PfBlockerNG high CPU
-
Really no one an idea where this CPU load comes from? Currelty no traffic nothing, only a few idle clients
i looks to me, that I´ve activated some feature, which is simply to much for the pc engines hardware (APU), but I can´t figure out what.11682 root 32 0 51908K 38264K piperd 3 170:52 22.36% /usr/local/bin/php -f /usr/local/pkg/pfblockerng/pfblockerng.inc index 11320 root 24 0 14596K 8564K kqread 1 89:11 7.08% /usr/local/sbin/lighttpd_pfb -f /var/unbound/pfb_dnsbl_lighty.conf 11584 root 22 0 51908K 38264K piperd 2 45:19 4.33% /usr/local/bin/php -f /usr/local/pkg/pfblockerng/pfblockerng.inc dnsbl -
I see the same thing :
12506 - I 0:00.47 /usr/local/bin/php -f /usr/local/pkg/pfblockerng/pfblockerng.inc dnsbl 12638 - I 0:00.44 /usr/local/bin/php -f /usr/local/pkg/pfblockerng/pfblockerng.inc index 12863 - S 0:00.51 /usr/local/bin/php -f /usr/local/pkg/pfblockerng/pfblockerng.inc queriesThese 3 stay in the process list.
I guess it depend on the options you choose.edit : but it's normal that they are there - they are launched and pushed in the background. Quiet are for php script files, but it can be done.
Running process as interpreted script code like PHP will ask a lot of resources, true. -
Hi Gertjan,
That is crystal clear. These processes are always running.
If everything is running normal, the processes are running but not consuming a lot of CPU (max 2-3%). After some time (12-36 hours) especially the index command starts consuming about 25% CPU - constantly, without any drops.I don´t understand the reason.
Because my system is fanless, i just want to understand the reason and if possible avoid this kind of situation to not heat up unnecessarily the CPU (after 36h it touches 70 degree celsius).
To be more precise:
It is clear that the processes are running. The question is: Why does the process pfblocking.inc index start to consume a lot of CPU after time, and why does he continuosly consume the resources until:- I reboot the system or
- I disable DNSBL, Update and reload and immedately after enable DNSBL and update reload again
In both cases the "high" CPU load disapears and for the next 12-36 hours everything is running fine :)
Regards,
Frosch1482 -
Did you ever resolve this issue? I'm currently experiencing the same thing.
-
@lunaticfringe80 said in PfBlockerNG high CPU:
Did you ever resolve this issue? I'm currently experiencing the same thing.
Could be related to the pfctl/multicore issue.
Search the forum. Its 11.3 stable related.
-
@lunaticfringe80
Unfortunately not. Still the high CPU is there... Sucks a little bit =) -
after upgrading to 2.4.5-P1 things become even worse.
I had to switch off PfBlockerNG because the high CPU load resulted in packet loss and very bad DNS resolution times.I´m currently installing Pihole in a VM. Hopefully this issue will be fixed soon, so that PfBlockerNG can be used again.
(As far as i understood it might be a general 11.3 release issue. Therefore I guess I have to wait for release 12) -
Can you check if everythuing goes fine with one small list like :
Wait a day or so, see if it is stable.
If ok, add another list :
and re test - be patient.
Etc.
Raise the number of feeds, or more important : the number of IP/DNSBL step by step.
Btw : open the manual, and do a file consisty check.
edit : better : have a look at the latest official Netgate's video. Do as instructed. -
@Gertjan Hi, thank you for your help.
I executed the fsck command in single user mode as explained in the vid.
No issues where found (done it 3 times :))with the IP block lists i have no issue. The issue with high CPU (and load average > 2.0) starts when i use DNSBL for ad blocking.
You say i should raise the number of feeds slowly and see what happens. I was using the default lists from the feed.
BR
Frosch1482 -
@Frosch1482 said in PfBlockerNG high CPU:
The issue with high CPU (and load average > 2.0) starts when i use DNSBL for ad blocking.
The issue is :
@Frosch1482 said in PfBlockerNG high CPU:
IP block lists
To many ..... hundreds of thousands IP's and domain nmaes, handles by PHP does take even a powerful system to a crawl.
Any system can download them fast.
But the sorting, weeding out the doubles, preparing the files so unbound can read them etc, takes time.
Then unbound has to build it's internal structures so it can work with them .... that takes time.That why I propose to start with one small feeds - just a few IP's and/or DNSBL.
My question is : does the problem persist ?@Frosch1482 said in PfBlockerNG high CPU:
I was using the default lists from the feed.
What does that mean ?
By default, pfBlockerNG does not have any feeds active.
So, you activated one of them ?
All of them ? -
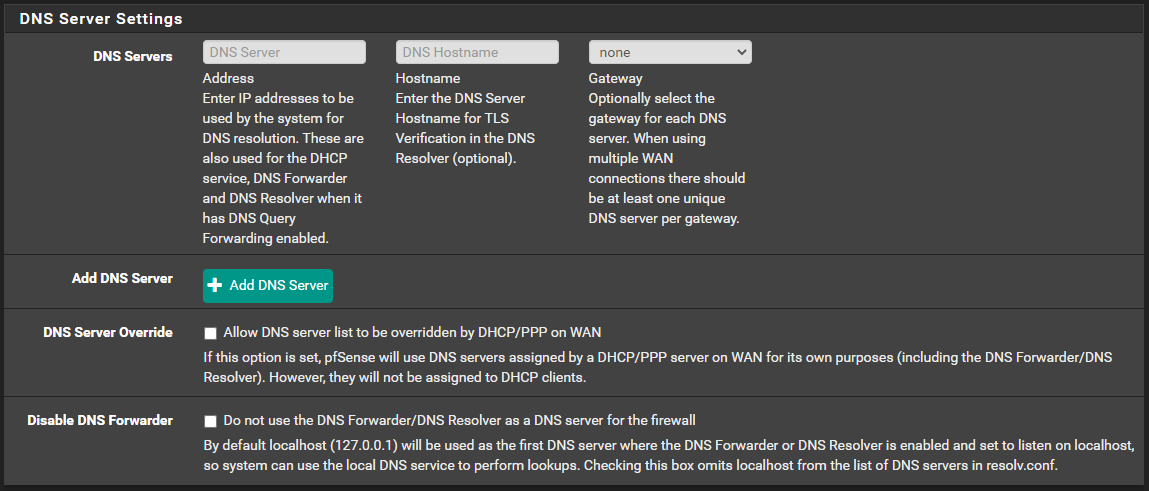
Are you using unbound and not the forwarder?
Delete any DNS related stuff under system -> general. It will make pfblocker significantly quicker since it doesnt have to resolve to external dns
-
Done!
-
How does that work if we remove the servers from System > General? The DNS Resolver uses those to forward queries, so name resolution fails completely when I do that.Fixed. It helps not to use a VPN interface that depends on name resolution for name resolution.I too am testing this with just a single list to start. It would be a bit disappointing if pfblockerng could not handle the load, considering I was previously using Pihole on a Raspberry Pi Zero with a million domains in the blocklist without issue. I've got pfSense on an Odyssey X86 which is significantly more powerful.
-
@lunaticfringe80 said in PfBlockerNG high CPU:
How does that work if we remove the servers from System > General? The DNS Resolver uses those to forward queries, so name resolution fails completely when I do that.
I too am testing this with just a single list to start. It would be a bit disappointing if pfblockerng could not handle the load, considering I was previously using Pihole on a Raspberry Pi Zero with a million domains in the blocklist without issue. I've got pfSense on an Odyssey X86 which is significantly more powerful.
It works for the rest of us :) Something is worng in your setup.
-
@Cool_Corona The DNS issue was a dumb oversight. Unbound was set to go out on a VPN interface with a domain name which of course won't work if it can't resolve the name. I appreciate the helpful reply, though.
The real issue here is the pfblockerng performance, which doesn't seem to be working for everyone.
-
@lunaticfringe80 said in PfBlockerNG high CPU:
@Cool_Corona The DNS issue was a dumb oversight. Unbound was set to go out on a VPN interface with a domain name which of course won't work if it can't resolve the name. I appreciate the helpful reply, though.
The real issue here is the pfblockerng performance, which doesn't seem to be working for everyone.
No worries. I get that, but we need to eliminate a lot of things first to get to the problem.
What packages are you running and are you using thePFB Devel or std. package?
-
I've tried both so far. Currently testing the devel package, and the problem has just re-emerged.

What I did was uncheck the box to keep settings, completely uninstalled pfblockerng-devel, reinstalled pfblockerng-devel. I ran the wizard, and then went in to the feeds and disabled all but just one feed per group, leaving the top one in each. I set the update frequency to once a day and then entered my maxmind key. Then I ensured pfblockerng and dnsbl were both enabled. It was fine for about 5 hours and then it begins again. There's correlating state table usage as well:

Now here it is over the past 5 days. The first group is from the standard pfblockerng package, second group is from the devel package.

It just keeps repeating that pattern until I restart it, then it comes back within minutes to hours.
I've tested it with and without suricata, snort, squid, badnwidthd, darkstat, apcupsd, and clamd running. I've run it with none of those, and variations of different ones running. No difference in result. The only other things consistently running have been openvpn and then telegraf for monitoring.
-
Have you tested LAN for malware/spyware??
Have you noticed anything suspicious in the states table???
-
This post is deleted! -
There's only two machines running windows, one is my primary desktop, and the problem happens while it is completely powered down. It gets regular scans and I'm cautious online so I'm pretty confident it's clean. The other is a work laptop that goes through corporate VPN before I even login, and these events happen while it is offline too.
Everything else runs Linux and I'm pretty confident they are not compromised.
There's a lot of IoT on the network, the two Nvidia Shield's are pretty chatty and were top of my pihole block counts in my previous setup, but if those cause this problem it would kinda defeat the purpose. Stopping devices like that from phoning home is part of why I'm sinkholing dns to begin with.
I did not realize I could directly monitor the states table, I see it in the diagnostics menu so I will watch it during these events.