Help with fw rules, vlan and LG TV (Miracast)
-
Hello,
I'm still new at this and maybe I'm trying to do something that is not possible. But I hope the collective can help. I also did a lot of searching, but I have not been able to find the answer to my situation. So here goes:TL;DR
I need help adjusting my FW rule to allow screensharing from Office VLAN to IoT VLAN. The devices can see each other, but my IoT FW rule (that prevents VLAN to VLAN communication) blocks the screensharing to complete. So what FW rule should I implement to allow screensharing sessions, but still block other VLAN to VLAN traffic?The setup
- Pfsense 2.4.5-RELEASE-p1
- Avahi 2.1_1
- Office VLAN (10.10.20.xx)
- IoT VLAN (10.10.40.xx)
- LG TV (Miracast) on IoT VLAN (10.10.40.50)
The Use Case
- Cast/Screenshare from Office VLAN to LG TV on IoT VLAN
Current status
I can discover the LG TV on my Office VLAN (Avahi is working). When I establish a screensharing session I can see in pfTop a connection "ESTABLISHED: ESTABLISHED" between my laptop (10.10.20.54) and the LG TV (10.10.40.50)But, the screensharing is blocked by my FW rule, that blocks access to Office and other VLANs.
Firewall Rules
These rules are in place to prevent traffic to flow between VLANS. Maybe there is a better way. FYI. my WAN address is part of RFC1918 range.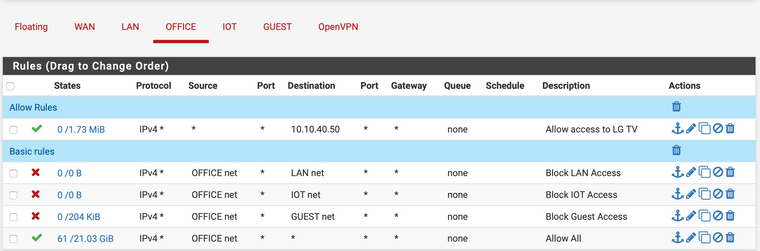
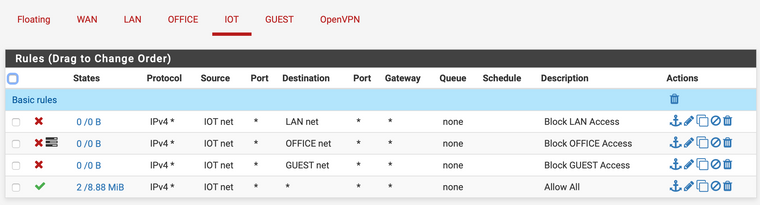
pfTop
As you can see, then there is an established connection form my laptop (10.10.20.54) to the LG TV (10.10.40.50)
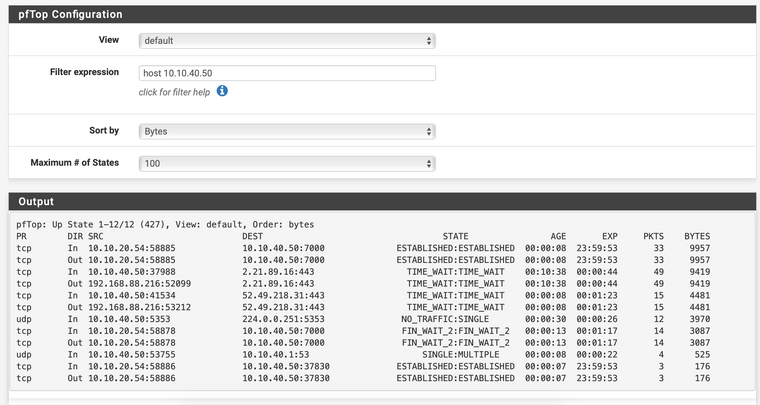
Firewall Log
And unfortunately then the session is blocked by my FW rule. If I disable this rule, then it works. But I thought that if the connection is initiated by 10.10.20.54 (Office) then 10.10.40.50 (IoT) would be allowed to respond on any port.
-
As it's UDP, there's no concept of a "session" - the TV is sending packets to the office LAN that are correctly being blocked based upon your rules
You could add an exception above the Block Office Access rule with:
protocol
IPV4 UDPsource
IOT netport
*destination
OFFICE netport
52499which would allow the traffic.. but it's not "return" traffic as far as the firewall is concerned, so it's blocking based on your current ruleset.
(you could make this more specific, if it's only the TV you want to allow - make the source the TVs IP address, and if the source port is always 35553 then add that too... if there are multiple TVs, you could create an alias for them and add them all in to that alias and use the alias as the source...)
-
@tehwolf
I'll test this, but as far as I remember, the the destination port that the TV is sending on is random (in this case 52499). I would assume that mira cast would have a range that I can define.I'll also take a look at the source port (35553) to see if that is static.
Thanks for the input and explanation.
-
@lipsum said in Help with fw rules, vlan and LG TV (Miracast):
@tehwolf
I'll test this, but as far as I remember, the the destination port that the TV is sending on is random (in this case 52499). I would assume that mira cast would have a range that I can define.I'll also take a look at the source port (35553) to see if that is static.
Thanks for the input and explanation.
Did you ever get this working? Can you please share your setup?
-
@logboss Not in a ideal way with specific miracast ports. I simply assigned the TV a static IP and added Allow rule from TV to Office Net and from the Office Net to the TV. So not they can communicate on all ports to TV IP.
Not great, but it works :-)
IOT Net Rule

Office Net Rule
