New Snort 4.0 + = dumb
-
This post is deleted! -
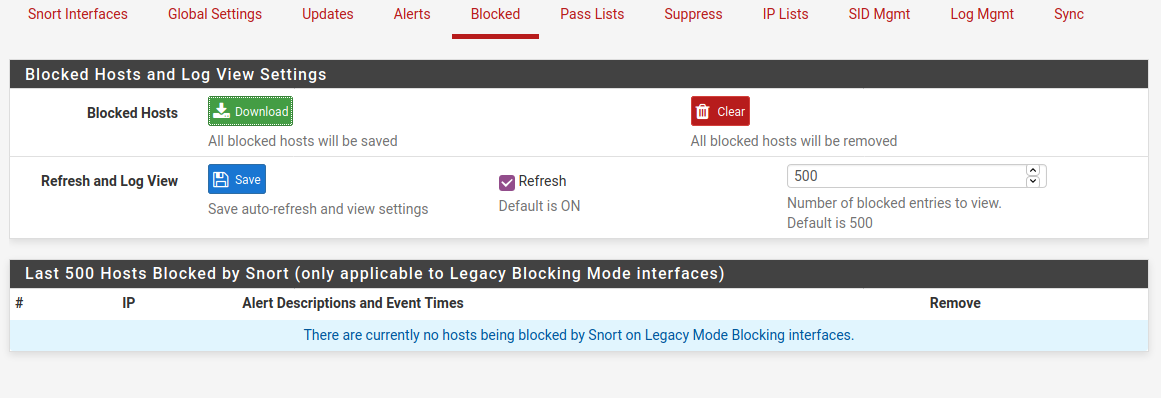
Blocked Tab is for legacy blocking not inline blocking.
-
"Blocked" really has no meaning with inline IPS mode. Drop is the key action for inline IPS mode. Block implies a host IP is not permittted to send/receive any traffic regardless of protocol or port number. That is not true for inline IPS mode. A given individual packet is "dropped" in that mode when a rule triggers, but other packets for the same host can pass unhindered assuming they do not trigger a rule. Thus inline IPS mode allows much more granular control of security by selectively dropping packets instead of simply blocking all traffic.
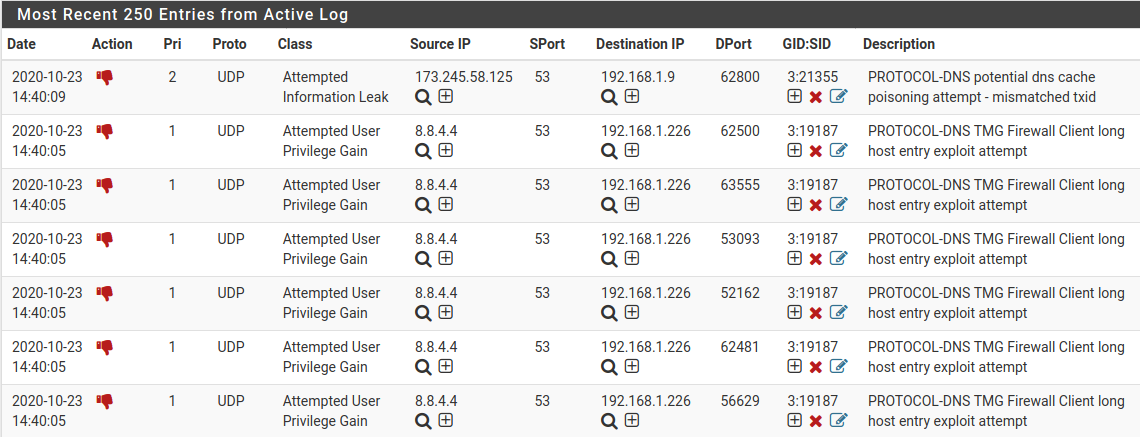
So when you use Inline IPS Mode, you need to look on the ALERTS tab and note the action under the ACTION column. Alerts that result in drops are also supposed to render in red text, but perhaps that's not working properly (I will take a look at the PHP code and see about that). The BLOCKS tab is worthless for all inline IPS interfaces. It is still relevant for any Legacy Blocking Mode interfaces, though, so that's why it's still present. Some folks have split setups with some interfaces using inline mode while others use Legacy Blocking mode.
Your question and statements indicate perhaps you are inexperienced with managing an IPS. Take a look at the Sticky Posts in the top of this sub-forum and read through some of them. They do a good job of explaining the differences between Inline IPS Mode and Legacy Blocking Mode. There are also some great reads about using the SID MGMT tab features to control your rules without "clicking each alert".
-
Just a quick recap
I use Suricata. Running mixed interfaces.
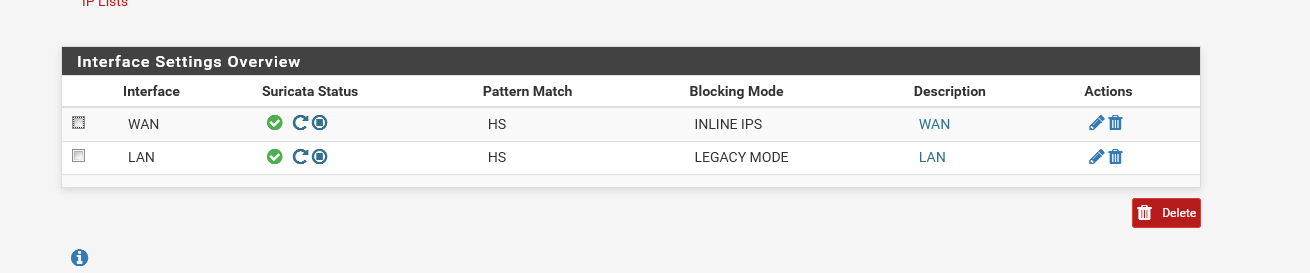
the funny thing is.... when running mixed mode, alerts from the Inline IPS shows up in blocked tab as well.
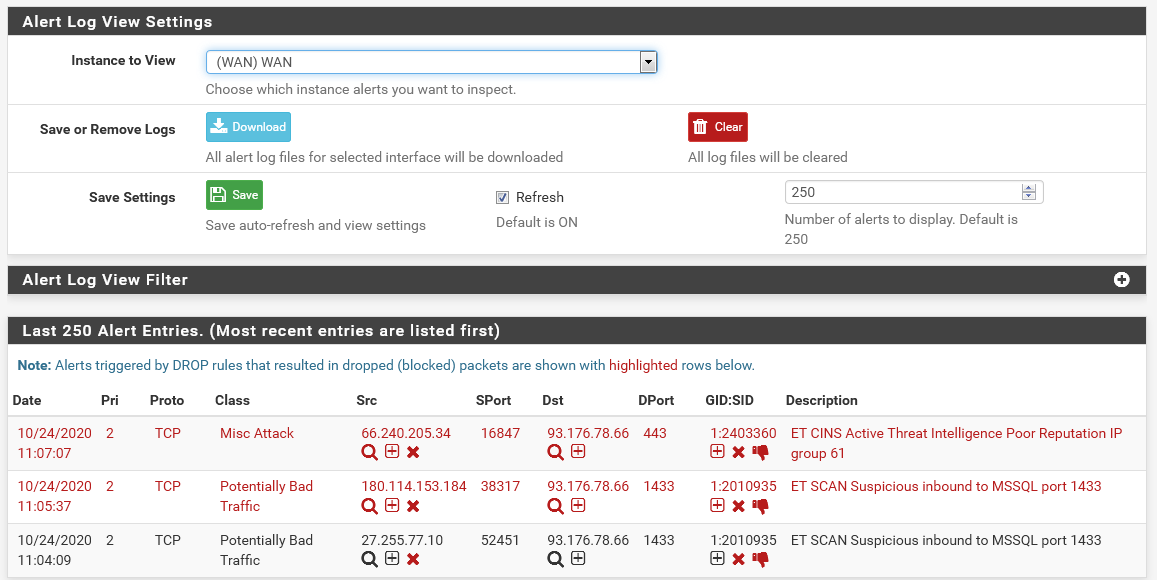
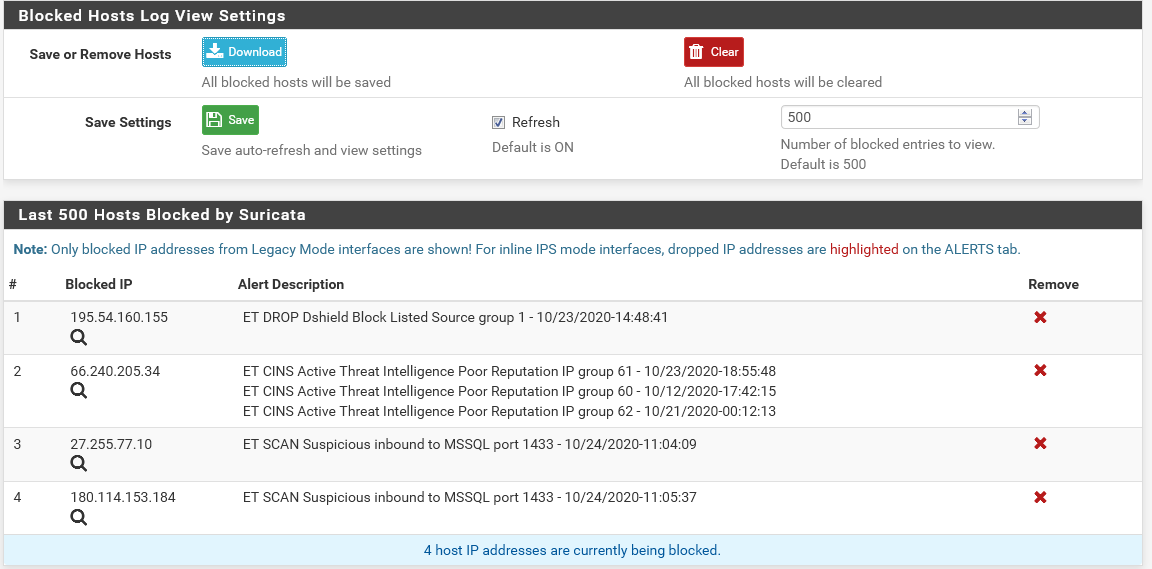
And it actually figures in the dashboard widget as well
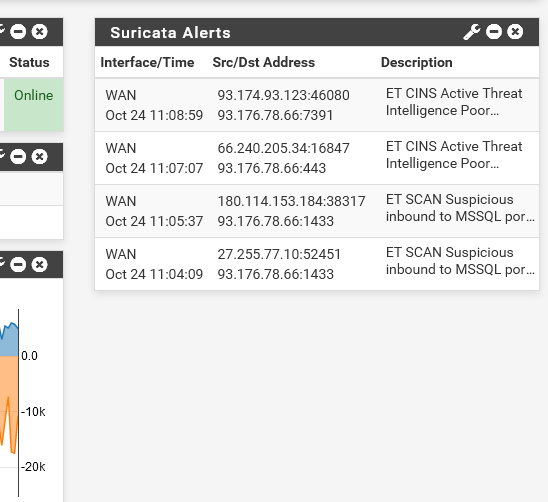
A note: I dont mind showing of my external IP. Its a home lab so nothing to get there if people decide to try

-
@Cool_Corona said in New Snort 4.0 + = dumb:
Just a quick recap
I use Suricata. Running mixed interfaces.

the funny thing is.... when running mixed mode, alerts from the Inline IPS shows up in blocked tab as well.


And it actually figures in the dashboard widget as well

A note: I dont mind showing of my external IP. Its a home lab so nothing to get there if people decide to try

The OP's questions were about Snort, not Suricata. There are some differences in how the binary portions of those two package log things.
-
Just out of pure curiosity - do you have 1433 open to the public net? Really? If not what is the point of the IPS, since that would just get dropped with any other traffic not sent to a port you have forwarded.
So some off topic advice - having 1433 open to the public net, not a good idea ;)
-
you should.. stop.. asking embarrassing questions



-
No I dont but I like to know who is knocking and where/when/what they are looking for.
Thats why. And you dont have to agree. :)
-
but you don't need suricata/snort to see it,
that traffic would bounce off the firewall
you just need the firewall log -
^ Exactly firewall log all of that by default..
Here is the last 2000 entries 180 of them have been hits to 1433.
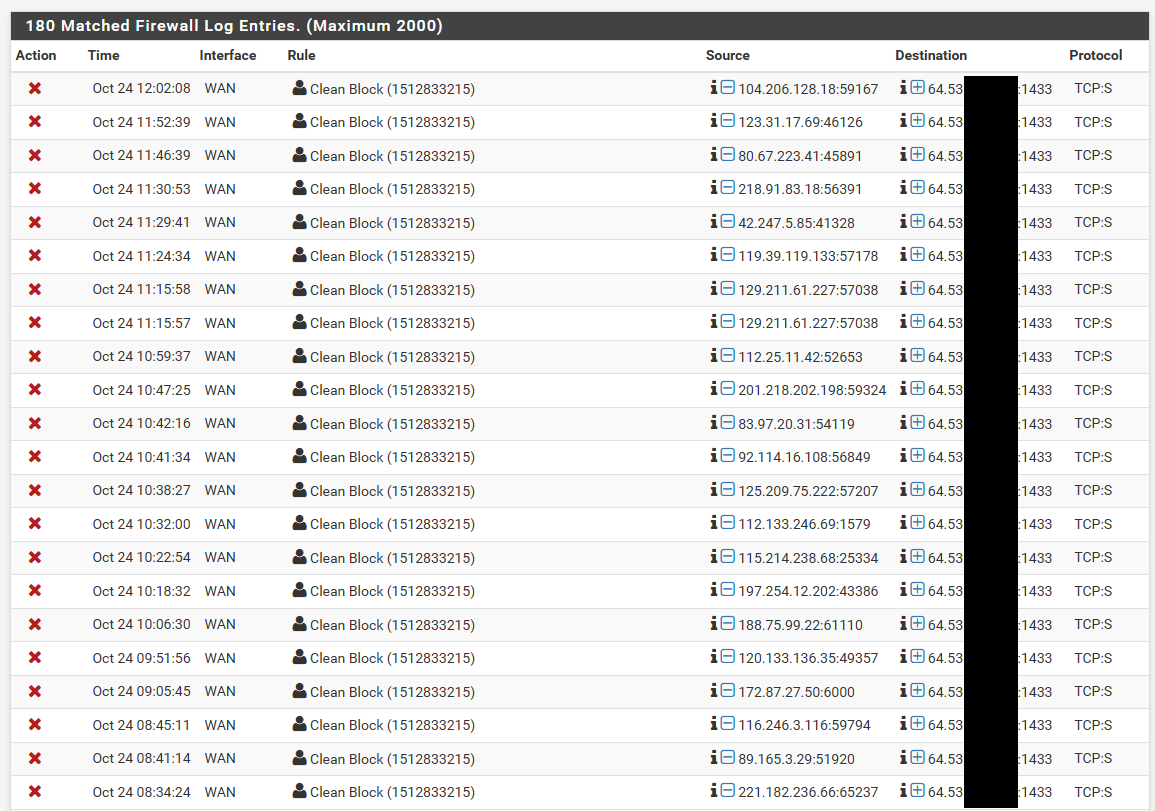
I concur that it can be interesting see what noise is out there, but there is little need of running IPS for that.. But there is a lot of noise. I turned off the default log because there is too much, I don't need or want to see out of state traffic.. I really only want to see stuff that sent a syn. And for udp its just way to much.. So I only log the interesting udp ports via another rule.
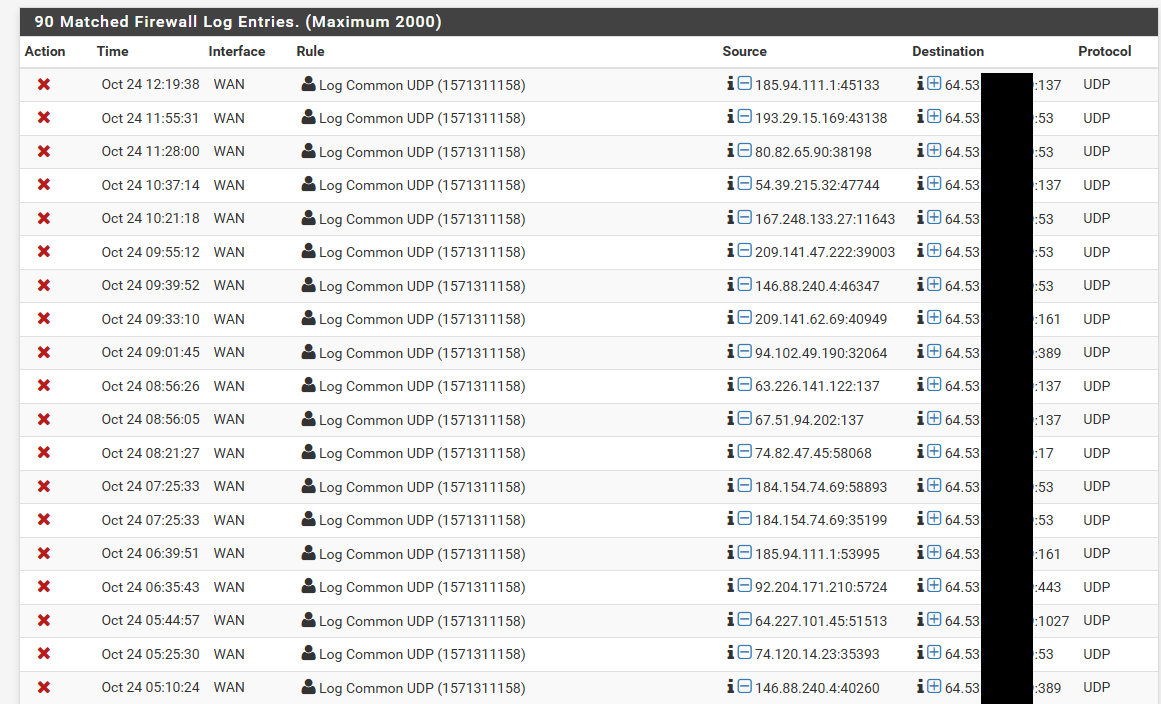
Your free to run what you want - but calling what you want to run, for really no other reason that your interested in what noise is hitting your wan, and then calling it dumb? That seems a bit odd to me is all.
-
@wolfsden3 said in New Snort 4.0 + = dumb:
I'm finding the new snort 4.0 + to be dumb and MUCH HARDER than the older version.
It seems like this new version of Snort is trying to solve problems that didn't exist and it's making all new problems. Maybe it's just me, dunno.
Any insight would be helpful.
If you choose not to enable Inline IPS Mode, then there is absolutely no difference in how Snort 4.x operates compared to Snort 3.2.x -- none at all.
If you choose to use the new Inline IPS Mode (and you have a netmap-supported NIC), then you do have to learn a few new things as the underlying technology behind Inline IPS Mode is fundamentally different.
If you do not like the new mode, then simply do not enable it and everything will be exactly the same as it was with the older package versions.