ALLOW: LAN to WAN
-
@anengelsen Do you have any rules at all on the IOT interface? Your device at 10.27.0.26 is trying to reach the dns on the firewall.
-
@chpalmer I have one firewall rule.
Originally I was hoping I could apply this rule, to provide IoT Devices with full-access to external (WAN) resources:
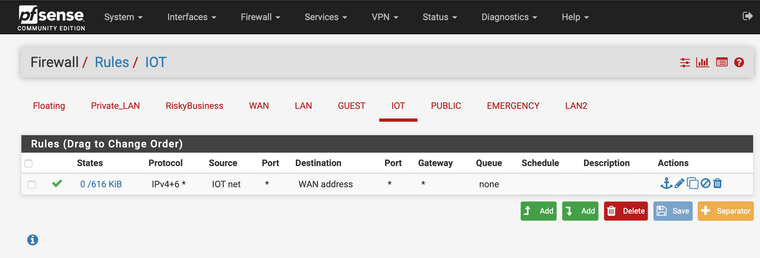
When that didn't work, I was required to employ the following firewall rule.
Note: This (updated) rule DOES provide "IoT Devices" with access the the 'World Wide Web'; but it is wayyy too permissive (for my liking).
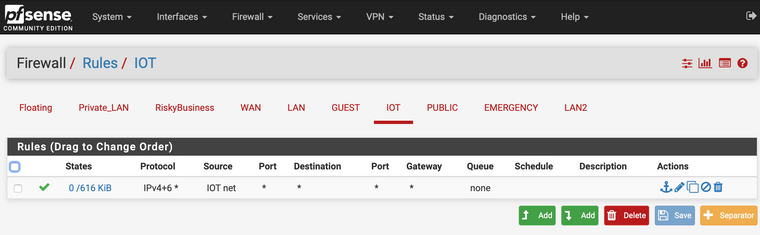
I think I have my NAT rules configured correctly:
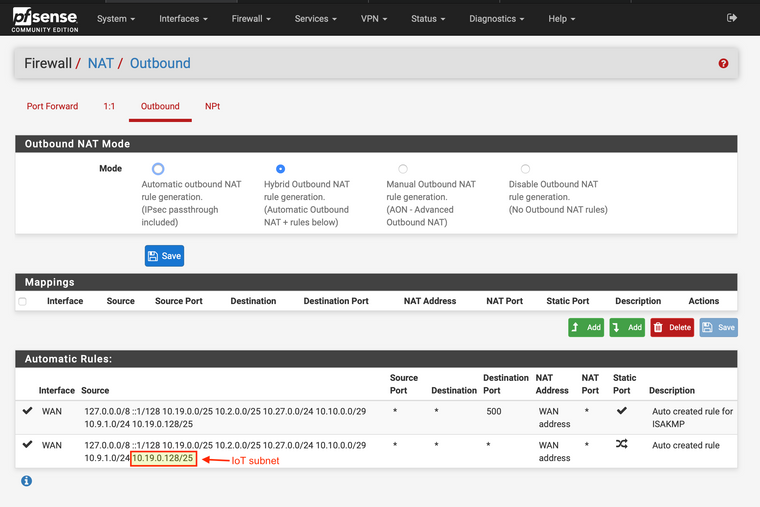
Thoughts?
-Michael- -
If you want to block Traffic to other local networks you need to block or reject (I prefer to reject from internal networks).
There are several ways to accomplish this, mostly I just use as my Destination Firewall Rule Invert Match and choose the RFC1918 alias I have created.
Above this Rule you need to make sure to allow DHCP and DNS to the Firewall, otherwise this traffic will also be blocked by the any to !RFC1918 Rule.-Rico
-
@Rico I think this makes sense to me & I will attempt to implement & test it on my PFSense box.
That being said, would it be possible for you to attach a screenshot that displays the list of firewall rules you have successfully implemented?
Based on your suggestion, would't I want to PERMIT (not block/reject) traffic that matches the inverse firewall rule?
I want to permit traffic w. a destination that does not belong to the RFC1918 address space. Correct?
-
I think you need to read up how the rules work, adding the destination as your WAN address just won't fly.
https://docs.netgate.com/pfsense/en/latest/book/firewall/introduction-to-the-firewall-rules-screen.html
You need to block access on the IOT interface outbound to your other subnets.
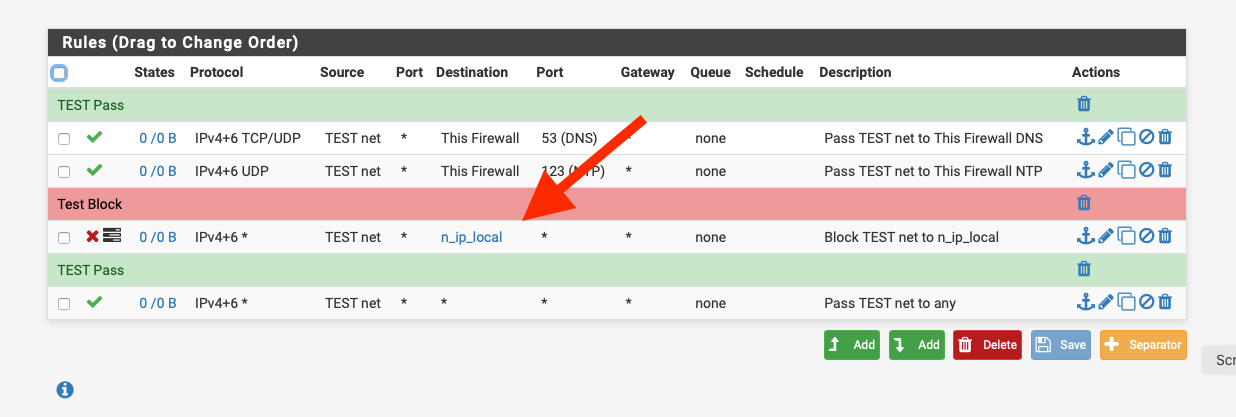
n_ip_local is an alias that contains my local subnets.
-
You need to add an alias under Firewall -> Aliases, and set it to look like this:
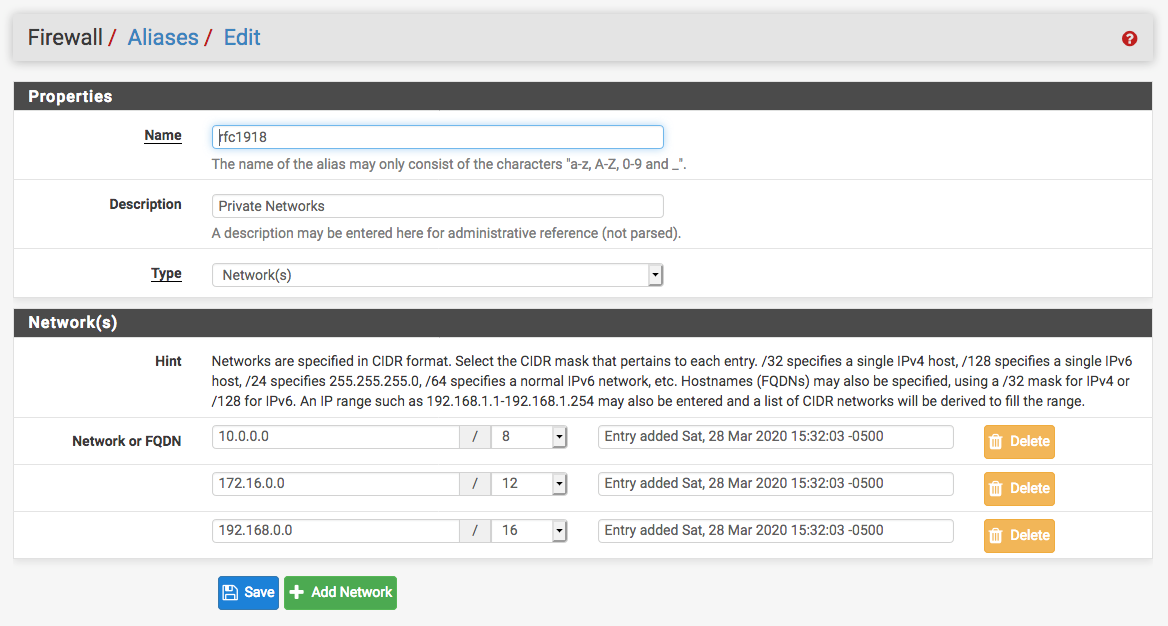
Now, on the Interface you want to give ONLY internet access to, create a block or reject rule that says block source "IoT net" to destination "rfc1918", then save it, then move it to the top of the firewall rule list on the IoT tab. Create another rule, allow "IoT net" to any destination, save it, and move it to the very bottom of the IoT firewall rule list.
That should do just what you want it to do - block IoT from internal networks, yet still allow it to the internet. Make sense?
From the official documentation: Setup isolating LAN and DMZ, each with unrestricted Internet access
https://docs.netgate.com/pfsense/en/latest/config/example-basic-configuration.html#setup-isolating-lan-and-dmz-each-with-unrestricted-internet-accessJeff
-
@NogBadTheBad said in ALLOW: LAN to WAN:
https://docs.netgate.com/pfsense/en/latest/book/firewall/introduction-to-the-firewall-rules-screen.html
You need to block access on the IOT interface outbound to your other subnets.

n_ip_local is an alias that contains my local subnets.
@NogBadTheBad Your first two firewall rules reference "This Firewall".
According to the PFSense Documentation, "This Firewall" resolves to "any IP address assigned to any interface on this firewall [pfSense software version 2.2+]."
https://docs.netgate.com/pfsense/en/latest/firewall/firewall-rule-basics.htmlAs such, wouldn't it make more sense to use "Test address", for the destination value? Or is there a reason why "This Firewall" would be the "preferred" destination?
-Michael-
-
It’s still the same device at the end of the day and the ports are locked down in the rule.
I just copied the firewall rule from another interface and changed the interface and source.
-
@NogBadTheBad said in ALLOW: LAN to WAN:
@anengelsen
It’s still the same device at the end of the day and the ports are locked down in the rule.I just copied the firewall rule from another interface and changed the interface and source.
The only reason I ask is because I am tempted to create an "Interface Group" that contains every-single Interface--except for the WAN interface. I could then apply a firewall rule that will give all interfaces the ability to perform DNS and NTP lookups.
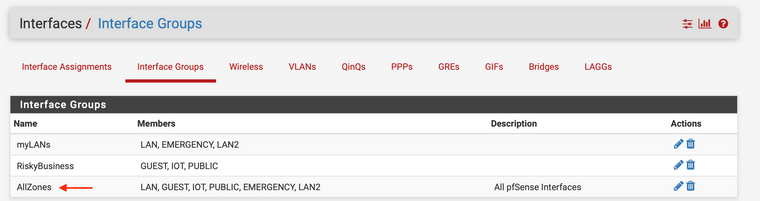
The "this firewall" option makes this very doable!
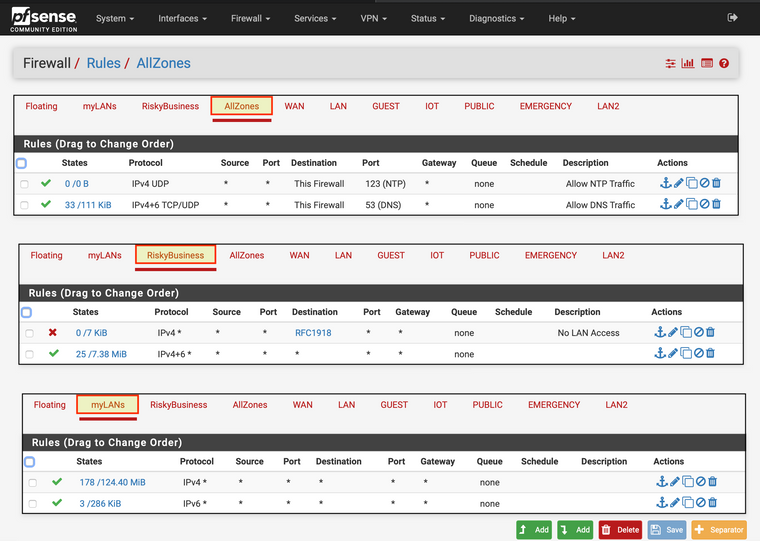
My thought process is...if I have interfaces with similar access requirements; using interface groups is more efficient, compared to maintaining identical firewall rules, that would otherwise be applied to the individual network interfaces.
-
Thank you everyone for your advice, guidance, and support. I now have a much better understanding of firewall rules, firewall aliases, and interface groups.
I was able to successfully create firewall rules that are permissive (allow IoT devices to connect to the Internet); but my firewall rules are not too permissive (IoT devices CANNOT interact with devices connected to the LAN subnet).