VLAN Configuration Question
-
Hi,
Yes, pfSense can handle this task without any other difficulties.
"How complicated is the setup? = wants some professional knowledge, but nothing is impossible with learning...please keep in mind, NGFW is not something you can leave alone, requires continuous, almost daily administration!
here in the forum you can get answers to anything that only causes problems during installation and subsequent management
PS:
I would further segment the network to.. "D" VLAN for WLAN devices (phones / tablets) only
and
"E" VLAN for gaming consoles (because the UPnP & NAT-PMP)
-
I’d have wifi on the same subnet as the ethernet devices.
Class your vlans on use, I have the following:-
LAN <- This is just used for switch management
USER <- My Macs, iphone, ipad, work laptops, etc ...
GUEST <- Where I let my guests connect
IOT <- My IOT devices
DMZ <- Where I place my publicly accessible stuff
The last 3 vlans can only access the internet.
Does your wifi support vlans?
-
@DaddyGo Thank you for your feedback!
I like your suggestion to put our phones/tablets and gaming consoles on separate VLANs. Also love that NGFW supports UPnP which might simplify things for our gaming consoles.
I also love playing around with new devices and software. So, no worries about learning new things on my end. This is probably how we ended up having quite an elaborate network for a home environment. ;)
I have also gained experience with various platforms (Netscreen, Sophos SG/XG, Meraki and others) over the years. However, I am somewhat concerned about your statement that I would have to do daily administration work using NGFW. I mean I understand that it will take some time to get the configuration into place, but why would I have to do daily administration once everything is up and running? Could you please elaborate on that? TIA!
@NogBadTheBad Thank you for your feedback!
Your setup also raises some interesting ideas and, yes, we also have a GUEST network, but I forgot to list it since it is handled by the wireless access point.Yes, our current wireless solution (aging Meraki) supports VLAN. How do you like the UniFi AP-AC-Pro? It is one of the devices I have looked at, but I was hoping to find a device supporting WIFI 6.
One new question for both of you: Our current solution allows me to assign multiple VLANs per interface/subnet. Is this possible with NGFW? I have seen the VLAN configuration screen and I am confused by the need to assign one interface to one VLAN without giving the option to assign it to all interfaces.
-
@jst68 said in VLAN Configuration Question:
One new question for both of you: Our current solution allows me to assign multiple VLANs per interface/subnet. Is this possible with NGFW? I have seen the VLAN configuration screen and I am confused by the need to assign one interface to one VLAN without giving the option to assign it to all interfaces.
VLAN 10 on one pfsense interface is different to VLAN 10 on an other interface, you'd need to set up a LAG i.e. bond 2 x 1Gb interfaces together.
Create them here:-
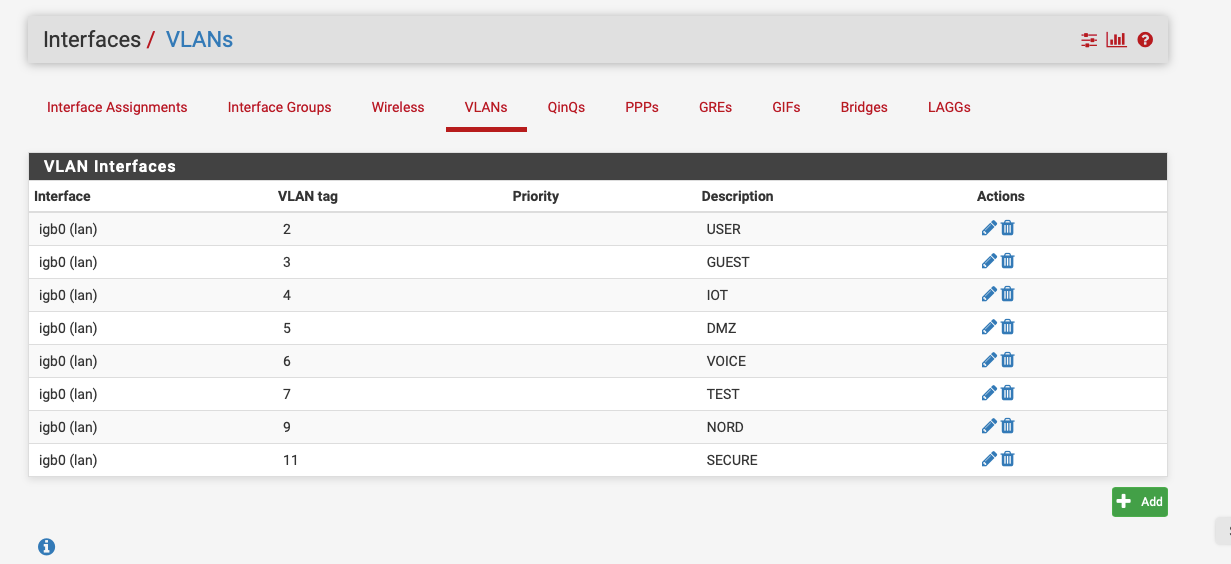
Add them to the interfaces here:-
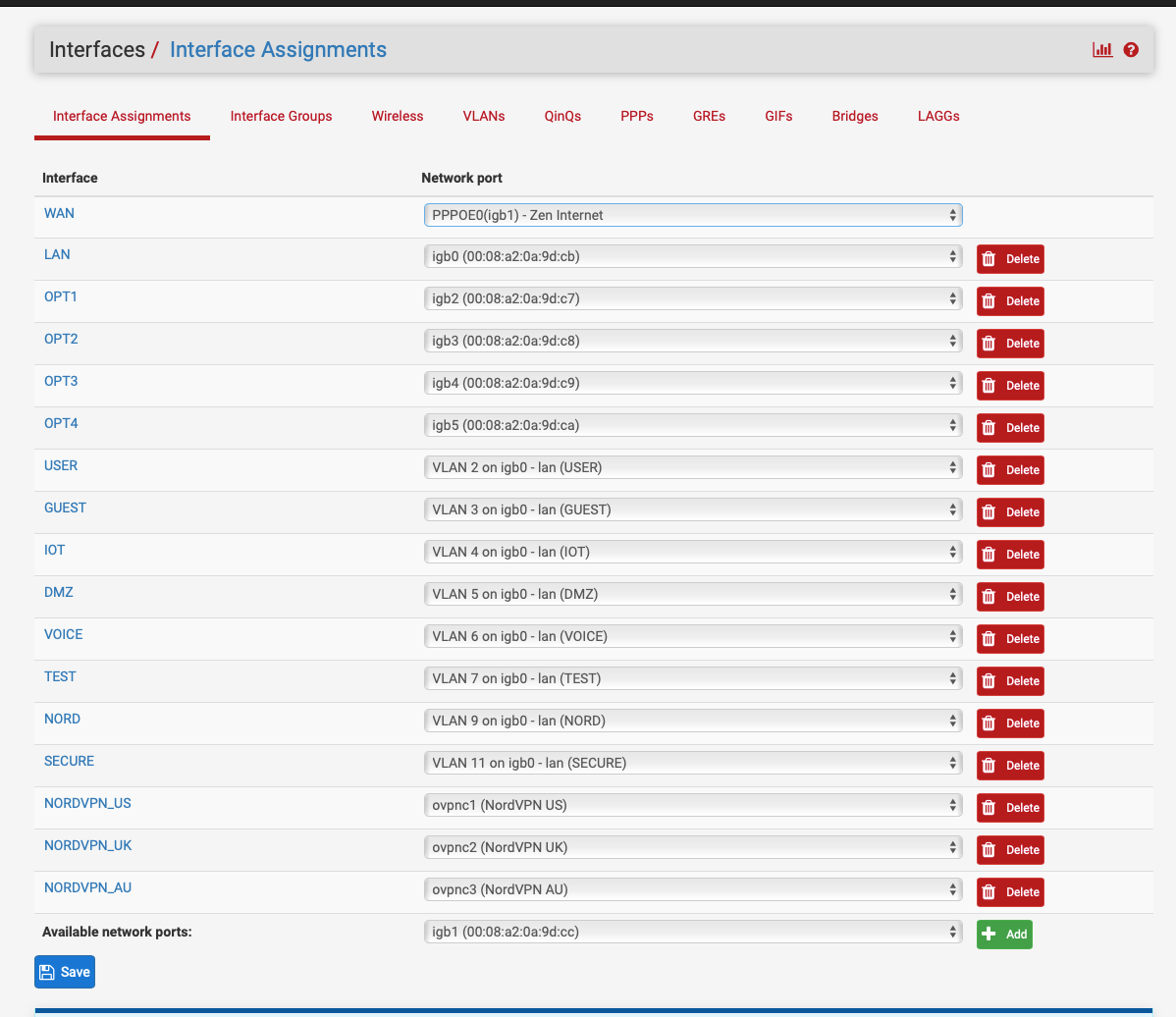
The Ubiquity stuff seems to be the flavour of the month due to cost and it handles vlans.
-
@jst68 said in VLAN Configuration Question:
@DaddyGo Thank you for your feedback!
Hello,
As @NogBadTheBad suggests, the more parts you divide your network into, the more secure it is.
(WiFi devices, game consoles, phones are almost mandatory for these)
there is currently a small problem with pfSense UPnP, but it is in the process of being fixed and is only affected by multiple consoles on the same networkhttps://forum.netgate.com/topic/154153/test-request-upnp-fix-for-multiple-consoles-playing-the-same-game-static-port-outbound-nat
VLAN question on same interface:
although at this point I would note that for many VLANs, it is not enough to create a LAG
VLANs consume the bandwidth, on the interface or interfaces (1Gig) in LAG (2Gig)
if you can, choose a solution where you can integrate a +++quad NIC into the hardware
or
for example, I use hardware that has 4 ports on the motherboard (Intel I350 !!!!) plus four portals on an addon card level (Intel I350 also !!!)
it already has eight physical interfaces, it is smoothly enough for a very secure SOHO environment(thus, fewer VLANs need to be placed on one physical interface
in my opinion, I by no means place more than 2 - 3 VLANs on one physical interface
(unless, not 10Gig is the speed of that physical interface))@jst68 "Could you please elaborate on that? TIA!"
pfSense begins with long learning and after that comes satisfaction and joy....
it will help a lot if you have experience with devices from reputable companies (Cisco Meraki, Sophos, etc.), but pfSense is great because it's not as rigid as Cisco ASA and not so expensiveby daily administration I mean that in an NGFW environment, you will receive alerts and blockages on a daily basis, which needs to be investigated
it is not a switch that we configure and let it work
for example:
want to visit a website, but the system will not allow it
and it has been used so far, but let's say pfBlockerNG now blocks either Snort or Suricata or Squid, etc.ERGO:
so you need to look at why these applications consider the site in question dangerousit can usually be said that 4 -6 months and all its lists, rules and operating conditions will be fine-tuned
the second thing: since it is a communit-supported opensource system, it responds much faster to any changes, vulnerability fixes, so it is very important that you always follow the updates
many people don't think so and postpone the update for months, but it's nonsense, the updates are not made in vain and put into the system
finally, an important suggestion to get rid of a lot of headaches....
do not use NICs with Realtek or other unnamed ethernet controllersthe soul of NGFW is the NIC
the following Intel ethernet controller basics are a particularly good choice for pfSense:
I340, I350, I210, I211 -
@NogBadTheBad and @DaddyGo
Thank you again for your feedback!The VLAN information is very helpful for me. I also have finally been able to setup a small test box. More testing might result in more questions...

-
this would have been my next suggestion - test environment first - before releasing pfSense to your family, hahahahaa
even with this you can avoid a lot of unspoken slander
come back to us if you have any questions

-
Also a test or lab VLAN like @NogBadTheBad lists is a very good idea to test things out before running it on other VLANs that could drop your wife's/family's acceptance level

-
-
because I think we're over it....hahaha
that’s why you have to work (on pfSense config), when everyone is asleep
