall disabled in both hypervisor and Virtual Machine).
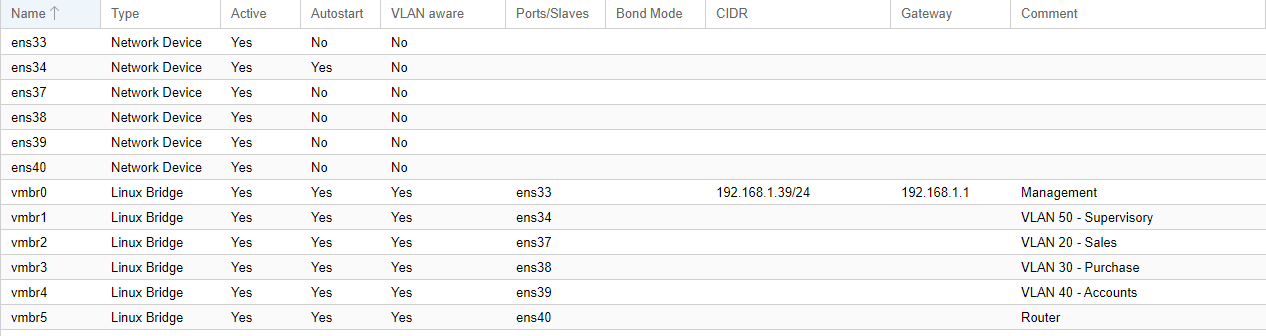
In pfSense I have tried multiple possible configurations, included the suggested in the pfSense book. The WAN interface or em1 to Proxmox and then to the router and em2 towards the switch. Then VLAN 50 created in them respectively.
I have also tried setting a bridge with the parents interfaces and the em1.50 and em2.50. ICMP is allowed in the Firewall rules on every interface
The only configuration that works is when VLANs are removed and I bridge the parent interfaces then the ping is successful, but the switch has to be in access mode and the router cannot have sub interfaces.
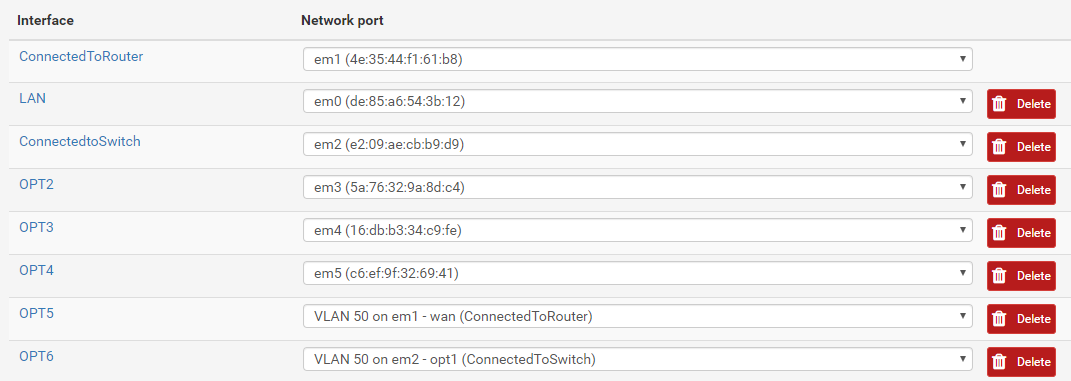
At last, the router - 7200 Software (C7200-JK9S-M), Version 12.4. With the following sub interfaces, connected to em1 through Proxmox. Subnet mask in the router is x.x.x.248 or 29, same as in the switch.
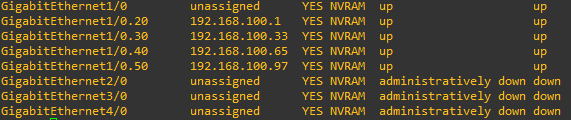
Is it a problem that the interfaces in the switch are Gigabit? I have had the same issue with Proxmox, not being able to set it up as trunk and pass VLAN tags, so I was hoping that pfSense could do it instead.
Should I not use the WAN interface to connect to the router?
I am a student so I might be missing something important. Any help would be appreciate once again!
Thank you in advance.
-
If you're keeping it as pictured, R1 is acting as the internet, so you'll want to configure the physical interface connected to PFsense with an IP outside of your LAN subnet(s). Also, since R1 is the internet, you can remove all of those sub interfaces.
On PFsense, remove the VLAN on em1 (OPT5), configure em1 with an IP in the subnet configured on R1. Then, I would create 3 additional VLANs (20, 30, 40) on em2 and keep the addressing simple like this:
VLAN 20 - 192.168.20.0/24
VLAN 30 - 192.168.30.0/24
VLAN 40 - 192.168.40.0/24
VLAN 50 - 192.168.50.0/24On the switch, create vlan's 20, 30 and 40. Re-configure the SVI for VLAN 50 with an IP in the 192.168.50.0/24 subnet (e.g. 192.168.50.1). Add "ip default-gateway 192.168.50.1", so the switch is accessible on the network via 192.168.50.1 for management (this can be changed to whatever SVI you choose for management).
Unfortunately, I have no familiarity with Proxmox, so any changes made during your troubleshooting may need to be reverted back to default.
Lastly, if you have devices connected to your switch, you'll need to verify that your switch ports are in the correct VLAN.
Should I not use the WAN interface to connect to the router?
R1 is acting as your ISP, so the WAN interface needs to be connected to R1
-
Thank you for your answer