Trying to block all but Windows Updates for Servers
-
Hi,
I am trying to block my servers from Internet access except for Window Updates and Antivirus updates.I got the list of dns that needs to be allowed.
I created a Aliase for them:
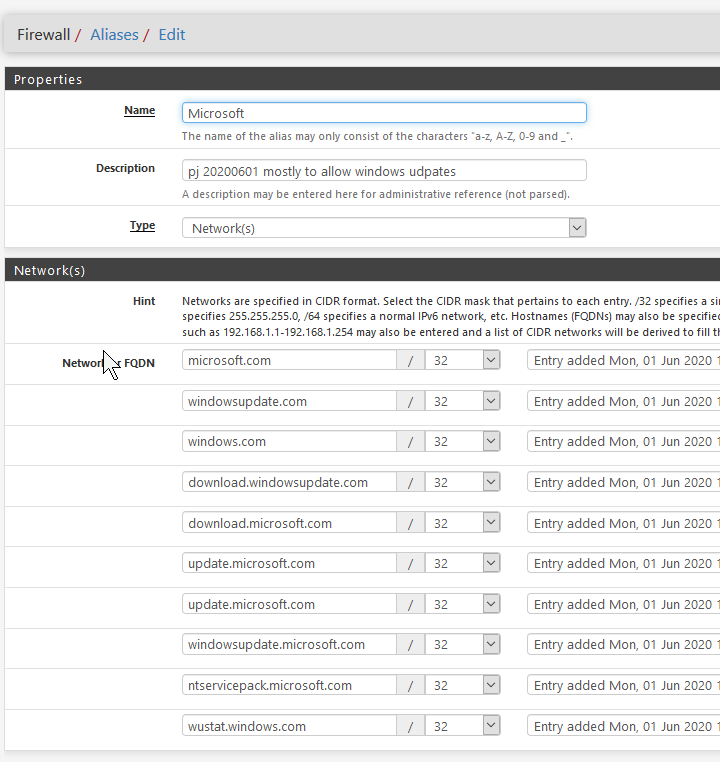
And created 2 rules to allow Microsoft and CrowdStrike (we do see packets on them)
And 2 rules to block all the rest
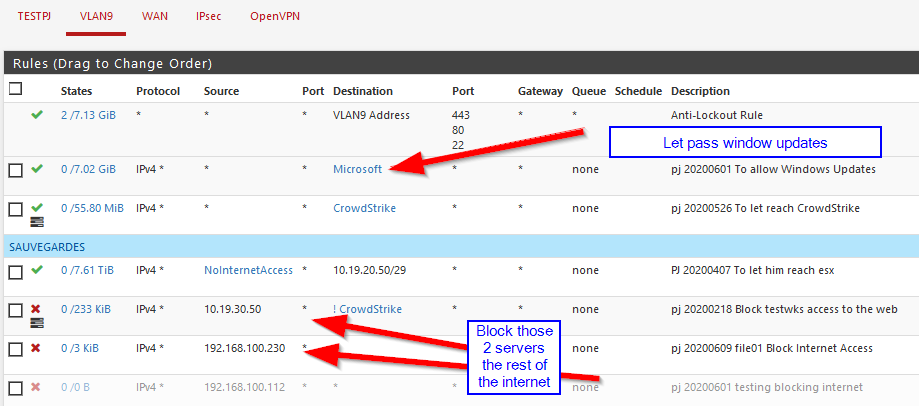
But updates are still failing.
Anyone have a clue?
tx -
@PhilJans
Hi,
why don't you use pfBlockerNG-devel? -
What about it?
-
just an idea
there are complete microsoft domain and antivirus developer lists for pfBlockerNG + GeoIP IPv4, IPv6 block
what, if you use it the other way around?microsoft is full of other telemetry, if you also block them with the internet, you may not get updates the way you want
-
@DaddyGo Interesting.
Right now it does not work, need to fix the plugin, but once it's done, I'll look for this.
Thanks for the info -
I am even thinking here, for example, of the Akamai CDN
the biggest supplier of win update stuffWindows_telemetry_bl.txt
Windows_telemetry_bl_2.txt
Windows_telemetry_bl_3.txt -
I try to do the same kind of things, because the risk / unwanted things are often not coming from the internet, but they are starting at your own computer / tv, etc.
However it is almost a disaster. Because:
- you not really know which FQDN Microsoft is using for what
- it is changing
- it is not a single server, but a cloud service
- if you are using IPV6 it is even a bigger issue, since you cannot filter on source IP, because you do not know the (changing) IPV6-source IP.
What I sometimes do is a combination of IPV4-source IP with an alias with FQDN's.
And / or I override the domain in my DNS sending the IP to just "NoWhere"But I agree with @DaddyGo that pfBlockerNG is perhaps in this case the easiest option.
Louis
-
Privacy comes first and this is not respected by many manufacturers (such is the world today).
Therefore we must act.BTW:
"Thanks for your comment, but not relevant, they are just extract of the lists and they are constantly updated.Windows_telemetry_bl.txt
Windows_telemetry_bl_2.txt
Windows_telemetry_bl_3.txtLike:
https://raw.githubusercontent.com/wlqY8gkVb9w1Ck5MVD4lBre9nWJez8/W10TelemetryBlocklist/master/W10TelemetryBlocklisthttps://raw.githubusercontent.com/WindowsLies/BlockWindows/master/hostslist
(but I don’t want to give tips, let everyone work out for knowledge)
Not to mention that the original issue of the OP it wasn't that and you can see my name next to the

-
You may simply not have been paying attention when you created these, but those aliases are for IPs, yet you've added URLs, you therefore need to change type from network to URL and re-add them.
Each type does give you a description below in the hint field
FYI if you add microsoft.com you dont also need to add it's subdomains, so update.microosft.com will also be allowed based on microsoft.com being allowed at the lower level.
The first 3 in your URLs cover all the others below.You may be better with Squid or PfBlockerNG though as noted above and block specific domains, even if you only use PFBlockerNG for custom domains on a whitelist.
-
Then once again for the sake of those who don’t pay attention (DNSBL!!!)

I didn't make the lists, these are ready lists.everyone uses or does not use them to their own taste
-
More problems nearby ....
Encrypted DNS, very necessary to protect against governments like “China” (and a lot others), are coming. But of course one big disadvantage ….. DNS-based blocking options ….. will be gone …
So lets enjoy the moment ..
Louis
-
exactly....
The biggest bullshit in the world is the DoH, and many more experts will have a say.
The current best solution, option:
Unbound + pfBlockerNG + DoT + DNSSEC + CF DNSThis should not be a matter of debate at this time.
And don't forget we raised it high (China), because we're stupid and we manufactured in everything with them, hahaha "Know - how" - "privacy", etc.
https://en.wikipedia.org/wiki/Know-howBTW:
+++edit:
and now we are crying that china is approaching - we are like that and ready -
Sorry, I am fully aware of DNSBL and suggested this as an option as well as squid, but I also answered the OPs question directly, their rules wont work with URLS under and IP field.
This does not need to be an argument or a push in the direction you would prefer to OP to go, so i therefore answered their specific question.
I'm not saying there aren't better ways to do what they want, but their question was why doesn't their rules work and it's because they have URLs in an IP field
-

