How to whitelist Anydesk (Remote Access Software) in snort?
-
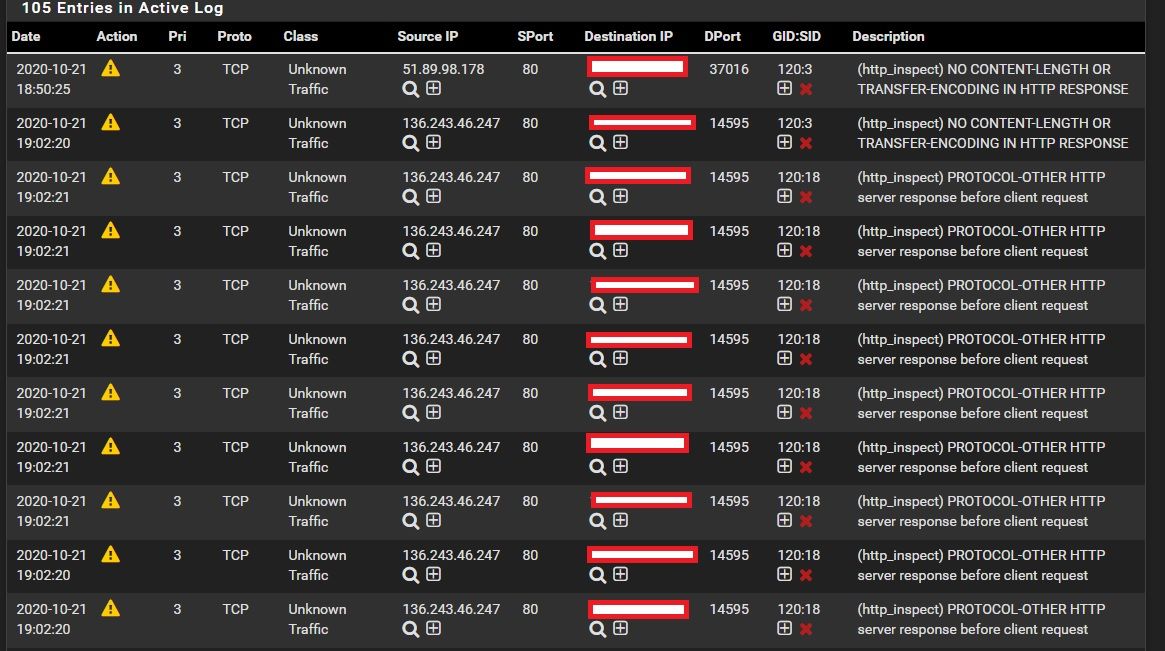
@Gertjan The program which is using the 80 and 443 port is Anydesk software, (Anydesk is a remote access software same like TeamViewer) as I mentioned we are using anydesk software to access our systems on our LAN from the internet.
The sources IP addresses that you can see on logs are all the Anydesk IPs.
What I want to do is to whitelist Anydesk in snort, and I do not know how to accomplish this, should I configure IP pass list in snort by adding all the IPs which belong to Anydesk?
-
@noor92 said in How to whitelist Anydesk (Remote Access Software) in snort?:
@Gertjan The program which is using the 80 and 443 port is Anydesk software, (Anydesk is a remote access software same like TeamViewer) as I mentioned we are using anydesk software to access our systems on our LAN from the internet.
The sources IP addresses that you can see on logs are all the Anydesk IPs.
What I want to do is to whitelist Anydesk in snort, and I do not know how to accomplish this, should I configure IP pass list in snort by adding all the IPs which belong to Anydesk?
Whitelisting is not what you want in this case.
You broke the cardinal rule of IDS/IPS that I preach about and that @Gertjan mentioned. You installed the package and immediately enabled blocking without first carefully selecting your rules and evaluating your network traffic for several weeks in non-blocking mode to see what false positives occur so you could disable those rules. So now you are reaping the result of not following the suggested course. You are getting nuisance blocks.
You have a series of clear false-positive rules from the HTTP_INSPECT preprocessor in that ALERTS tab capture. If you search this forum for a bit, you will find a lot of posts where this is discussed and what to do about it.
The IDS/IPS packages are not a good fit for inexperienced IT Security admins. These packages are not like anti-virus products that you can just install, update, and forget about. They require constant maintenance and tuning. You also need a firm foundation in the threats out there (how they work) as well as knowledge of the rules syntax and how they detect the threats. Finally, it stands to reason you need to know how to actually configure and operate the package in question. Installing the IDS/IPS packages on a home network for experimentation and learning is one thing, but installing them on a commercial production network without lots of experience configuring and maintaining them is a recipe for disaster.
-
@bmeeks said in How to whitelist Anydesk (Remote Access Software) in snort?:
You have a series of clear false-positive rules from the HTTP_INSPECT preprocessor in that ALERTS tab capture. If you search this forum for a bit, you will find a lot of posts where this is discussed and what to do about it.
You can disable the pre proc rules here if needed:-
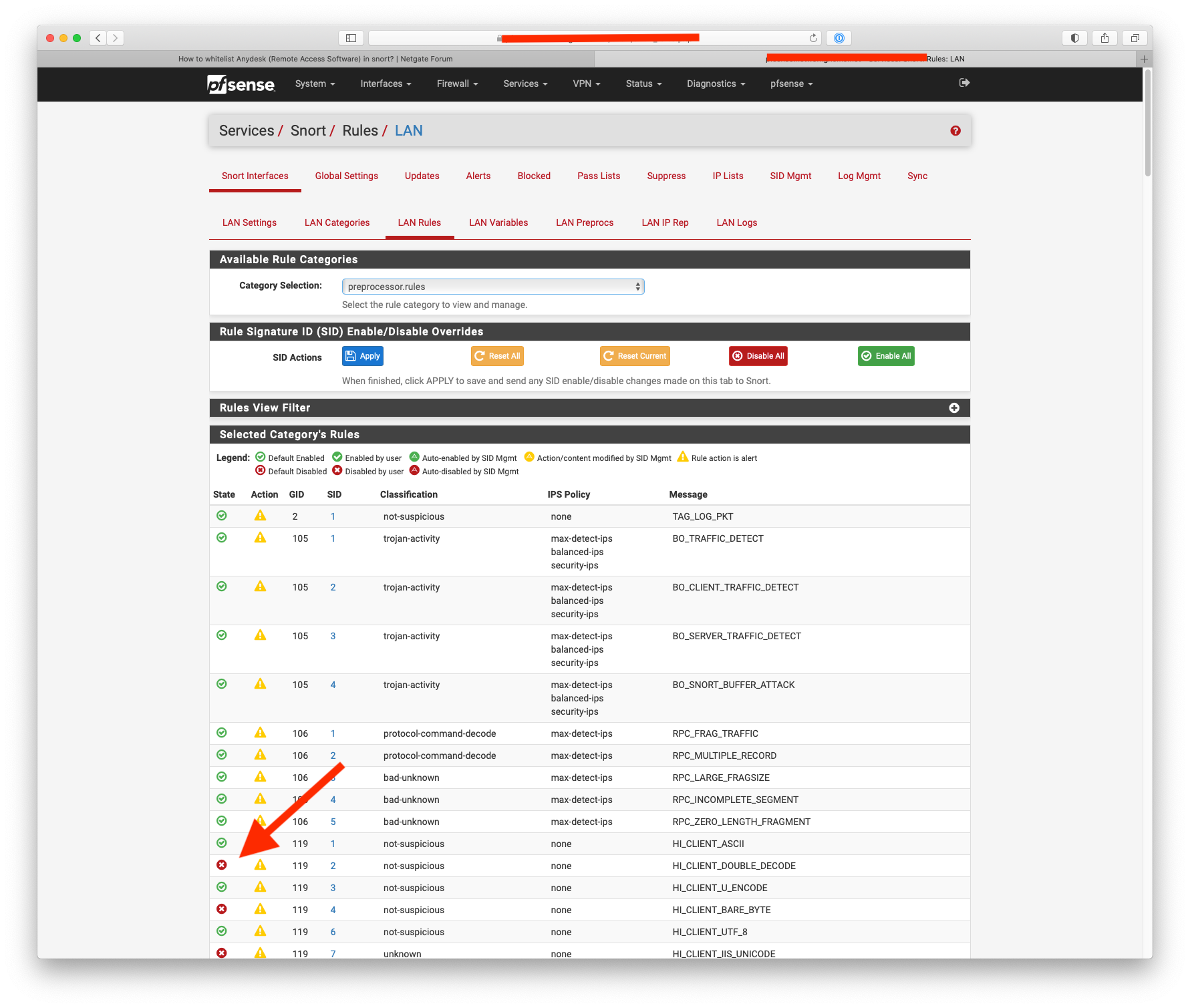
@bmeeks is the filtering option broken ?
-
@NogBadTheBad said in How to whitelist Anydesk (Remote Access Software) in snort?:
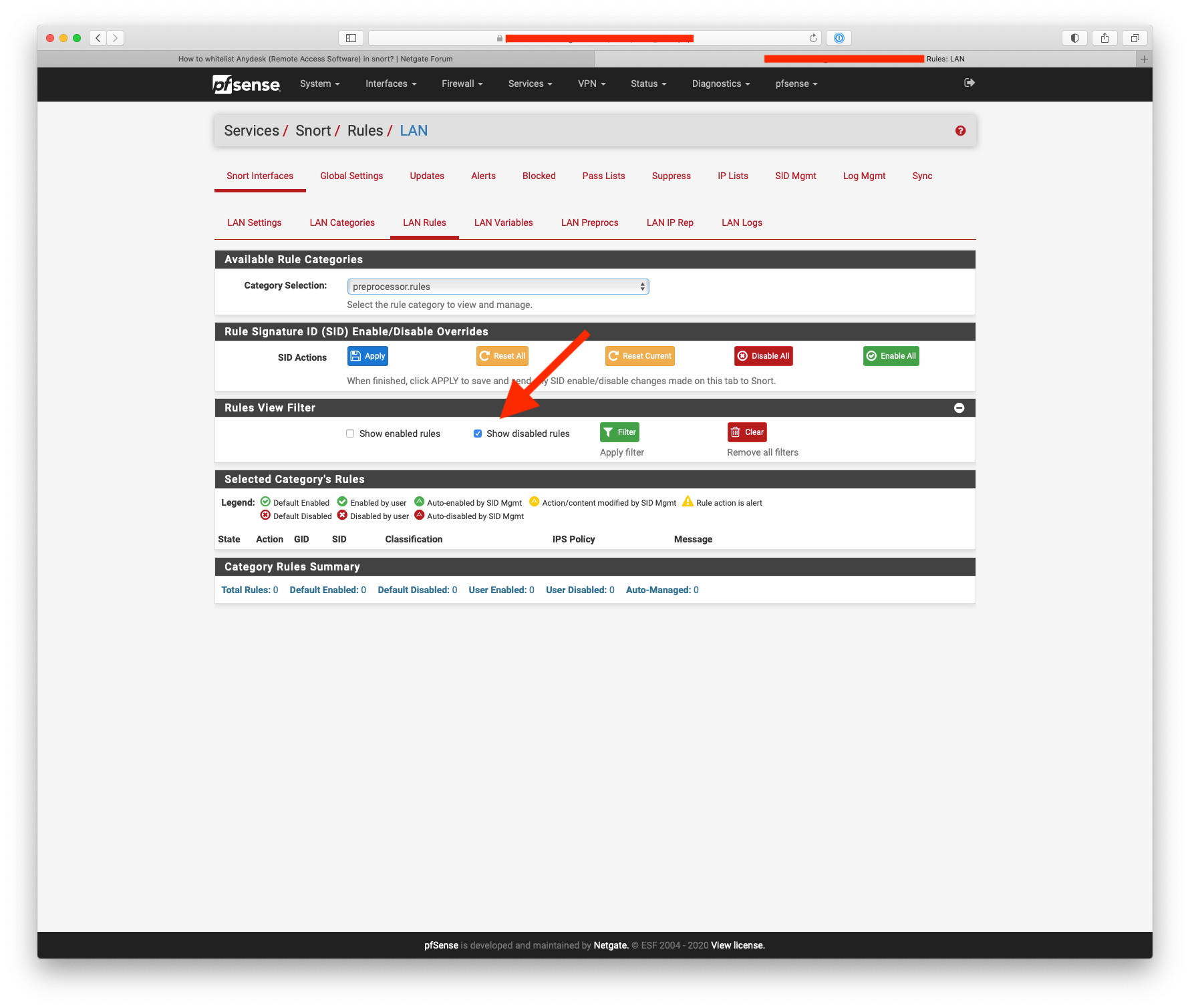
@bmeeks is the filtering option broken ?

It's not supposed to be ...
 , but I have not checked it lately. I will need to test it.
, but I have not checked it lately. I will need to test it. -
@NogBadTheBad:
I just tested the "Disabled Rules" filter on my firewall and it worked (in Snort). -
@bmeeks Thanks for your reply, the answer was short and I ve just got it from another fellow member here, I just need to suppress the alert, please correct me if I am wrong.
-
That must be :
-
@bmeeks said in How to whitelist Anydesk (Remote Access Software) in snort?:
@NogBadTheBad:
I just tested the "Disabled Rules" filter on my firewall and it worked (in Snort).Should it not also filter disabled by user rather than disabled by default?
As a test I disabled 1:49361 and it doesn't show:-
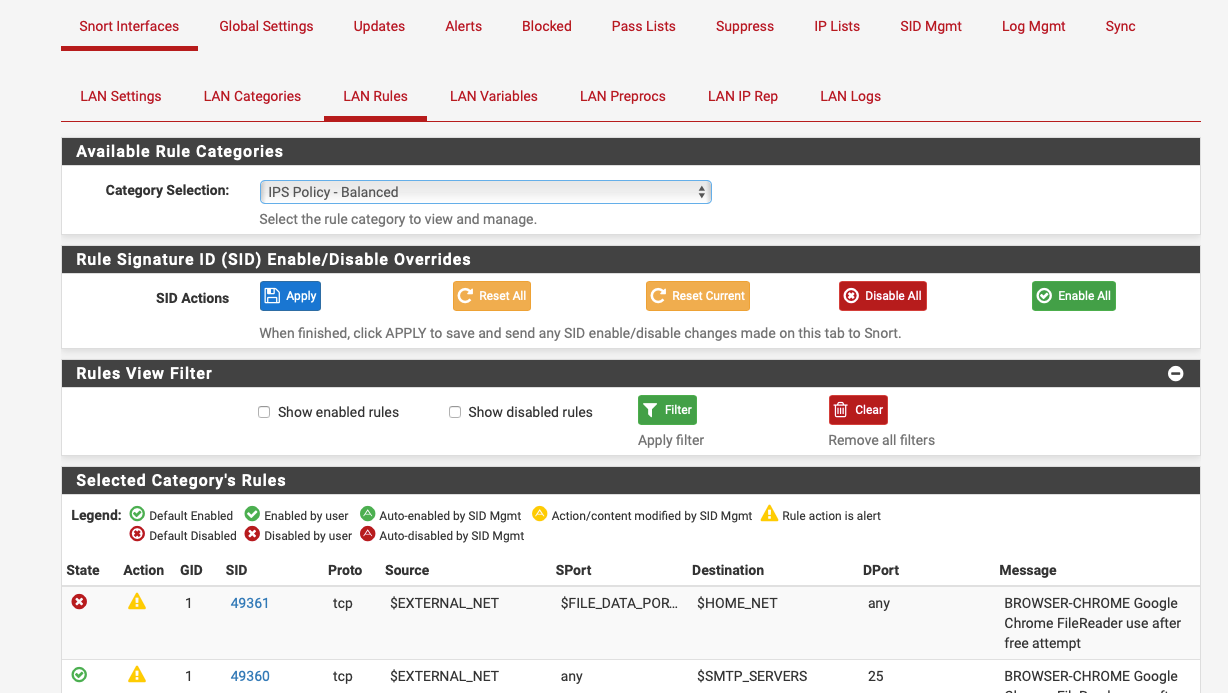
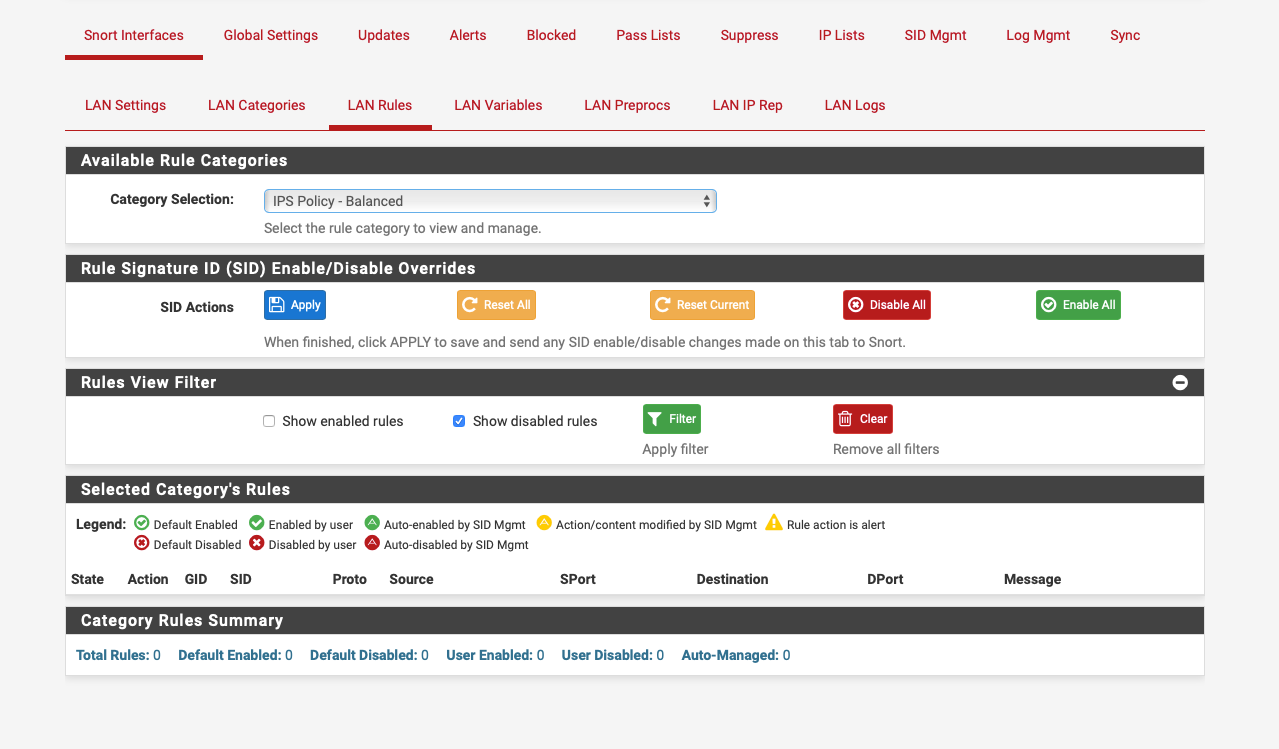
-
@NogBadTheBad said in How to whitelist Anydesk (Remote Access Software) in snort?:
@bmeeks said in How to whitelist Anydesk (Remote Access Software) in snort?:
@NogBadTheBad:
I just tested the "Disabled Rules" filter on my firewall and it worked (in Snort).Should it not also filter disabled by user rather than disabled by default?
As a test I disabled 1:49361 and it doesn't show:-


I need to check the code to see what it's doing. I know it catches rules disabled by SID MGMT configurations, because that's how I have a number of the HTTP_INSPECT rules disabled.
-
@noor92 said in How to whitelist Anydesk (Remote Access Software) in snort?:
@bmeeks Thanks for your reply, the answer was short and I ve just got it from another fellow member here, I just need to suppress the alert, please correct me if I am wrong.
I would instead suggest disabling those rules. They are highly prone to false positives. Suppressing them still loads them into memory, and CPU cycles are wasted evaluating traffic against them. They just don't generate alerts when suppressed. Disabling them results in them never even being loaded up, so RAM and CPU cycles are conserved for more important rules.