Permissing Routes to Multiple OpenVPN Clients
-
In a network that may reach 30+ openvpn clients running on Tomato, is their a standard practice for routing each client to each other? Essentially each client has a device (IP Phone) at the .2 address. Is it better to create 1 route, like a /18 to cover all the networks and then use rules to allow an alias list of .2 addresses and another rule to block everything else? Or do you create an individual route to each network's phone. Both methods are possible, but which tends to be better for memory resources, troubleshooting, and ongoing maintenance? Thanks.
-
I guess a question that arises with doing something like a /18 route is how to you exclude yourself from being a member of that group?
-
@PGalati There is a setting for that on openvpnserver
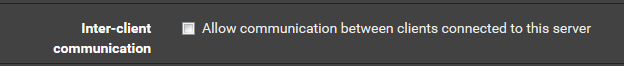
Subnets are older but work in all cases.
A flat network is easier to administer
I dont understand what .2 means for you
clients will get incrementint ip's either in /30 steps of just sequential ip's.Whats the point of concern in a phone network?
A telephone will start poking around other phones?However, if the phones need to communicate with each other, and depending on the configuration. there might be a need to send direct rtp traffic from phone to phone.
-
I am looking to connect a network that has a Cisco CallManager phone system with a phone, 192.168.xxx.2, at multiple locations each connected by openVPN.
192.168.1.0/24 Phone System Network and OpenVPN Server
192.168.10.2 Phone OpenVPN Client
192.168.18.2 Phone OpenVPN Client
192.168.35.2 Phone OpenVPN Client
192.168.46.2 Phone OpenVPN ClientEach phone must be able to send and receive traffic directly for both parties to hear each other. Is it more efficient to create fewer route statements that span multiple subnets or create each route individually? I tested doing some individual push routes and it works but each additional vpn'ed phone requires additional statements to each branch. My concern is for privacy of the rest of the branch, .3-.254. If I route 192.168.1.0/18, 16k addresses, what would be the best method to allow each branch to see everyone's phone at .2, but not have access to the rest of their network? Plus is it possible to make a route statement that will include your local branch but not create a route error.
Thanks
-
@PGalati IMHO routing should be left at minimum needed routes to avoid errors.
Since we are talking networks I assume there is a pfsense in each location right?
A simplefiltering rule at the edge there can fix all your security and privacy concerns. -
The openvpn clients will all be running Tomato firmware and the server is pfsense.
This is the wiki that led me to this question as it only shows an example of 3 networks.
Is there a "classroom preferred" method to scaling up? In the examples in the wiki, routes would be added as additional openvpn clients come online, and I am ok to do that, but does the /18 method save time as more networks come online. Anyone managing lots of openvpn clients care to share their method of building their route structure?
-
Apart from specific iroutes on each client.
If you enable peer 2 peer then routing is done inside vpn server and you cannot control it with pf firewall rules
You could route just the phone ip's but its a bit crude.
I would route /18 and enforce any filtering on the tomato level.