Question on HAProxy, VIPs, DHCP, and Firewall Rules
-
Hi PiBa,
LastChk is blank. Not sure if it matters, but I do not have health checks enabled on any backend.
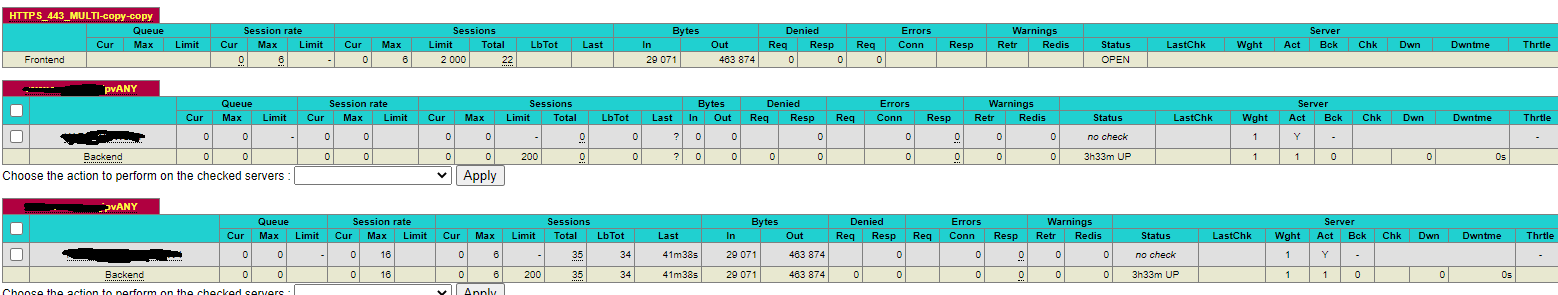
-
@bjk002
Enabling http health-checks could help determine if haproxy is able to properly connect, negotiate ssl, and send a http request. And tell on which of those steps its possibly failing. -
OK.
Here is the full list of backends and frontend stats, with blackouts for identifying info.
Every backend defined with red status in below image is an HTTPS connection. Those in green are HTTP.
Some of those red status backends (the actual servers) are listening on both HTTP and HTTPS ports (80 / 443). I can flip the backend from HTTPS port to HTTP port and everything works (enabling/disabling SSL check as appropriate).
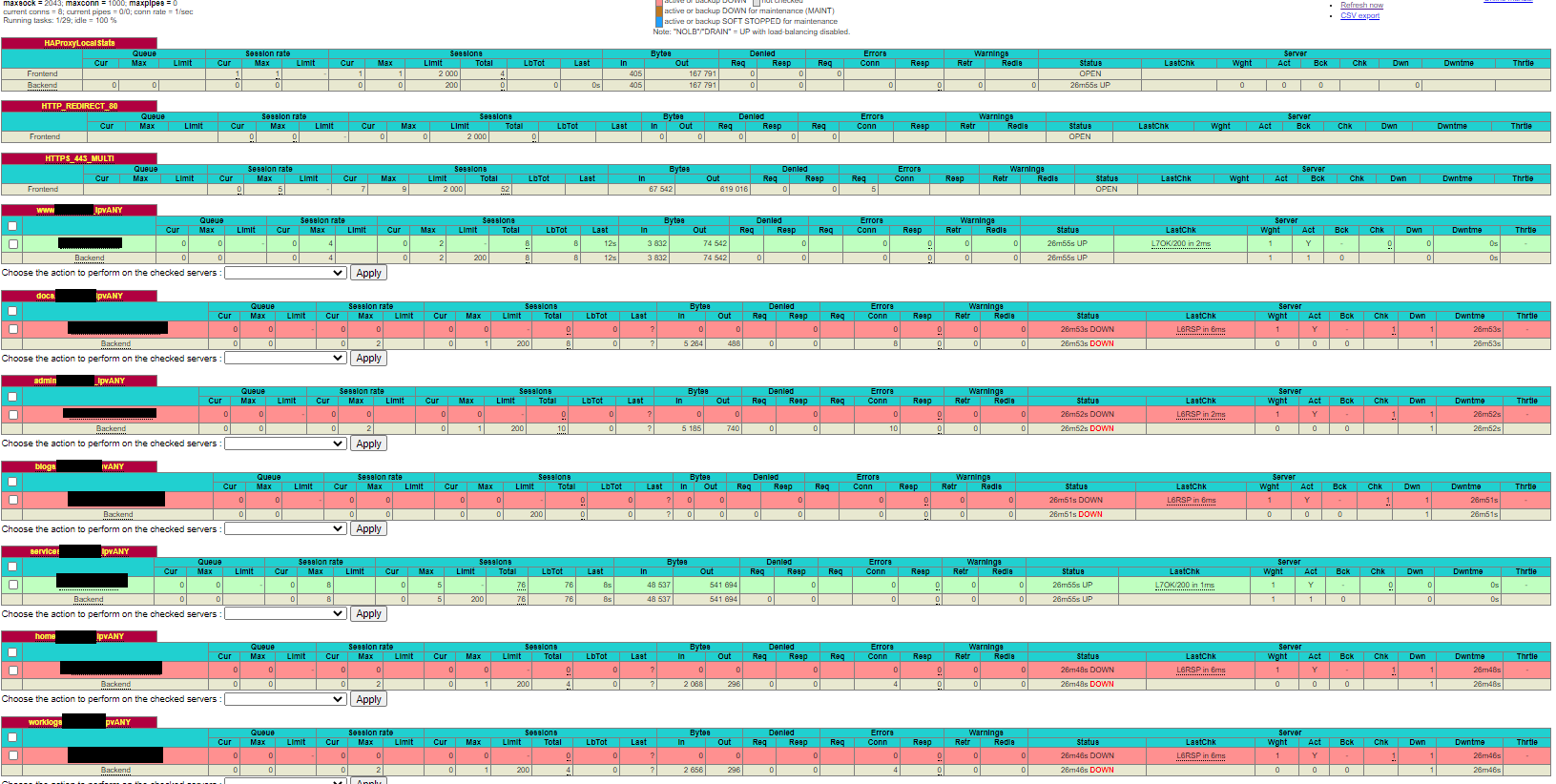
So I am at a loss...
I've got to believe this is some problem in my firewall rules, but I just do not see it.
-
to prove the point, I flipped the "docs" backend to HTTP. Below is the result:
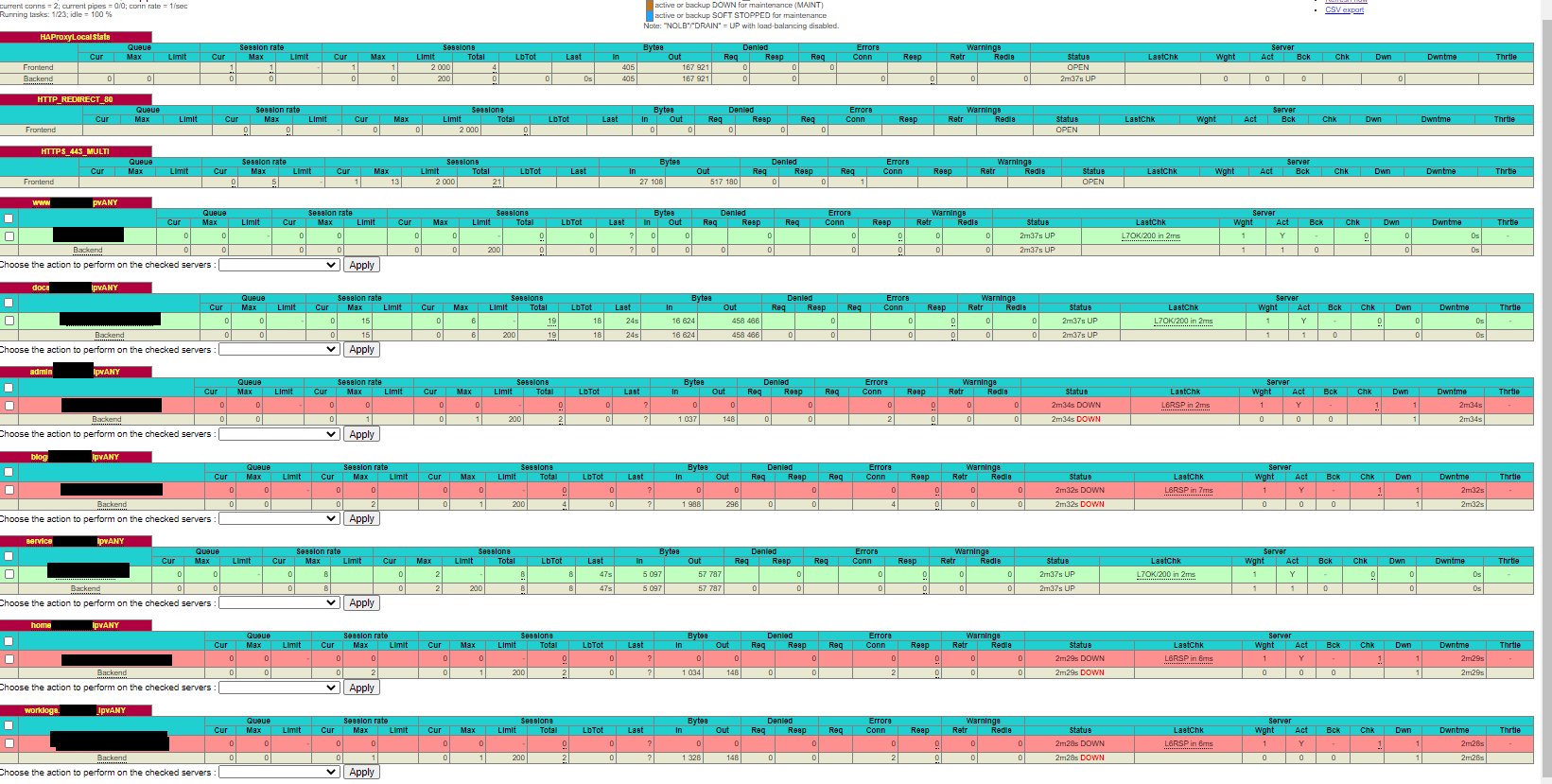
-
@bjk002
he problem is NOT a firewall-rules problem, as all the LastChk says "L6RSP in 3ms". This means that a TCP-connection was made succesfully. But the certificate/cipher negotiation failed.. If you 'hover' with your mouse over that line it might tell a little bit more about the reason that failed.If you are only switching the 'port' on a already configured server it 'might' remember the old port.. If you hover with your mouse over the servername it should show the ip:port its trying to connect to verify that its showing the 443 port there..
Finally can you paste the configuration of a backend as it appears in haproxy.cfg (bottom of settings tab) here when its configured for the ssl-checks?
-
@PiBa said in Question on HAProxy, VIPs, DHCP, and Firewall Rules:
haproxy.cfg
PiBa,
Thanks for sticking with me. I hear you regarding firewall/rules.
Hovering over the "L6RSP in 6ms" yields "Layer6 invalid response: SSL handshake failure" for each backend.
I hovered over server name affiliated with each failed backend, and the server:port were correct for each.
Below is the content of haproxy.cfg for one backend with SSL. I changed domain and server names to obscure.
backend worklogs.example.com_ipvANY mode http id 100 log global option log-health-checks errorfile 503 /var/etc/haproxy/errorfile_worklogs.example.com_ipvANY_503_ErrorPage503 timeout connect 30000 timeout server 30000 retries 3 option httpchk OPTIONS / server EXAMPLESERVER EXAMPLESERVER.example.com:443 id 101 ssl check inter 10000 ca-file /var/etc/haproxy/ca_5ea74728e9b92.pem crt /var/etc/haproxy/server_clientcert_5ea9847021976.pem resolvers globalresolvers -
@bjk002
I see you configured both a CA-certificate and a client-certificate for the server.. Are you sure a client-certificate is needed to connect to the server? Can you try without those?
If that works then only add the CA-certificate, and try again. If it still works 'maybe' add the client cert back.?. -
Let me give that a try. I'll report back.
-
Confirmed. it works with no client cert.
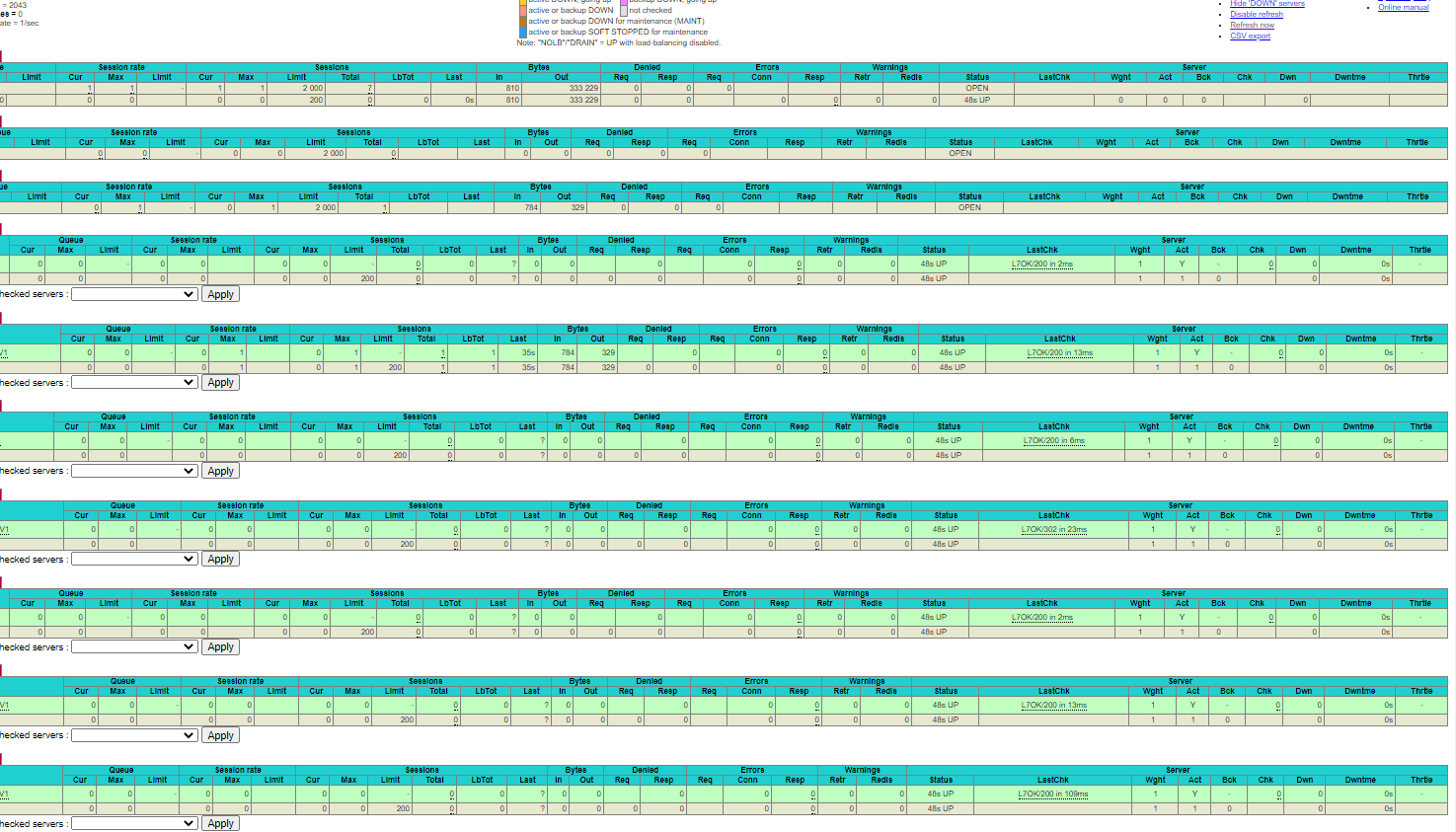
I will need to add client cert back and retry, but I've got to run for now. TY!!!
-
@bjk002
Okay thats good news ;) . As for the client-certificate, when you connect with a browser to the servers, do they ask you for sending/selecting a client certificate from your browser? (This would mean most people cant visit those sites when they would connect to the servers, but maybe that intended.?.) -
@PiBa - real quick - yes, good news. =)
And, yes, originally, you get a prompt for the client cert. it is intended.
I'll fiddle with it later this evening and see if I can get everything to work.