OpenVPN routing issue with LAN
-
I'm wondering now since my VPN clients are in a gateway group does that affect how these rules work?
I tried adding NAT rules as is described here but that does not make a difference.
I feel like I'm losing my mind. I've tried so many things and nothing seems to work...
-
OK I've gotten this more condensed I think,
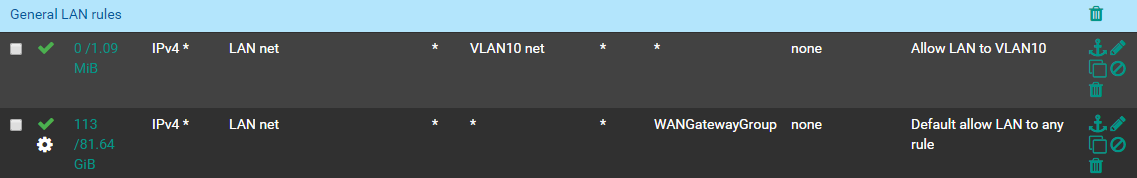
- VLAN clients that are using the VPN client tunnel can ping LAN/VLAN/VPN clients.
- LAN clients NOT USING the VPN client tunnel can ping LAN/VLAN/VPN clients.
- LAN clients USING the VPN client tunnel CANNOT ping VLAN clients using the VPN client tunnel.
So everything is almost working the way I need it to. Just need to sort out no. 3.
-
-
@JohnKap said in OpenVPN routing issue with LAN:

is this option set?
These are OpenVPN clients. I don't see that option under clients, only under the OpenVPN server section.
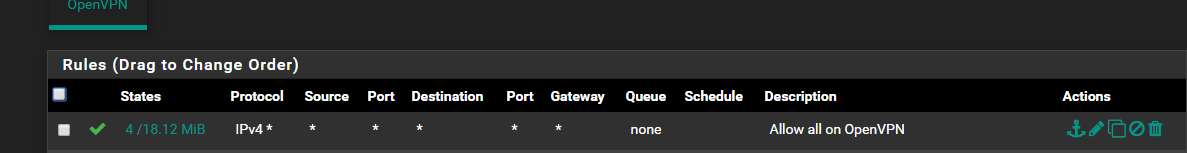
My issue is with LAN devices that are pushed through the OpenVPN client tunnel not being about to ping VLAN clients using the VPN client tunnel.
It's the last piece of the puzzle. I will further lock things down with the VLAN but I wanted to get everything communicating properly first.
-
Traceroute to a box on the VLAN from LAN device using the OpenVPN client tunnel on pfSense:
traceroute to 192.168.20.2 (192.168.20.2), 30 hops max, 60 byte packets
1 10.15.0.1 (10.15.0.1) 51.183 ms 51.160 ms 52.507 ms
2 {EXTERNAL_VPN_IP} (EXTERNAL_VPN_IP) 53.454 ms 53.635 ms 54.852 msSo it looks like it does not recognize the IP as being local?
EDIT: from pfSense admin I can ping any device from any source and it works. So it's just the the clients can't seem to find the correct route.
-
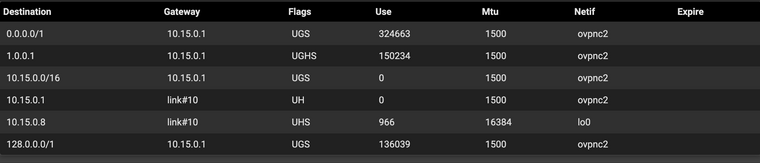
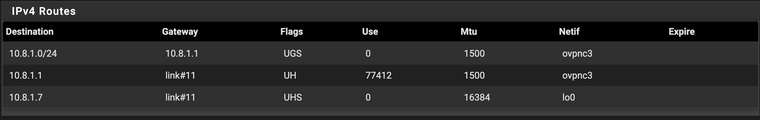
Can you have a look at diagnostics / routes. I'm guessing each client that connects gets a /32 and there is no route between the clients.
-
@JohnKap said in OpenVPN routing issue with LAN:
Can you have a look at diagnostics / routes. I'm guessing each client that connects gets a /32 and there is no route between the clients.
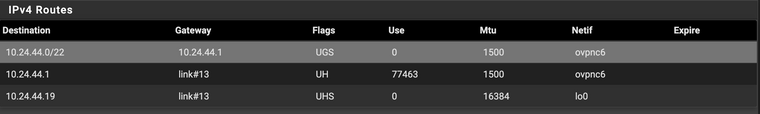
These are the local routes for the OpenVPN clients:
10.15.0.0/16
10.8.1.0/24
10.24.44.0/22External all have IP_ADDRESS/32
I'm learning as I go. Does this have significance to my situation?
-
I discovered I can ping the VLAN gateway IP from a LAN device using the VPN tunnel just not anything else on the VLAN.
ALL devices on the VLAN are forced through the VPN tunnel. It seems like they should all be able to talk to each other since they are all on the same VPN subnet even though they are on different actual subnets.
-
I dug into this a bt further today and found this article: Bypassing Policy Routing
Now it all works! I guess I can add stricter rules per VLAN now as needed?
-
tun mode.
Under OpenVPN, Client Export Utility, Advanced, Additional Configuration Options, add a line as such:
push "route 192.168.10.0 255.255.255.0"
,where 192.168.10.0 is the network you want to allow clients access..
-
@bjk002 said in OpenVPN routing issue with LAN:
tun mode.
Under OpenVPN, Client Export Utility, Advanced, Additional Configuration Options, add a line as such:
push "route 192.168.10.0 255.255.255.0"
,where 192.168.10.0 is the network you want to allow clients access..
Apologies if I used improper terminology but this was actually LAN hosts that were routed through the OpenVPN Client tunnel could not connect to other devices on the VLAN/LAN. My solution is posted above :)