understanding firewall rules
-
@JKnott I have crafted an even slicker rule for my IoT known this now.


-
@JKnott said in understanding firewall rules:
didn't see RFC1918 in the available selection.
You have to create your own alias for this.. Its a one time set it and always have it sort of thing..

-
I guess I'll have to set up that alias, though in my application I don't need anything beyond the 172.16.0.0 block. Does having the 3 ranges affect filter performance?
-
Not sure how have a couple extra networks in aliases would affect anything to be honest.. Other than the table that stores them would be bigger ;)
If your not using the other networks, not really going to matter.. But this way if you do happen to throw up a vlan using some other rfc1918 space, you wouldn't need to alter your rules blocking your vlans ;)
To be honest, might not be a nice built in addition.. but then again it takes all of 5 seconds to create - and if built in, users would prob use it wrong anyway ;) heheheh
-
I have created the alias and see I can add it to rules. However, I'm surprised it wasn't already there, given it's a default rule on the WAN interface. However, adding 172.16.0.0 /16 was easy enough.
-
Thank you all for your responses. Let me answer any questions that were directed to me.
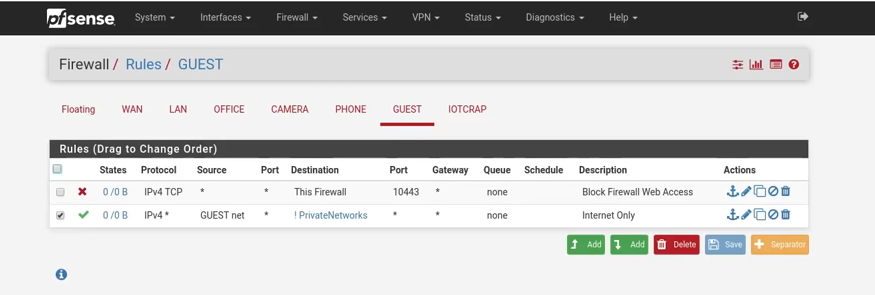
@Gertjan said in understanding firewall rules:The image you showed : the answer depends on what the alias "PrivateNetworks" is.
Probably all -other ? - local networks like 192.168.x.0/24 so this rules allows guest to visit the net.
If "PrivateNetworks" doesn't include the GUEST network then the first rule makes sense.
If it includes the GUEST network, then users couldn't use pfSense's DNS facilities (probably ok for pure DoH fans).
Yes the PrivateNetworks did not include GUEST & IOTCRAP. It included all the other networks that are listed on top -- ie LAN, OFFICE, CAMERA & PHONE@JKnott Thanks for your rules. They make sense. Was the Allow ICMP rule only to make sure that you can connect to the GUEST network in case the internet is not working for the Guest device?
@johnpoz said in understanding firewall rules:
Well his rule below that allows anything that is not rfc1918, or that is what I am guessing from his privatenetworks alias.. Maybe he has multiple Ips on the firewall that are not rfc1918?
No privatenetworks were just his other networks as I mentioned above. I don't think he included the RFC1918 networks. If we include RFC1918 -- would it mean that 2 guest devices won't be able to see each other either?@johnpoz said in understanding firewall rules:
Where did you see that? Also keep in mind many users post up guides and images of how they do stuff without really understand what they are doing ;)
This was a youtube video by Lawrence Systems. Here's the link: https://www.youtube.com/watch?v=ouARr-4chJ8
So from all the replies, I understand that if you include the RFC1918 networks, then you don't need to explicitly create the Block rule for the Web Admin to pfSense. But if the RFC1918 is not included in the alias, then that rule is required in order to explicitly block Guest devices from accessing the pfSense admin.
Thank you all again -- you guys gave me some good tips regarding firewall rules. Much appreciated.
-
Trying to edit my previous post to separate my answers which kind of got included in the quotes. But the forum keeps giving me this error:
ERROR
Post content was flagged as spam by Akismet.comIs post editing not allowed?
-
@Inxsible said in understanding firewall rules:
@JKnott Thanks for your rules. They make sense. Was the Allow ICMP rule only to make sure that you can connect to the GUEST network in case the internet is not working for the Guest device?
That is correct. I like to be able to test things. With my rules it is possible to ping elsewhere on the Internet, but if that fails, where's the problem? With pinging the interface available, I know at least WiFi is working properly and pfSense is up.
-
So that have that same rule on all of their interfaces they were showing.. But if they are only going to have allow rules to specific - like the camera vlan where he only allows access to camera server on 192.168.5.5 it serves no real purpose..
-
@johnpoz said in understanding firewall rules:
So that have that same rule on all of their interfaces they were showing.. But if they are only going to have allow rules to specific - like the camera vlan where he only allows access to camera server on 192.168.5.5 it serves no real purpose..
So I guess the reason they didn't block the RFC1918 address is so that they could allow the CAMERA net to have access to their NVR which was on their internal LAN.
-
I have set up security cameras and the recorders had 2 Ethernet ports, one for the cameras and one for the main network. There is no need to pass the RFC1918 addresses, as there's no reason for them to try to be routed.
-
Huh? The firewall block rule makes no sense in the video because they have no allows that would allow the access. They only have a single allow rule that allows access to the 192.168.5.5 address.
There is no point in creating block rules, unless you are putting them above a rule that would allow access because its wider open.. default is deny..
There is no point in creating more block rules, when that is default - the only time you need to block something is if you have a rule that would allow it because its an more open allow then you want.