Block rule from Alias A to Alias B, to save copying rules
-
Hello all,
I'm configuring an SG-1100 box, to replace my Ubiquiti UniFi USG 3P. I now have the same VLANs set up in pfSense and they work on my UniFi switches. Now comes translating the firewall rules for those VLANs. Actually this is question #2 but I'll put it in a different topic so it will show up in other people's search queries.So in UniFi I could also define an Alias (UniFi calls them Firewall Groups). And I could create a rule From FW Group A to FW Group B. Example:
Firewall Group A "VLANs to block RFC1918 networks"
192.168.20.0/24
192.168.30.0/24
192.168.40.0/24
192.168.60.0/24
192.168.70.0/24
Firewall Group B "All RFC1918 networks"
192.168.0.0/16
172.16.0.0/12
10.0.0.0/8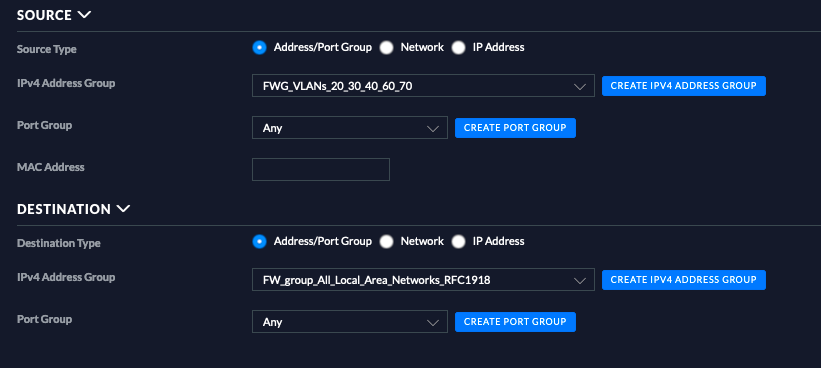
In this manner I only need one rule to block RFC1918 for 5 VLANs. In pfSense, I can see no other way than to apply a rule in one VLAN and copy it forth 4 times. This is more work.
Also, in UniFi if I add a VLAN I can simply add a subnet to the FW group and be done with it.Now I don't have a massive # of VLANs, this list is about it. But I like the ease of management: say if I want to change the rule I need to change it 5 times instead of one.
Don't get me wrong I really like pfSense so far and I am contemplating on substituting my USG for a Netgate box. Hopefully there is a way to do this "two way alias" trick in pfSense?
Many thanks,
Pete -
In pfSense you can use the floating rules tab for that. Rules you define here can be applied to multiple interfaces, no alias needed for that.
With "Quick" checked, the rule is applied befor rules on the interface tabs, without that, interface tabs rules have prio.
-
Excellent, thank you. I was peeking at the floating rules tab, however the docs.netgate discouraged me to try it. I will give it a go now

Edit: I see now how things can get confusing so I understand the docs.netgate warnings. In UniFi there is only a floating rule list of LAN IN rules.
Now that I am deciding on which of those rules should go to the floating tab and which should go into each VLAN tab, I see that I should proceed with care. As I understand the documentation, the following order is maintained:- Floating rules marked as Quick, top to bottom
- Rules in dedicated WAN/LAN/VLAN tabs, top to bottom
- Floating rules marked as non Quick, top to bottom
The example above goes in category 3: non Quick. So I need to make sure that none of the dedicated rule sets (category 2) are to be executed thereafter. This is doable in a one-time well thought out design. However, when making alterations to the category 2 tabs in a later stage, the floating rule tab and the interoperating order design could be easily overlooked, leading to a mess.
At this point I think the safest way to using floating rules is to start with only Quick rules, as they are the most straightforward. An example would be to allow multiple VLANs to Pass to VLAN 20 (printers) for printing. This should have the Quick checked and can be at the top of the list.
Pete
-
One thing I stumble across while translating the UniFi FW rules to pfSense:
In pfSense I have a guest VLAN50. When I go to Firewall -> Rules and click the VLAN50 tab, I have the following rules set up:
- Block IPv4 TCP / Source: Any Destination: "This Firewall" port 10443 (works fine)
- Pass IPv4 Any / Source: Any Destination: ! RFC1918
The second rule aims to pass any traffic except destined to the local area networks 10.0.0.0/8, 172.16.0.0/12 and 192.168.0.0/16. It is an exact copy of the rule I have in UniFi.
Except...it blocks internet traffic too. When I connect a client to VLAN50 I get no internet connectivity whatsoever.
When I disable the rule or when I only block the other VLANs, all goes well.
Is it impossible to block RFC1918 in pfSense this way?
Thanks, Pete
-
@Cabledude said in Block rule from Alias A to Alias B, to save copying rules:
As I understand the documentation, the following order is maintained:
Floating rules marked as Quick, top to bottom
Rules in dedicated WAN/LAN/VLAN tabs, top to bottom
Floating rules marked as non Quick, top to bottomOn position 2 there are rules on interface groups.
@Cabledude said in Block rule from Alias A to Alias B, to save copying rules:
At this point I think the safest way to using floating rules is to start with only Quick rules,
Most use the Quick option in floating rules.
An example to not check it could be allowing internet upstream traffic, while you have a block rule for certain destinations on an interface tab.@Cabledude said in Block rule from Alias A to Alias B, to save copying rules:
Pass IPv4 Any / Source: Any Destination: ! RFC1918
The second rule aims to pass any traffic except destined to the local area networks
It does exactly that. It matches and pass the traffic if the destination is not an RFC1918 network.
However, consider if you use pfSense for DNS resolution you will additionally have to add a rule allowing TCP/UDP port 53 to pfSense (a prime example for a Quick-floating rule).
So maybe you only can't resolve hostname with this rule. -
@viragomann said in Block rule from Alias A to Alias B, to save copying rules:
On position 2 there are rules on interface groups.
Yes actually that is what I meant
Most use the Quick option in floating rules.
Right, understood.
An example to not check it could be allowing internet upstream traffic, while you have a block rule for certain destinations on an interface tab.
I see
@Cabledude said in Block rule from Alias A to Alias B, to save copying rules:
Pass IPv4 Any / Source: Any Destination: ! RFC1918
The second rule aims to pass any traffic except destined to the local area networks
It does exactly that. It matches and pass the traffic if the destination is not an RFC1918 network.
However, consider if you use pfSense for DNS resolution you will additionally have to add a rule allowing TCP/UDP port 53 to pfSense (a prime example for a Quick-floating rule).
So maybe you only can't resolve hostname with this rule.You are most likely right that I also blocked DNS on LAN by using RFC1918. Can't check now I shut everything down it's bed time.
That is another difference then between pfSense and UniFi: Even if i block all local hosts (RFC1918), UniFi leaves the VLAN router address open (e.g. 192.168.50.1 for VLAN50 192.168.50.0/24).
To prevent users on VLANs connect to the UniFi Firewall (USG) I block ports 22, 80 and 443, thus maintaining DNS resolution.pfSense and UniFi appear to use a flipped approach in many ways. With UniFi when you create VLANs, no rules (default) means traffic can flow freely across LAN and all VLANs.
Kind regards,
Pete -
@viragomann
Just to confirm I added a pass TCP/UDP port 53 rule above the Block RFC1918 and now the clients on the VLAN have internet connectivity.Based on your input (pass port 53) I have found info on this subject on the Netgate docs pages.
Thanks!
Pete -
@viragomann said in Block rule from Alias A to Alias B, to save copying rules:
However, consider if you use pfSense for DNS resolution you will additionally have to add a rule allowing TCP/UDP port 53 to pfSense (a prime example for a Quick-floating rule).
I see your point, but I'm not sure how to define the floating rule destination. Objective: allow all VLANs to pass <interface> net to each respective <interface> address. I have VLANs 10, 20, 30, ..., 70. So I can select those VLAN interfaces as source, but what do I select as destination? Does VLAN10 traffic net need to route to VLAN10 address or can I simply select the LAN address - port 53 as the destination so all VLANs route to the LAN interface port 53?
Thanks,
Pete -
@Cabledude
You can set the destination to "This firewall". This is an implicit alias for all IPs assigned to pfSnese. -
@Cabledude said in Block rule from Alias A to Alias B, to save copying rules:
Excellent, thank you. I was peeking at the floating rules tab, however the docs.netgate discouraged me to try it. I will give it a go now
You can also use an interface group for that without having to use Floating rules - which can be a bit tricky. But Groups handle the same way as interface rules. No special in/out/quick/nonquick/select interface/rule mismatch :)
So if you want to define rules on all VLANs, just create a group "ALLVLANS" and put all VLAN interfaces in it :) Just remember that group interfaces are processed first, so if you block something in groups, there's no "passing it" later as it's already blocked :)
-
@JeGr said in Block rule from Alias A to Alias B, to save copying rules:
You can also use an interface group for that without having to use Floating rules - which can be a bit tricky.
Thanks! It'll be either floating rules or an interface group - I'll try both and learn new things.
@viragomann said
@Cabledude
You can set the destination to "This firewall". This is an implicit alias for all IPs assigned to pfSnese.Okay I will try that and see how it goes, thanks a lot you guys, this is a great place!
Now all I need to figure out is how to use my pfSense box to replace my ISP's fiber 200/200 / ipTV box and route VLANs 4 and 6 through the pfSense box using IGMP. Exciting stuff :-)