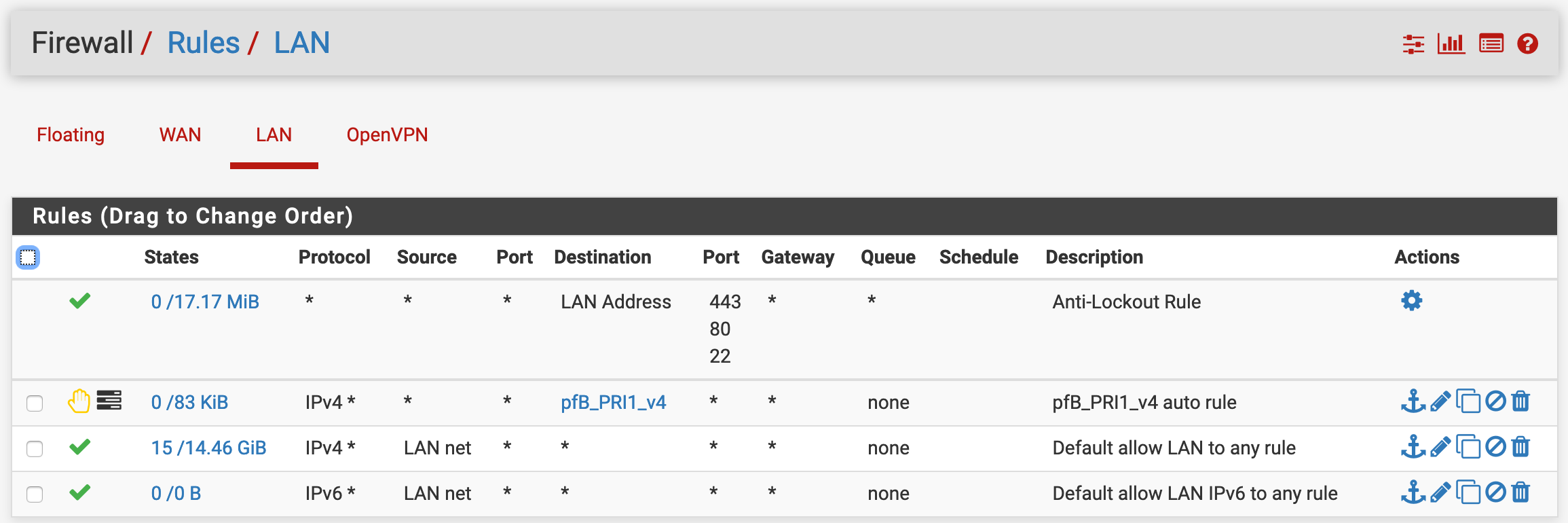
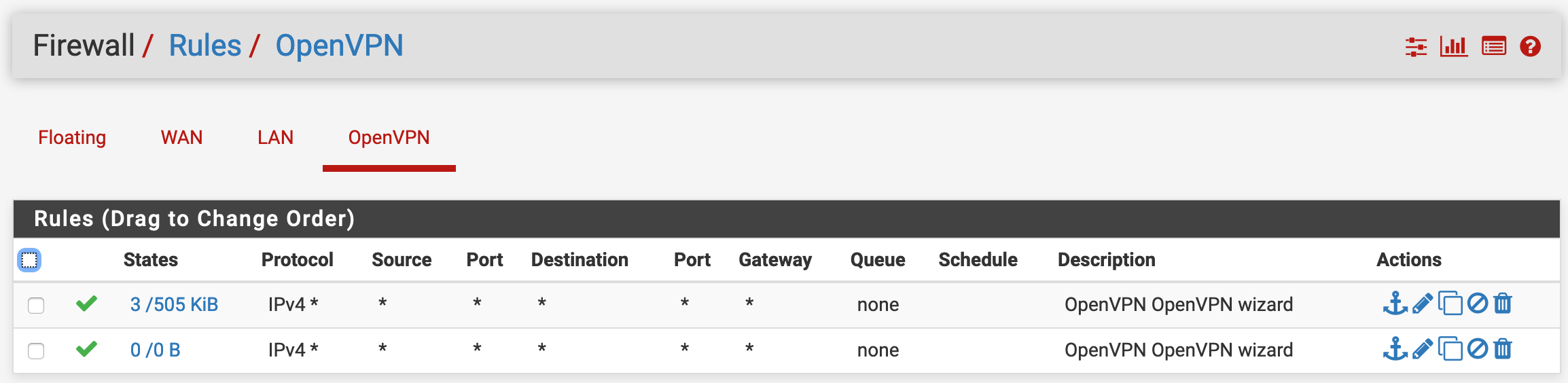
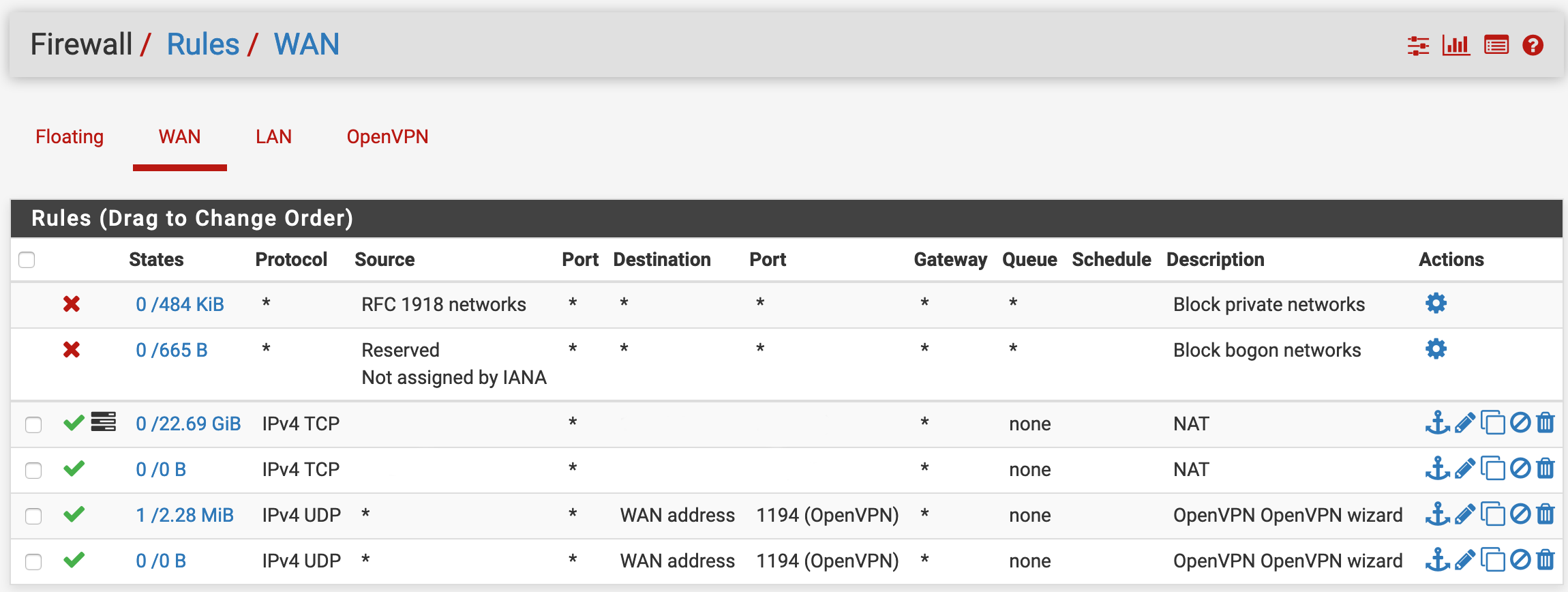
Cannot access LAN resources
-
I have been struggling with OpenVPN setup for a few days now. Clients can successfully connect to VPN and ping pfSense and access Web GUI but cannot ping or otherwise access LAN devices. After many hours of googling and trial error, it still does not work.
Any help is highly appreciated and I'm happy to provide more details if needed! TIA.
My setup is:
OpenVPN server at pfSense (10.0.0.1) which is ESXi VM.
LAN network 10.0.0.0/8
VPN tunnel is 10.0.8.0/24
Firewall rules generated by OpenVPN wizard (screenshots below)
Clients: Mac OS 10.15 and Android 10. Both using OpenVPN ConnectServer config:
dev ovpns1
verb 1
dev-type tun
dev-node /dev/tun1
writepid /var/run/openvpn_server1.pid
#user nobody
#group nobody
script-security 3
daemon
keepalive 10 60
ping-timer-rem
persist-tun
persist-key
proto udp4
cipher AES-128-CBC
auth SHA256
up /usr/local/sbin/ovpn-linkup
down /usr/local/sbin/ovpn-linkdown
client-connect /usr/local/sbin/openvpn.attributes.sh
client-disconnect /usr/local/sbin/openvpn.attributes.sh
local pfsensewanip
tls-server
server 10.0.8.0 255.255.255.0
client-config-dir /var/etc/openvpn-csc/server1
verify-client-cert none
username-as-common-name
plugin /usr/local/lib/openvpn/plugins/openvpn-plugin-auth-script.so /usr/local/sbin/ovpn_auth_verify_async user TG9jYWwgRGF0YWJhc2U= false server1 1194
tls-verify "/usr/local/sbin/ovpn_auth_verify tls 'OpenVPN-Cert' 1"
lport 1194
management /var/etc/openvpn/server1.sock unix
push "route 10.0.0.0 255.0.0.0"
push "dhcp-option DNS 10.0.0.1"
ca /var/etc/openvpn/server1.ca
cert /var/etc/openvpn/server1.cert
key /var/etc/openvpn/server1.key
dh /etc/dh-parameters.2048
tls-auth /var/etc/openvpn/server1.tls-auth 0
ncp-ciphers AES-128-GCM
persist-remote-ip
float
topology subnet
Client config (created by client export utility)
dev tun
persist-tun
persist-key
cipher AES-128-CBC
ncp-ciphers AES-128-GCM
auth SHA256
tls-client
client
resolv-retry infinite
remote pfsensewanip 1194 udp4
auth-user-pass
remote-cert-tls server
Routes on Mac OS
➜ ~ netstat -nr
Routing tablesInternet:
Destination Gateway Flags Netif Expire
default 192.168.43.71 UGSc en0
10 10.0.8.1 UGSc utun2
10.0.8/24 10.0.8.2 UGSc utun2
10.0.8.1 10.0.8.2 UH utun2
127 127.0.0.1 UCS lo0
127.0.0.1 127.0.0.1 UH lo0
169.254 link#5 UCS en0 !
192.168.43 link#5 UCS en0 !
192.168.43.71/32 link#5 UCS en0 !
192.168.43.71 dc 34:c9:e6:6c UHLWIir en0 1199
34:c9:e6:6c UHLWIir en0 1199
192.168.43.151/32 link#5 UCS en0 !
224.0.0/4 link#5 UmCS en0 !
224.0.0.251 1:0:5e:0:0:fb UHmLWI en0
255.255.255.255/32 link#5 UCS en0 !
OpenVPN Connect log
29/09/2020, 13:06:03 OpenVPN core 3.git::3e56f9a6 mac x86_64 64-bit built on Aug 25 2020 18:39:33
⏎29/09/2020, 13:06:03 EVENT: RESOLVE ⏎29/09/2020, 13:06:03 Frame=512/2048/512 mssfix-ctrl=1250
⏎29/09/2020, 13:06:03 UNUSED OPTIONS
1 [persist-tun]
2 [persist-key]
4 [ncp-ciphers] [AES-128-GCM]
6 [tls-client]
8 [resolv-retry] [infinite]
⏎29/09/2020, 13:06:03 Contacting pfsensewanip:1194 via UDP
⏎29/09/2020, 13:06:03 EVENT: WAIT ⏎29/09/2020, 13:06:03 UnixCommandAgent: transmitting bypass route to /var/run/agent_ovpnconnect.sock
{
"host" : "pfsensewanip",
"ipv6" : false,
"pid" : 7749
}⏎29/09/2020, 13:06:03 Connecting to [pfsensewanip]:1194 (pfsensewanip) via UDPv4
⏎29/09/2020, 13:06:03 EVENT: CONNECTING ⏎29/09/2020, 13:06:03 Tunnel Options:V4,dev-type tun,link-mtu 1569,tun-mtu 1500,proto UDPv4,keydir 1,cipher AES-128-CBC,auth SHA256,keysize 128,tls-auth,key-method 2,tls-client
⏎29/09/2020, 13:06:03 Creds: Username/Password
⏎29/09/2020, 13:06:03 Peer Info:
IV_VER=3.git::3e56f9a6
IV_PLAT=mac
IV_NCP=2
IV_TCPNL=1
IV_PROTO=2
IV_GUI_VER=OCmacOS_3.2.2-1899
IV_SSO=openurl⏎29/09/2020, 13:06:04 VERIFY OK: depth=1, /CN=OpenVPN/C=FI
⏎29/09/2020, 13:06:04 VERIFY OK: depth=0, /CN=OpenVPN-Cert/C=FI
⏎29/09/2020, 13:06:04 SSL Handshake: CN=OpenVPN-Cert, TLSv1.2, cipher TLSv1.2 ECDHE-RSA-AES256-GCM-SHA384, 2048 bit RSA
⏎29/09/2020, 13:06:04 EVENT: GET_CONFIG ⏎29/09/2020, 13:06:04 Session is ACTIVE
⏎29/09/2020, 13:06:04 Sending PUSH_REQUEST to server...
⏎29/09/2020, 13:06:05 Sending PUSH_REQUEST to server...
⏎29/09/2020, 13:06:07 Sending PUSH_REQUEST to server...
⏎29/09/2020, 13:06:07 OPTIONS:
0 [route] [10.0.0.0] [255.0.0.0]
1 [dhcp-option] [DNS] [10.0.0.1]
2 [route-gateway] [10.0.8.1]
3 [topology] [subnet]
4 [ping] [10]
5 [ping-restart] [60]
6 [ifconfig] [10.0.8.2] [255.255.255.0]
7 [peer-id] [0]
8 [cipher] [AES-128-GCM]⏎29/09/2020, 13:06:07 PROTOCOL OPTIONS:
cipher: AES-128-GCM
digest: NONE
compress: NONE
peer ID: 0
⏎29/09/2020, 13:06:07 EVENT: ASSIGN_IP ⏎29/09/2020, 13:06:07 TunPersist: short-term connection scope
⏎29/09/2020, 13:06:07 TunPersist: new tun context
⏎29/09/2020, 13:06:07 CAPTURED OPTIONS:
Session Name: pfsensewanip
Layer: OSI_LAYER_3
MTU: 1500
Remote Address: pfsensewanip
Tunnel Addresses:
10.0.8.2/24 -> 10.0.8.1
Reroute Gateway: IPv4=0 IPv6=0 flags=[ IPv4 ]
Block IPv6: no
Add Routes:
10.0.0.0/8
Exclude Routes:
DNS Servers:
10.0.0.1
Search Domains:⏎29/09/2020, 13:06:07 SetupClient: transmitting tun setup list to /var/run/agent_ovpnconnect.sock
{
"config" :
{
"iface_name" : "",
"layer" : "OSI_LAYER_3",
"tun_prefix" : false
},
"pid" : 7749,
"tun" :
{
"adapter_domain_suffix" : "",
"add_routes" :
[
{
"address" : "10.0.0.0",
"gateway" : "",
"ipv6" : false,
"metric" : -1,
"net30" : false,
"prefix_length" : 8
}
],
"block_ipv6" : false,
"dns_servers" :
[
{
"address" : "10.0.0.1",
"ipv6" : false
}
],
"layer" : 3,
"mtu" : 1500,
"remote_address" :
{
"address" : "pfsensewanip",
"ipv6" : false
},
"reroute_gw" :
{
"flags" : 256,
"ipv4" : false,
"ipv6" : false
},
"route_metric_default" : -1,
"session_name" : "pfsensewanip",
"tunnel_address_index_ipv4" : 0,
"tunnel_address_index_ipv6" : -1,
"tunnel_addresses" :
[
{
"address" : "10.0.8.2",
"gateway" : "10.0.8.1",
"ipv6" : false,
"metric" : -1,
"net30" : false,
"prefix_length" : 24
}
]
}
}
POST unix://[/var/run/agent_ovpnconnect.sock]/tun-setup : 200 OK
{
"iface_name" : "utun2",
"layer" : "OSI_LAYER_3",
"tun_prefix" : true
}
/sbin/ifconfig utun2 down
/sbin/ifconfig utun2 10.0.8.2 10.0.8.1 netmask 255.255.255.0 mtu 1500 up
/sbin/route add -net 10.0.8.0 -netmask 255.255.255.0 10.0.8.2
add net 10.0.8.0: gateway 10.0.8.2
/sbin/route add -net 10.0.0.0 -netmask 255.0.0.0 10.0.8.1
add net 10.0.0.0: gateway 10.0.8.1
MacDNSAction: FLAGS=F RD=1 SO=5000 DNS=10.0.0.1 DOM= ADS=
open utun2 SUCCEEDED
⏎29/09/2020, 13:06:07 EVENT: CONNECTED datafix@pfsensewanip:1194 (pfsensewanip) via /UDPv4 on utun2/10.0.8.2/ gw=[10.0.8.1/]⏎29/09/2020, 13:06:07 Connected via utun2
⏎29/09/2020, 13:06:07 MacLifeCycle NET_IFACE en0
Firewall rules
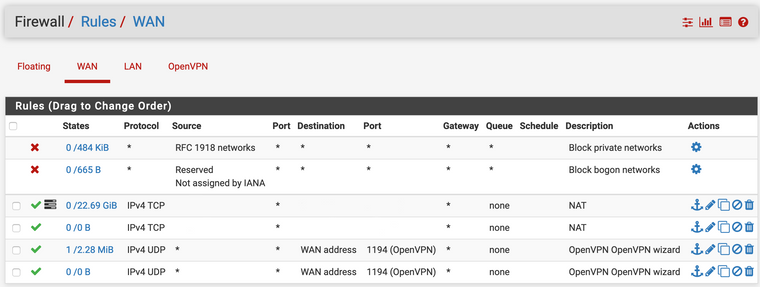
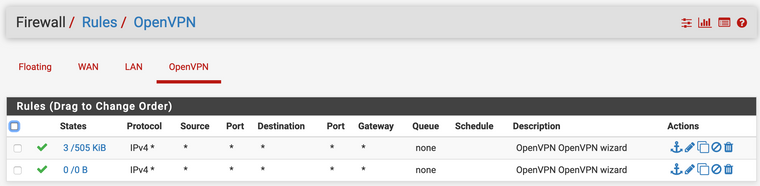
-
@pmk885 said in Cannot access LAN resources:
LAN network 10.0.0.0/8
VPN tunnel is 10.0.8.0/24These networks are overlapping.
Do you really need a /8 LAN???
-
@viragomann said in Cannot access LAN resources:
@pmk885 said in Cannot access LAN resources:
LAN network 10.0.0.0/8
VPN tunnel is 10.0.8.0/24These networks are overlapping.
Do you really need a /8 LAN???
Thanks for your reply.
Should I change VPN tunnel to something like 192.168.1.0/24 then?
I don't need /8 LAN. Maybe I have chosen that based on some tutorial. Can /8 LAN cause any issues?
-
@pmk885 said in Cannot access LAN resources:
I don't need /8 LAN. Maybe I have chosen that based on some tutorial.
Never seen such stupid turorial.
@pmk885 said in Cannot access LAN resources:
Can /8 LAN cause any issues?
You even met one possible issue.
Also consider on the remote side of the VPN. Clients using a subnet out of 10.0.0.0/8 may have problems to access your network.So I'd suggest to scale down your LAN and change the OpenVPN tunnel to somenthing uncommon.
-
@viragomann said in Cannot access LAN resources:
Never seen such stupid turorial.
I think in this case the admin was stupid

@pmk885 said in Cannot access LAN resources:
Can /8 LAN cause any issues?
You even met one possible issue.
Also consider on the remote side of the VPN. Clients using a subnet out of 10.0.0.0/8 may have problems to access your network.So I'd suggest to scale down your LAN and change the OpenVPN tunnel to somenthing uncommon.
Changed LAN to /24 and tunnel to 192.168.50.0/24. Everything is working fine now. Many thanks for your help! I knew it's not a difficult solution.
Just to make sure, should my config be now problem free?
-
Have you updated the "Local networks" in the server settings to your new LAN subnet?
On WAN interface you have two equal OpenVPN wizard rules. So you may delete one.
You're allowing access to anywhere on the OpenVPN tab, so ensure you can trust all clients.
-
@viragomann said in Cannot access LAN resources:
Have you updated the "Local networks" in the server settings to your new LAN subnet?
Forgot that, fixed now.
On WAN interface you have two equal OpenVPN wizard rules. So you may delete one.
I did delete the whole vpn server and reconfigured it with wizard before posting here so apparently it made duplicate rules. Fixed now.
You're allowing access to anywhere on the OpenVPN tab, so ensure you can trust all clients.
I'm the only one using the VPN and I'll add SSL/TLS auth for more security.
Thank you again!