OpenVPN clients NATing to ipsec site-to-site
-
Hi all, i need help for resolve my problem with Routing and NAT OVPN clients to ipsec network
OpenVPN clent--->pfSense GTW (NAT by LAN IP of pfSense) ---> ipsecbut now if I traceroute to destination host in ipsec network, i get this:
OpenVPN clent--->pfSense GTW ---> WAN (NAT) ---> Internetpackages not route to ipsec networks and not NATed by pfSense LAN IP
LAN 192.168.55.0/24 pfSesne IP 192168.55.1 for LAN clients GTW
OVPN 172.16.200.0/24 pfSesne IP 172.16.200.1 for OVPN clients GTW
IPSEC 192.168.0.0/8 -
Hi,
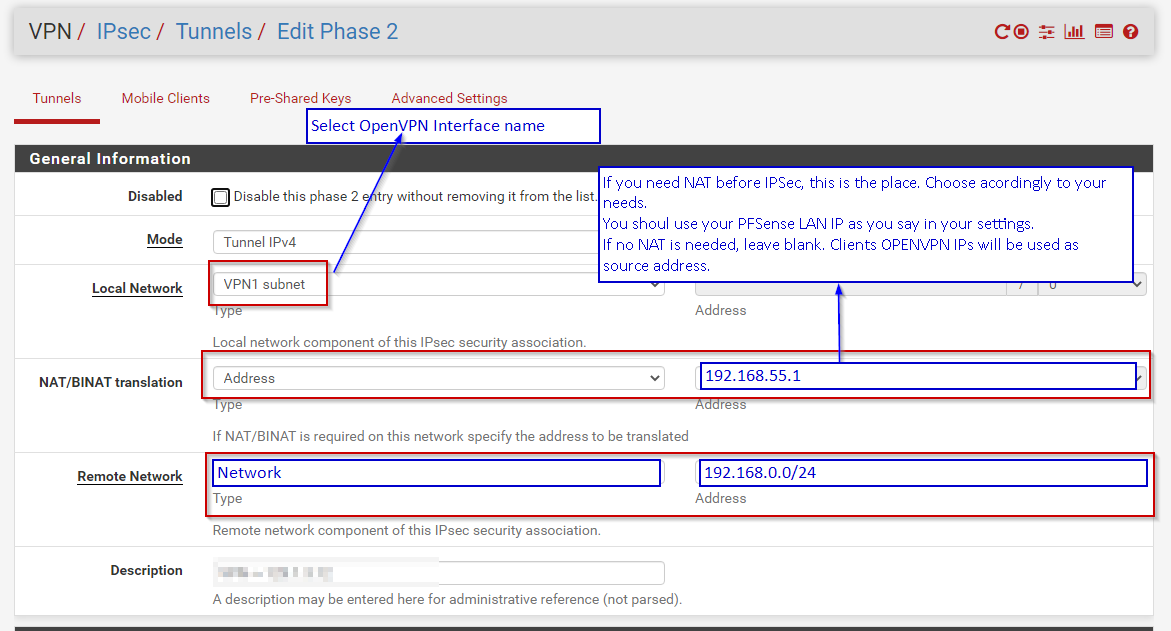
All the trick resides on Phase2 entries and Openvpn Remote networks setup.
Let's start on OPENVPN config.
You should configure OPENVPN Server Tunnel Settings like this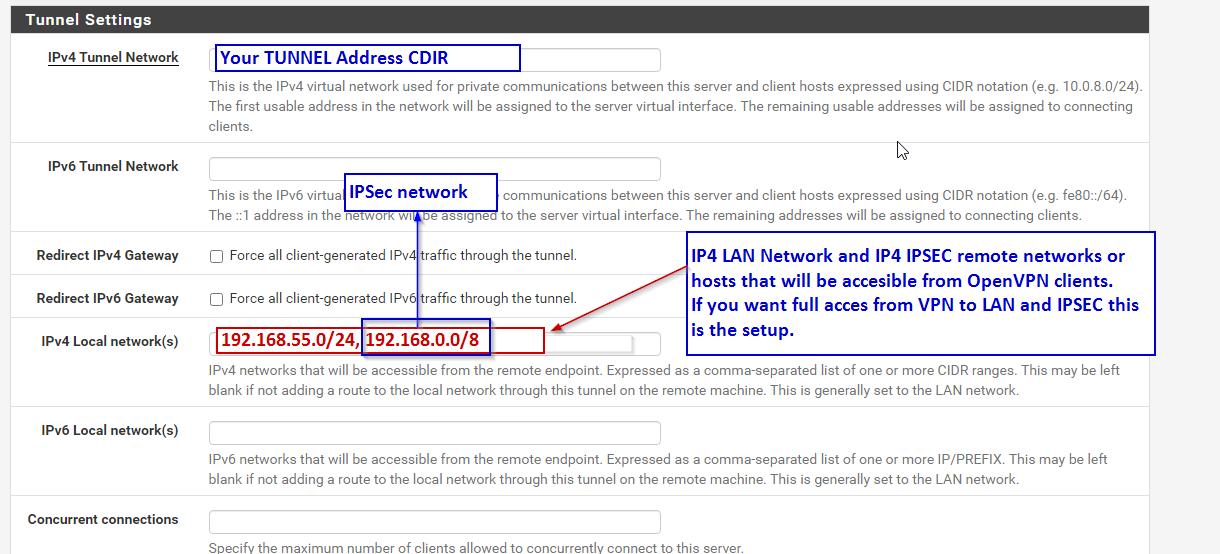
And now let's go for IPSec
I will assume Phase1 is connecting properly
You should add a new Phase 2 entry for injecting OPENVPN traffic from clients to IPSec remote network
The final picture will be something like this
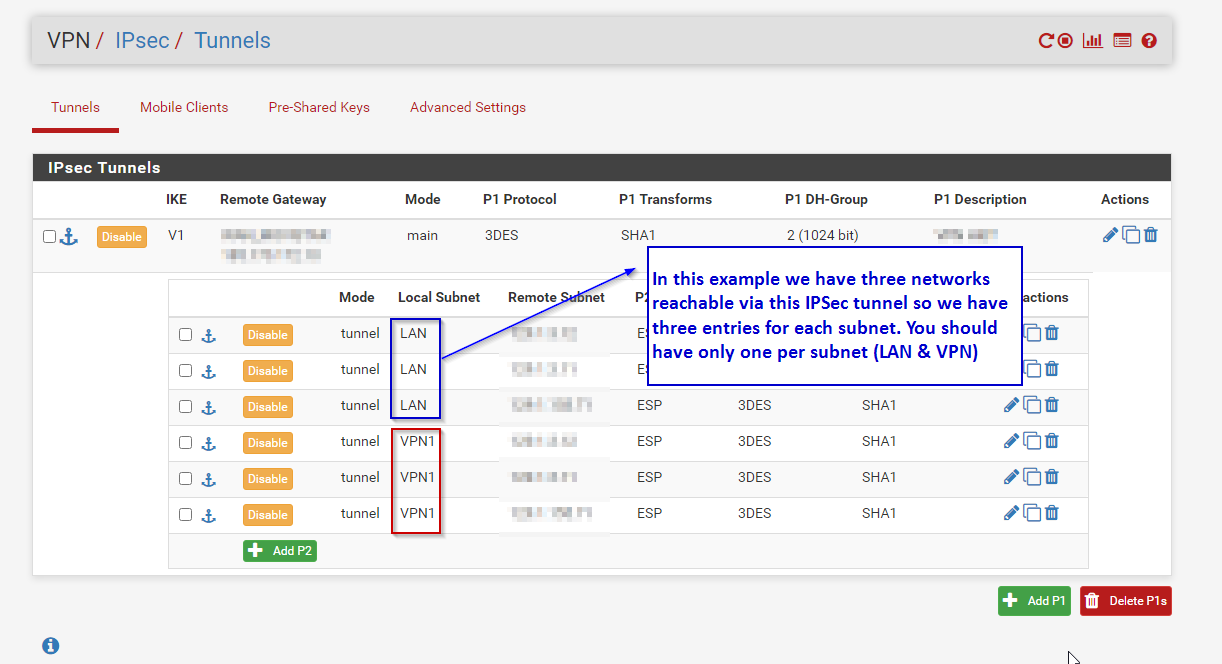
Just add a new P2 for IPSec traffic
And finally check Rules on OpenVPN and IPSec interfaces to let traffic flow
Here we have an example of what we have in a customer. There are restrictions of traffic getting through the tunnel to the IPSec remote network
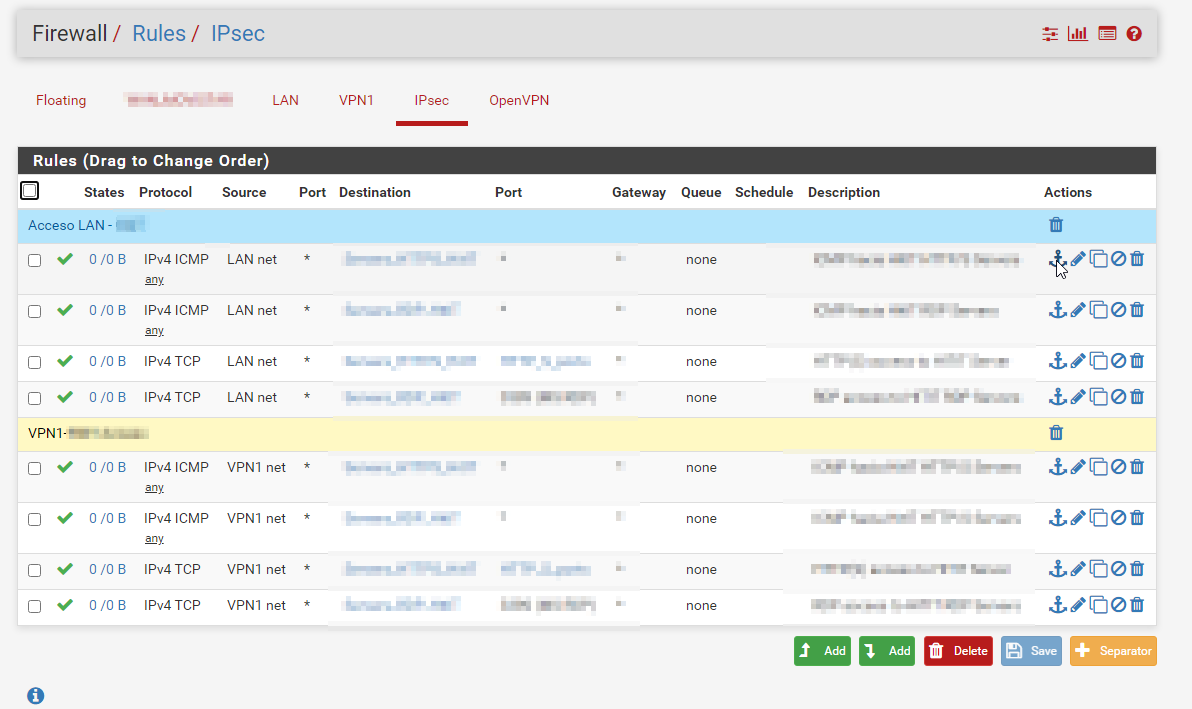
And we have full acces from OpenVPN clients
We have all NAT outbound set as default
When connected, in Status - IPSEC - Overview you should see something like this
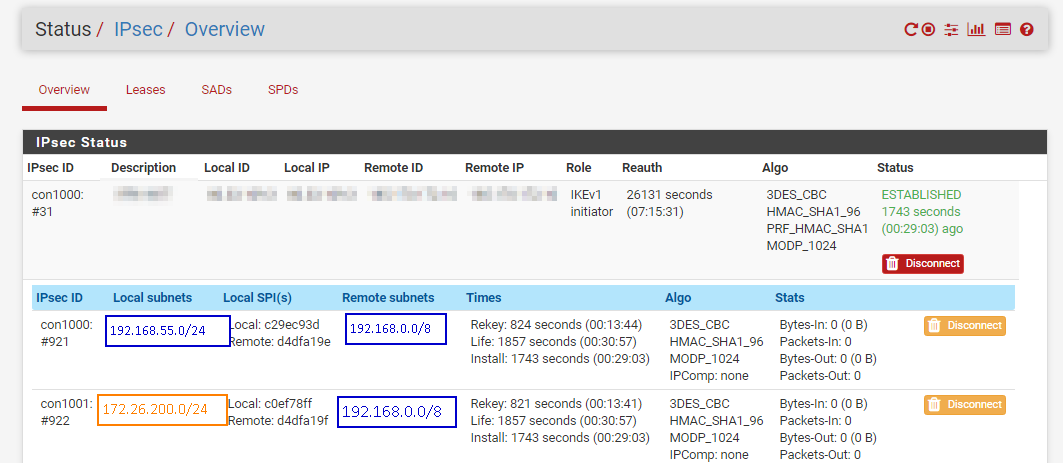
When testing connection, just send a ping from OPNVPN Subnet (you can use your pfsense OpenVPN box IP as source IP) and check on status if packets-out increases. If they do, you are injecting OpenVPN traffic through IPSec tunnel.
If there's no response, check other side firewall and settings.
We had a strong headache with a provider that did not set rules properly on their side.
But if there is increasing Packets-out count, you're sending the traffic properly.Also note that when doing traceroute from OpenVPN client subnet you will have a "strange" response.
It will be something like this in your case, assuming remote IPSec gateway public IP address is 203.0.113.10Traza a 192.168.0.15 sobre caminos de 30 saltos como máximo. 1 7 ms 6 ms 7 ms 172.26.200.1 {pfsense OpenVPN IP address) 2 79 ms 77 ms 77 ms 203.0.113.10 {IPSec remote gateway public IP)} 3 78 ms 78 ms 77 ms 192.168.0.15 {remote ip}That's correct and traffic is tunnelled inside IPSec.
Hope this helps.
-
This post is deleted!