Firefox users and DOH
-
@Cool_Corona That's the old version ... you need to upgrade to pfBlockerNG-devel.
-
@NollipfSense said in Firefox users and DOH:
@Cool_Corona That's the old version ... you need to upgrade to pfBlockerNG-devel.
But if one doesnt want to run development versions ??
-
No problem at all.
And you're right : doing it the manual way, collecting all the related host/domain names, adding them manually to the system 'hosts' file (be needing 2.5.0 to do this ... oops) or better: use the Custom Options on the unbound page, like building and maintaining your own llist (feed).Several forum pages already spook about doing just this, before @BBcan177 implemented it.
As other forum pages states that the pfBlockerNG (old) is to be abandonedly, and them he's - the authot - is using the new one for close to two years now.
Pretty solid package, with new features, quick follow up in case of issues, etc.But serious : what is your motif to stay with the ancient one ?
You're not using 2.4.5-p1 ? -
@Gertjan said in Firefox users and DOH:
No problem at all.
And you're right : doing it the manual way, collecting all the related host/domain names, adding them manually to the system 'hosts' file (be needing 2.5.0 to do this ... oops) or better: use the Custom Options on the unbound page, like building and maintaining your own llist (feed).Several forum pages already spook about doing just this, before @BBcan177 implemented it.
As other forum pages states that the pfBlockerNG (old) is to be abandonedly, and them he's - the authot - is using the new one for close to two years now.
Pretty solid package, with new features, quick follow up in case of issues, etc.But serious : what is your motif to stay with the ancient one ?
You're not using 2.4.5-p1 ?I am using 2.4.5p1 but not using dev. packages.
If its production ready then I suggest the package maintainer will let us know if it is so we can exchange them....
-
or DNSBL
https://heuristicsecurity.com/dohservers.txt+++it may not be complete and can be bypassed, but it can be a good start
-
the use of dev package in the case of pfBlockerNG, especially the package maintainer (@BBcan177) he referred to it countless times !!!!!!!
-
@DaddyGo said in Firefox users and DOH:
the use of dev package in the case of pfBlockerNG, especially the package maintainer (@BBcan177) he referred to it countless times !!!!!!!
I am fairly new here, so I dont know who bbcan is?
If the package is supposed to be used instead of the "old" one, then I suggest to remove it completely from the packages list.
-
BBcan177 = maintainer of the pfBlockerNG and just feel free to use the devel version
the old package (no devel), as far as I know it is only maintained to a very small extentwhat he keeps and what he removes i.e. his decision and Netgate's

-
@Cool_Corona said in Firefox users and DOH:
who bbcan is?
The forum who-is-who : https://forum.netgate.com/users and check the 3 tabs.
Big number of pfBlockerNG youtube videos - and an official Netgate's pfBlockerNG video will do for the introduction.Not a Netgate employee, just another guy who had that smart idea to write a package for pfSense. It became popular.
@Cool_Corona said in Firefox users and DOH:
If the package is supposed to be used instead of the "old" one, then I suggest to remove it completely from the packages list.
It's his baby, so he decides;
"devel" means probably that he is actively developing it.
Which is the case. -
So I do run devel, I do have that option enabled. I am not sure how to test it as the default DOH in Firefox tries to test first if it can use DOH and if it can't it just keeps using DNS. I am not getting any errors. I want the errors as it could indicate a compromised host.
Do you know what the "Firefox DoH blocking" does? I understand if you use Snort/Suricata you can identify by a traffic pattern that the https is a rapid DNS result and not a large MTU payload of data, but that takes time and some intelligence.
DoH reminds me of when skype was blocked in business so the users or authors of skype just made it look like web traffic. Hell if that is ok, then they should just put the whole Internet on 80/443. :-)
Thanks,
Joe -
You should for sure setup the canary as well for this doh nonsense!!
https://support.mozilla.org/en-US/kb/canary-domain-use-application-dnsnet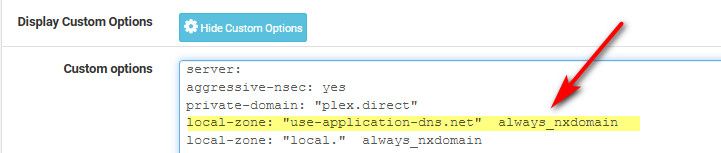
$ dig use-application-dns.net ; <<>> DiG 9.16.3 <<>> use-application-dns.net ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NXDOMAIN, id: 45559 ;; flags: qr rd ra; QUERY: 1, ANSWER: 0, AUTHORITY: 0, ADDITIONAL: 1 ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 4096 ;; QUESTION SECTION: ;use-application-dns.net. IN A ;; Query time: 3 msec ;; SERVER: 192.168.3.10#53(192.168.3.10) ;; WHEN: Fri Jun 12 06:42:50 Central Daylight Time 2020 ;; MSG SIZE rcvd: 52 -
On any LAN would the DNS admin be able to just make all domains canary so that DNS traffic is visible for the FireFox application? The issue is that custom malware will not look for the canary and just do DoH....
Thanks,
Joe -
Yeah that only works for firefox.. But I would put in all possible methods to block the nonsense that is doh..
I have that setup, I have firefox config setup to not use it, and I use a block list of known doh domains and block those.. Security and privacy my ASS.. It is just another way to monetize users.. It sure and the F is not about user privacy..
It is a slap in the face to all local controls - They are saying F you admins, we don't give 2 shits about your local controls - we want the user data, so we will let them send it to us directly! And good luck stopping us - we will just do it so it looks like normal web traffic..