What do your firewall rules look like?
-
@Raffi_ Yeah, those are automatically created rules for my NAT redirect on those ports. The firewall rules are granting access to the instance of the service running on "localhost" (see picture). So with DNS and NTP running on localhost on pfsense in addition to the guest and LAN interfaces if someone tries to exit their subnet on those ports it will be redirected to localhost on the firewall rather than exiting the network. For example, if you have 9.9.9.9 setup as your DNS provider on your laptop and were on my guest network it will use my DNS instead of quad9 and you will never know. This lets me do filtering for phishing using a blocklist in DNSBL, although it's really a reactive way to do it but I cant find a better way without spending a bunch of money.
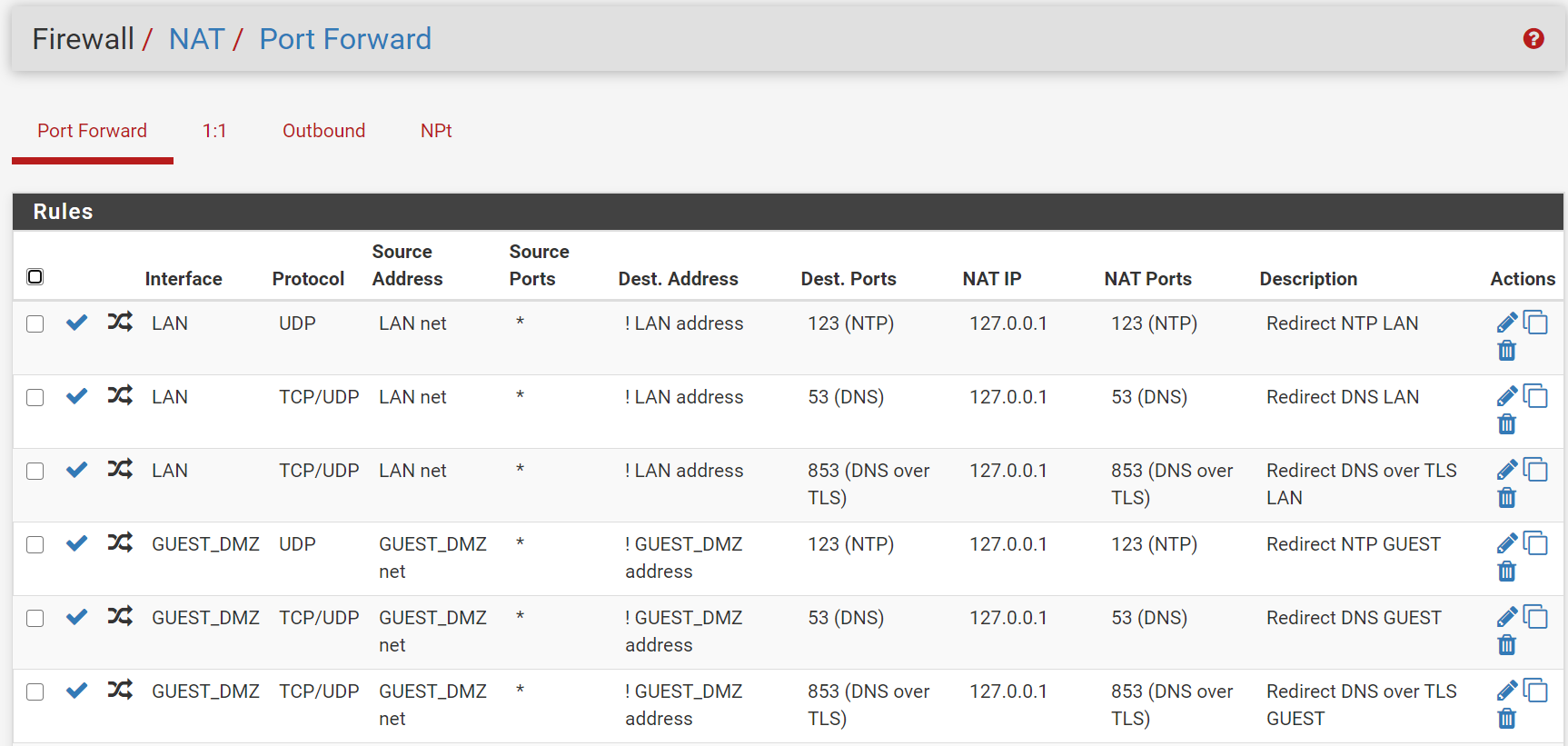
-
Ahh ok, cool. I probably should be doing something similar.
-
@Raffi_ For this to work you might also need to block use-application-dns.net in your DNS server to prevent DNS-over-HTTPS (DoH) from accidentally bypassing your DNS server. I feel trying to stop DoH entirely is futile, but preventing the accidental bypass like this is easy. This can easily be done in DNSBL or you can create a custom zone in your DNS advanced settings like below.
server: local-zone: "use-application-dns.net" always_nxdomainhttps://support.mozilla.org/en-US/kb/canary-domain-use-application-dnsnet
EDIT: Updated local-zone to always_nxdomain
-
If you have a number of interfaces/VLANs, you can put them into an interface group and reduce your port forward entries for DNS and NTP. Then also, just a single rule in each of the two interface groups to pass the translated traffic, rather than having them duplicated in every interface (or choose the "Pass" option for the associated rule).
ps. thanks @ex1580 for raising 853 (DNS over TLS), I need to look into that! Even more reason to consider using interface groups for this.
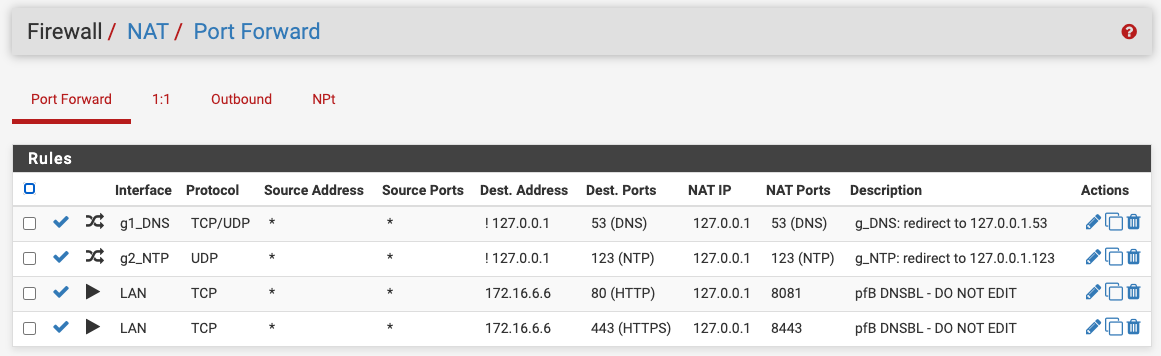
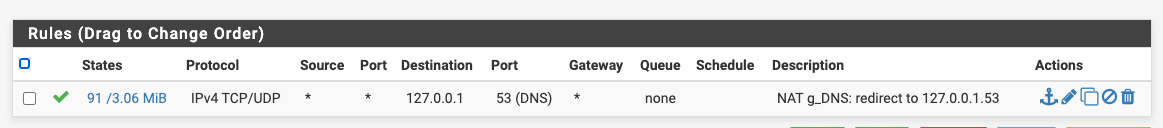
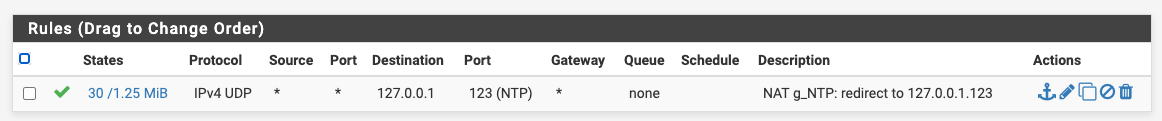
-
@ex1580 said in What do your firewall rules look like?:
@Raffi_ For this to work you might also need to block use-application-dns.net in your DNS server to prevent DNS-over-HTTPS (DoH) from accidentally bypassing your DNS server. I feel trying to stop DoH entirely is futile, but preventing the accidental bypass like this is easy. This can easily be done in DNSBL or you can create a custom zone in your DNS advanced settings like below.
server: local-zone: "use-application-dns.net" redirect local-data: "use-application-dns.net A 0.0.0.0"https://support.mozilla.org/en-US/kb/canary-domain-use-application-dnsnet
I think I already have the prevent firefox DoH option in pfblocker. That is the main one I'm concerned with since it does that by default.
-
@billl Thanks! I looked into the groups when you first mentioned it and will keep it in mind next time I redo my rules! I didnt jump on it right way as it would be a big change from my rules for each interface. Looks nice though.
-
@ex1580 said in What do your firewall rules look like?:
server:
local-zone: "use-application-dns.net" redirect
local-data: "use-application-dns.net A 0.0.0.0"With blind trust, I have been using @jimp's recommendation of:
local-zone: "use-application-dns.net" always_nxdomain
though I have also seen @johnpoz using:
local-zone: "use-application-dns.net" staticDoes it not matter what the parameter is, as long as it is not NOERROR?
I'm curious about your local-data setting:
local-data: "use-application-dns.net A 0.0.0.0"
I haven't seen that one before .. -
I am currently using
local-zone: "use-application-dns.net" always_nxdomain
This needs to return NX.. So this is the easiest method to do that.
-
Thanks @johnpoz ! NXDOMAIN is the optimal response however their website lists a few other options. I will update my documentation now. https://support.mozilla.org/en-US/kb/canary-domain-use-application-dnsnet
-
Are any of you using a port alias to filter outbound ports? I find that for incoming traffic it's a no-brainer to filter protocol, ports, and even geoip but outgoing is another story.
I was looking around at port filtering recommendations and while I believe that it depends on what you need, and if I was being paid to do this at home and for friends and family would certainly track down every device and app, I see people posting things like "80, 443, and 21 are all you need outbound" which I find laughable. If I did that at home I think most of my stuff would stop working (but at least I would have a web browser to search for why).
I recently got around to adding a "allowed_ports_outbound" alias to my rules that allow internet access (this is a default deny scenario) and I feel like once you get above port 1000 it's the wild west as far as each app and service wanting it's own thing. Take for instance if I wanted to allow Zoom, Google Meet, and Skype. Sure 80, and 443 are the base requirement but give them an inch and next thing you know they want TCP nearly everything (looking at you Skype). That doesnt even take into account smart devices.
So, as I was going from "allow all ports" to something which will make no difference but may someday make it easier to block a port, I decided to carefully filter below 1000 then not so much above that number, just knocking out a chunk of IRC in the 666X range per SANS recommendations. It's been good so far! What are you doing?
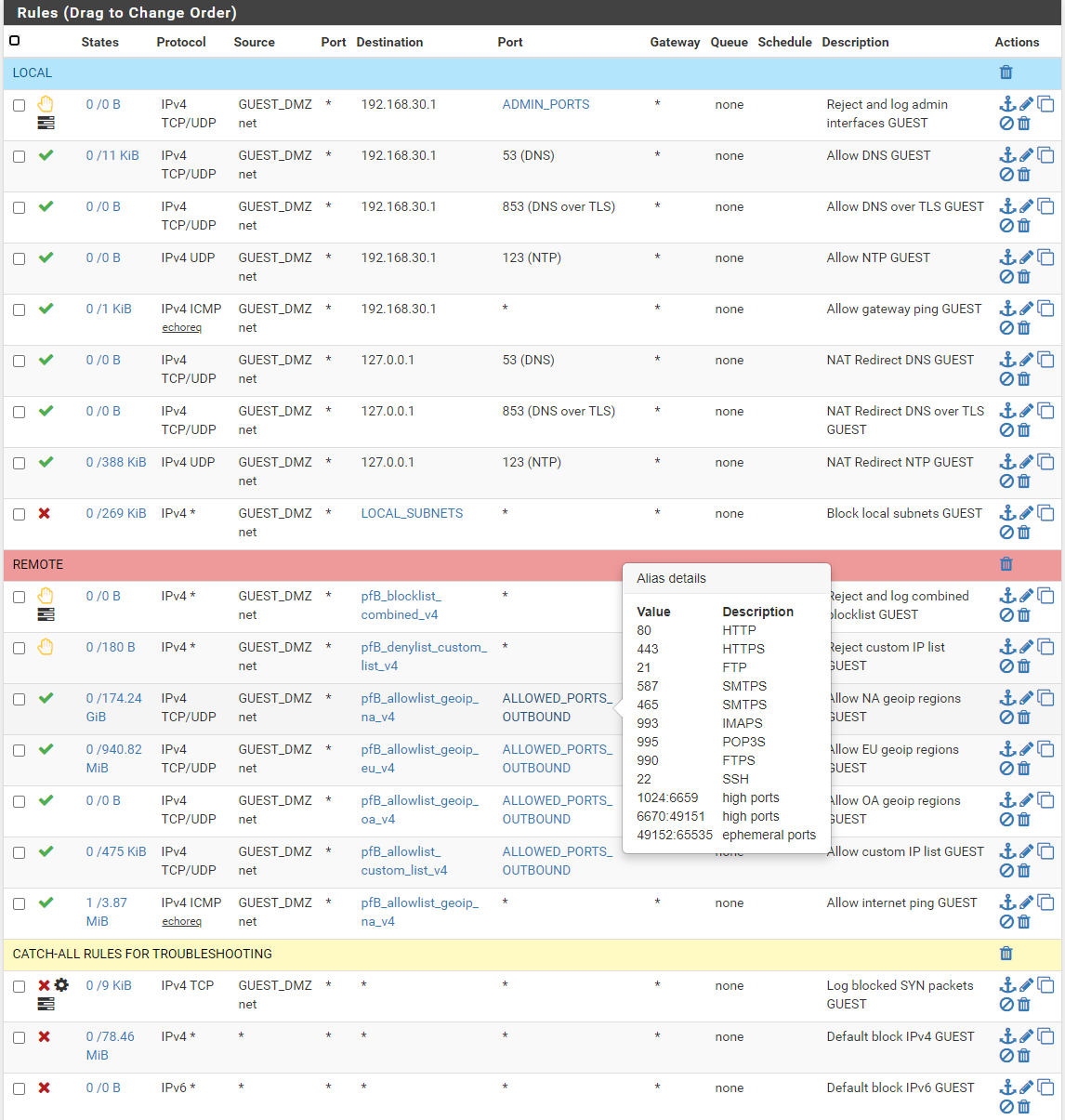
-
@ex1580 yeah, I think you'd go crazy trying to keep track above 1024.
Thanks for the tip about 666X - I need to look into that!Here are my rules for a standard user device VLAN:
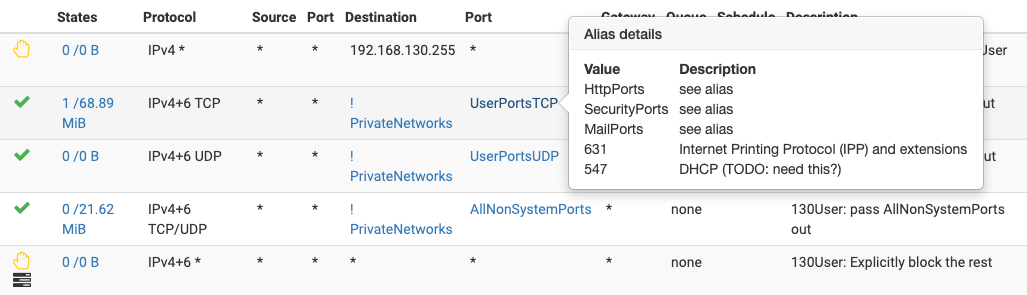
and here are my rules for the VLAN I use for work:
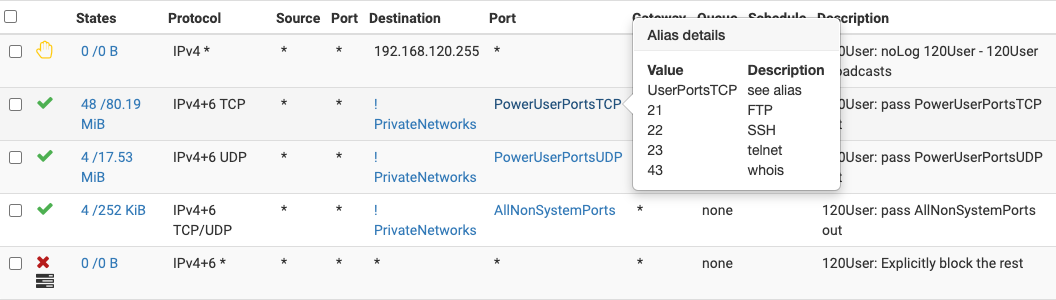
-
@billl Looks good, thanks for sharing! In regard to your TCP port 547 for DHCPv6 this may be helpful (replace with your management address of course): https://192.168.0.1/status.php#FirewallpfFirewallRules
-
You don't need any rules for dhcp.. They are auto enabled when you enable dhcp and are hidden.
-