Suricata IDS and IPS
-
@anx said in Suricata IDS and IPS:
@bmeeks Point 2. I do not need to put any info in Snort Rules Filename? thanks
Point 4. I will remove WAN completely from Suricata, however, if I will start to use Open VPN or any kind of VPN services on pfsense, should I enable it again ?I'm sorry, yes you do need to put in the Snort Rules filename. When I was writing my original reply I thought you were using Snort. The name of the required file is
snortrules-snapshot-29160.tar.gz.Also, since you are running Suricata, you will find a number of Snort rules that will throw errors and fail to load during startup. This is normal as Suricata does not understand all of the same rules syntax as Snort.
Unless you are really bent on using Suricata, I kind of suggest starting with Snort as the use of IPS Policy is a bit better there as no rules will fail to load. The packages have identical GUI setups.
-
@bmeeks Ok, thank you, But I read that suricata uses multithreading ?
-
@anx said in Suricata IDS and IPS:
@bmeeks Ok, thank you, But I read that suricata uses multithreading ?
Yes, but it has no practical effect on performance unless you are pushing more than 1 Gigabits/second sustained traffic. No home user ever does that, and neither do most Small Offices.
There are portions of the Suricata detection model where traffic still gets funneled through a bottleneck. Lots of tests have been done between Snort and Suricata with realworld traffic, and the results are mostly a toss-up in terms of which is faster.
-
@bmeeks this is fantastic information. I will remove Suricata and install Snort . 1Gb not a chance here :)
-
It seems that there is an issue with Server ?
The process will require 80 MiB more space.
2 MiB to be downloaded.
[1/4] Fetching pfSense-pkg-snort-3.2.9.11.txz: .......... done
[2/4] Fetching snort-2.9.16.txz: . done
pkg-static: https://pkg.pfsense.org/pfSense_v2_4_5_amd64-pfSense_v2_4_5/All/snort-2.9.16.txz: Operation timed out
Failed -
@anx said in Suricata IDS and IPS:
It seems that there is an issue with Server ?
The process will require 80 MiB more space.
2 MiB to be downloaded.
[1/4] Fetching pfSense-pkg-snort-3.2.9.11.txz: .......... done
[2/4] Fetching snort-2.9.16.txz: . done
pkg-static: https://pkg.pfsense.org/pfSense_v2_4_5_amd64-pfSense_v2_4_5/All/snort-2.9.16.txz: Operation timed out
FailedYes, it does seem to be an issue with the package repo server. Give it a few minutes and retry.
-
@bmeeks I don’t like to write (cringe text) therefore I only need to tell how good other person is
your style is frenetic, especially as you steer the beginner OP onto the right way
maybe you also worked as a teacher at some point? -
@DaddyGo said in Suricata IDS and IPS:
etic, especially as you steer the beginner OP onto the right way
maybe you also worked as a teacher at some point?It's true, it's very rare to find such an approach to other people
-
I told you to listen to him and follow (I also learned many - many new things from IPS / IDS from his descriptions and from him "jflsakfja", but unfortunately he is no longer with us
in this confusing world such a mentality, huhuhuh .... rare
you are also a good guy, others right away they are demanding and think they "shiting" out IT
-
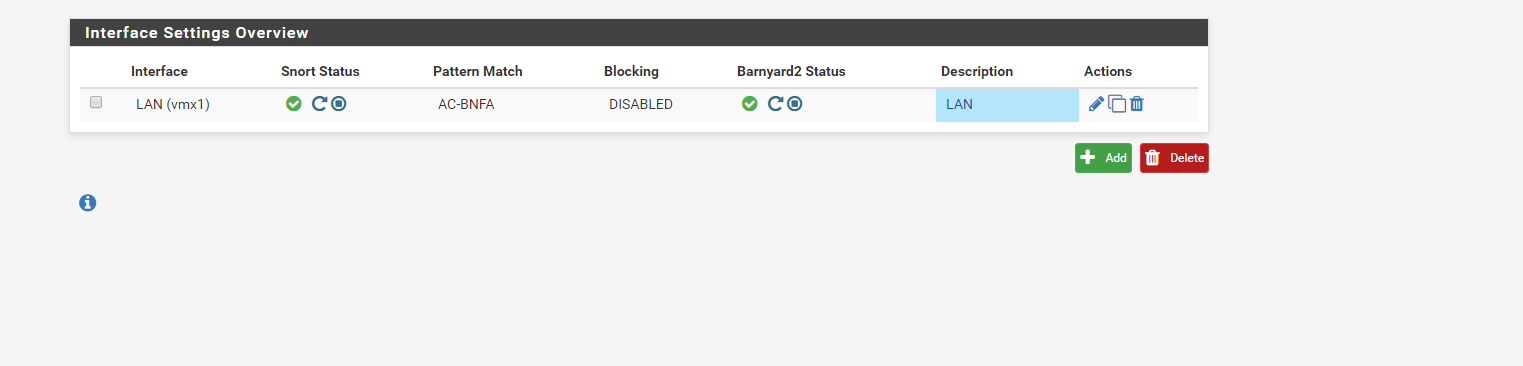
I enabled the IPS Policy to check it. However, still is showing that the blocking is disabled on LAN.
am I doing something wrong? thanks
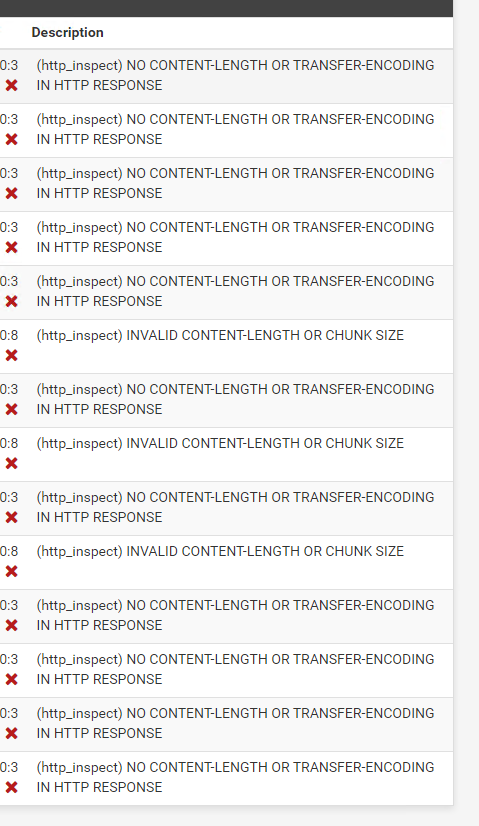
Also, noticed that only these alerts I can see.
-
@DaddyGo said in Suricata IDS and IPS:
@bmeeks I don’t like to write (cringe text) therefore I only need to tell how good other person is
your style is frenetic, especially as you steer the beginner OP onto the right way
maybe you also worked as a teacher at some point?In fact I was a technical instructor for a number of years in my career. I first worked on, and then later taught others how to work on, nuclear power plant control systems. Later I moved over to the Information Technology side of things and worked in cyber security for a number of years before retiring early to enjoy life before I get too old to do so ...
 .
. -
@anx said in Suricata IDS and IPS:
I enabled the IPS Policy to check it. However, still is showing that the blocking is disabled on LAN.
am I doing something wrong? thanks

Also, noticed that only these alerts I can see.

Enabling a policy will not automatically turn on blocking in either Suricata or Snort. For Snort, you will need to manually enable blocking on the INTERFACE SETTINGS page for the interface. If I recall the setting is called Block Offenders. However, don't rush to enable that until you learn more about tuning your rules.
Those HTTP_INSPECT alerts are the false positives I was talking about. There are several of those rules which alert these days on web traffic that is actually not malicious. Look through those alerts and click the red X beside the GID:SID (Generator ID and Signature ID) column on the ALERTS tab to disable those false positive rules. I personally have a number of those rules disabled in my setup.
Here is a link to an older and long thread with posts from various users showing which rules they enable and disable and why: https://forum.netgate.com/topic/50708/suricata-snort-master-sid-disablesid-conf. It's a good place to start learning about alert suppression and rule disabling.
-
Hi guys,
How to check if actually IDS is working? I have installed PfBlockerNG to block Adds only.
Since then, I dont see any IDS alerts. Hmm
-
Hi,
if you have the ability to run a KaliLinux virtual machine (or nativ), you will find all the tools for the different tests.
I hope you meant pfBlockerNG -devel -
@DaddyGo said in Suricata IDS and IPS:
pfBlockerNG -devel
Yes, Devel version.
Ok, will try with Kali. thanks
-
@anx said in Suricata IDS and IPS:
@DaddyGo said in Suricata IDS and IPS:
pfBlockerNG -devel
Yes, Devel version.
Ok, will try with Kali. thanks
If you have put Snort or Suricata on your LAN, you will need to direct your Kali machine towards that interface.
With a properly tuned IDS you actually don't want to see any alerts as a normal thing. A few alerts now and then is what you would expect. For example, on my LAN my most recent Snort alerts are from April 30th of this year. And those were two HTTP_INSPECT preprocessor rules that mine and my wife's iPhones triggered. I run the IPS Balanced policy on my LAN along with a handful of the ET Open categories.
Because I frequently need data to test with, I also run a Snort instance on my WAN and use a pair of ET Open "known bad IP address" categories enabled there purely to generate alerts for research. I run the Emerging CIARMY and Emerging DSHIELD categories on my WAN to generate that testing data. These two categories are actually just lists of IP addresses from known bad actors. They generate several hundred alerts per day on my WAN from the random Internet "noise" that is always there due to bots scanning for open ports and such.
-
Hi Guys
Is there any way that when the pfBlockerNG -devel will block website, will actually block it with some information that is blocked by it? Instead that SSL is invalid? thanks
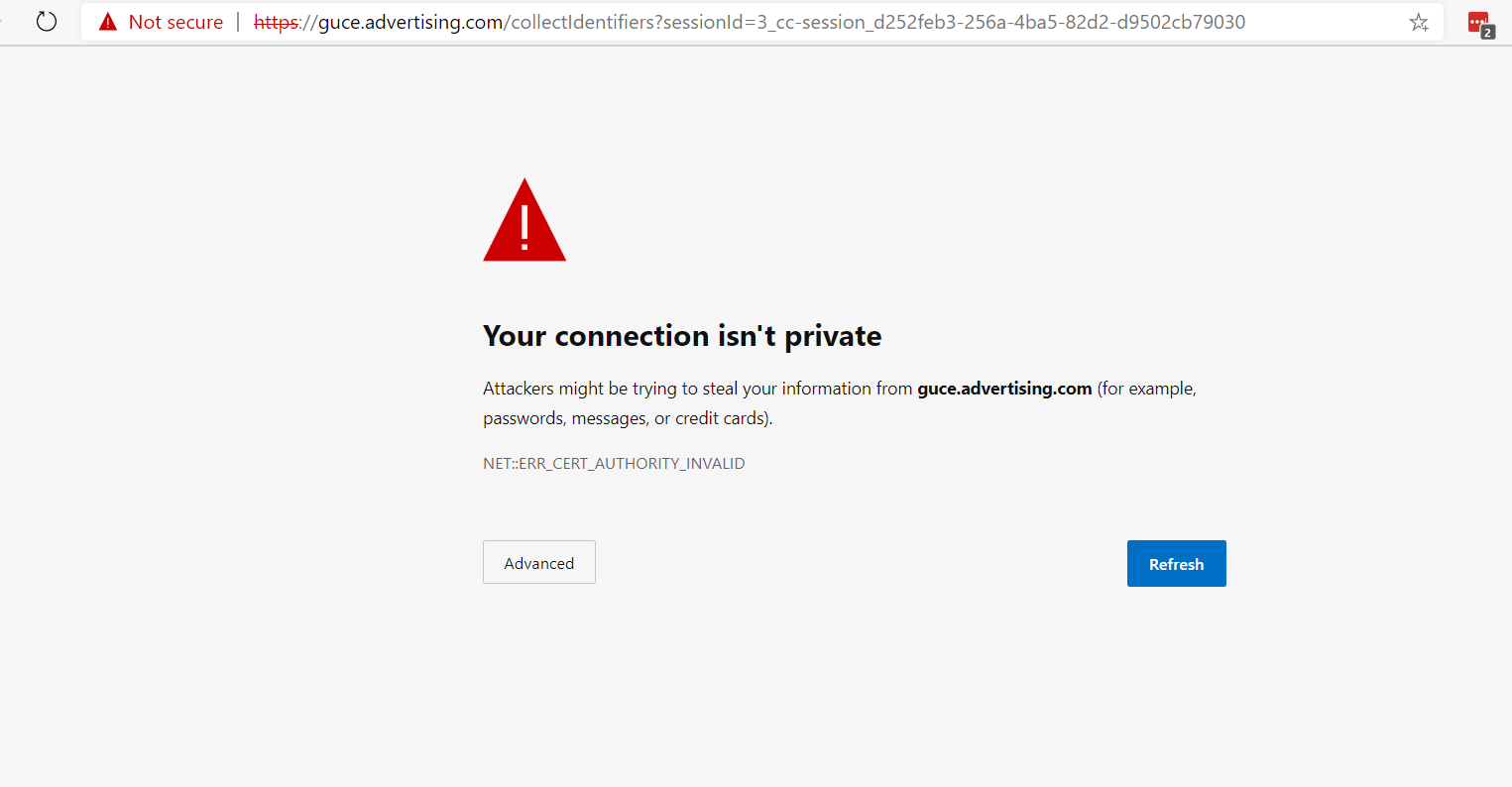
-
@anx said in Suricata IDS and IPS:
Hi Guys
Is there any way that when the pfBlockerNG -devel will block website, will actually block it with some information that is blocked by it? Instead that SSL is invalid? thanksIt is included in the name of "advertising"
have you activated the AD block list?SSL:
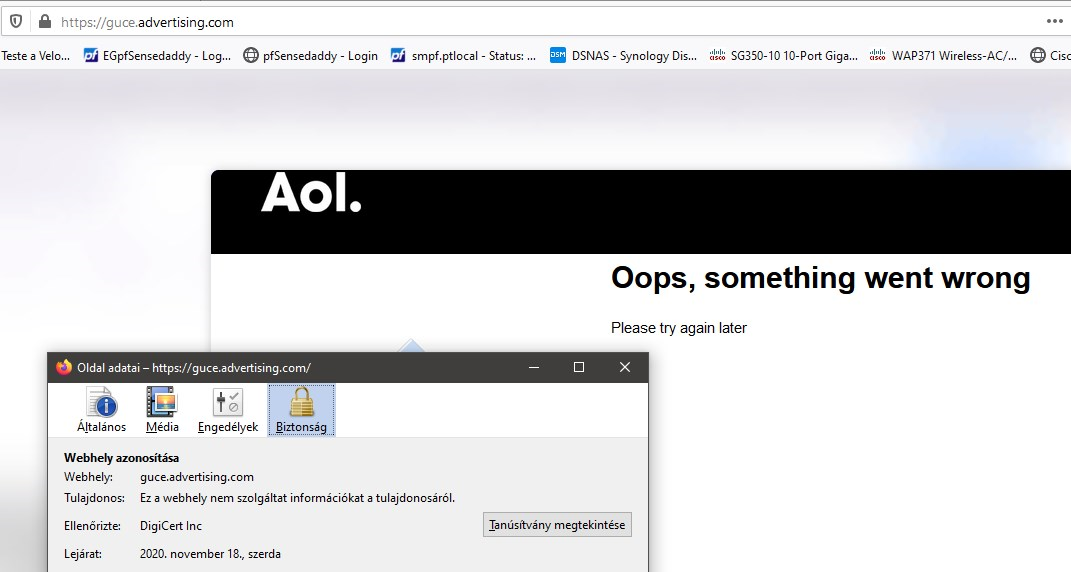
-
@anx said in Suricata IDS and IPS:
Hi Guys
Is there any way that when the pfBlockerNG -devel will block website, will actually block it with some information that is blocked by it? Instead that SSL is invalid? thanks

You will get more responses and better answers to pfBlockerNG questions by posting your question over in the pfBlockerNG forum here: https://forum.netgate.com/category/62/pfblockerng.
-
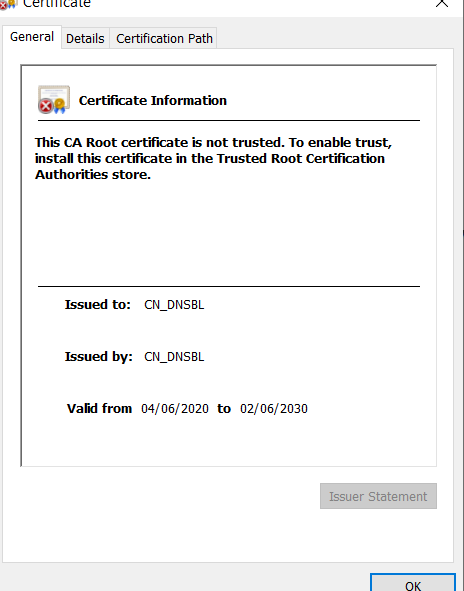
Yes, and i am happy to block it. But rather to have ssl invalid would be nice to have information that the pfBlockerNG blocked ad . I See that the blocker replaced the cert ?