hAproxy hands over client IP to apache2 logs [SOLVED]
-
Did you enable this in the frontend settings? You might need to instruct apache to log it as desired.
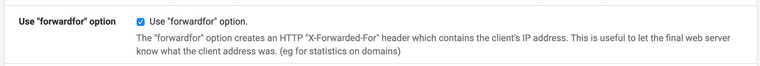
-
yes done that already before the post
now checked again and addedAdvanced pass thru
http-request set-header X-Client-IP %[req.hdr_ip(X-Forwarded-For)]now checking again.
brNP -
@noplan
What you're looking for is called "transparent proxy mode".You can enable it in the backend advanced settings: Transparent ClientIP.
-
Transparent proxy mode is a hack. I would avoid it.
-
@Derelict
What exactly is the drawback of the transparent mode?I'm evaluating HAProxy for my purposes these days and did some tests so far.
The impossibility to distinguish the origin clients IP was a thing which was bothering me. And I had also no luck with the forwardfor option.However, in the meantime I found that the webservers do not take over the clients IP into the log by default, though forwardfor is enabled. The websers logging need to be configured to do that.
-
same here. not gonna use it.
-
The websers logging need to be configured to do that.
true ... any luck ?
and what option on HAproxy did u use ? -
-
thx
im gonna try this asap -
@viragomann said in hAproxy hands over client IP to apache2 logs:
@Derelict
What exactly is the drawback of the transparent mode?I'm evaluating HAProxy for my purposes these days and did some tests so far.
The impossibility to distinguish the origin clients IP was a thing which was bothering me. And I had also no luck with the forwardfor option.However, in the meantime I found that the webservers do not take over the clients IP into the log by default, though forwardfor is enabled. The websers logging need to be configured to do that.
It tries to warn you in the GUI. I have seen it break other things in weird, hard-to-diagnose ways.
WARNING Activating this option will load rules in IPFW and might interfere with CaptivePortal and possibly other services due to the way server return traffic must be 'captured' with a automatically created fwd rule. This also breaks directly accessing the (web)server on the ports configured above. Also a automatic sloppy pf rule is made to allow HAProxy to server traffic.
Workaround exists only by configuring a second port or IP on the destination server for direct access of the website.
Having this option enabled also means that a client on the same subnet as the server wont be able to connect.
Use Client-IP to connect to backend servers. By default, failed health check are logged if server is UP and successful health checks are logged if server is DOWN, so the amount of additional information is limited.
Interface that will connect to the backend server. (this will generally be your LAN or OPT1(dmz) interface)
Connect transparently to the backend server's so the connection seams to come straight from the client ip address. To work properly this requires the reply traffic to pass through pfSense by means of correct routing.
When using IPv6 only routable ip addresses can be used, host names or link-local addresses (FE80) will not work.
(uses the option "source 0.0.0.0 usesrc clientip" or "source ipv6@ usesrc clientip")Note : When this is enabled for any backend HAProxy will run as 'root' instead of chrooting to a lower privileged user, this reduces security in case a vulnerability is found.
-
@Derelict
I have read the warnings and hints, but I'm not able to evaluate the real drawbacks.- CaptivePortal is not in use here.
- Accessing the webserver directly is still possible by split DNS and bypassing HAProxy.
- Slopy rule - don't know, what it really allows. The rule seems to be hidden.
- Running HAProxy as root - this is what I'm a bit worry about.
Anyway, since I've got it made to see the clients IP in the webservers log, there is no need for me to run HAProxy in transparent mode now.
-
i m gonna mark this as solved
cuz first when u r able to read ;)
apache2.conf .... you find this
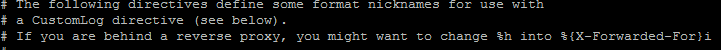
and second you put this in haProxy
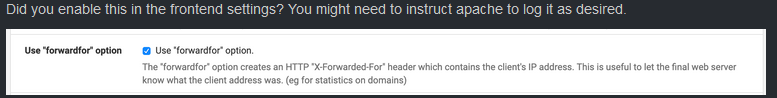
and (for the fun this)
http-request set-header X-Client-IP %[req.hdr_ip(X-Forwarded-For)]!!but be aware as @Derelict mentioned !!

DONE DEAL !
thanx all for the help ... nP -
@noplan said in hAproxy hands over client IP to apache2 logs [SOLVED]:
and second you put this in haProxy
http-request set-header X-Client-IP %[req.hdr_ip(X-Forwarded-For)]

The X-Forward-For header option is just a simple checkbox in haproxy frontend settings as @Derelict illustrated above by a screenshot. -
@viragomann said in hAproxy hands over client IP to apache2 logs [SOLVED]:
@noplan said in hAproxy hands over client IP to apache2 logs [SOLVED]:
and second you put this in haProxy
http-request set-header X-Client-IP %[req.hdr_ip(X-Forwarded-For)]

The X-Forward-For header option is just a simple checkbox in haproxy frontend settings as @Derelict illustrated above by a screenshot.In the first reply to your question.
When you use advanced options like that you remove the ability of the pfSense developers to migrate your configuration as things change in the upstream package.
-
i think not tested yet but on the toDo list
that the problem was that apache log format was not changed.so that either the gui option nor the advanced option
was processed by apache
so next step is to check if its workin without advanced setting.
keep you posted NP