How to restrict OpenVPN traffic
-
Any further thoughts?
-
@qwaven said in How to restrict OpenVPN traffic:
In regards to floating rules. There is likely something else going on with the firewall. I had a previous issue where NAT redirects would not work until I created a floating rule. I never got an answer to why but I suspect the same reason is why I needed to create floating rules for OpenVPN.
Then you have bigger issues. There's no reason why some NAT redirect would require a floating rule.
I disabled the automatically generated openvpn rule found on the WAN interface. (as it was doing nothing)
Em.. yes it is. It allows access to the OpenVPN server from the internet? If you don't have that one, how the hell should one connect to your OVPN Server on pfSense from the outside world?
I created basically a copy of it but as a floating rule
you shouldn't. That's bonkers. The rule was created there for a reason (by the wizard I assume).
tcpv4, any source, any port, dest WAN Address, port 1194 (OpenVPN), ...rest are default/empty
Why TCP? OVPN is UDP by default.
Without showing screenshots of your configuration, there'll be nothing we can do to help rather then guessing as you don't provide that much intel about your configuration, setup and rules.
I'd need at least
- WAN Interface config
- Interface assignment (do you have OVPN interfaces assigned)
- NAT - Port Fordwards, Outbound NATs and 1:1 NATs to narrow down problems
- Rules - Rules from Float, WAN, OpenVPN & if you have an ovpn interface assigned that one too
- OVPN server configuration
I think that's it. Without that, all other help is like reading a magic-8-ball. :)
Cheers
\jensEdit:
When I tried to create one. The firewall seems to have treated it as the main LAN interface and put the anti lockout rules there. ??
I removed it. Created a dummy interface called LAN. The same anti lockout rules were added.
I created, again the VPN interface, no anti lockout this time.
I read that only after I sent my message. WTF? You don't have a LAN configured? You only have a WAN? You said earlier in the thread, that pfSense is your only router. So how are you running a "router" of any kind, if you didn't have a LAN setup before and your WAN was the only interface? What are you trying to build here? No wonder you had problems with redirects and such, if you didn't have a LAN configured. There's some red bold help text that reads "without having a LAN, pfSense is NOT ROUTING anything". So by adding the VPN interface you activated routing mode for the first time. Before PF was NOT active at all as there was no second interface to route with. So it's no wonder you have that all configured backwards.
Are you trying to setup pfSense as a VPN-Gateway kind of thing like your own external VPN access provider? Then you'd have to go a slightly different route to set it up in the first place. The "dummy"-LAN isn't such a bad idea then after all, but that kinda setup needs a bit more fine-tuning. It's possible but not "run out of the box" kind of easy.
-
Hi JeGr,
Thanks for the reply.
Yes it does seem like there is something else not working properly with the firewall rules. I never was able to understand why my PFSense is acting this way. Previously I had tried to open ports w/ NAT to two identical servers and was never able to get that working with the auto generated rules. Currently they are working fine with either NAT Pass (no rule) or floating rules. ---but this is kinda a different topic.
Same result appears to be for the OpenVPN rules. The one that was created automatically on the WAN interface does not appear to ever be used.
Just for the sake of argument I went and disabled my floating rule, and enabled the auto generated rule.
Result:
I can no longer connect to my OpenVPN server at all.Disable the auto generated rule, enable the floating rule
Result:
Immediately I am able to connect to my OpenVPN server (but I cannot do anything)There was a typo. I meant IPv4 not TCPv4. Basically allowing anything except IPv6.
The rules:
Floating:
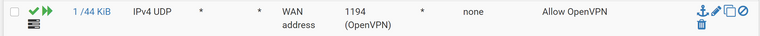
Auto generated (currently disabled):
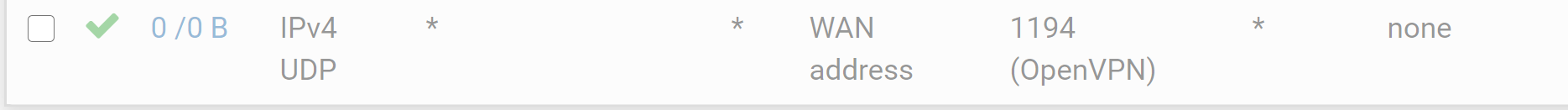
So I'm going to try and clarify the interfaces I have next.
I do have a LAN, several actually.
WAN: PPPoE connection
LAN: This is the dummy one I just created. Assigned it a dummy IP also.
5 other interfaces that connect to various other active networks (internal) <-- these would be treated as LAN
I then have OpenVPN we'll call them A and B
Interface A, this is a VPN I used to use to connect out to a third party provider. I would use a redirection rule for some traffic to use this as the gateway. It worked fine before. Currently that gateway is disabled.
Interface B, this is the newly created interface. Recall, before creating this I could at least reach Google from my new VPN config. Since adding I cannot do anything at all other than connect.Hopefully that ^ explains, if not let me know.
Nat rules:
Under port forward I just have the two rules for the two servers I mentioned at the top of this post. They do not have anything to do with OpenVPN and will omit.
1:1 rules = nothing there
Outbound:
Hybrid Outbound NAT rule generation.
(Automatic Outbound NAT + rules below)Then I see rules like this, one for each network. There are also some for the redirection/gateway created for OpenVPN interface A.

Then for automatic rules there is the typical ones
Interface WAN, source of all my internal networks, source port any destination any port 500 NAT Address is my WAN address - auto created rule ISAKMP...
Interface WAN, source of all my internal networks, source port any destination any port any NAT Address is my WAN address - auto created rule...OpenVPN Config
Under Servers I just have the one were trying to get working.
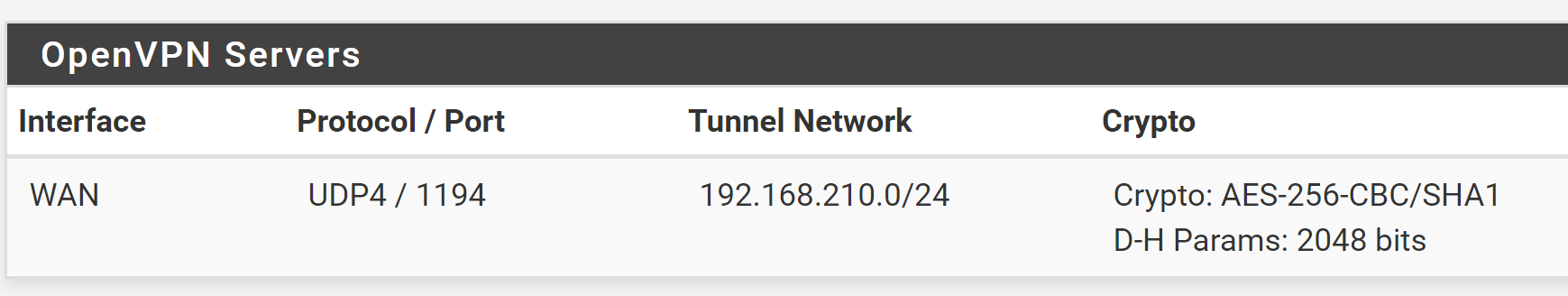
As the openvpn server config page is quite large I will try and list just want I have set.
auth is backend local database, over udp, using tun layer 3. Is on my WAN interface with the default port 1194
I have TLS with TLS authentication
I am using a local CA+certificate on PFSense.
I have a tunnel network set, same as the one listed in the screenshot above.
Nothing for IPv6 (I do not use IPv6)
Redirect IPv4 gateway is checked to Force all client-generated IPv4 traffic through the tunnel.
Under client settings I have:

Advanced client:
I provide some public DNS servers, nothing else setAdvancecd:
Hopefully I got it all, if I missed something let me know.
Cheers!
-
OK I'm trying to see that through from the top.
WAN PPPoE
LAN dummy
5 other interfacesWere those interfaces there when you set the system up or did they come later on? As said if you install pfSense without a LAN first, pf doesn't work. Only after adding the lan (that is internally called lan, not optX) is routing and firewalling really enabled!
Before I go deeper in your post with details about OVPN or others: could you show me the interface assignment screen and how wan/lan are configured? I somehow sense a deeper problem in the whole setup if all parts like the filtering, rules, nat etc. behave THAT strange :)
Also did you configure anything in System>Advanced in Firewall&NAT section especially?
-
@JeGr said in How to restrict OpenVPN traffic:
OK I'm trying to see that through from the top.
WAN PPPoE
LAN dummy
5 other interfacesWere those interfaces there when you set the system up or did they come later on? As said if you install pfSense without a LAN first, pf doesn't work. Only after adding the lan (that is internally called lan, not optX) is routing and firewalling really enabled!
Before I go deeper in your post with details about OVPN or others: could you show me the interface assignment screen and how wan/lan are configured? I somehow sense a deeper problem in the whole setup if all parts like the filtering, rules, nat etc. behave THAT strange :)
Also did you configure anything in System>Advanced in Firewall&NAT section especially?
I honestly cannot recall how the interfaces originally were created. It has been operating fine otherwise mostly for quite some time.
My guess is that I setup a very basic PFSense WAN/LAN setup.
Created the other interfaces
Removed the LAN interface once it was working as I did not require it.Interfaces
Note: re added this with more information...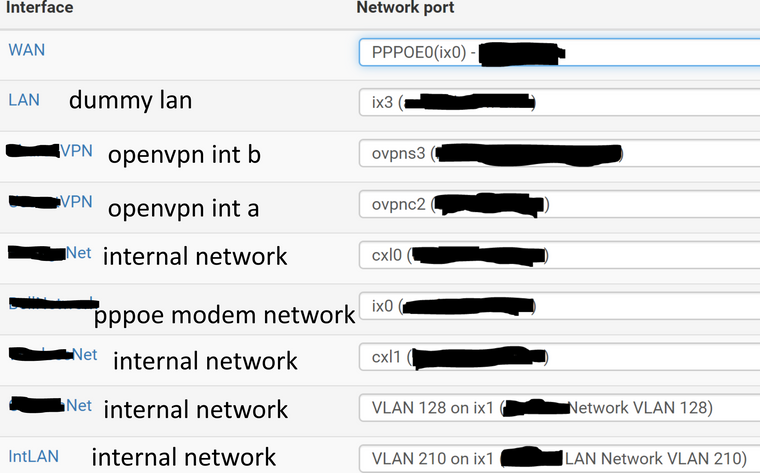
Firewall & Nat
Taking a look at the Firewall & Nat page I am not really seeing anything that stands out as 'modified' with the exception of perhaps the NAT section since I am using hybrid.I will post a few screenshots
The rest is all blank.
Cheers!
-
Any further input?
Cheers!
-
sorry, currently away from home and in project, hope I can jump back in next week, but anyone else may jump in anytime!
-
@JeGr said in How to restrict OpenVPN traffic:
sorry, currently away from home and in project, hope I can jump back in next week, but anyone else may jump in anytime!
Ok no problem, thanks for the reply.
Let me know if you have any thoughts when your able.
Cheers!
-
That screenshot with your interface names and MAC addresses all masked out is really gonna hurt us when it comes to helping you with your posted problem. None of that is "super secret proprietary data" that anybody can do anything with.
-
It's more that I did not want some of the naming / descriptions public, none of which should matter for troubleshooting.
Cheers!