OpenVPN Firewall Rule Help
-
I only want to allow VPN Clients to access a fileshare and utilize DNS. I have the OpenVPN setup and I can access the share, but I can also ssh and use other protocols I don't want clients to use.
Network:
WAN (Public IP)
OPT1 -> OpenVPN interface
OpenVPN network (10.100.x.x/24)LAN network (192.168.0.x/24)
Internal LAN (192.168.1.x/24)I have all routes necessary to reach the servers
Servers:
Fileshare (192.168.1.162/24)
DNS (192168.1.160/24)WAN Rules:
Default block all except OpenVPN ruleLAN Rules:
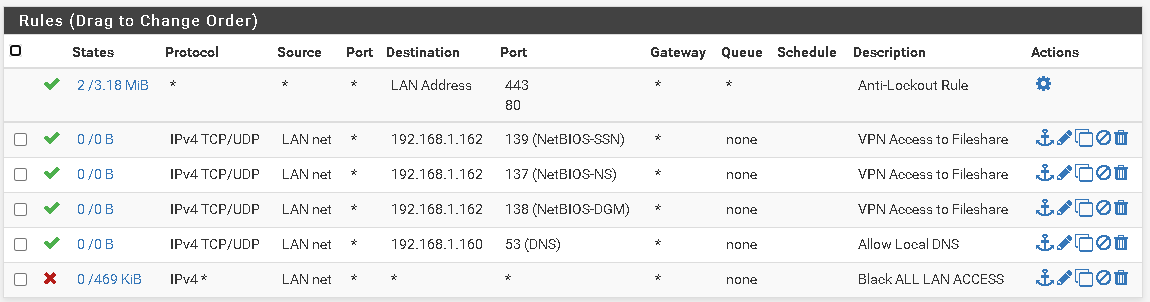
OPT1 Rules:
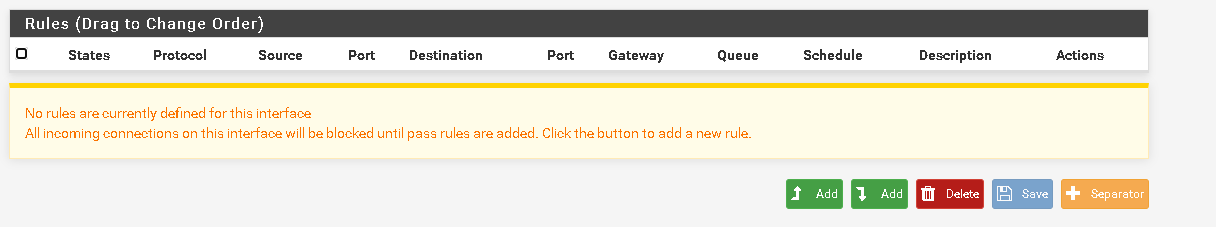
OpenVPN Rules:
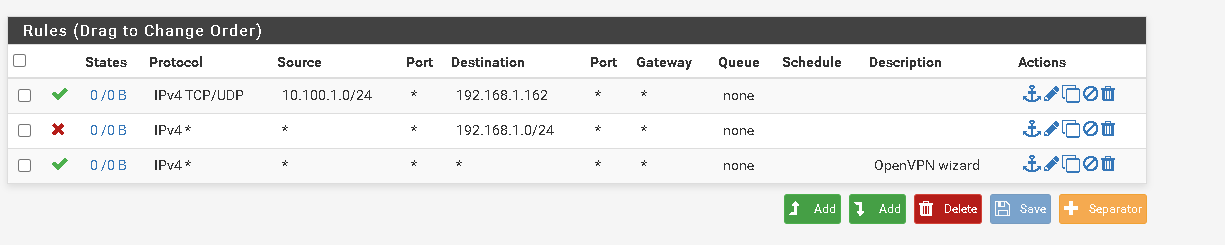
I need help on my OpenVPN Rules and my LAN Rules. I assume OpenVPN rules are assigned through OPT1 and I don't need to make any rules on that interface. I've also setup Client override on a test user account to only allow access to one network.
How to I make it so VPN Clients can only access those servers?
-
@New-PfsenseUser
EDIT:
After looking at these rules the clients wouldn't be able to access anything over the LAN since their source IP is in the 10.100.1.x range and I'm only allowing the LAN NET 192.168.0.x network. So would I change all of those LAN NET's to the VPN Client subnet? Is this correct? -
@New-PfsenseUser said in OpenVPN Firewall Rule Help:
OPT1 -> OpenVPN interface
What's the reason for assinging an interface to the OpenVPN instance?
You're running an access server, correct?
Only one or do you have multiple OpenVPN instances?Note that the OpenVPN rules tab is an interface group including all OpenVPN instances you are running. Rules on this tab are applied to all OpenVPN instances and are prioritized against rules on interface tabs. So if you have a rule in place there which is allowing any to any (wizard default), it will be applied and other rules (on OPT1 tab) will be ignored.
For SMB you may have to allow 137:139 TCP/UDP and 445 TCP. For DNS you have to allow 53 TCP/UDP.
@New-PfsenseUser said in OpenVPN Firewall Rule Help:
I've also setup Client override on a test user account to only allow access to one network.
Consider that you have to controll the access by firewall rules. The network you provide in the CSO does only the push-routes part. But it doesn't prevent the client from creating his own routes and accessing what ever he want.
-
Okay, that makes sense. Also, do you know why a VPN Client wouldn't be able to get to a fileshare on subnet 192.168.1.x /24? The PFSense LAN port is 192.168.0.1 and it hits the other server NIC with IP 192.168.0.5, so there should be an internal local bridge. I even checked the firewall and added a push route for that subnet and still can't even ping it.
-
@New-PfsenseUser said in OpenVPN Firewall Rule Help:
Also, do you know why a VPN Client wouldn't be able to get to a fileshare on subnet 192.168.1.x /24?
Possibly the client uses the same local network range?
To set up 192.168.0.x or 192.168.1.x networks in conjunction with VPN is not a wise decision at all.
-
It's a 2003 Windows Server with 2 NICS, It can talk to the NIC that's connected through a switch to the PFSense, but not the other NIC. If there's a better way, I'm more than happy to go with that. I haven't been able to find anything better with the massive constraints I have for it.
-
@New-PfsenseUser I found my problem with accessing local resources, my test environment was the same local ip the client was on as one of the servers. Unfortunately I can't change this, so I believe I can do either a redirect through the VPN Gateway or figure a way to change either sides IP. Obviously changing the server IP would be best practice since multiple users having to change some of their home networks wouldn't work and server IP's under classful C is not ideal.
-
Going to try the following:
-
Change test local IP and try a fresh setup
-
try the gateway redirect
-
Change automatic NAT to manual while adding the OpenVPN Internal Network
-
Add a static route from the OpenVPN subnet to the LAN Interface IP
-
-
Figured it out on my own, had to reach the pfSense Book, some googling, and testing on a standalone station. Forum was not much help, honestly.
What I did:
-
Put a deny all IPv4+6 right above the default OpenVPN allow any any rule
-
Only permitted the ports needed to allow file sharing and AD authentication (Google them. It should be 135, 137-139, 88, 445, etc. if you have older equipment)
-
I then made an alias for my client IP, Internal IPs I need to manage, and ports for that management. So ports 3389,22,80,443, etc. It's whatever you need for your situation.
-
When making new users for other clients I forced them to a single IP within the Client Specific Override and made sure to allow random ports for concurrent connections
-
Make new users and assign them into groups if they need special access, like IT needs to RDP to a server etc.
-
DO NOT USE THE SAME USER ACCOUNT FOR ALL CLIENTS, you can do this but it's a liability, hard to manage, and have organized logging. If it's just a few people, I can understand it, but for 50-100? make the users or link to an authentication server
That got me up and going for the most part, I had to work with legacy VMWare, so I had to reinvent the wheel with some of the virtual networking/bridging.
TIP:
- Read the pfSense Book first for any questions you have
- Understand the rule processing order
- Group interface rules are in a higher order than your interface rules, so filter the group first, the interface LAN should be filtered afterwards to follow suit.
This is just what I did to fix my problem, I've found decent guides with these links and this documentation... (see below)
https://docs.netgate.com/manuals/pfsense/en/latest/the-pfsense-book.pdf
https://chrislazari.com/pfsense-setting-up-openvpn-on-pfsense-2-4/
https://www.informaticar.net/openvpn-on-pfsense-enable-access-to-the-lan-resources/
keep in mind that the last two links do not highlight security after making it work, that's what the pfSense book is there to provide. Read page 172 and finish that chapter to understand it. Then, like I said, test it yourself and verify your rules work. I wasn't able to find a direct answer for my question and struggles, so I'm hoping this helps someone too. I've attached pictures too because maybe I'm wrong and there's a better way to do it.
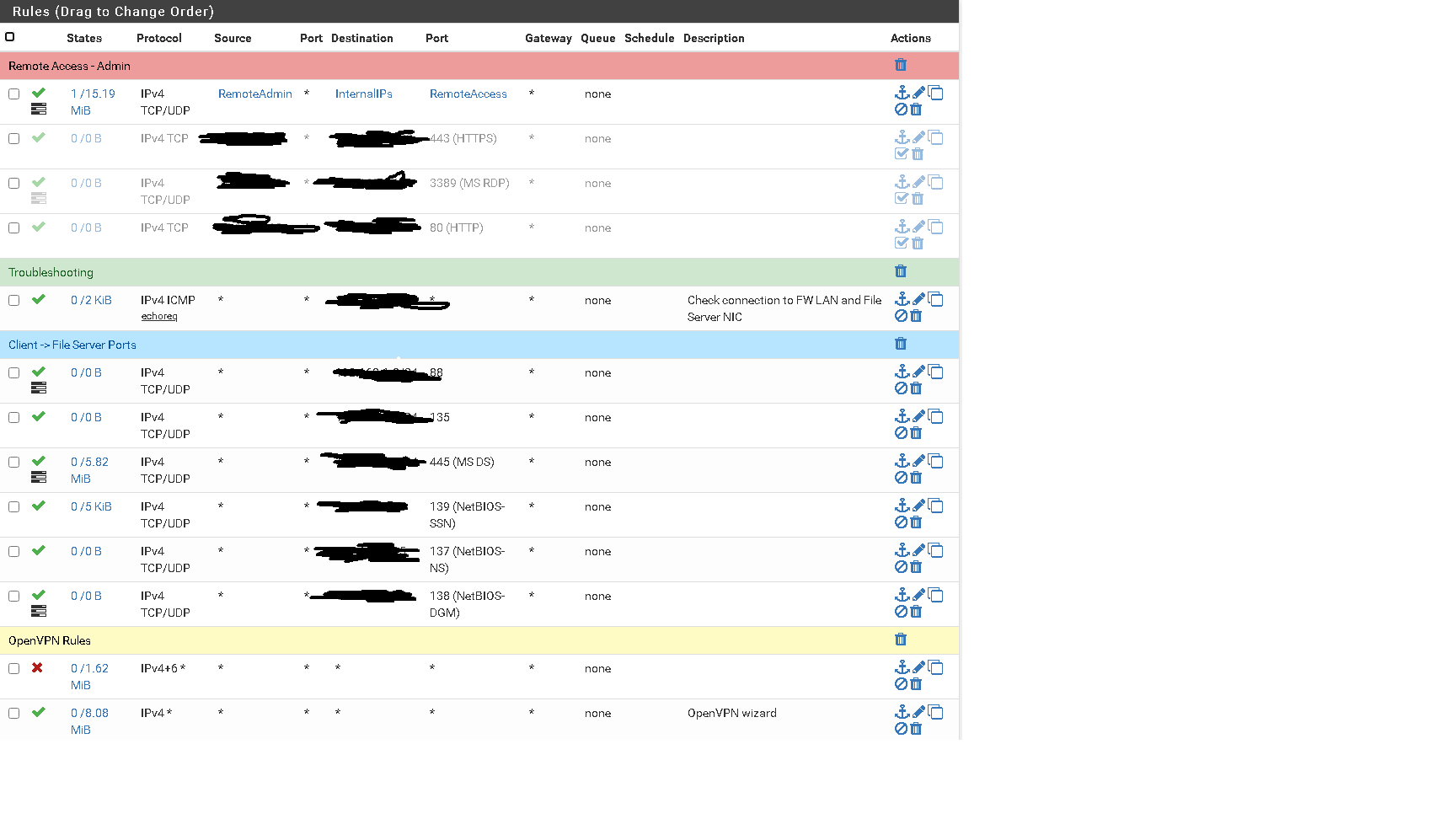
If this is wrong, feel free to correct me and give me a better solution.
Thanks
-