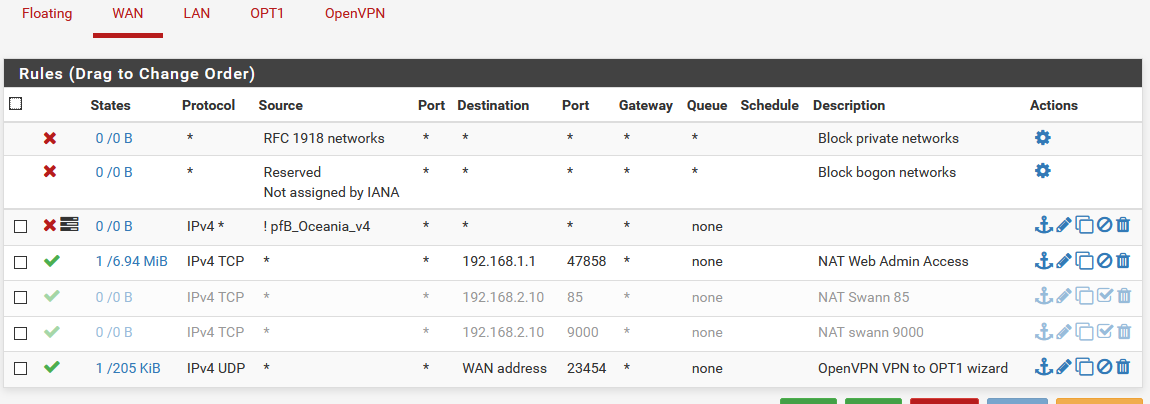
OpenVPN client can ping but not access server on LAN
-
@AKEGEC Not really... Sorry
-
Your dest is wrong in that outbound nat.. your vpn client is coming from 192.168.10 right, and he is talking to your security device on 192.168.2.x right?
So your outbound nat dest would be the 192.168.2 network.. not 192.168.10
The point of the outbound nat to talk to a device on a 192.168.2 network that has no gateway on the device, is to make the traffic look like its coming from its own network 192.168.2..
The destination is the opt1 network.. 192.168.2
client 192.168.10.2 --- vpn ---192.168.10.1 (pfsense) 192.168.2.1 --- 192.168.2.x
So you want to nat this 192.168.10 traffic to look like it came from 192.168.2.1, so 2.x knows how to talk back to it without a gateway..
-
Go to Firewall > Aliases > +Add
Name: Private OPT1 or bla bla bla
Type: Network(s)
Network or FQDN: 192.168.10.2-192.168.10.254
If your OPT1 IP interface is 192.168.10.1, you must excluded your OPT1 interface ip address.
Press Add Network button -
I regijied the outbound, here are the results
On the OpenVPN Interface
12:40:36.930315 IP 192.168.10.2 > 192.168.2.10: ICMP echo request, id 1, seq 69, length 40
12:40:36.931039 IP 192.168.2.10 > 192.168.10.2: ICMP echo reply, id 1, seq 69, length 40The OPT1 interface
12:42:01.418506 IP 192.168.2.1 > 192.168.2.10: ICMP echo request, id 50048, seq 73, length 40
12:42:01.419125 IP 192.168.2.10 > 192.168.2.1: ICMP echo reply, id 50048, seq 73, length 40Looks like it's replying to the default gateway now at least.
-
Yup that looks good..
You should be able to talk to that device now on anything not just icmp
To that device any traffic coming from your vpn will just look like its coming from pfsense 2.1, which is on its own network and it can talk to.
This should also circumvent any device firewalls that would prevent talking to some service from a different network.
-
@AKEGEC What do I put in the second box that comes up after pressing "Add network"? Or did you mean "save"?
-
Have no idea why he wants you to create an alias, there is no need for one in such a setup.
-
@johnpoz Still not getting a response from the security system....
-
Well do you sniff test again.. Do you see traffic going to your security system looking like its coming from 2.1, do you see a response - does the response go back to yoru vpn client?
If you see traffic going back over the vpn to your vpn client - its not a pfsense issue.
-
@johnpoz This is when trying to access the webpage:
On the OpenVPN interface
12:54:58.643002 IP 192.168.10.2.63027 > 192.168.2.10.85: tcp 0
12:55:00.483117 IP 192.168.10.2.63202 > 192.168.2.10.85: tcp 0
12:55:00.483881 IP 192.168.2.10.85 > 192.168.10.2.63202: tcp 0
12:55:00.868709 IP 192.168.10.2.63202 > 192.168.2.10.85: tcp 0
12:55:00.868786 IP 192.168.10.2.63202 > 192.168.2.10.85: tcp 283
12:55:00.869464 IP 192.168.2.10.85 > 192.168.10.2.63202: tcp 0
12:55:00.870122 IP 192.168.2.10.85 > 192.168.10.2.63202: tcp 108
12:55:01.651781 IP 192.168.2.10.85 > 192.168.10.2.63202: tcp 870The OPT1 interface
12:53:08.909190 IP 192.168.2.1.63368 > 192.168.2.10.85: tcp 0
12:53:08.909830 IP 192.168.2.10.85 > 192.168.2.1.63368: tcp 1440
12:53:09.143689 IP 192.168.2.10.85 > 192.168.2.1.37840: tcp 0
12:53:09.170709 IP 192.168.2.10.85 > 192.168.2.1.51729: tcp 0Looks like everything should be working....
-
Not doesn't look right to be honest.. Looks like you sent 2 syns maybe, you have 2 different source ports there.
Well clearly your seeing answers back to your vpn client.. I would open them in say wireshark, make sure its not the security system sending back F off with a RST..
But if you see return traffic going back to the client over the vpn - pfsense is doing exactly what it suppose to..
This is traffic 2 3 different source ports
12:53:08.909830 IP 192.168.2.10.85 > 192.168.2.1.63368: tcp 1440 12:53:09.143689 IP 192.168.2.10.85 > 192.168.2.1.37840: tcp 0 12:53:09.170709 IP 192.168.2.10.85 > 192.168.2.1.51729: tcp 0 -
@johnpoz I'll install wireshark and have a look, it looks like it's trying to connect to the webpage in the browser, but never gets there.
-
@johnpoz Could DNS be causing issues here? I don't think I have it setup correctly.
-
@johnpoz said in OpenVPN client can ping but not access server on LAN:
12:53:08.909830 IP 192.168.2.10.85 > 192.168.2.1.63368: tcp 1440
12:53:09.143689 IP 192.168.2.10.85 > 192.168.2.1.37840: tcp 0
12:53:09.170709 IP 192.168.2.10.85 > 192.168.2.1.51729: tcp 02.10 is serving up the webpage right? And 10.2 is the client trying to view the webpage.
You clearly are getting there, and your seeing answers.. But what are the answers... Pfsense has no control over the answers.. It just forwards the packets back and forth between the client and the server.. It has no interest or influence over what those answers might be.
-
@johnpoz That's correct. I can get it fine by going through the net with standard port forwarding, just this VPN stuff is causing problems.
-
To pfsense there is NO difference.. Pfsense doesn't care if what interface you come in on, be it a vpn interface or wan interface..
You have something else going on..
You can clearly see pfsense doing what it was told, send traffic to dest IP on port X, and then return whatever is returned to who asked for it, if there is an answer - no matter what that answer might be.
-
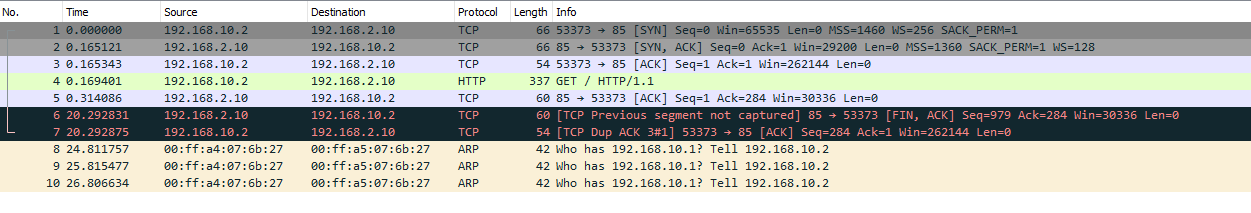
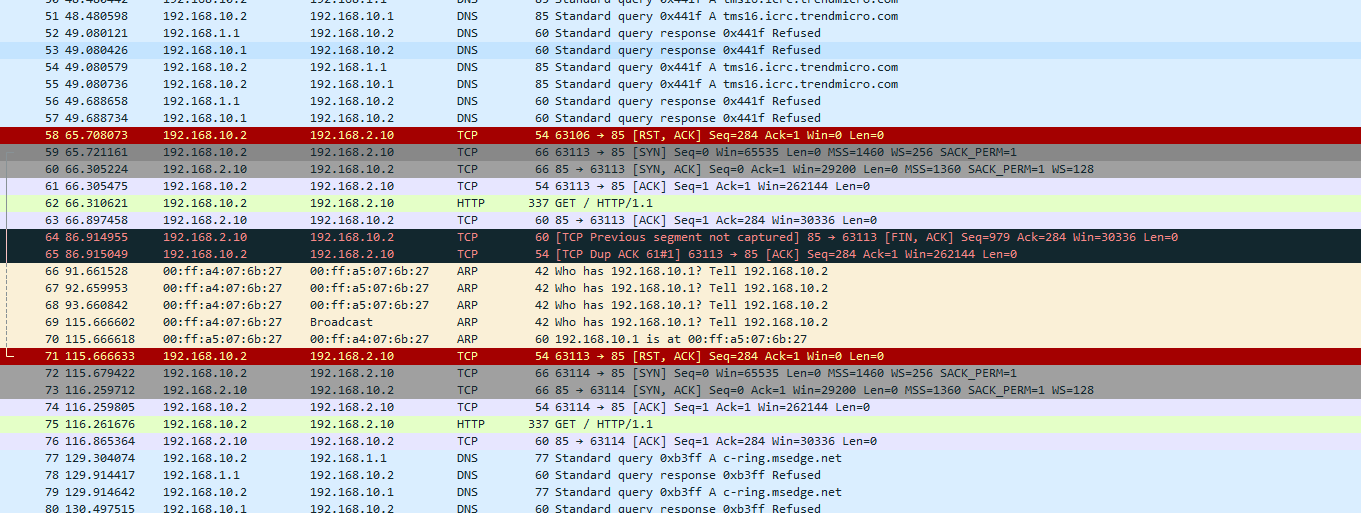
@johnpoz This is from wireshark. I've not used it before so not sure what I'm looking at.
 .
. -
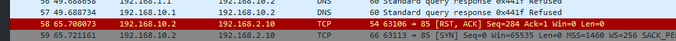
This is 10.2 telling 2.10 to F off with this connection.. The RST is a reset for this connection
This is 10.2 asking 2.10 for something that get http 1.1
2.10 answers.. But then your 10.2 looks be trying to find c-ring.msedge.net from 192.168.1.1, and 192.168.1.1 telling him sorry no REFUSED.
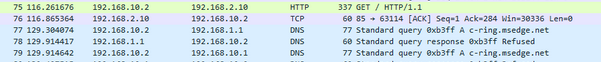
If your wanting your vpn clients to use pfsense (unbound) for dns, you have to add your vpn tunnel network to the ACLs on unbound.. Or yeah it will refuse any connections.
I take it this some ring camera? And looks like your client 10.2 needs to talk to ring to finish the connection??
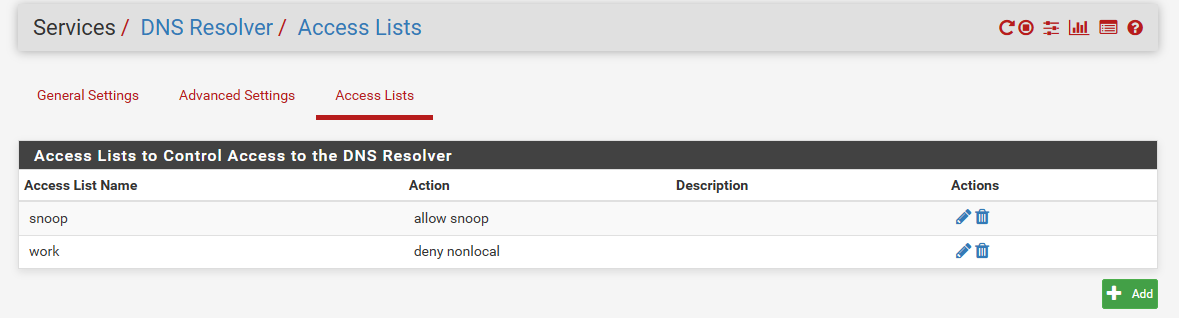
Out of the box unbound allows queries from networks pfsense is directly attached too.. But tunnel networks do not get access automatically.. You have to allow them via ACL.
edit: I do not have ring anything to play with... But you sure you can use ring without internet access.
I would test by putting say 2 devices on your opt network. Where neither actually have internet access and try and access your ring device.. Its possible some sort of auth or something has to happen via the internet??
-
@johnpoz It's for a Swann network security system.
I'm assuming I don't need DNS for this VPN at all since I'm purely using IP addresses. I might remove the DNS servers from the OpenVPN config.
I'm pretty sure it'll work offline as I can connect to it via a simple NAT port forward and still no gateway.
-
@johnpoz This is from wireshark after I removed DNS from the OpenVPN server config and re-exported it to the client