Access 4G modem GUI behind pfsense over vpn
-
Nop, I didn't.....
If I can be honest,I am not an super expert with PfsenseCan you give me some help please?
Thanks
-
@ismurdegus said in Access 4G modem GUI behind pfsense over vpn:
If I can be honest,I am not an super expert with Pfsense
Me either.

Maybe something like this?
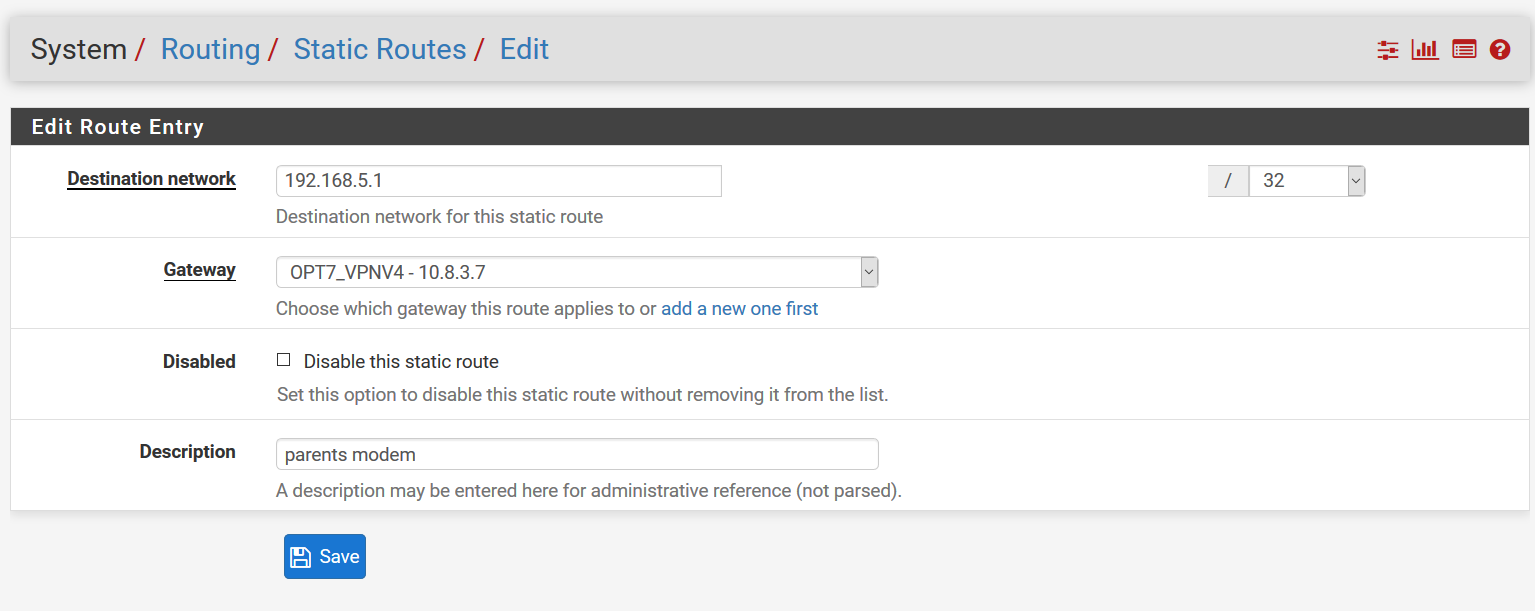
Give it a try at your place (but with your VPN-Connection) and if it doesn't work, I shut my mouth.
-
This post is deleted! -
On my system, I don't have the OPENVPN for GATEWAY
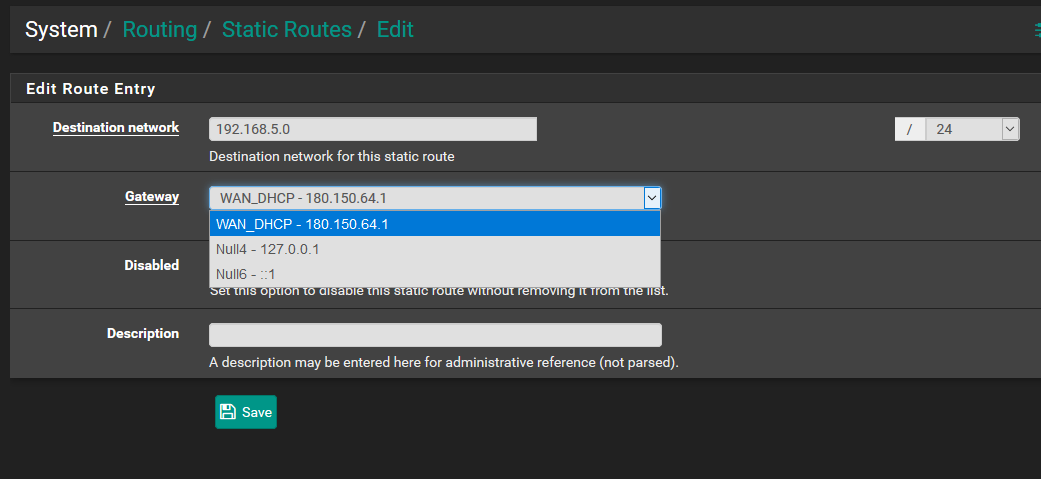
-
Routing alone won't make it work.
The issue is that the 4g modem only knows directly connected network, and sends everything else to internet (or nowhere).
Create an outbound nat rule on wan intearface, with target ip the wan network.
Use the wan interface as source. -
I tried to follow your instruction, like I say I am not an expert....
I create the rule on the SITE2, but is not working :-(
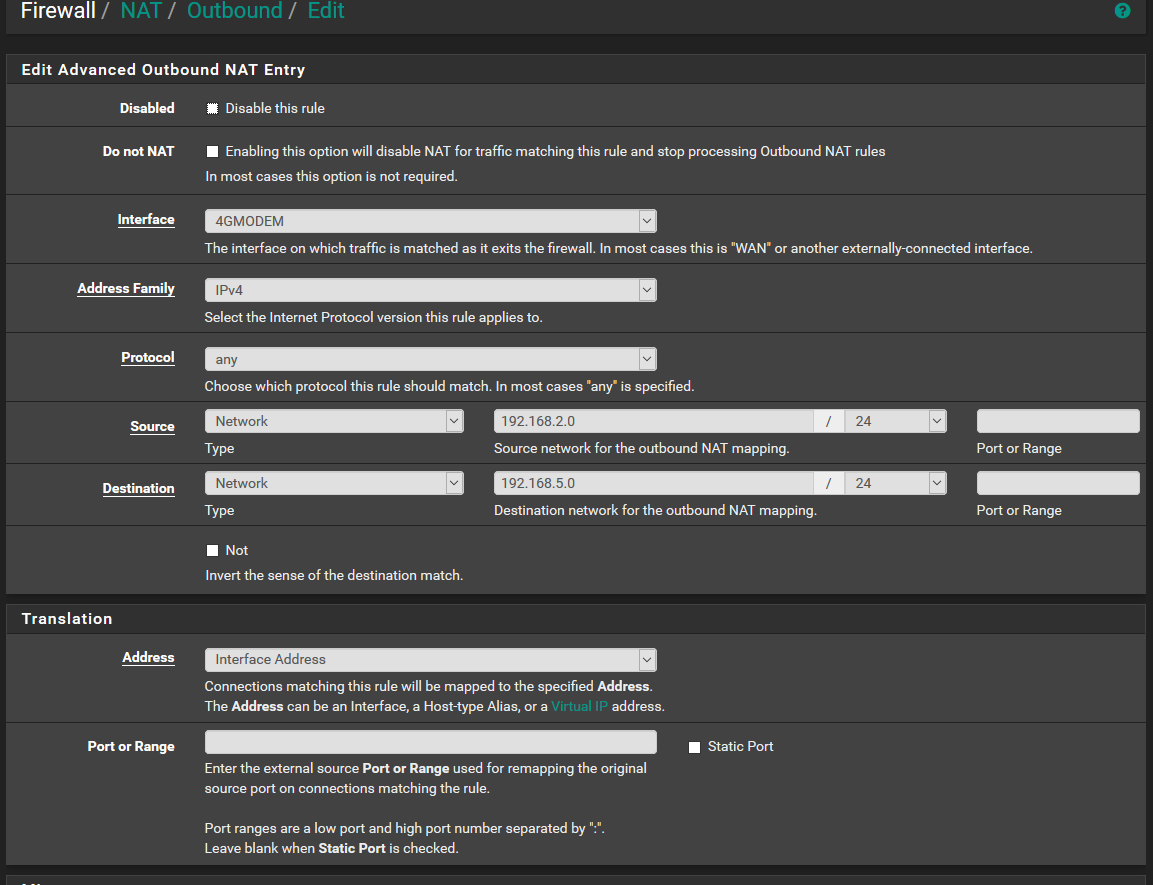
-
@ismurdegus Source should be any, and certainly not 2.0
Put at least 192.168.0.0/16 as source.As for routing in openvpn , it is handled via openvpn server config page, NOT static routes.
You need sto add 192.168.5.0/24 as an ipv4 local network there. -
I don't fully understand your comment, so I hope I did this right....
On SITE2 I setup the follow but still doesn't work :-(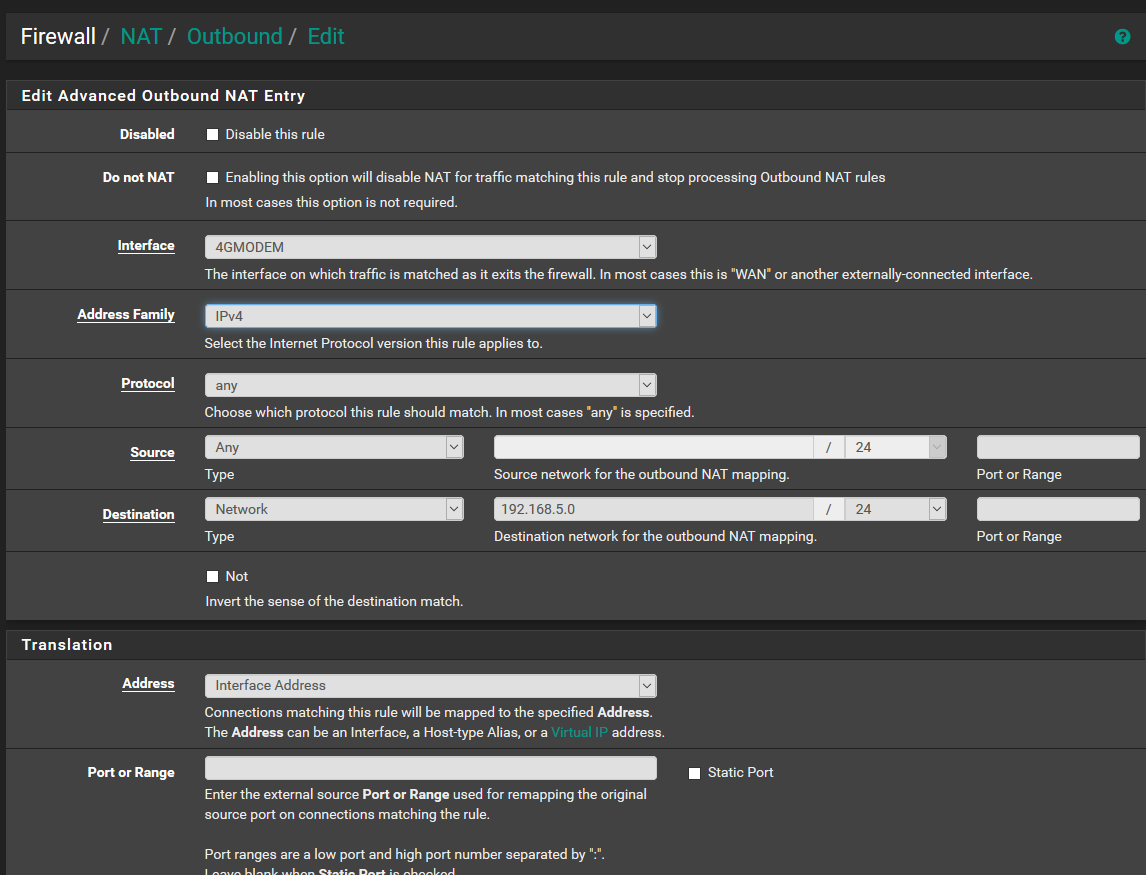
Also what you say before:
"As for routing in openvpn , it is handled via openvpn server config page, NOT static routes.
You need sto add 192.168.5.0/24 as an ipv4 local network there."This is doesn't make sense at all for me.
Can you give me more details please?
Thanks
-
nat rule is ok.
As for routing, you should go to the pfsense acting as client config page
near the bottom, tunnel settings
IPv4 Remote network(s)IPv4 networks that will be routed through the tunnel, so that a site-to-site VPN can be established without manually changing the routing tables. Expressed as a comma-separated list of one or more CIDR ranges. If this is a site-to-site VPN, enter the remote LAN/s here. May be left blank for non site-to-site VPN.
put 192.168.5.0/24 , 192.168.2.0/24 save, reestablish and retry
-
Already done this on the SITE2 (VPN Client) but still no working
