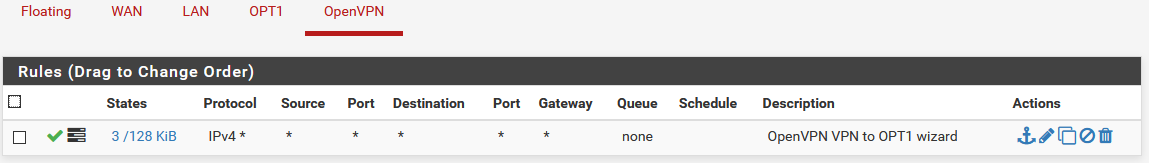
OpenVPN client can ping but not access server on LAN
-
To pfsense there is NO difference.. Pfsense doesn't care if what interface you come in on, be it a vpn interface or wan interface..
You have something else going on..
You can clearly see pfsense doing what it was told, send traffic to dest IP on port X, and then return whatever is returned to who asked for it, if there is an answer - no matter what that answer might be.
-
@johnpoz This is from wireshark. I've not used it before so not sure what I'm looking at.
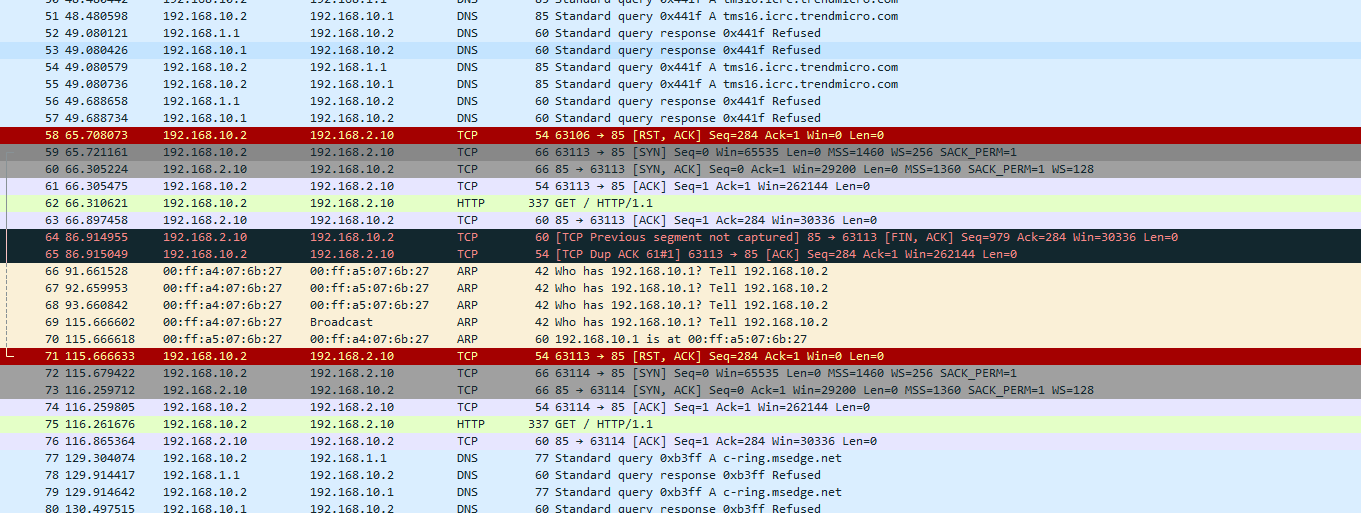 .
. -
This is 10.2 telling 2.10 to F off with this connection.. The RST is a reset for this connection
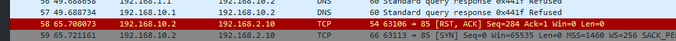
This is 10.2 asking 2.10 for something that get http 1.1
2.10 answers.. But then your 10.2 looks be trying to find c-ring.msedge.net from 192.168.1.1, and 192.168.1.1 telling him sorry no REFUSED.
If your wanting your vpn clients to use pfsense (unbound) for dns, you have to add your vpn tunnel network to the ACLs on unbound.. Or yeah it will refuse any connections.
I take it this some ring camera? And looks like your client 10.2 needs to talk to ring to finish the connection??
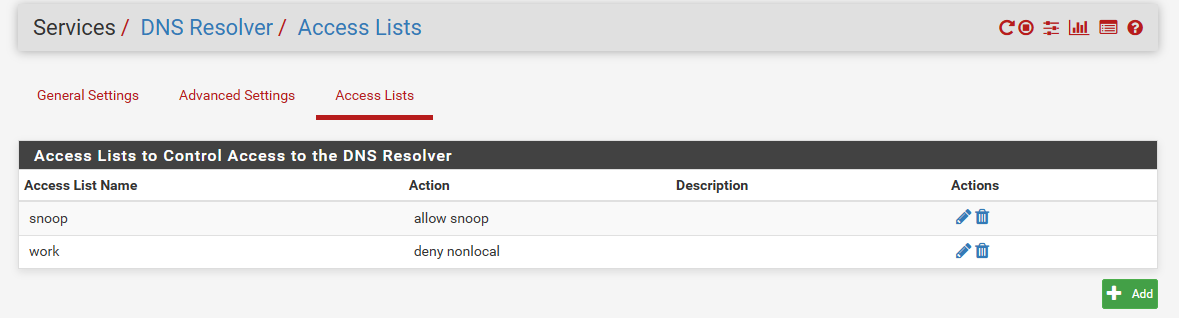
Out of the box unbound allows queries from networks pfsense is directly attached too.. But tunnel networks do not get access automatically.. You have to allow them via ACL.
edit: I do not have ring anything to play with... But you sure you can use ring without internet access.
I would test by putting say 2 devices on your opt network. Where neither actually have internet access and try and access your ring device.. Its possible some sort of auth or something has to happen via the internet??
-
@johnpoz It's for a Swann network security system.
I'm assuming I don't need DNS for this VPN at all since I'm purely using IP addresses. I might remove the DNS servers from the OpenVPN config.
I'm pretty sure it'll work offline as I can connect to it via a simple NAT port forward and still no gateway.
-
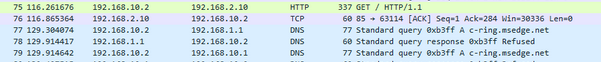
@johnpoz This is from wireshark after I removed DNS from the OpenVPN server config and re-exported it to the client
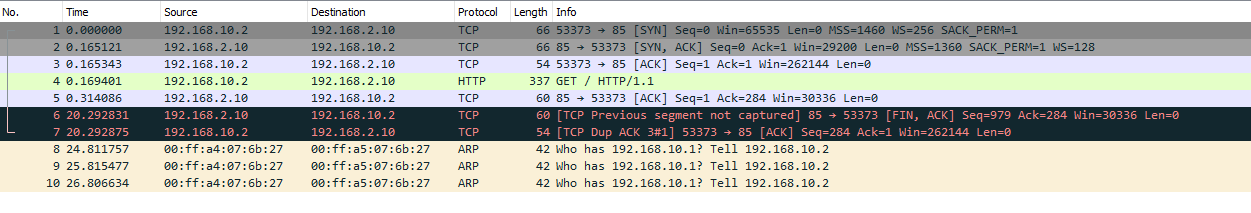
-
@Andy142 said in OpenVPN client can ping but not access server on LAN:
I'm pretty sure it'll work offline as I can connect to it via a simple NAT port forward and still no gateway.
Sorry not possible.. Unless your talking about after you put in the source nat..
You can not talk to something from another network, be it vpn or internet without what your talking to having a gateway.. Unless you do source natting.. Just not possible!
Your showing bits and pieces of a sniff... In that last one your showing a connection closing with Fin,Ack.. from 2.10 to 10.2 - that is your securing telling 10.2 I don't want to talk any more.
How are you testing this port forward you - actually from the OUTSIDE, ie the internet.
Also looks like you might have lost vpn connection there, or that sure isn't just your internet connection? Since seeing arp for pfsense 10.1 looking for your client? 10.2
-
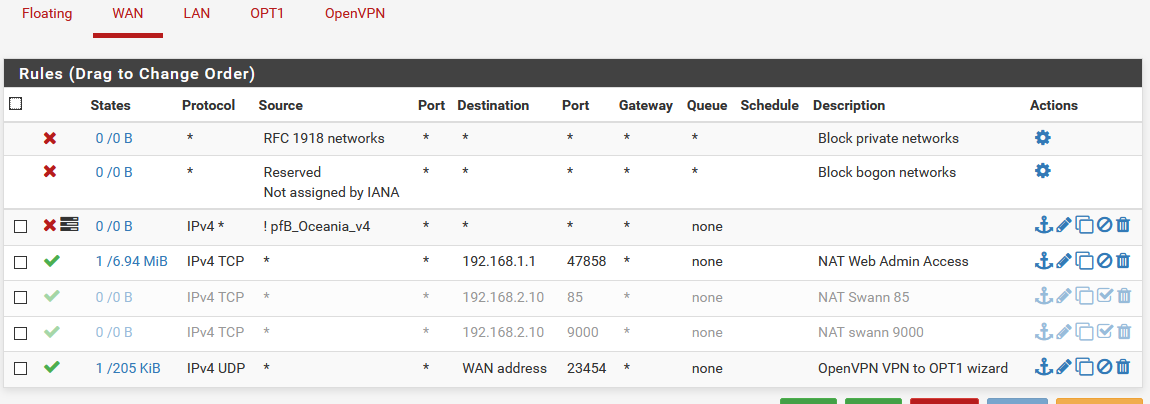
@johnpoz When I setup a NAT like in the picture below, and use my WAN IP to connect, it works just fine (so long as I have port 9000 as well).
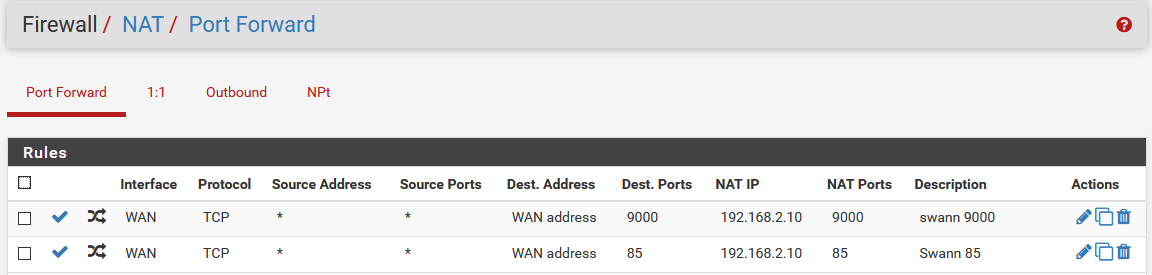
OPT1 still doesn't have a gateway set.
I am running on a slow latent connection, but it's still fast enough to run youtube low quality.
-
@Andy142 said in OpenVPN client can ping but not access server on LAN:
and use my WAN IP to connect,
From where??? If your on the same network and using nat reflection.
Let me state this again... You can not talk to a device from a different network, without that device knowing how to answer you... Its just not possible!! Period!
So either this device needs a gateway to send traffic that is not local to its network, or its needs route specific to know where to send traffic for specific networks that might be talking to it.
Without the client having a gateway or a specific route it is IMPOSSIBLE to talk to it from another network.. Period!!
Unless you source nat/proxy the connection so that the device your talking to thinks the traffic is local to its network, and can send the traffic back to the source natted IP or proxy that is on its local network..
OPT1 still doesn't have a gateway set.
Opt1 would never have a gateway set, its a local interface of pfsense... When you say gateway - it means the devices on opt1 pointing back to pfsense as their gateway..
Out of the box if a client on this opt1 network gets dhcp from pfsense, it would be handed a gateway of the pfsense opt1 IP.. So yes your device on your opt1 network would have a gateway (pfsense)
Do you have gateway set on your pfsense lan interface? If so then its WRONG!! The only interface on pfsense that would have gateways are your wan connection(s).. This is how pfsense knows how to answer traffic from the internet..
-
@johnpoz I'm pretty lost now. I'm currently out of the country and using a VPN to get back into Australia.
I was thinking that my OPT1 interface didn't have access to the internet because it didn't have a gateway set, but now I realise that's wrong.
I'm also confused how I can connect to the security system with basic port forwarding to the Security system, but when I VPN into the LAN, I can only ping and not access the webpage.
-
I don't know the ins and out of how this security device works. But clearly it has a gateway (pfsense). And there is no reason to do the source natting of your vpn connection.
From what you have shown the device is answering.. But was showing RST from your client, and Fin,ack from your device to your clients.. Both are ways to END a conversation.
So what is actually the issue with vpn vs internet not sure? But from what you have shown pfsense is doing what its told to correctly.
I would suggest you sniff on pfsense opt1 interface for your device IP. Set the sniffing packets limit from 100 to 0 so you can see the full conversation... Then start a conversation from internet doing your normal forwarding..
So you can see what is all involved with normal working conversation. Then make sure you kill any states for this conversation.. Reboot the device say, and then doing the same sniffing and talking from your vpn client.. So you can see what might be different?
Off the top of head, thing that might be different while your on the actual internet with your client doing port forwarding on pfsense is you have access to internet from your client via the same connection. While your vpn connection would change that sort of connection, etc.
Its possible your device phones home and checks something before allowing connection? It could be all kinds of things. But from what you have shown pfsense is doing exactly what it should be doing, and again doesn't care if your coming from the internet or a vpn.. It just allows the traffic or it doesn't..