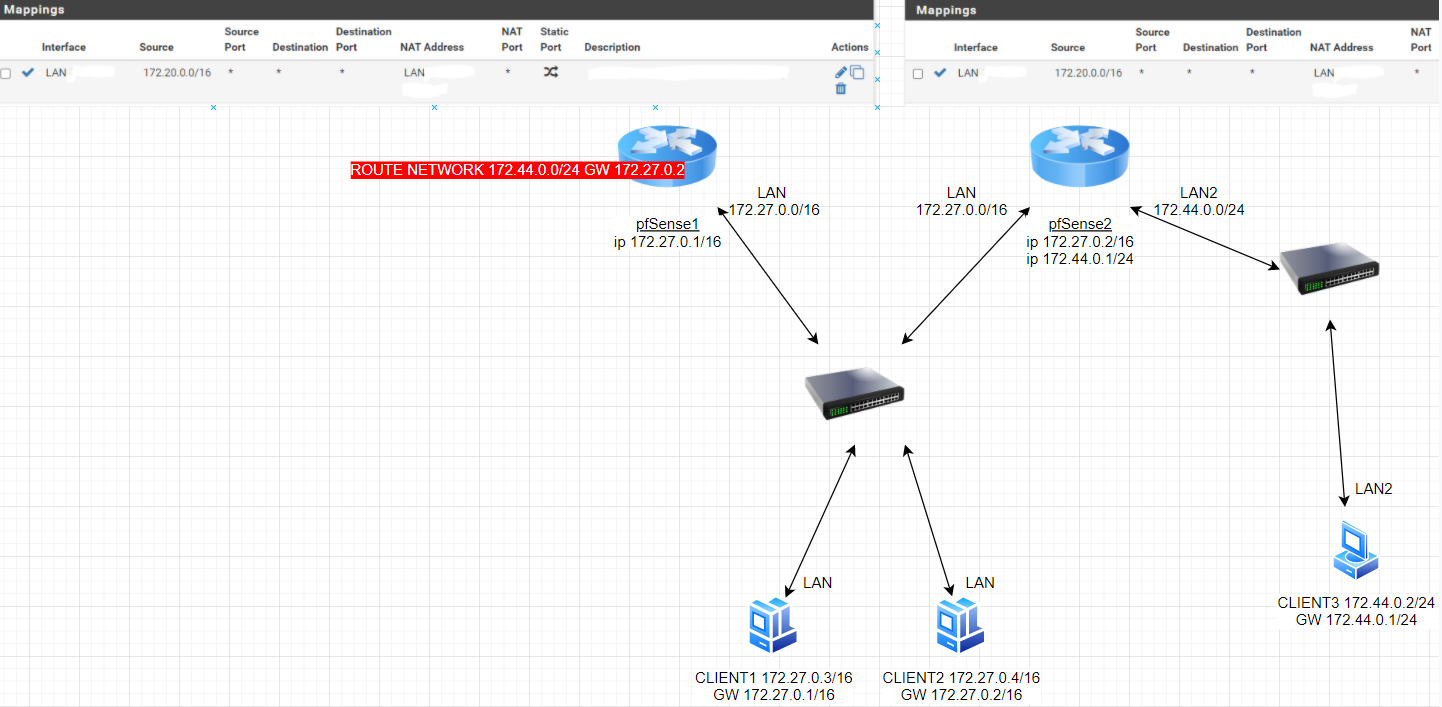
routing tra 2 pfsense
-
mi verrebbe da dire che la connessione risulta asimmetrica
avrei creato una rete di transito /30 e messo una rotta statica da una parte e dall'altra sinceramente
se lo vede @johnpoz magari...
what do you think? borked?
-
Without any translation I can tell you that putting hosts on what is clearly a transit network this 172.27/16 is going to end up in asymmetrical traffic flow.
So unless that pfs2 is natting. And doing port forwarding. Starting to talk to 172.44.anything is going to be problematic for that box talking to pfs1 as its gateway.
But yeah my first impression of such a drawing is borked..
Here is proper way to do that.
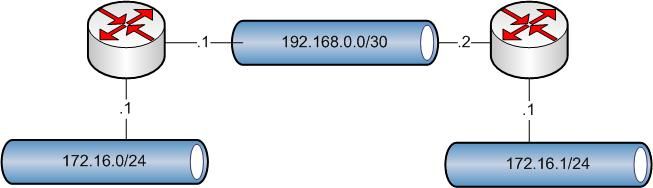
Also where did you come up with 172.44? That is not rfc1918 space.. I doubt your T-Mobile who owns 172.32.0.0/11
Also use realistic network sizes.. /16 You have anywhere near 65k hosts on your transit network there? A /16 never belongs on an interface. It is a route summary mask, or a rule on a firewall. Or a subnet you assign to a location or building or department. You would never use a /16 for an actual network segment
-
grazie per le risposte e i suggerimenti !!!
nel caso avessi anche un terzo pfSense (pfSense3) che fa da server OpenVpn per raggiungere le reti presenti negli altri pfSense, come consigliate il collegamento? -
allo stesso modo, creando un'altra rete di transito e aggiungendo le opportune rotte
-
@kiokoman per la rete di transito non posso usare sempre la stessa?
-
eh no, ma nn e' che di indirizzi ip ne manchino, crei una interfaccia vlan se non hai schede di rete libere e la sfrutti per creare una rete di transito, come ti ha suggerito johnpoz una la fai 192.168.0.0/30 e l'altra 192.168.1.0/30 senza dimenticarti di creare le regole di firewall che permettano il traffico
-
@kiokoman praticamente ogni pfSense se deve fare da router va creata una rete di transito diversa, in modo da non avere 2 gateway pfSense sulla stessa rete .....giusto?
se però ho il caso che un pfSense deve fare solo da proxy squid (devo disattivare in qualche modo la funzione routing) potrebbe stare sulla stessa rete con un altro pfSense che fa da router? -
si, se disattivi il routing si
-
@kiokoman qual'è il modo migliore per disattivare il routing sul pfSense che fa solo da proxy?
-
mai fatto personalmente ma in giro ci sono delle guide
https://support.adamnet.works/t/running-on-a-transparent-pfsense-bridge/79
https://www.reddit.com/r/PFSENSE/comments/6eia7h/pfsense_squid_in_transparent_mode_on_bridge/ -
@kiokoman se il terzo pfSense è un server OpenVpn e i client vpn 172.29.0.0/16 devono raggiungere 172.27.0.0/16 e 172.24.0.0/24 creando le regole di firewall che permettano il traffico, qual'è la configurazione corretta?
Con questa per raggiungere 172.24.0.0/24 devo passare per le 2 reti di transito, se il pfSense1 fosse offline non raggiungo 172.24.0.0/24 del pfSense2:
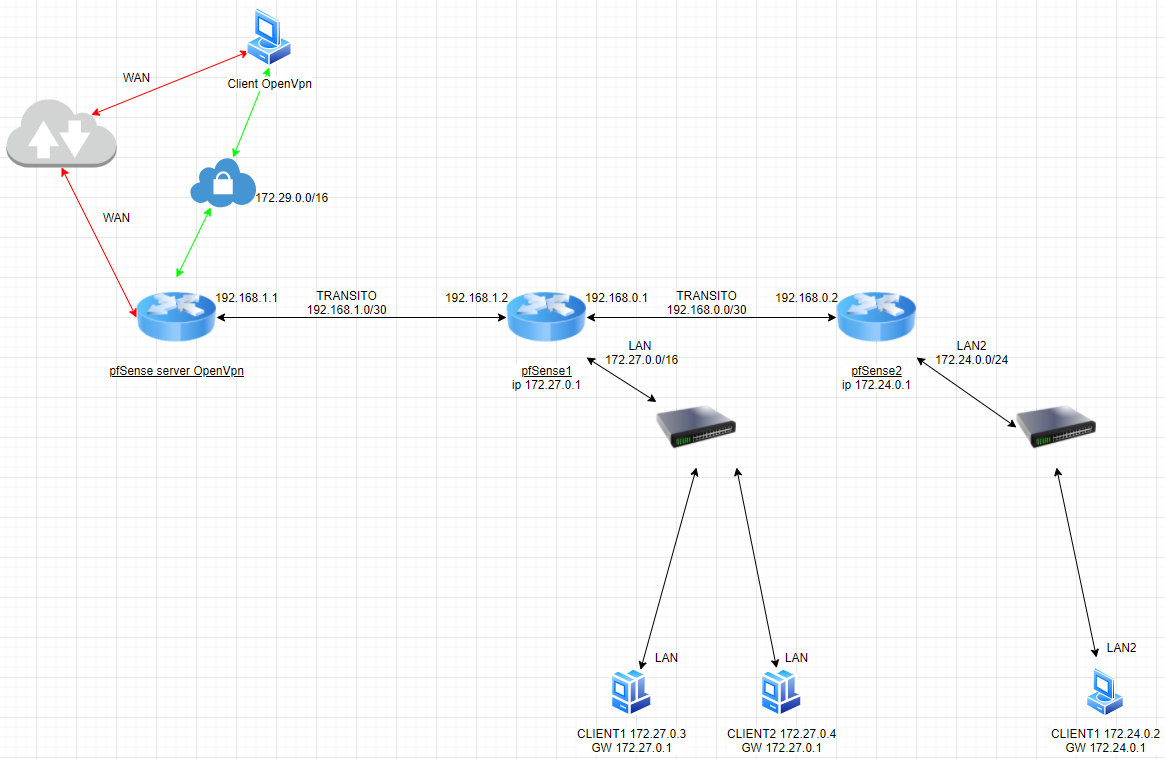
mentre in questo caso da client vpn per raggiungere 172.27.0.0/16 e 172.24.0.0/24 dovrei passare solo sul pfSense interessato:
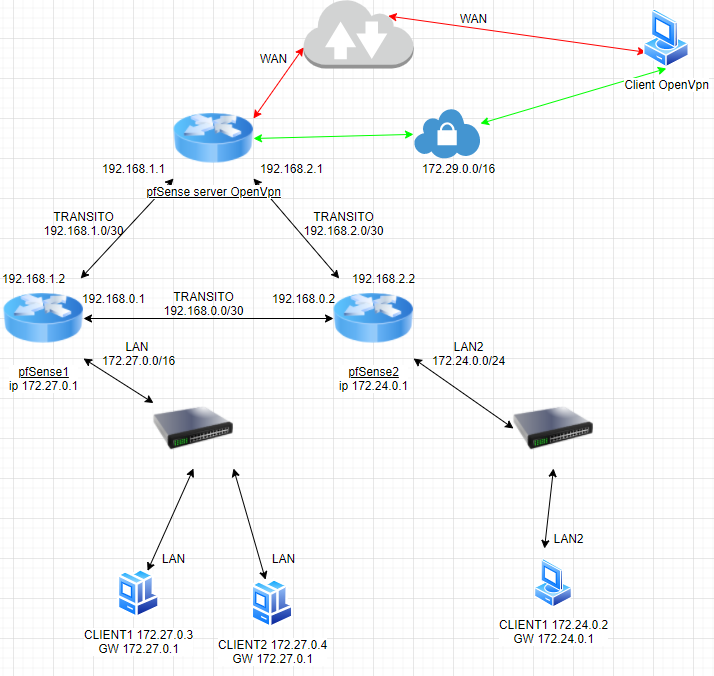
Grazie dell'aiuto
-
esatto, nel primo caso se pfsense1 non fosse funzioante/raggiungibile non lo sarebbe neanche il pfsense2
il secondo schema secondo me è buono
@johnpoz i think the second drawing is good, what do you think? -
Yeah that looks more normal.. I still don't get why added a 3rd pfsense?
Or why the 2 downstream ones, when you could get by with just the 1 pfsense router that is labeled as the openvpn one..
why can you not just hang these two networks 172.27/16 ad 172.24.0/24 off the 1 pfsense router?
I prob missing quite a bit since don't read Italian ;)
172.29/16 is a very large tunnel network - guess your planning on lots of concurrent connections?
And if going to set it up like that, hope not natting at those 2 downstream pfsenses
-
@johnpoz ho bisogno di 2 pfSense perchè fanno anche da proxy "squid" con autenticazione windows active directory per i 2 domini della lan e lan2, il terzo pfSense volevo dedicarlo solo alla OpenVpn;
in questo modo in caso di manutenzione del pfSense1 o pfSense2 almeno una rete resta online.Per il tunnel vpn al massimo ho 50 client quindi posso mettere /24.
""And if going to set it up like that, hope not natting at those 2 downstream pfsenses""
cosa vuoi dire?grazie
-
che ti ritroveresti con una doppia nat ma non so a quali inconveniente andresti in contro sinceramente, se configurato correttamente non vedo problemi...
lui dice che potresti comunque mettere tutto sul primo pfsense e un secondo pfsense lo potresti usare come backup per https://docs.netgate.com/pfsense/en/latest/highavailability/index.html