OpenVPN and Deutsche Glasfaser - IPV6 and CGNAT blocking connection?
-
Yes. My phone (Samsung S20) is on Vodafone in Germany and I have read that they have IPv6 nationwide.
Edit - I did some digging and it has an IPv6 address too. -
@charry2014 That's great, you don't need any IPv4, at least not if you want to connect the phone to home via OVPN.
-
The site https://ipv6-test.com/ reports that my firewall is filtering ICMP v6 messages. Could this be a problem for OpenVPN? I am suspecting it might. How do I enable this?
-
No. How is your IPv6 configured? I think your ISP is doing native IPv6.
-
I think so too, but I am not sure of much from my ISP.
One thing I did notice is that when I connect to whatismyipaddress.com or similar from different computers in my LAN that the IPv6 address that is returned is different for each one. The IPv4 address is the same, as I would expect. Now I think I am stumbling into a noob difference between IPv4 and IPv6 addresses.
So the question - what actually is the IPv6 address of my PFSense WAN?
-
You can see it in the interfaces-gadget and other places.
 (Status - Interfaces)
(Status - Interfaces) -
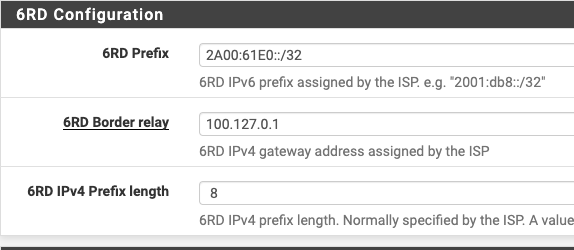
Alright - so it is something like 2a00:61e0:abcd
 :?
:?It is not the much longer address 2a00:61e0:b00b5:34dd:6969:beef:babe:face?
-
@charry2014 Can't say but maybe you did something wrong. Try this and go for DHCPv6 and not 6rd.
-
Boom - that did it - using the IPv6 address for the WAN as shown in the Interfaces widget on the dashboard packets are now flowing.
I now get an authentication error, but the connection is there. Authentication errors are kinda the staple for getting OpenVPN working so somehow I am back on known territory now.
-
No, OpenVPN uses UDP, not ICMPv6. However, ICMPv6 is used for a lot of things, so be careful about any rules blocking it.
-
One nice thing about IPv6 is there are plenty of addresses to go around. This means no longer having to share an address with NAT. Not only does each device get an address, it will often get several. With SLAAC, privacy addresses are often used. These are random number based addresses and you get a new one every day. They expire after a week. This is in addition to the consistent address, so you could have as many as 8 public addresses on each device.
-
Thanks everyone for your help - it seems that a little background reading would be a good idea sometime soon. This may well change the settings in the firewall rules, then?
-
That depends on what the rules do. If filtering on protocol, then you can often create a single rule that handles both. If filtering on address, then you'd need separate rules.
-
So here it is, best I can remember it. All the things I changed to get this working:
System - Advanced - Networking

Interfaces - WAN

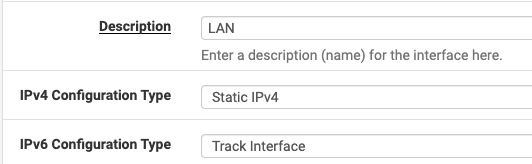
Interfaces - LAN:
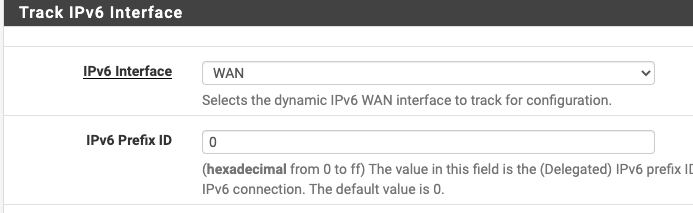
The PFSense WAN IPv6 address is then in the Dashboard.
Finally I meant to link to beechy.de above but got the wrong link pasted in.
-
That link @Bob-Dig provided says 6rd is going to be shut down, which means you should be configuring for DHCPv6 instead. My ISP did the same thing. They provided both 6rd and 6to4 tunnels, until they provided native IPv6 via DHCPv6-PD. This is what you should be configuring for, as that link describes.
-
@Bob-Dig said in OpenVPN and Deutsche Glasfaser - IPV6 and CGNAT blocking connection?:
this
Feeling brave I tried DHCPv6 like suggested instead of 6rd and from a quick late-night hack it broke the IPv6 connectivity for me. This is one for more experimentation.
For the moment my pressing requirement is to fix my OpenVPN authentication issue rather than future-proofing the IPv6 connection.
-
My authentication problems seem to be documented as a PFSense bug here so I have downgraded the login to SSL/TLS only and it works. Will keep researching the correct settings for DHCPv6. Cue small celebration here...
One further question - is there any way I can access my home network over IPv4? This would be very handy, for one thing my employer only allows IPv4 traffic through their network, and I am sure to travel to corners of the world where the mobile network is not quite so modern as here. I have no idea what options there may be for this.
-
If you mean connecting to your home network over an IPv4 tunnel, with IPv4 endpoints, probably not.
-
Not with that CGNAT address. Perhaps you could get an IPv6 tunnel from he.net. It will send IPv6 in IPv4 UDP packets, similar to that 6rd tunnel you were using. Then you'd use IPv6 to access your network.
It sure will be nice when the world moves fully to IPv6, so that we can put all this NAT nonsense behind us.
-
I think he was asking about accessing his network from an IPv4 source. Seems he has IPv6 worked out.