Config OpenVPN to reach the lan side through a router?
-
forget dns at the moment. Things need to ping by ip first.
vpn client will an ip from the network you specified as the tunnel network.
You need to specify additional networks further down too. (ie 192.168.100.0/24)
all net stations must know (have routes) to reach vpn.
Put a route on pf for second lan pointing to 172.16.1.10 for network 192.168.100.0/24
point second router default gw to pf
and point stations default gw to second router lan and it will workAnd post your vpn and lan firewall rules too
-
as an alternative , wifi is most probably a bridge, so just connect a lan port of the wifi router to the same lan as pf and forget about second lan
-
I think this is what @netblues is talking about, but don’t use a full blown WiFi router just for wireless access. Either wire it up like above, or if it’s a recent model, turn it into just an access point.
In access point mode, then simply plug it in anywhere on the LAN side of the pfsense box.
-
@netblues I'm going to test your suggestions, although I think I've tested before.
The AP alternative is what I was considering after all this difficulties, so I will test also.
Thanks! I'll keep you on touch with results... -
@akuma1x thanks, gonna test AP also...
-
@netblues I've pushed a route to the LAN gateway of second router in PfSense Open VPN server, and at the moment I'm able to ping till the WAN gateway of the second router (LAN router), but not to the LAN gateway, so i guess the problem must be in the second router, but I still don't know what the problem it's.
From a LAN side computer i can ping till the LAN gateway of PfSense, so we have upload but not complete download.
Any ideas? -
@ReneMG Please provide an updated diagram with devices And routing/default gw info from all border devices.
And also your lan and openvpn fw rules. -
@netblues here we have the Network Diagram:
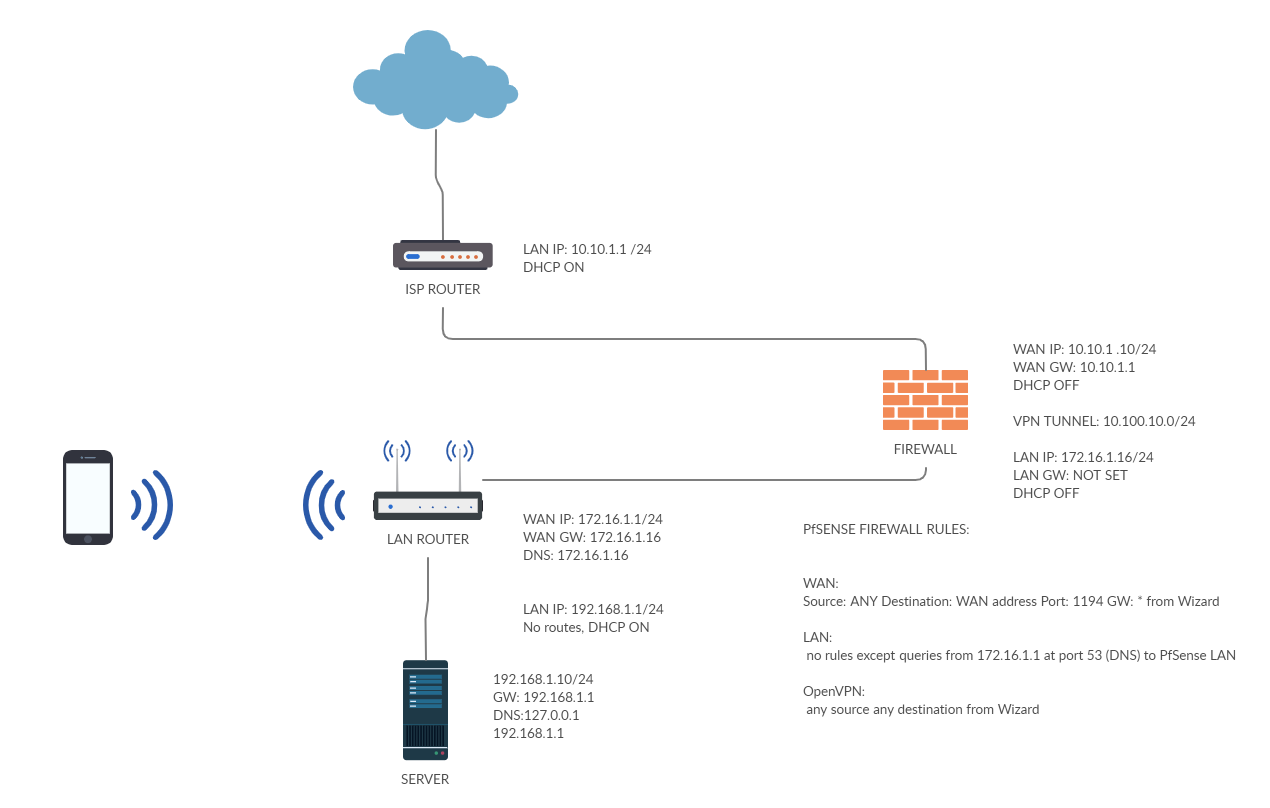
An the PfSense rules:
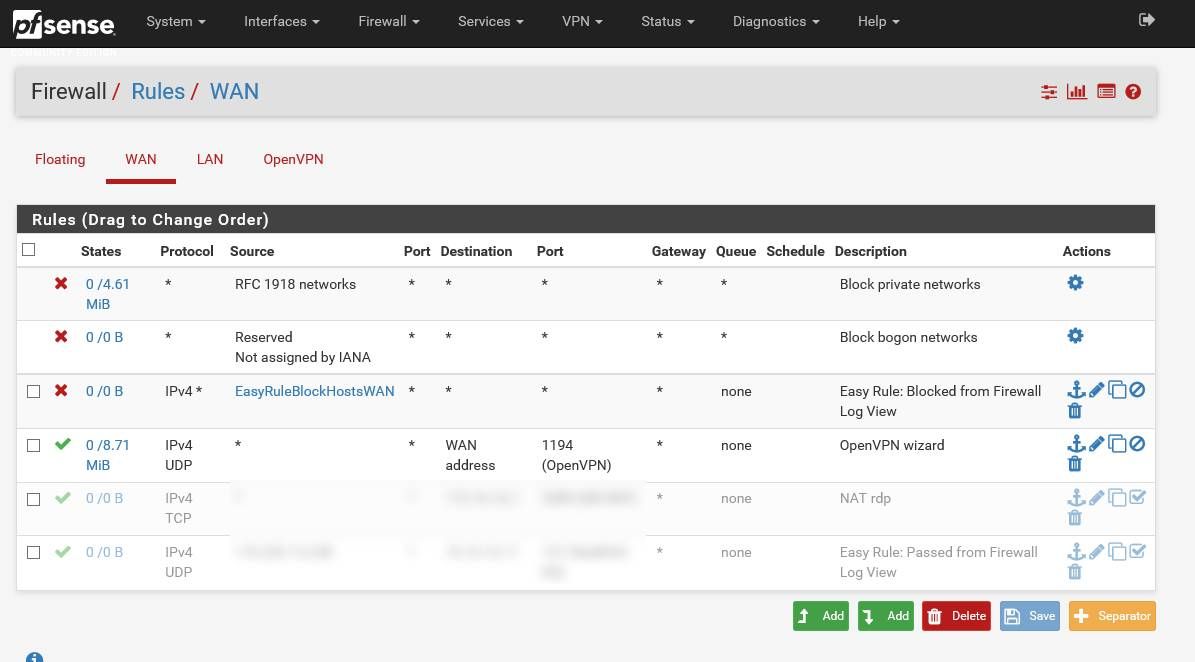
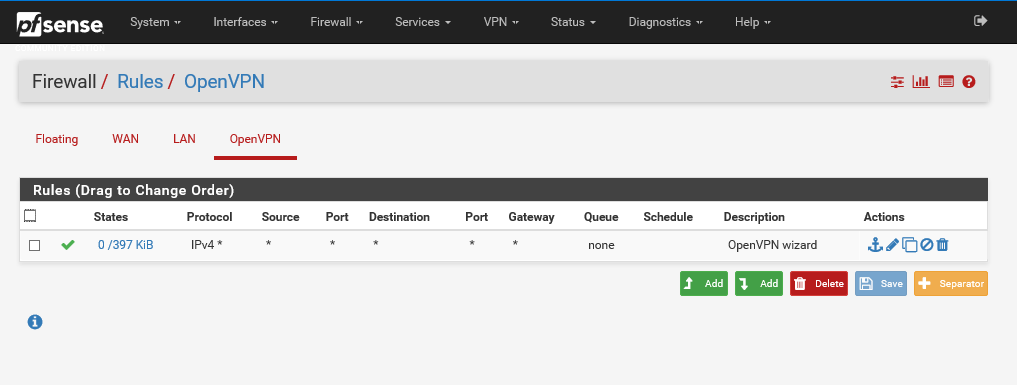
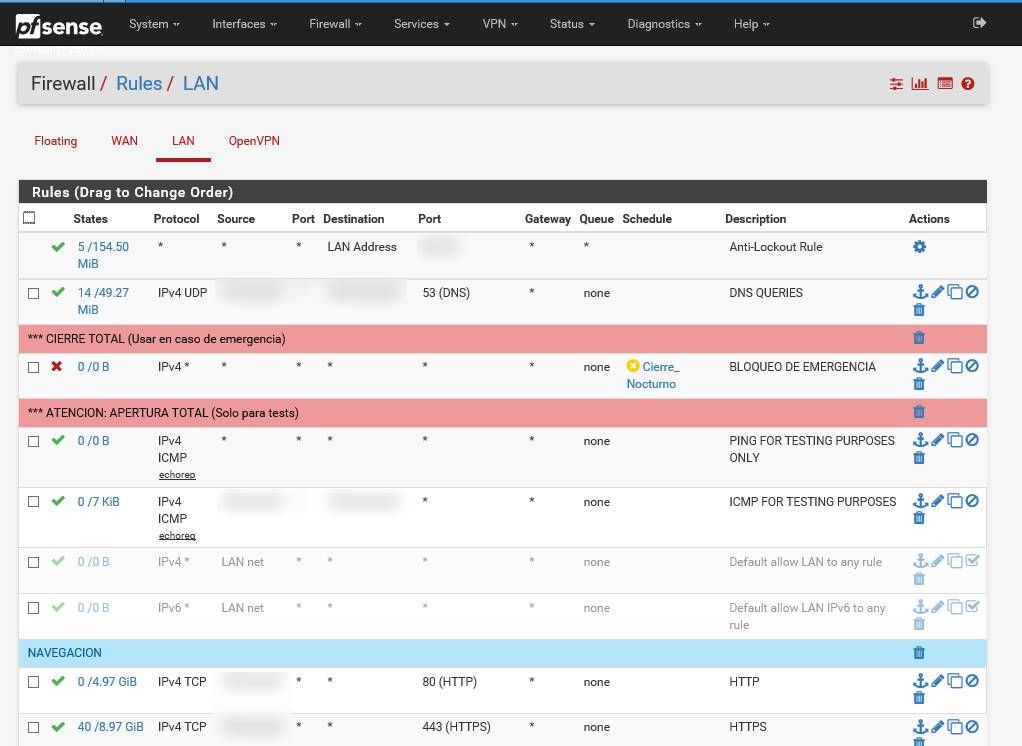
I hope it helps you...
And thank you so much for your time! -
@ReneMG So far, so good.
A few remarks./questions/ irrelevant to the problem.
I suspect you are port forwarding 1194 for vpn to work.
Since you are behind nat, you dont need to block rfc1918. You are only blocking your isp router.
Are you also natting on pf (ie you are on double nat) This can possibly be improved.
Also dns queries are also tcp.. in some cases.
Consider moving icmp allow before your night schedule disable all rule.
(At least when debugging, forgotten schedules can mislead you)
as a rule of thump, in such an environment you should allow all ,when debugging routing issues, and when you have connectivity established, start narrowing down access.Now regarding the issue.
Make sure you have a static route on pf for network 192.168.1.0/24 pointing to 172.16.1.1
on 192.168.1.1 router. Is nat off?
can you ping from pf cli to 192.168.1.10 ?
Is any host firewall on 192.168.1.10 off?If the above works, then we can focus on the vpn. (post your vpn config)
-
@netblues answering under your comments:
I suspect you are port forwarding 1194 for vpn to work.
TRUE. I was port forwarding the vpn port 1194 in the isp router, but actually the rule has been deleted.Since you are behind nat, you dont need to block rfc1918. You are only blocking your isp router.
I didn't' know it but i have disabled that rules and I wasn't able to see any difference, so i let them as they was.Are you also natting on pf (ie you are on double nat) This can possibly be improved.
No, no natting on pf at this moment, later maybe...Rules are set just right now in "allow all" mode for testing
Regarding the Issue:
*Make sure you have a static route on pf for network 192.168.1.0/24 pointing to 172.16.1.1
I added an static route under System>Routing>Static Routes, but first i had to add a gateway (172.16.1.1) to be able to point at iton 192.168.1.1 router. Is nat off?
If i put NAT off, internet connection downscan you ping from pf cli to 192.168.1.10 ?
Nope, and also not at 192.168.1.1Is any host firewall on 192.168.1.10 off?*
No firewalls On all over the net (hosts, routers)And with the tests, OpenVPN server is not working anymore. it sends an 10054 UDP Unknown error. So, I reinstalled it and still gets the error.
And now I'm stopped here, trying to guess why this error. -
@ReneMG said in Config OpenVPN to reach the lan side through a router?:
on 192.168.1.1 router. Is nat off?
If i put NAT off, internet connection downsSince 192.168.1.1 is using nat, this is essentially a firewall, which won't allow traffic to be routed.
Obviously port forwarding isn't an option.
In many wifi cheap routers disabling nat makes them a router, but I have no idea if that is the case. Maybe the firewall needs to be adjusted. Often, such wifi routers have bugs, or features crippled.
So, no, it won't work unless 192.168.1.1 starts behaving as a router.
We need to see details of that box. -
@netblues I have something similar to good news.
Today I've reinstalled the Pf, after that and without having nothing configured, I've tried pings from host to Pf and from Pf to host, results were that ping always stopped at LAN gateway of second router.
Then, i added a static route to that network under system, routing and tried again... and bingo! I received the answer from LAN gw of second router.
But... not all are good news, cause this set up was tested before without results.... but not from a clean install, so, now I have to add rules and install the openvpn server again and see what happens...but at least now I know that the config works from this point.
It's wonderful, isn't it?
Im gonna try to make all the necessary settings again and test the openvpn, so I guess I will continue giving you feedback about the further steps...cause I guess it wont work again at some point.
Thank you so much for your help and support...I'm so happy like a child! ;) -
@netblues Once i install the OpenVPN Server again and it sets the wizard rules i have no ping to LAN hosts, if i uninstall it, ping is working, so i guess the problem is a rule of the openvpn server or related to it.
Now, at least I know the cause, and I can focus on it. I'm going to try to have all this working together, although i don't know why the rules are making this behaviour!
Any suggestion?
Thanks! -
@ReneMG The rules of openvpn server are unrelated to lan access.
Unless there is some ip confict somewhere. -
@netblues Lan hosts are setting their ip's from Lan router by dhcp, the pfsense is recently installed without any setting except openvpn server.
it has to be another question!... -
[SOLVED]
I'm going to resume the steps to help others:-
Clean installation of PfSense
-
Add OpenVPN server in manual mode, not Wizard
-
Try to connect a client and take a look at inbounds connections at firewall, select the rule to the 1194 port and Permit it.
-
Modify the rule to allow any host to connect to the server
That's all, at least for me. I have the OpenVPN server working and clients can ping a host through a second router behind PfSense.
I hope it helps!Thank you very very much! special thanks to netblues without whom this wouldn't have been possible.
Thanks!
-