HAproxy prevent sending back correct CN, when not sent.
-
So little back info.. Which I was not aware of until recently.. Because I never actually tried it, and just assumed when wrong CN sent it wouldn't work because of my ACLs and not having a default backend setup, etc.. So thought HArproxy would just send back a 503..
So I have a openvpn instance listening on 443.. And if you hit that and your not an openvpn connection with the correct info (tls key) open just drops you. Which is all good.. But also wanted 443 for my ombi site, my plex users can request stuff.
So using a portshare in openvpn, if its not openvpn traffic, it gets handed over to haproxy via a loopback listening on 9443.. This does the ssl offloading for ombi and gives the remote user a secure https connection to me.. The backend in haproxy talks to the ombi instance via just normally http port.
All good with the world.. Figure hey some bot hitting my IP just randomly on my IP would get back a 503.. And that would be good since they could never actually hit my ombi instance.
But what I found out the other day was hey if you hit https://publicIP - you get back this error.
Connecting to 64.53.x.x:443... connected. WARNING: certificate common name ‘host.domain.tld’ doesn't match requested host name ‘64.53.x.x.’. HTTP request sent, awaiting response... 503 Service Unavailable 2020-08-25 06:09:37 ERROR 503: Service Unavailable.What? That is not good, I don't want to send some bot that info about what cn to use..
Well thought there has to be away to stop that via some ACLs (which I thought I had in place).. So found some stuff (older) talking about another frontend and dummy backend, etc. That seems a little much.. I take it those were old and some really old versions of haproxy.
While I use haproxy, and have done some neat stuff with it, never really had to dive into it because it just did what I asked it to do via the gui. I really only use currently for that one site, in the past I have hosted up a few other things, etc. But never anything fancy or complicated.
Reached out to @PiBa and bob's your uncle, one setting and now get back exactly what I thought would happen.. If you don't send the correct sni, you just get told to F off ;)
Just need to set strict-sni
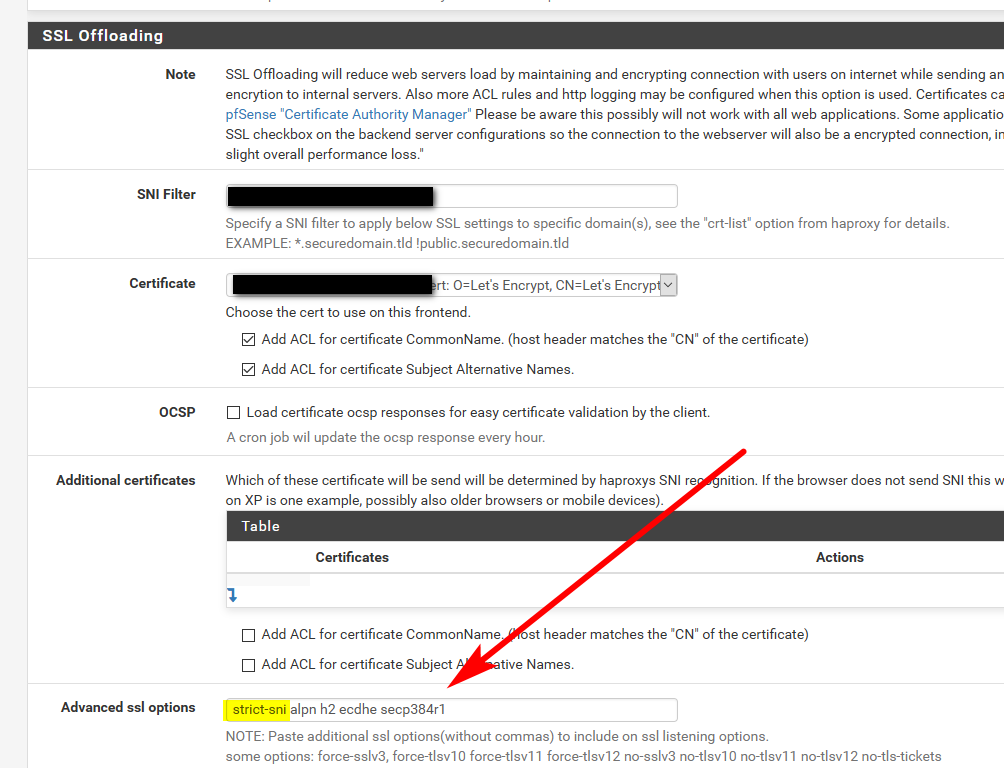
Now if you hit just the IP you get back this.
wget https://64.53.x.x --no-check-certificate --2020-08-28 00:52:05-- https://64.53.x.x/ Connecting to 64.53.x.x:443... connected. OpenSSL: error:14094458:SSL routines:ssl3_read_bytes:tlsv1 unrecognized name Unable to establish SSL connection.Which is what I want to happen - don't have the correct sni, get told to F off ;)
If you send the correct sni, then you get access to login
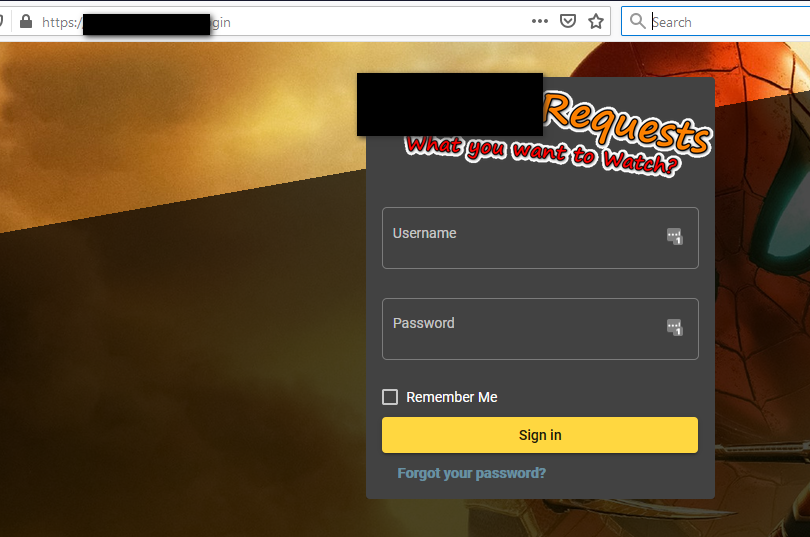
So big thank you to @PiBa posted this info on the chance anyone else wants this to happen on their setups.