OpenVPN Site to Site VPN: No LAN to LAN Communication
-
Hi all,
I have two sites:
A) LAN: 12.1.1.0/24 (server)
B) LAN: 11.1.1.0/24 (client)Tunnel Address: 192.168.50.0/24
At this moment, I have the site to site VPN up; however, two LANs can't communicate with each other.
Here is the odd part (...i think), both pfSense box itself can reach the LANs (example, box A can reach LAN of box B) only if I source the traffic from the new tunnel interface (OPT1 for example). If I source from LAN interface, no luck.
I verified that followings were taken care of:
- Firewall rules. Under LAN/OpenVPN/OPT1 all pretty much allow any any
- I tried Outbound NAT as some threads suggested, no luck.
- Routing seems to be okay:
Destination Gateway Flags Use Mtu Netif Expire
default 192.168.1.1 UGS 412450 1500 igb0
11.1.1.0/24 link#2 U 346097 1500 igb1
11.1.1.1 link#2 UHS 258 16384 lo0
12.1.1.0/24 192.168.50.1 UGS 790 1500 ovpnc1
127.0.0.1 link#4 UH 97 16384 lo0
192.168.1.0/24 link#1 U 134359 1500 igb0
192.168.1.68 link#1 UHS 0 16384 lo0
192.168.50.1 link#8 UH 251091 1500 ovpnc1
192.168.50.2 link#8 UHS 0 16384 lo0- I even added static routes on both sides. Here is an example on client box:
12.1.1.0/24 OPT1_VPNV4 - 192.168.50.1 OPT1
What else am I missing? Let me know if you need more information.
Thanks,
-
Are you really using 12.1.1.0/24 and 11.1.1.0/24 or did you obfuscate the address space?
-Rico
-
Apart from the invalid address space, openvpn has its own internal routing table too
You need to specify the networks behind the clients
something like that
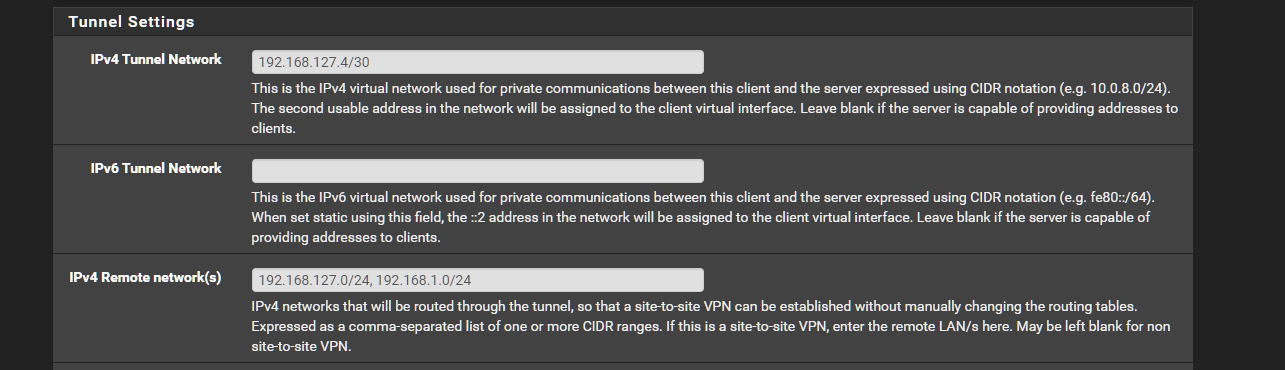
-
@Rico Hi Rico,
I am actually using 12.1.1.0/24 and 11.1.1.0/24 on the LAN side. Lets just say this is the network I adopted. I have over 20 locations where I want to place Netgate firewall and doing proof of concept at this moment to see if its feasible.
Since I am using odd addressing space, is this the reason why my two LANs having issues?
-
@netblues Hi ,
Thanks for the feedback! I haven't tried that. I only have 12.1.1.0/24 & 11.1.1.0/24 as remote network.
-
So guys,
I was able to resolve the issue by switching the network to private addresses (i.e. 12.1.1.0/24 -- > 10.12.12.0/24) and by adding static routes.
I am not sure why I wasn't able to route 12.1.1.0/24 even with static routes properly. Currently, its working flawlessly with Cisco ASAs and I am planning on migrating over 20 sites to Netgate.
Any suggestions? Is it even possible to route public networks via internal VPN cloud?
Thanks,
-
@Teh_Bot openvpn or any other vpn technology isn't automatically filtering on any ip's (with a very few exceptions, like localhost, sometimes apipa etc)
Still, you need to declare to vpns the ranges that will pass through.
See the openvpn wiki entry
https://community.openvpn.net/openvpn/wiki/RoutedLansputting nat rules in a vpn is not recommended, and it does make things difficult to comprehend.
I suspect there was some typo somewhere and was eliminated by renumbering.
-
If you needed static routes to make this work you did it wrong. You will experience occasional strange issues if you use static routes.
Let OpenVPN install the routes using the Remote Networks fields.
-
This post is deleted!