Is pfBlockerNG able to block all outbound traffic except whitelistet sites?
-
Dear NollipfSense,
thanks for the answer!
unfortunately I was not able to find the answer to my questions even after performing an extended search, that's why I asked here.Your write, that the firewall blocks all except what I allow. By default, it's the other way round: outbound traffic is allowed unless denied. I know, that I can change that easily by creating a rule in pfSense. The point is, that whitelisting on pfSense level is possible only for IP-adresses. When whitelisting to allow Windows updates for example, I have to whitelist domain names ("windowsupdate.microsoft.com"), that are represented by hundreds of IP adresses. So whitelisting in pfSense itself is not helpful.
That's why I thought, I could perform whitelisting on pfBlockerNG level, that has an option for whitelisting domain names.
However, the question is, how pfSense and pfBlockerNG interact:
- does whitelisting in pfBlockerNG affect only those sites, that are blocked in pfBlockerNG?
or
- can I allow outbound traffic to sites by whitelisting them in pfBlockerNG, even if outbound traffic is generally denied on pfSense level?
or
- is it possible to deny all outbound traffic in pfBlockerNG and whitelist the domains needed?
For a experienced user of pfSense and pfBlocker NG it might sound supid what I'm asking, however I was not able to find an answer to my question regarding the "interaction" of pfSense and pfBlockerNG. I would be very grateful, if you could give me a hint by answering my three questions ;-)
-
@RolandW said in Is pfBlockerNG able to block all outbound traffic except whitelistet sites?:
does whitelisting in pfBlockerNG affect only those sites, that are blocked in pfBlockerNG?
Actually that depends on what whitelisting you are talking about as pfBlocker has two things it can block. DNS Blacklists and via IP Feeds/Lists. DNS Blacklisting interacts with Unbound (the default DNS Resolver) whereas IP Feeds can auto-create rules (or aliases to be used in rules).
So it depends what exactly you are asking.
-
Dear JeGr,
what I want to do is basically simple: block all outbound traffic except for a few whitelisted domains.It's probably not possible to block all traffic using DNS blacklists with wildcards, neither it seems feasible to create IP feeds (that, as I understand, become aliases in pfSense rules), that block everything (1.1.1.1/0 ???), because they would probably be too long. Therefore, if whitelisting in pfBlockerNG is only meant for making exceptions to DNS blacklists, I probably cannot use pfBlockerNG for what I want to do.
Have you got another idea what I could do?
Roland
-
hi,
I'm interested too ....
I should only allow these domains:
*.larksuite.com
*.ibytedtos.com
*.byteoversea.com
*.larksuitecdn.com
and deny all the internet;
even setting up a proxy squid, Larke software needs to have direct access to these domains without going through the proxy;
how do i configure pfBlockerNG?
client PCs use a windows active directory server as dns,
how can I do it?
thanks -
@RolandW It seems that you have the answer ... you claimed in your first post that you had a few IPs ... the correct action is to create aliases with the FEW IP addresses and then create LAN firewall rule to allow those and block all else. You really don't need pfBlockerNG.
-
@NollipfSense said in Is pfBlockerNG able to block all outbound traffic except whitelistet sites?:
@RolandW It seems that you have the answer ... you claimed in your first post that you had a few IPs ... the correct action is to create aliases with the FEW IP addresses and then create LAN firewall rule to allow those and block all else. You really don't need pfBlockerNG.
I should only allow these domains:
*.larksuite.com
*.ibytedtos.com
*.byteoversea.com
*.larksuitecdn.com
and deny all the internet;
how do i configure pfBlockerNG DNSBL?Thanks
-
@xalex1977 See the post above yours! You don't need pfBlockerNG ... here is a starting idea (see image below), then create a firewall rule to allow/pass any protocol from LAN net to destination (my connection Alias) then add another firewall rule below the first blocking all other connections. Help yourself from this info.
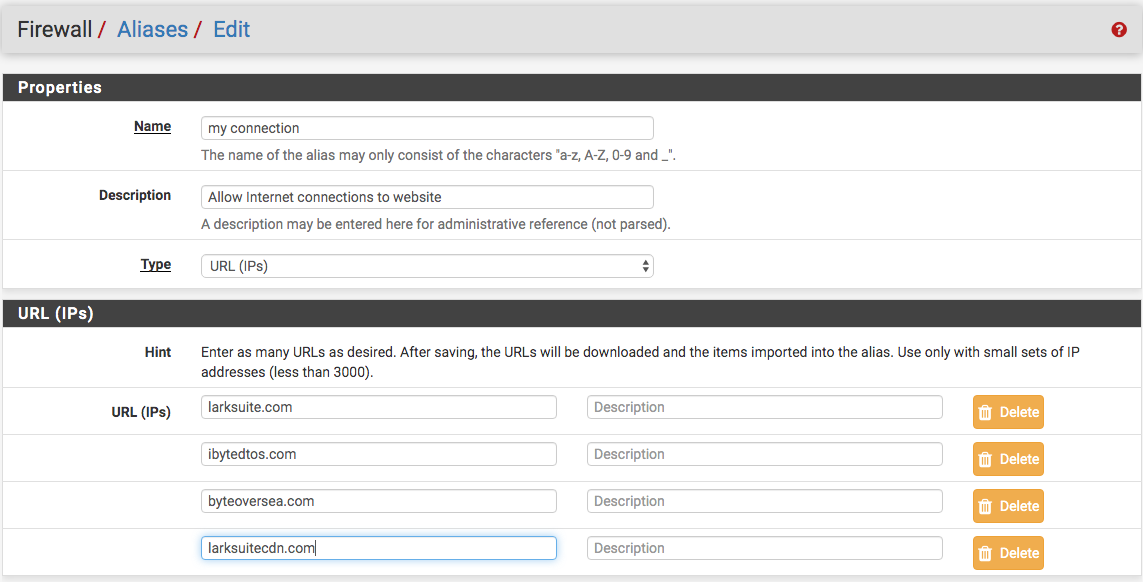
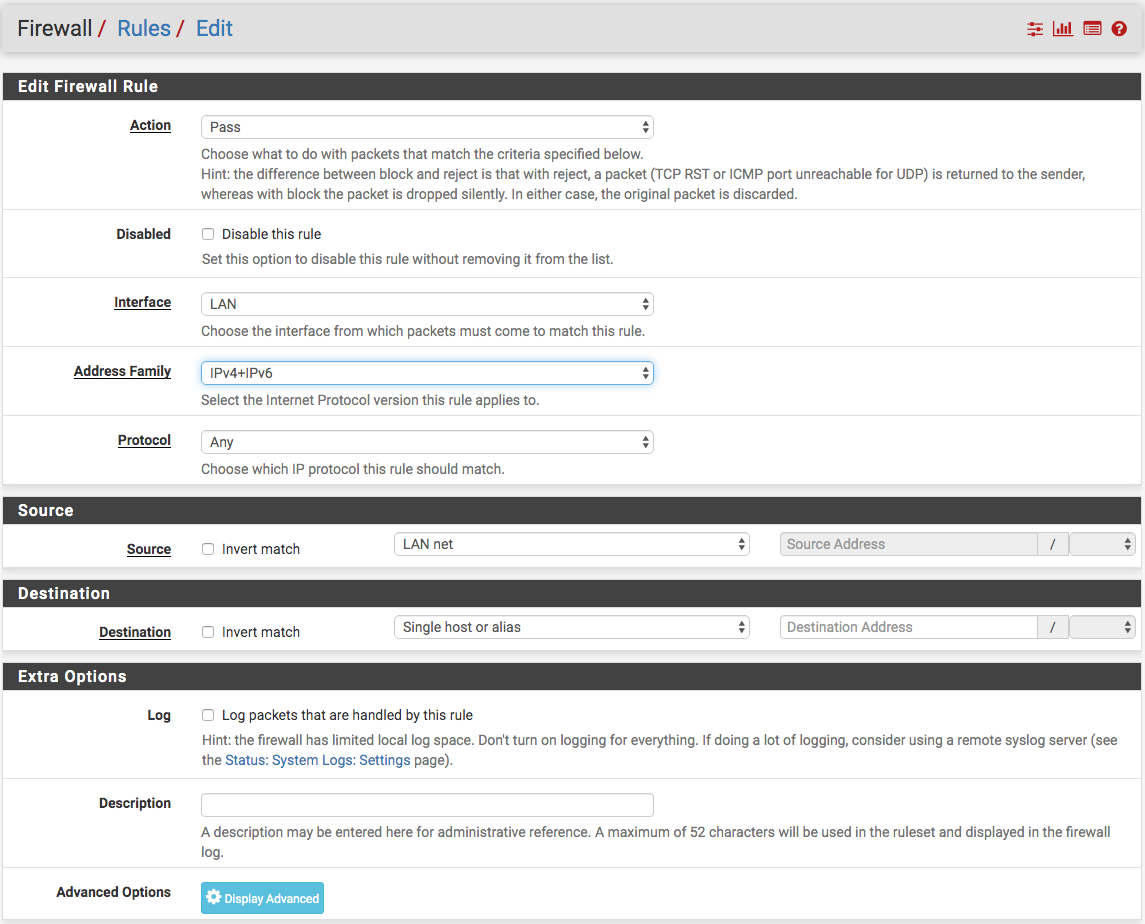
-
@NollipfSense but with these aliases can not unlock all subdomains or with the latest versions also work for subdomains?

-
@xalex1977 said in Is pfBlockerNG able to block all outbound traffic except whitelistet sites?:
@NollipfSense but with these aliases can not unlock all subdomains or with the latest versions also work for subdomains?

You won't need pfBlockerNG and not sure why you think it would not work for any subdomains ... remember, you could add up to 3,000 domains or subdomains to the alias my connection; so, stop rolling your eyes
-
@NollipfSense unfortunately from the software specifications I don't know the names of the subdomains and I think they change constantly, thanks for the help
-
@xalex1977 You should start your own thread.
-
You won't need pfBlockerNG and not sure why you think it would not work for any subdomains ... remember, you could add up to 3,000 domains or subdomains to the alias my connection; so, stop rolling your eyes
I have to bring this up again because I'm in a similar position:
I want to block all outbound traffic on 443 except a few whitelisted domains (teamviewer, windowsupdate).
I tried it with your approach of definining an alias with URLs but I'm always running into the problem that I can't whitelist every subdomain.
For example Windows update: there is a huge amount of subdomains that I would have to whitelist for Windows update to work... xxx.microsoftupdate.comCan I use pfblocker for this and blacklist all except a whitelist with domains (including subdomains)? For example, allow access on 443 to *.microsoft.com . To my knowledge, this isn't possible with firewall rules only.
-
@jhaeu90
I meanwhile figured out, how to do that: you need squid and squidguard. All http and https traffic (ports 80 & 443) then goes through squid/squidguard, the rest goes through the firewall.In squid enable "Transparent http Proxy" & "SSL filtering", "splice all" intercept interface "LAN".
In squidguard create a "target category", in the "Domain List" put in all domains, that should be allowed. Then, under "common ACL" open the "Target rules list", set your newly created list to allow, and for "default access (all)" -> deny. Thats it!
To allow Windows updates I figured out by trial and error that you need to allow a lot of domains (not only windowsupdate.com)
-
@jhaeu90 It might be easier to use firewall alias for all the sites you want to route via 443 and create a firewall .
-
@rolandw
Thank you, this solved it for me. -
G greenlight referenced this topic on
-
A abanet referenced this topic on
-
If Squid/LightSquid/SquidGuard becomes deprecated, I need some alternative to block everything except whitelist. Same solution as @RolandW wanted, i.e. whitelist domains using WILDCARDS like *microsoft.com to include subdomains.
Firewall rules can't be used for that, eventually @RolandW used squid and squidguard, but that's no longer an option.
So can this be done using pfBlockerNG? I have searched the forum for this but haven't found it. -
@CZvacko it’s been many years but long ago we had a client on a restricted Windows Server network (not pfSense). IIRC in Windows DNS Server we forwarded selected sites (so, domain override) to public DNS, and disabled using root servers which is a checkbox on Windows. So nothing else resolved. Maybe similar will work on pfSense?
-
@CZvacko I don’t think you can achieve exactly that with pfBlockerNG.
PfBlockerNG has a IP block feature that can be used both as a blocking and whitelisting option and that would be great to use - except you have no easy way to create the “positive” list with IP addresses of every subdomain.
PfBlockerNG also has a DNS Blacklist option with a wildcard subdomain blocking - which is exactly what you want if it could be turned around as whitelisting feature. But I as far as I can figure there is no way to do that because what it really does is make the DNS server resolve all those names as a local or 0.0.0.0 address rather than actually resolve them.
-
I've been going back and forth with TAC about this, since like @CZvacko, we need to have a replacement for SquidGuard when it is removed. For completeness, since I don't see it linked anywhere else in this thread, here are the firewall requirements for a local WSUS server in an isolated network. If you aren't' using a WSUS server and update directly from microsoft then the same requirements apply to workstations.
Also before anybody jumps in with Windows Update specific workarounds, this issue is not limited to Windows Update, it's just a good example use case. We have other applications with the same requirements, namely no access to the internet except for specific whitelisted URLs that may be wildcards and almost certainly point to a CDN. Both of which requiquirements preclude using the native pfsense firewall.
I have not set up a test environment to try this in yet and I have some reservations about it being a suitable replacement for a filtering forward proxy but this is TAC's recommended solution at this time:
Start reply from TAC support on 2023-11-29:
pfBlockerNG is not a supported package by TAC, so we cannot provide any assistance beyond best effort for it.
However, if you want to go the DNS-based filtering route, it's fairly straight forward:
- Create a rule allowing DNS traffic on ports 53 and 853 to the firewall and a deny rule for any other DNS destinations.
- Install pfBlockerNG and configure it to have a whitelist of the hostnames you want to allow. You can reuse the lists you have in squidGuard now and paste these hostnames with wildcards into the whitelist. Then simply deny all other DNS lookups besides the ones you wish to allow.
- Point your hosts at pfSense Plus for DNS lookups. Any hostnames not in the whitelist will return the IP of the firewall's block page for pfBlockerNG
You can also provide the ASNs for the various Microsoft IP blocks into pfBlockerNG, tell pfBlockerNG to use the "Alias" option, and then add firewall rules allowing and denying traffic like any other firewall rule using these ASN Aliases as the means of blocking or allowing traffic. Bear in mind that this will allow or deny all of Microsoft and not simply Windows Update, but if that is acceptable to you as a scope then it would work as well.
End reply from TAC support on 2023-11-29:
-
@AlternateShadow said in Is pfBlockerNG able to block all outbound traffic except whitelistet sites?:
DNS-based filtering route
I created a lab environment to see if such a solution is workable.
But since I have no experience with pfBlockerNG, I'm not sure if I'm going in the right direction. Step 1+3 seems clear, but step 2 does not.What I did: in IP - IPv4 I disabled default blocking category (since my logic is reversed - I'm bloking everything by default). Then I created new categories for allowed sites:
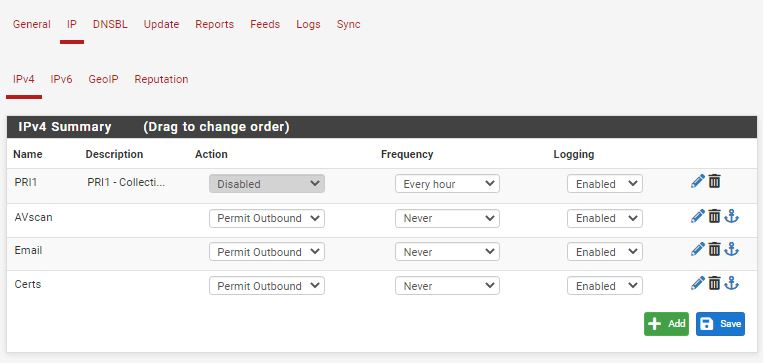
In each category I input related domains into IPv4 custom list (is this correct approach?)
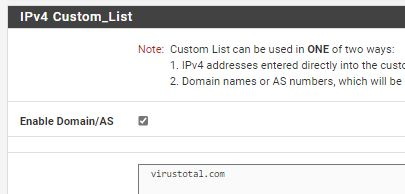
When I force update setting, it generate firewall rules
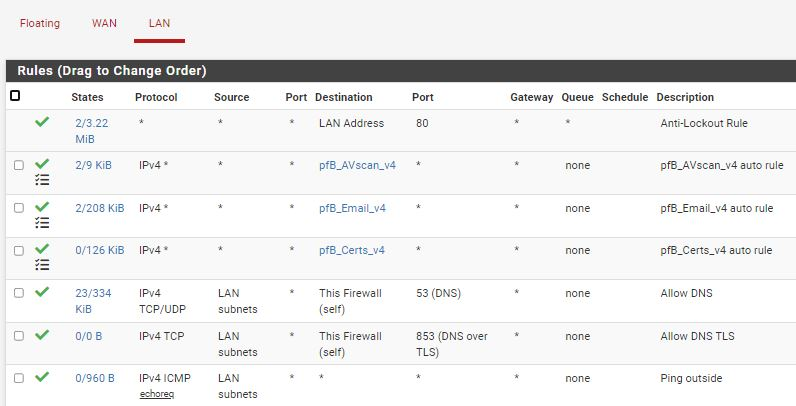
When try open related sites in webbrowser, not always they work. I thing issue is with IP based concept, for example: virustotal.com have different IP than www.virustotal.com (which in not allowed by FW).
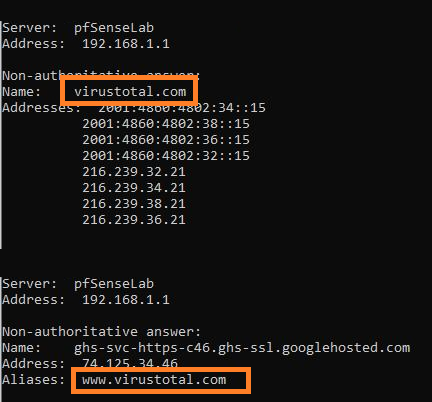
This is how step 2 should be performed ?
I also did some experiment under DNSBL - DNSBL Whilelist, but that didn't work at all :-(
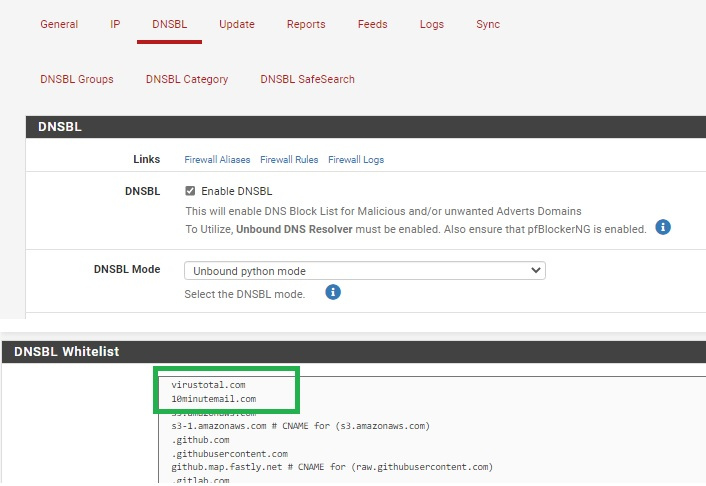
For example in Fortigate firewall is webfilter feature, where I can input wildcard and it allow website correctly.
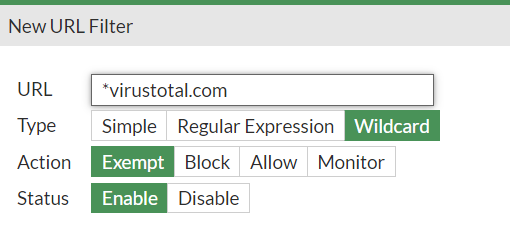
I'm looking for something similar in PFsense.