Setup for Routing - VLANS
-
tks for reply.
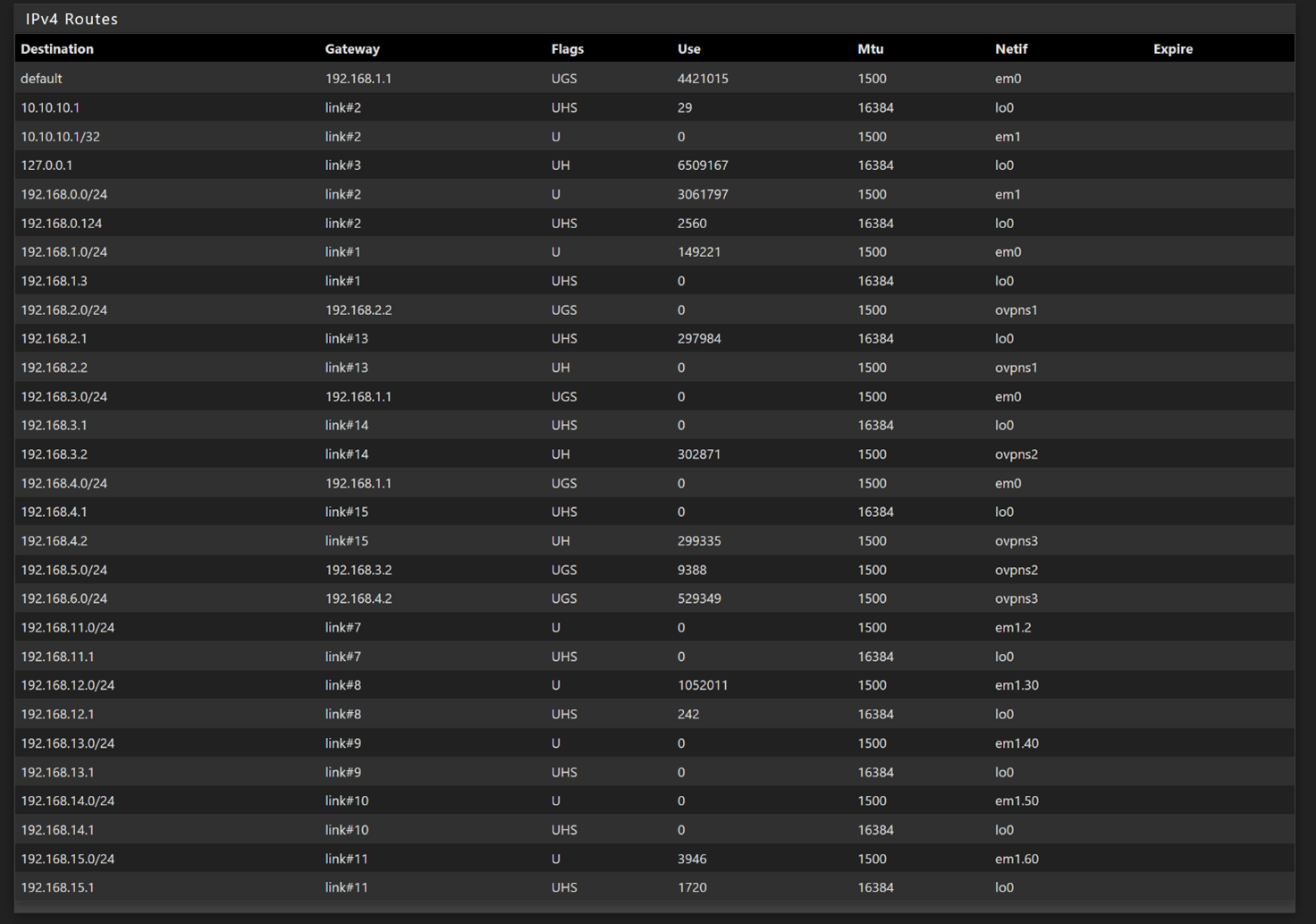
This my Routes
I are you forcing traffic out a specific gateway in your firewall rules?
Yes but for the moment I just check that it doesn't work with rules *With paket capture ping from my LAN to VLAN is (interface VLANprint)
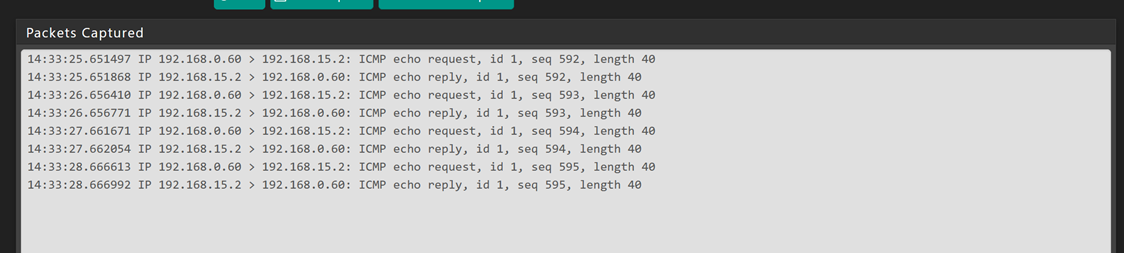
But if from the LAN I get the print command
Rules LAN
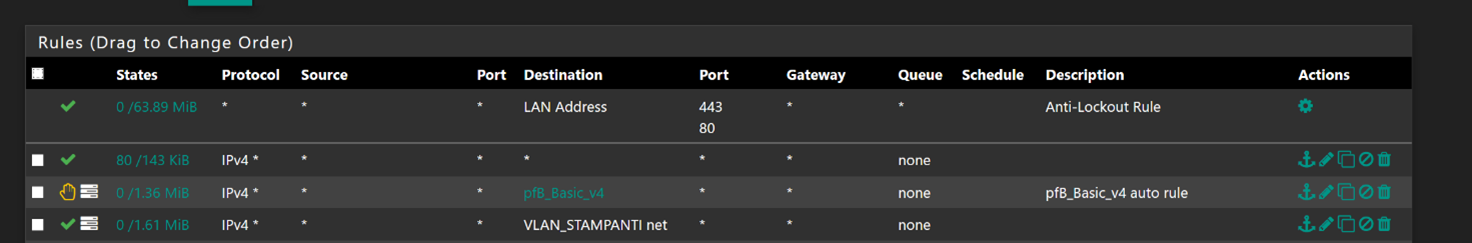
Rules VLAN
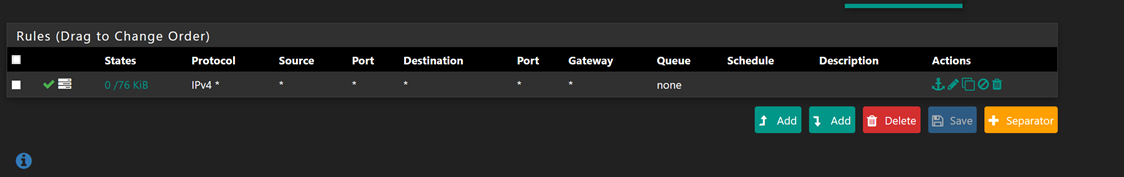
-
Bit confused.. Maybe you sniffed the wrong thing.. But if your seeing packets and answers on the vlanprint interface when you ping from lan, then the lan interface woudl also have to see that traffic.
Unless your pining just from pfsense itself?
You see seem to have a reject rule that that has hits on it.. What is in the pfB_basic_v4 alias?
edit: oh that is when you print..
Well if your not seeing anything hit pfsense to go anywhere when you try and print.. Then no pfsense can not allow or deny or route anything it does not see.. You need to check on your client trying to print, if your not seeing any traffic sent to pfsense, to get routed to your printer on your print vlan.
Even if the rule was blocking it - you would still see the traffic in the sniff.
example: Here I just sent a test print to my printer on a different vlan than my lan..
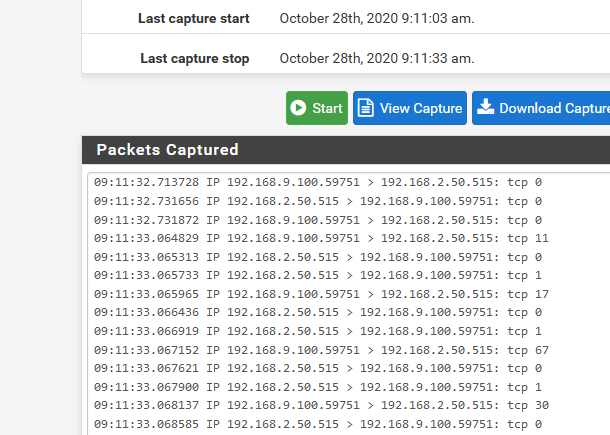
See the traffic sent to port 515 (LPD)
-
The pfB_basic_v4 is a default pfBlockerNG rule that blocks IP spam, so it should not interfere between LAN and VLAN.
However pfB_basic_v4 alias is the second rule and the first is *
Maybe there's some "bug" in pfsense?
Reinstallation?

Everything works between VLANs and the print command works too.
With Packet Capture LAN if I do a print test I have no trace of packets exchanged
So even though the first LAN rule is * there's something that prevents data passing – maybe something has corrupted in the LAN


-
@federicop said in Setup for Routing - VLANS:
However pfB_basic_v4 alias is the second rule and the first is *
Rules are evaluated top down, first rule to trigger wins, no other rules are evaluated.
Oh I see - what is the point of that bottom rule.. if you have an any any.. And since you have an any any rule above your pfB reject - that rule would never be used.. But you have hits on it - so you must of moved your rules around?
Again rules are evaluated top down... So if you have a any any rule on the top, when would that reject rule ever been used? What would not be allowed by an any any rule??
With Packet Capture LAN if I do a print test I have no trace of packets exchanged
Then your not talking to pfsense when you client wants to send traffic to the printer.. So how could pfsense allow or deny anything?
Sniff on your client when you try this test print where it is sending the traffic? Do you have some specific route on the lan client, is the lan client using some vpn software?
-
To do the tests I put lan and VLAN firewall rules * so as to go beyond all the other rules.
the lan client has this configuration
192.168.0.60 – 255.255.255.0 – gatway and DNS pfsenseIt doesn't have VPN software and if I work in remote desktop on a PC in VLAN it works, so I think the problem is some ruless that block – but if the first ruless is * how does it block?


The voip also has the same problem:
The voip server is in LAN and if a phone is in VLAN the IP address is assigned but I can't speak – the voip server does not detect the voip VLAN phone. -
this my configuration switch
GE4 - G10 - GE24 (is pfsense port - pfsense is virtual)All port 1UP is standard LAN
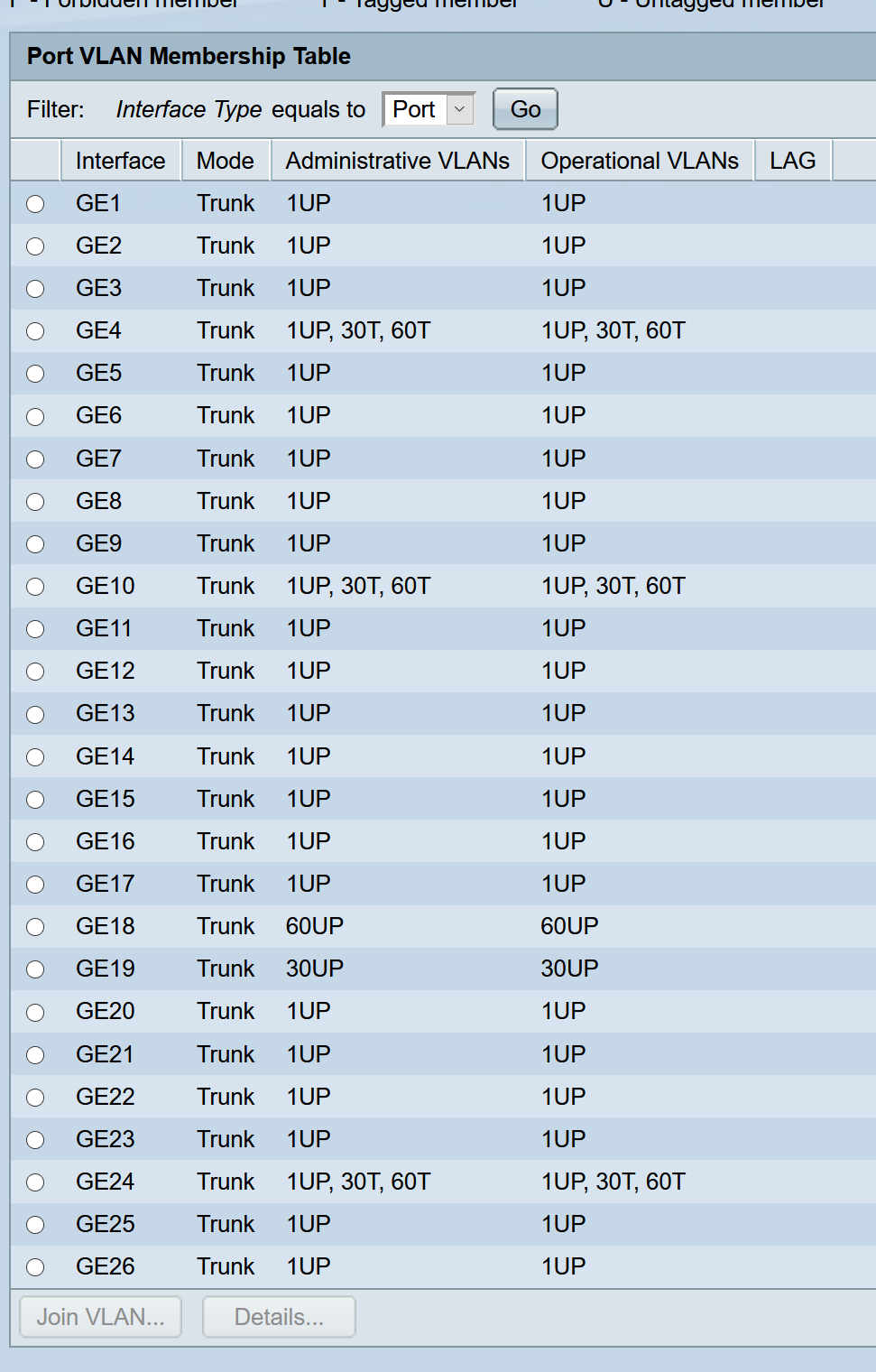
-
I assume this client can talk to pfsense, and use the internet through pfsense.. It pinged your printer right... But printing not working?
Lets state it again, pfsense can not route or firewall traffic it does not see.. If your sniffing on pfsense lan when you try to print.. And you see nothing... Nothing pfsense can do. Look to the client on why its not sending printing to pfsense to get to that IP on another vlan.
Doesn't matter what your firewall rules are - if you do not even see the traffic.. The interface will see the traffic via a sniff before any firewall rules are even looked at.
Do you have some print server on the lan that client is talking to try to print vs sending direct to device on print vlan?
You see traffic on the lan for this client when it uses the internet, when it pings say the vlan print IP of pfsense - right? So you should see traffic when it tries to talk to the IP on the printvlan.. If not - nothing pfsense can do.. Sniff on your client when you try and print.. Do you see it sending traffic - to where??
If your running vlans through a EXI server, are you allowing the tags to pass.. What do you have the vswitches setup as for vlans? 4095 needs to be set on port groups on your vswitches if you wan it to pass tags to pfsense.
-
The client reached pfsense
pings the VLANprinter and reaches printed web interface.If I launch printing from a VLAN1 client to VLANprint it works but if I do it from LAN and VLANprint no (same printer and client configuration).
The LAN Client seems to work in everything except for printing in VLANprint – for example, the remote desktop Client LAN and Client VLANPrint Works.
pfsense's exi virtual switch has vlan 4095 and dhcp works
the client is fisic no virtual - Virtual are only servers (pfsense and winserver)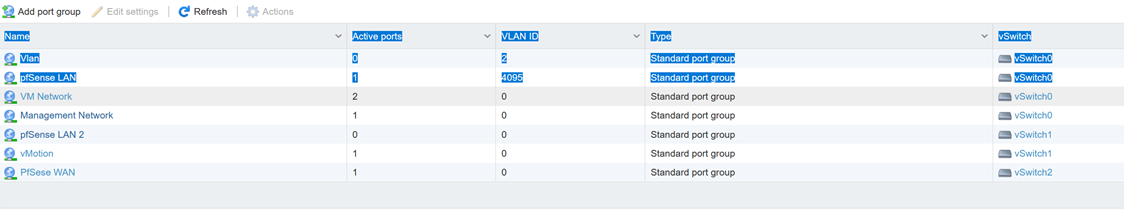
-
I fixed, the windows firewall blocked everything.

Now one last piece of information, if I have to force traffic out a specific gateway VPN (rules) my VLAN, have to set routes?
-
No again you don't have to set routes for anything connected to pfsense directly.
If you want to send a client out a vpn connection (vpn setup on pfsense to point to some service)
Then you would just policy route that via a firewall rule. Just making sure that you put any rules above that to allow local access (if you want)..
If you want to send clients trying to talk to 1.2.3.4 (publicIP) then sure you could create a route on pfsense for that dest network to use vpn connection. But that would really send any and all clients from behind pfsense out that vpn.
Better option is to just policy route what you want to use the vpn. Be it via either their IP/Net, dest IP/net or dest port, etc.
https://docs.netgate.com/pfsense/en/latest/multiwan/policy-route.html
Setting up a vpn client on pfsense creates a multiwan setup.. Since you have either your normal wan as gateway, or this vpn connection as a gateway.