pfSense as OpenVPN Client - cannot reach remote network from local network
-
@cmrt said in pfSense as OpenVPN Client - cannot reach remote network from local network:
the server gives out 10.4.0.0/24 addresses, and is configured with static IP 10.4.0.1 on tun0.
So 10.4.0.0/24 is the tunnel network.
@cmrt said in pfSense as OpenVPN Client - cannot reach remote network from local network:
I have added the OpenVPN network (10.4.0.0/24) to "IPv4 Remote network(s)"
There is no need to add the tunnel network to the "Remote network(s)".
@cmrt said in pfSense as OpenVPN Client - cannot reach remote network from local network:
However from my local machine (behind pfSense) I cannot reach 10.4.0.1 at all.
Is pfSense the default gateway on these machines?
I presume, you're trying to achieve a site-to-site connection to connect your local network with the remote LAN behind the server. Or are multiple clients able to connect to the server?
-
So 10.4.0.0/24 is the tunnel network.
Yes, but it's also the network I'm trying to reach
There is no need to add the tunnel network to the "Remote network(s)".
If I don't, I can't even ping 10.4.0.1 from pfSense; my understanding is that this happens because I'm not pulling routes, pfSense is getting 10.4.0.18 from the OpenVPN server and the other end of the tunnel (which I see from ifconfig) is 10.4.0.17. Without the route, pfSense would have no idea how to get to 10.4.0.1
Is pfSense the default gateway on these machines?
Yes
I presume, you're trying to achieve a site-to-site connection to connect your local network with the remote LAN behind the server. Or are multiple clients able to connect to the server?
I am actually trying to simply reach the server. I don't really have a remote LAN behind it. I need a VPN as a secure tunnel for transmitting backups offsite, but the OpenVPN server is the same server that will hold the backups, hence my trying to connect to it.
I tried adding 10.4.0.0/24 only to "Tunnel Networks": the highlighted route below was not there and pfSense couldn't ping it.
Adding 10.4.0.0/24 to both "Remote Networks" and "Tunnel Networks" doesn't solve my problem either, unfortunately: this is a ping and a traceroute from my local machine to 10.4.0.1 (OpenVPN server) after adding the /24 to Tunnel and Remote Networks: it has the same behaviour as when I only added it to Remote Networks.
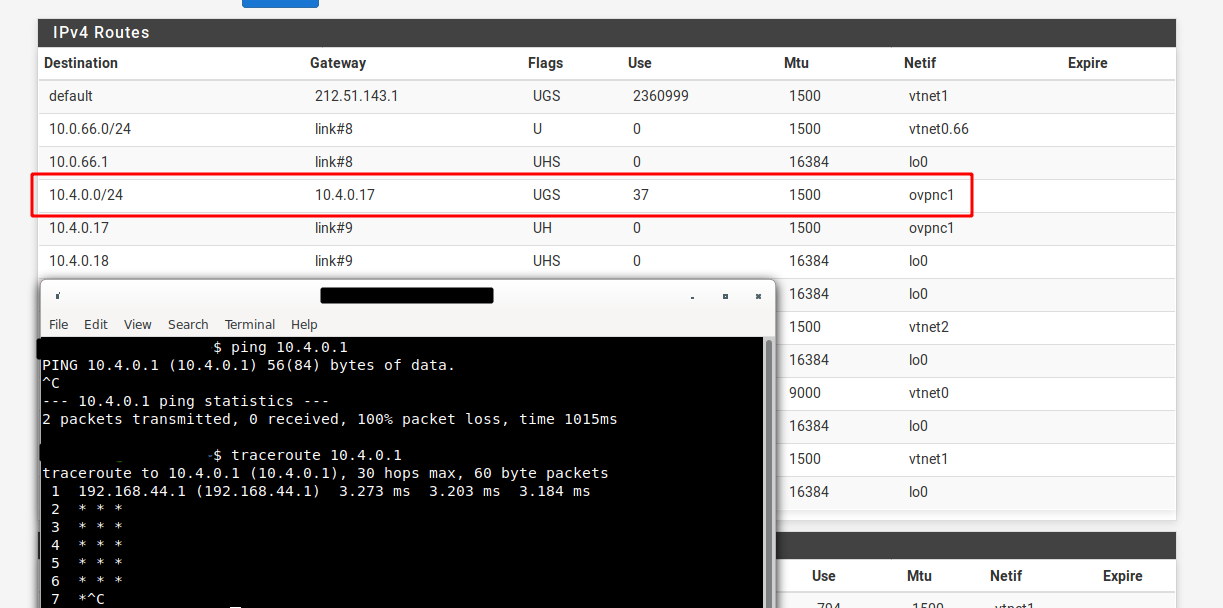
At the same time, everything works from pfSense itself
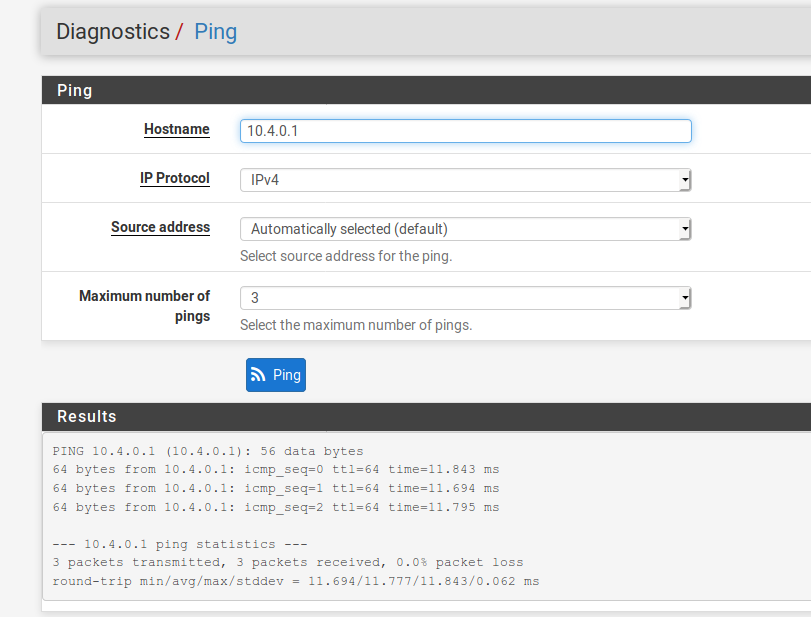
My firewall rules have a "Pass any/any" rule for both LAN (where the machine I'm using is) and OpenVPN
-
@cmrt said in pfSense as OpenVPN Client - cannot reach remote network from local network:
pfSense is getting 10.4.0.18 from the OpenVPN server and the other end of the tunnel (which I see from ifconfig) is 10.4.0.17. Without the route, pfSense would have no idea how to get to 10.4.0.1
Yes, that's true for a /30 topology.
@cmrt said in pfSense as OpenVPN Client - cannot reach remote network from local network:
this is a ping and a traceroute from my local machine to 10.4.0.1 (OpenVPN server)
What is 192.168.44.1?
Has the server set the route to your local network?
Asked some questions above, but you didn't answer. -
@viragomann said in pfSense as OpenVPN Client - cannot reach remote network from local network:
@cmrt said in pfSense as OpenVPN Client - cannot reach remote network from local network:
this is a ping and a traceroute from my local machine to 10.4.0.1 (OpenVPN server)
What is 192.168.44.1?
It's pfSense
Has the server set the route to your local network?
Just to clarify: if you mean "if you login to the server and check the routes do you see one to your local network" then no, I don't see them.
But if that was the problem, I should see ICMP packets coming out of
tun0when I check with tcpdump and ping from my local machine, and then the replies would get lost..To make sure this was not the issue I manually added the route on my OpenVPN server, but it didn't make a difference :(
Asked some questions above, but you didn't answer.
Sorry, I must be missing something - is there any specific question I didn't answer? I thought I did; I reread your post and can't figure out which one I missed.
EDIT: if you meant
Or are multiple clients able to connect to the server?
then the answer is yes, multiple clients can connect to it. The server is my VPN for "away from home", and all the clients are set up with certificates, can connect to it and browse the internet through it.
I tried connecting with my phone, checking the IP and then trying to ping it from behind pfSense, but I was not able to reach it (same as trying to ping the server itself)
-
@cmrt said in pfSense as OpenVPN Client - cannot reach remote network from local network:
Just to clarify: if you mean "if you login to the server and check the routes do you see one to your local network" then no, I don't see them.
But if that was the problem, I should see ICMP packets coming out of tun0 when I check with tcpdump and ping from my local machine, and then the replies would get lost..That's right. You should see the packets on the pfSense LAN (of course), on its OpenVPN interface and on the servers OpenVPN interface.
I'd check on all three point to investigate the problem.@cmrt said in pfSense as OpenVPN Client - cannot reach remote network from local network:
To make sure this was not the issue I manually added the route on my OpenVPN server, but it didn't make a difference :(
How have you done this? The routing has to be done by OpenVPN iroute option.
However, if you don't see the packets on the servers tun, there obviously is something wrong on the clients site.The other question was, if pfSense is the default gateway, however, that's already answered now with the pfSense LAN IP, the LAN device is sending its packets to.
-
@viragomann said in pfSense as OpenVPN Client - cannot reach remote network from local network:
That's right. You should see the packets on the pfSense LAN (of course), on its OpenVPN interface and on the servers OpenVPN interface.
I'd check on all three point to investigate the problem.On the OpenVPN server I checked with
tcpdumpand no packets get there; on the LAN side, pfTop shows something (I don't know what the0:0stands for) while pinging the OpenVPN server from my machine
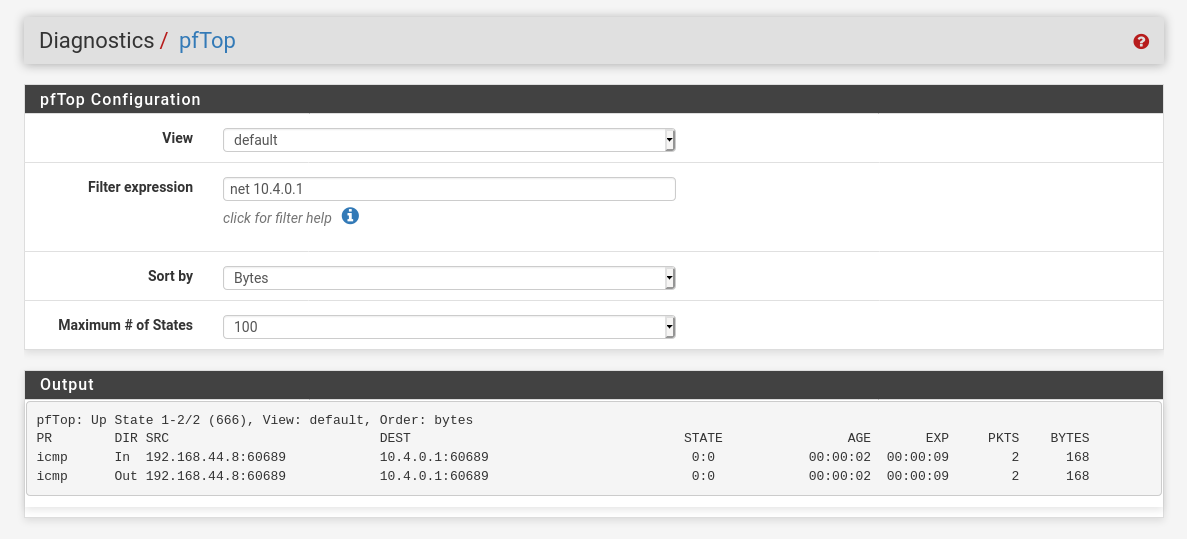
A packet capture on LAN shows only ICMP echo requests
23:18:42.438141 IP 192.168.44.8 > 10.4.0.1: ICMP echo request, id 17118, seq 1, length 64 23:18:43.452631 IP 192.168.44.8 > 10.4.0.1: ICMP echo request, id 17118, seq 2, length 64 23:18:44.475007 IP 192.168.44.8 > 10.4.0.1: ICMP echo request, id 17118, seq 3, length 64 23:18:45.499843 IP 192.168.44.8 > 10.4.0.1: ICMP echo request, id 17118, seq 4, length 64 23:18:46.523671 IP 192.168.44.8 > 10.4.0.1: ICMP echo request, id 17118, seq 5, length 64 23:18:47.547029 IP 192.168.44.8 > 10.4.0.1: ICMP echo request, id 17118, seq 6, length 64 23:18:48.571226 IP 192.168.44.8 > 10.4.0.1: ICMP echo request, id 17118, seq 7, length 64 23:18:49.595496 IP 192.168.44.8 > 10.4.0.1: ICMP echo request, id 17118, seq 8, length 64tcpdumpshows packets going through pfSense'sovpnc1interface, but never reachingtun0on the other side..? O_o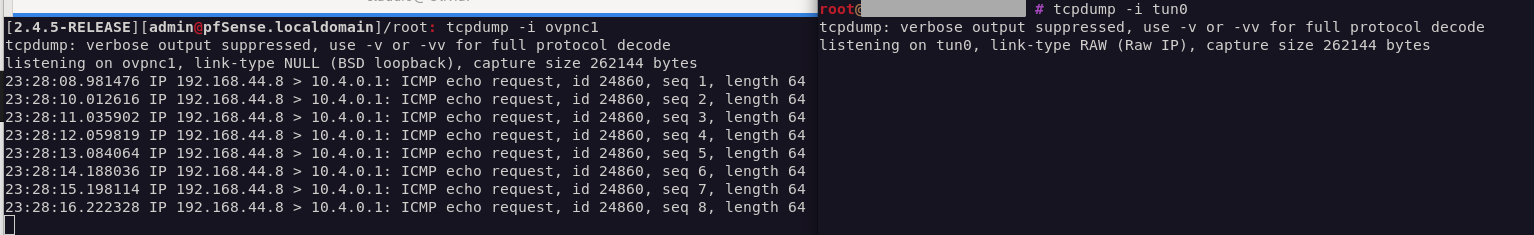
@cmrt said in pfSense as OpenVPN Client - cannot reach remote network from local network:
To make sure this was not the issue I manually added the route on my OpenVPN server, but it didn't make a difference :(
How have you done this? The routing has to be done by OpenVPN iroute option.
root@myserver:/root$ ip route add 192.168.44.0/24 dev tun0I wouldn't rely on it though, just testing if the lack of a "return route" was the cause of the issue.
However, if you don't see the packets on the servers tun, there obviously is something wrong on the clients site.
On this I agree. I wonder what, though.
-
What shows the routing table of pfSense?
@cmrt said in pfSense as OpenVPN Client - cannot reach remote network from local network:
root@myserver:/root$ ip route add 192.168.44.0/24 dev tun0I wouldn't rely on it though, just testing if the lack of a "return route" was the cause of the issue.
That's not the correct way to set a route. You're missing the gateway here.
However, as mentioned, this the routing is to be done by OpenVPN.If you only need access from the pfSense site to the server you may also nat the traffic and do not need routes necessarily. But if you want to access a device behind pfSense from the server you need it.
-
That's not the correct way to set a route. You're missing the gateway here.
I added the gateway, still unable to ping.
ip ro a 192.168.44.0/24 via 10.4.0.1 dev tun0I can look into getting OpenVPN to add it automatically, but I'd rather not mess with the configuration on the server.
However, as mentioned, this the routing is to be done by OpenVPN.
IIUC this won't happen if I choose "Don't pull routes", which I did (and have to do to avoid forwarding all traffic through the VPN).
If OpenVPN is supposed to setup routes on the server side when a client connects to it, then there's another type of problem, but it still doesn't explain why ICMP packets from LAN can't reach the server.
If you only need access from the pfSense site to the server you may also nat the traffic and do not need routes necessarily. But if you want to access a device behind pfSense from the server you need it.
I could NAT, but I was trying to avoid that. I'm also trying to figure out why this is not working, because if pfSense is able to ping the VPN server and has installed a route to it, why won't it properly route the traffic coming from the LAN through the tunnel the pfSense itself is using?
-
@cmrt said in pfSense as OpenVPN Client - cannot reach remote network from local network:
I added the gateway, still unable to ping.
ip ro a 192.168.44.0/24 via 10.4.0.1 dev tun0The clients IP is the gateway here!
@cmrt said in pfSense as OpenVPN Client - cannot reach remote network from local network:
IIUC this won't happen if I choose "Don't pull routes", which I did (and have to do to avoid forwarding all traffic through the VPN).
We are talking about the server. Checking "Don't pull" on the client has no effect on server site.
Go to the OpenVPN documention and search for iroute to find out how to do, still the server is not pfSense.
@cmrt said in pfSense as OpenVPN Client - cannot reach remote network from local network:
I could NAT, but I was trying to avoid that. I'm also trying to figure out why this is not working, because if pfSense is able to ping the VPN server and has installed a route to it, why won't it properly route the traffic coming from the LAN through the tunnel the pfSense itself is using?
Without NAT you have not equal conditions.
-
@viragomann said in pfSense as OpenVPN Client - cannot reach remote network from local network:
@cmrt said in pfSense as OpenVPN Client - cannot reach remote network from local network:
I added the gateway, still unable to ping.
ip ro a 192.168.44.0/24 via 10.4.0.1 dev tun0The clients IP is the gateway here!
That does not work (I checked the IP assigned to pfSense before adding the route).
# ip ro a 192.168.44.0/24 via 10.4.0.18 dev tun0 Error: Nexthop has invalid gateway.Just to make sure I didn't misunderstand you, I also tried
# ip ro a 192.168.44.0/24 via 192.168.44.1 dev tun0 Error: Nexthop has invalid gateway.@cmrt said in pfSense as OpenVPN Client - cannot reach remote network from local network:
IIUC this won't happen if I choose "Don't pull routes", which I did (and have to do to avoid forwarding all traffic through the VPN).
We are talking about the server. Checking "Don't pull" on the client has no effect on server site.
Go to the OpenVPN documention and search for iroute to find out how to do, still the server is not pfSense.
I'll try tonight if I can; I'm still not sure what difference it will make from me adding the routes manually for testing, but ok.
@cmrt said in pfSense as OpenVPN Client - cannot reach remote network from local network:
I could NAT, but I was trying to avoid that. I'm also trying to figure out why this is not working, because if pfSense is able to ping the VPN server and has installed a route to it, why won't it properly route the traffic coming from the LAN through the tunnel the pfSense itself is using?
Without NAT you have not equal conditions.
What do you mean by "not equal conditions"?
-
@cmrt said in pfSense as OpenVPN Client - cannot reach remote network from local network:
That does not work (I checked the IP assigned to pfSense before adding the route).
ip ro a 192.168.44.0/24 via 10.4.0.18 dev tun0 Error: Nexthop has invalid gateway.Just to make sure I didn't misunderstand you, I also tried
ip ro a 192.168.44.0/24 via 192.168.44.1 dev tun0 Error: Nexthop has invalid gateway.Again and again and again: That should be done by OpenVPN!
@cmrt said in pfSense as OpenVPN Client - cannot reach remote network from local network:
Without NAT you have not equal conditions.
What do you mean by "not equal conditions"?
When you ping the server from pfSense, the server sees the ping coming from 10.4.0.18 (or any other IP out of the VPN pool).
When you ping the server from a LAN device without NAT, the server sees the ping is coming from an IP in 192.168.44.0/24.
When you ping the server from a LAN device and nat the traffic, the server sees the is ping coming from 10.4.0.18 (or any other IP out of the VPN pool).
Ergo with NAT, the server doesn't see any differnce if the ping is coming from pfSense itself or from a device behind.
-
@viragomann said in pfSense as OpenVPN Client - cannot reach remote network from local network:
@cmrt said in pfSense as OpenVPN Client - cannot reach remote network from local network:
That does not work (I checked the IP assigned to pfSense before adding the route).
ip ro a 192.168.44.0/24 via 10.4.0.18 dev tun0 Error: Nexthop has invalid gateway.Just to make sure I didn't misunderstand you, I also tried
ip ro a 192.168.44.0/24 via 192.168.44.1 dev tun0 Error: Nexthop has invalid gateway.Again and again and again: That should be done by OpenVPN!
Now it is (added
route 10.4.0.0 255.255.255.0to the server config), but still doesn't work.Reading https://community.openvpn.net/openvpn/wiki/RoutedLans it makes it clear that the route to the local subnet hosted by the OpenVPN server does not need to be configured (its LAN, in that document, is
10.10.2.0/24and it's not added to the OpenVPN configuration, nor as an iroute parameter)@cmrt said in pfSense as OpenVPN Client - cannot reach remote network from local network:
Without NAT you have not equal conditions.
What do you mean by "not equal conditions"?
When you ping the server from pfSense, the server sees the ping coming from 10.4.0.18 (or any other IP out of the VPN pool).
When you ping the server from a LAN device without NAT, the server sees the ping is coming from an IP in 192.168.44.0/24.
When you ping the server from a LAN device and nat the traffic, the server sees the is ping coming from 10.4.0.18 (or any other IP out of the VPN pool).
Ergo with NAT, the server doesn't see any differnce if the ping is coming from pfSense itself or from a device behind.
In understand how NAT works, but my point still stands: why is the route that's definitely been added to pfSense not producing the expected results?
To be complete, I tried adding a NAT rule, and I still see no traffic.
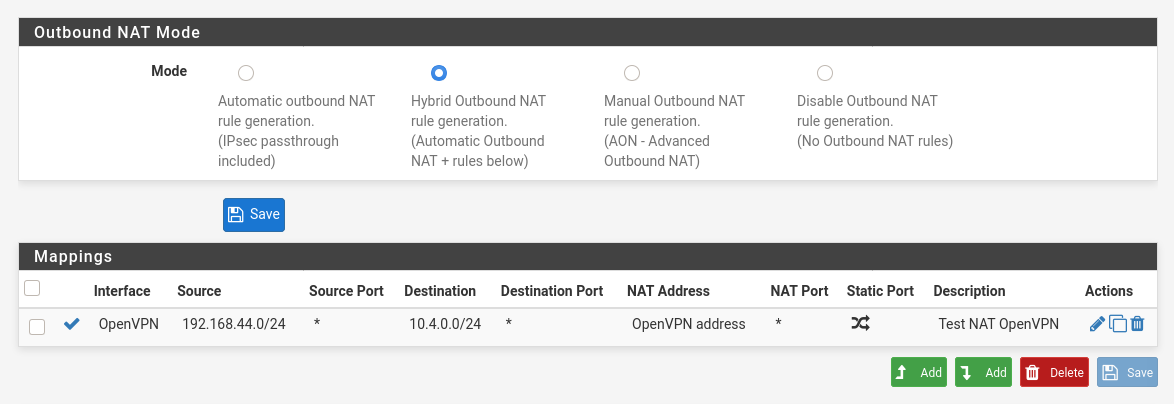
I also wiped all rules from the firewall of my OpenVPN box, to make sure this was not an issue with that, but that didn't help.
Something else is going on; I am struggling to understand what.
-
@cmrt said in pfSense as OpenVPN Client - cannot reach remote network from local network:
Now it is (added route 10.4.0.0 255.255.255.0 to the server config), but still doesn't work.
Reading https://community.openvpn.net/openvpn/wiki/RoutedLans it makes it clear that the route to the local subnet hosted by the OpenVPN server does not need to be configured (its LAN, in that document, is 10.10.2.0/24 and it's not added to the OpenVPN configuration, nor as an iroute parameter)I'm wondering how far you've read that document.
The route entries are telling his server to add a route for each of 10.10.1.0, and 10.10.3.0 to its kernel's routing table, and both will be routed to the tunnel interface and to openvpn. How will openvpn know what client to send each network to? The answer is iroute!
The thing is, we cant just drop the iroute into server.conf because it would then be used for every client, and iroute is only to tell the server at which client it should send traffic destined for a network that the kernel said should go to the openvpn interface. That is why we add the iroute commands to a ccd entry.
You will need client-config-dir /path/to/ccd/ in your server config file to enable ccd entries. ccd entries are basically included into server.conf, but only for the specified client. You put commands in ccd/client-common-name, and they are only included when the client's common-name matches the name of the file in ccd/.
@cmrt said in pfSense as OpenVPN Client - cannot reach remote network from local network:
In understand how NAT works, but my point still stands: why is the route that's definitely been added to pfSense not producing the expected results?
To be complete, I tried adding a NAT rule, and I still see no traffic.Have you done a tcpdump on the server after adding this NAT rule to see if it makes a difference?
-
@viragomann said in pfSense as OpenVPN Client - cannot reach remote network from local network:
@cmrt said in pfSense as OpenVPN Client - cannot reach remote network from local network:
Now it is (added route 10.4.0.0 255.255.255.0 to the server config), but still doesn't work.
Reading https://community.openvpn.net/openvpn/wiki/RoutedLans it makes it clear that the route to the local subnet hosted by the OpenVPN server does not need to be configured (its LAN, in that document, is 10.10.2.0/24 and it's not added to the OpenVPN configuration, nor as an iroute parameter)I'm wondering how far you've read that document.
The route entries are telling his server to add a route for each of 10.10.1.0, and 10.10.3.0 to its kernel's routing table, and both will be routed to the tunnel interface and to openvpn. How will openvpn know what client to send each network to? The answer is iroute!
The thing is, we cant just drop the iroute into server.conf because it would then be used for every client, and iroute is only to tell the server at which client it should send traffic destined for a network that the kernel said should go to the openvpn interface. That is why we add the iroute commands to a ccd entry.
You will need client-config-dir /path/to/ccd/ in your server config file to enable ccd entries. ccd entries are basically included into server.conf, but only for the specified client. You put commands in ccd/client-common-name, and they are only included when the client's common-name matches the name of the file in ccd/.
I'm wondering instead how carefully you've read it. The part you quoted is for the iroutes for the two client LANs (10.10.1.0/24 and 10.10.3.0/24), not for the route to the OpenVPN server network 10.10.2.0/24 (the Tunnel Network).
I am, as I explained above, trying to reach the OpenVPN server itself, which in the configuration above would be on 10.10.2.x, which does not, according to that page, need an iroute.
Also, for your reference:
https://docs.netgate.com/pfsense/en/latest/troubleshooting/openvpn-iroute.htmlWhen configuring a site-to-site PKI (SSL) OpenVPN setup, an internal route must be configured for the client subnet on the Client Specific Overrides tab set for the client certificate’s common name, using either the IPv4/IPv6 Remote Network/s boxes or manually using an iroute statement in the advanced settings.
Each network listed in the IPv4 Remote Network/s and IPv4 Remote Network/s boxes will have aniroutecreated automatically.Which is exactly what I've been doing from the start.
@cmrt said in pfSense as OpenVPN Client - cannot reach remote network from local network:
In understand how NAT works, but my point still stands: why is the route that's definitely been added to pfSense not producing the expected results?
To be complete, I tried adding a NAT rule, and I still see no traffic.Have you done a tcpdump on the server after adding this NAT rule to see if it makes a difference?
Yes, no traffic reaches tun0
-
Update: solved.
For posterity, the final configuration is:
on the OpenVPN server:- add
route 192.168.44.0 255.255.255.0(this is the LAN behind pfSense)
on pfSense:
- create OpenVPN config with "Don't pull routes"
- add Remote Network IPv4
10.4.0.0/24(which creates theiroute)
All that was missing from my initial configuration was
route 192.168.44.0 255.255.255.0in my OpenVPN server config.If someone stumbles upon this while having a similar problem, replace
192.168.44.0 255.255.255.0with your own LAN and netmask, and10.4.0.0/24with the OpenVPN network.I'm not sure how to mark this as solved (can't edit the original post) so if I can't figure it out hopefully a mod can mark it as such :)
- add
-
@cmrt said in pfSense as OpenVPN Client - cannot reach remote network from local network:
10.4.0.0/24
I cannot thank you enough for this post, THANK YOU. I have spent days on trying OpenVPN clients to access the 'remote lan' whilst using their local connection for the internet. This works! Thanks again.