Making Best Use of Physical NICs & VLANs
-
Hi,
I'm trying to consolidate lots of boxes into a more streamlined system and have acquired a Procurve 2910al. With it's many ports, PoE and 10G ability, it meets all of my current needs.
But, I also want to make best use of the physical resources on my pfsenseVM.
Both pfsense and the switch are both far more capable than my ability! My head is spinning with the different ways of configuring both, particularly w.r.t. VLANs.
I wonder if I can pick your brains please, to have a look at my layout and judge whether I'm making best use of my available equipment.
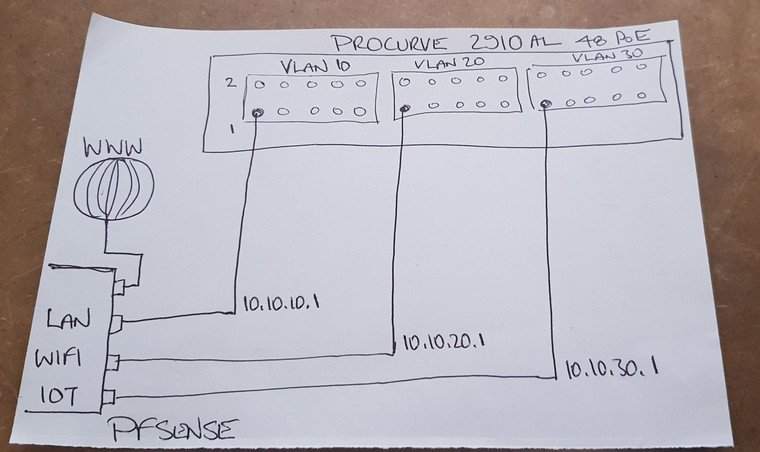
All feedback welcome.
TIA,
Paul
-
Looks ok.
For the ip ranges i'd go for something more uncommon like:
10.110.x.1 , and then just use x= 10 / 20 / 30 (match the vlan)Do you know that pfSense "can run" several vlans on/via one interface it's called vlan tagging (cisco calls it trunking) ?
I'd do like this:
Firewall IF
1: Wan (www)
2: Lan
3: Wifi/Iot (Tagged interface) : Separate vlans via vlan tagging (same cable)
4: Spare for future stuff.But what you have made (drawing) would work fine
Edit: Is your firewall 10G capable , or just the switch ?
/Bingo -
Thanks Bingo,
I've only just read about tagging whilst reading the switch manual about VLANs and their setup. Definitely something I'll bear in mind for the future.
Only the switch is 10g capable. My two servers and my main desktop are all on the same LAN. Certainly transfers between them are at near 10g speeds.
My pfsense is a VM on one of the servers with the 4 x 1g NICs being passed through to pfsense whilst the 10g stays with the bare metal server.
Are you hinting that there would be value in passing through the 10g NIC to the pfsense VM?
One thing that puzzles me with the switch is that I have had to enable DHCP on the VLAN 30 setup, in order for those devices to be able to see the internet. I thought that having pfsense handle DHCP meant that I would have to set the VLAN as static. It just seems wrong having the IOT server set to handle DHCP as well as the VLAN on the switch?
Attached is how IoT is configured.......... The devices on it are working..... I'm just not sure I understand how!
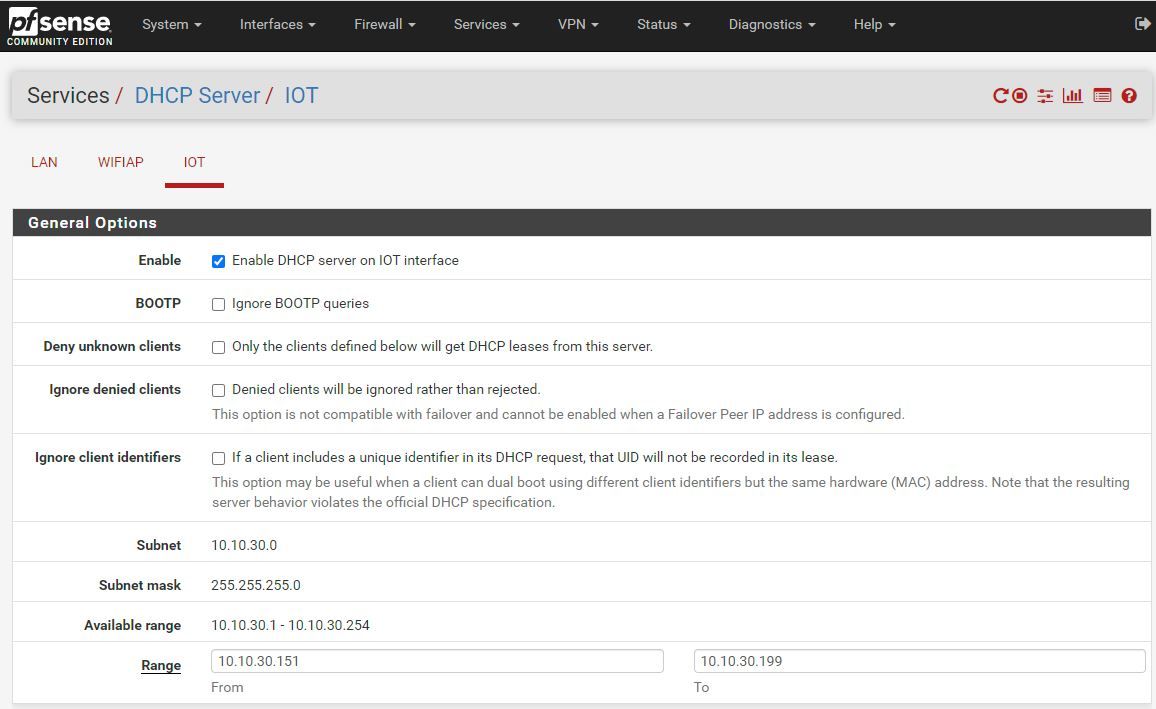
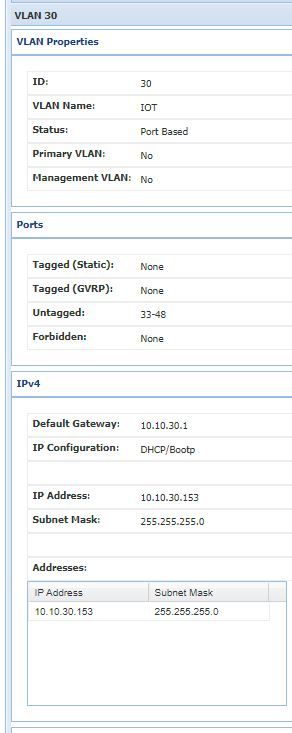
-
You should only have ONE dhcp server (per vlan) active at any time.
Else you risk getting overlapping leases.If you had to enable DHCP on the switch , then your Firewall IoT vlan is not connected to the Switch IoT Vlan , or you have DHCP Snooping enabled on the switch.
DHCP Snooping is a way to authorize (trust) certain switch-ports to pass DHCP lease messages.
You can test if dhcp works on the pfsense port by connecting a pc directly to the iot port , and see if you get an address. If you do ... dhcp is working on the pfsense. And it's the switch that somehow is preventing the dhcp to be passed. Either wrong vlan or DHCP Snooping.
Re: 10G to the FW ... I'd prob wait a bit , and get the feeling w. the 4x-1Gb card you seem to have. But it could be used in a later setup where you pass several Vlans down to the switch via 10G
/Bingo
-
Vlan
For HP's i only have a few HP1820's
You define the Vlan at one menu , but you define the Vlan members at another menu , on my switch thats port membership.
The port can have 3 states for the specific vlan shown (my Vlan was 100 in this example).
Untagged means it is sending/receiving normal lan frames aka. a normal lan port that is a member of the selected vlan.
Tagged - means the port tag's the data with a Vlan tag of the selected vlan
Excluded - This port has no relationship to the selected Vlan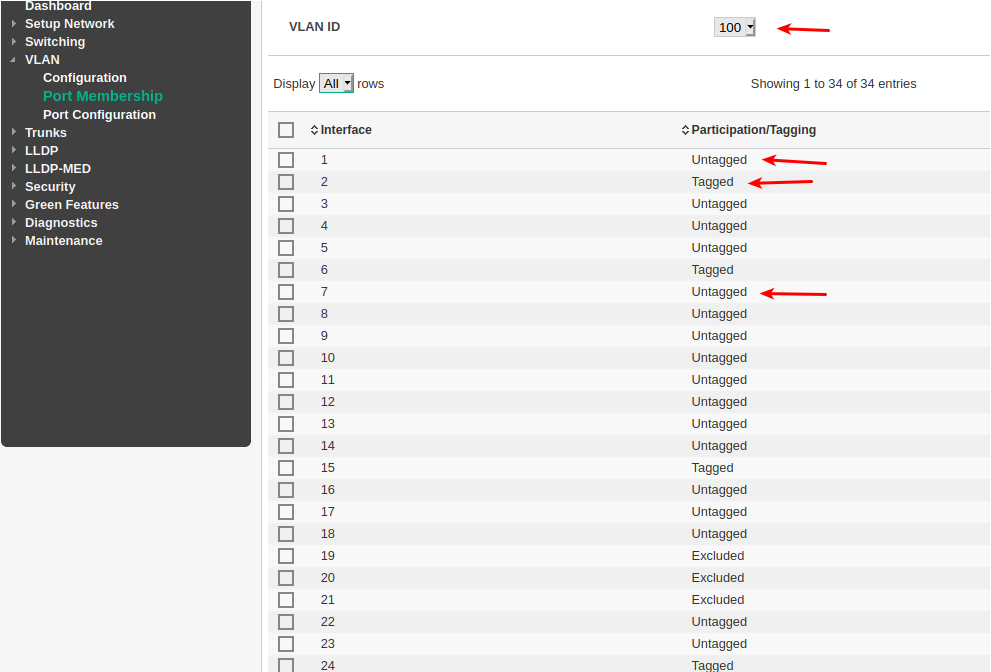
You would want untagged ports that are member of vlan 30 (IOT) , and pfSense IOT shluld be connected to one of those ports on the switch too.
-
A Vlan tag is like a "letter envelope" with the VLAN number as the envelope recipient address .
That way you can send multi vlan data , tagged, down the same cable, to multiple vlans. Because the correct recipient vlan is on the envelope (and data is in the envelope).
Once the envelope reaches the Lan interface that is set up for receiving taged packages, the device (pfSense or switch) knows to "open the envelope" and send the received data inside the envelope , to the Vlan stamped on the envelope (the tag).
Once the received data has been sent to the correct vlan , the device will send a copy of it to every port that is member of that vlan.
If the "member" port is untagged , it will not add any tags - aka that port will behave as a normal lan port (for a pc or whatever).
If the "member" port is tagged , it will be put in a new envelope (tagged) with the vlan stamped on it , and send out of that port.The same goes for xmitting data , when set up for tagging , the device puts the data in the envelope , and tags it (with the vlan) , and send it down the "line/interface/cable"
When the port is set up for untagged , the data is just sent out of that port. As normal ethernet data./Bingo
-
@pm1961
Once you get the hang of Vlans & tagginng, you could start to implement it in your system.For a simple setup like this one (3 vlans) , it might not be needed.
But it will give you flexibility, as ie. using tagging in your 10G interface would enable your VM's to talk 10Gb to separate Vlans (separation) , and let pfSense (VM) route and firewall traffic on those vlans.
Just backup (pfSense) / Snapshot a lot, while playing

-
Micro pfSense Add Vlan Guide
1: Create Vlan
Interface -> Interface Assignments -> Vlans

Press Green ADD in lower right2: Fill in Vlan data
Select interface to enable this vlan on
Add vlan number + description + Save
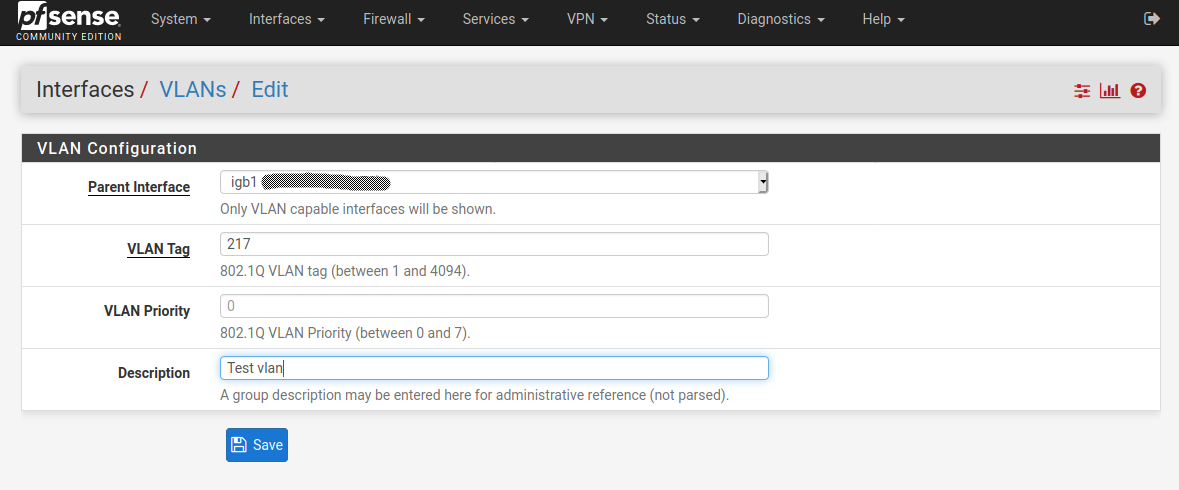
Now the Vlan has been created.3: Select the newly created vlan interface
Select it
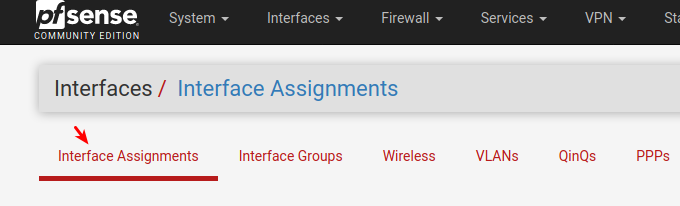
Scroll to bottom and find it in the pull down menu
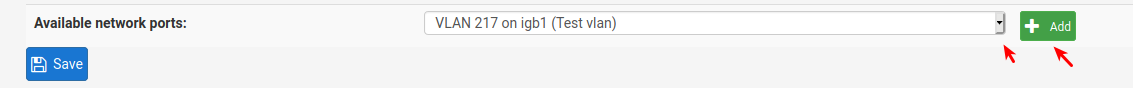
4: Fill in interface data , and enable it
Enable it
Prob change the description to a better IF name
Fill in IP interface address + subnet mask
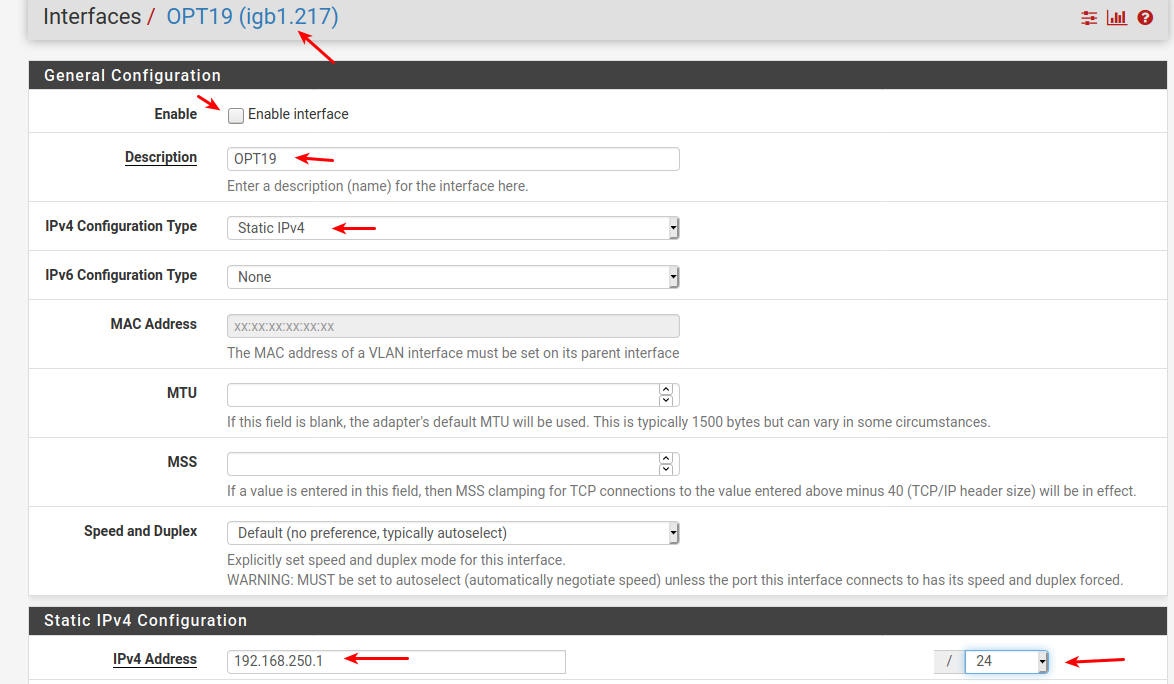
Save
Now you have created a new pfSense Vlan tagged IF.
Maybe add some dhcp server if needed.
Edit: I used 192.168.250.1 as ip net for vlan 217
I would prob have used 192.168.217.1 if real production , and i had the full control,Edit2:
You will have to match the config on your switch on the interface you connect the pfSense parent vlan interface to (i used IGB1)Create Vlan217 , make the switch interface a member of vlan217.
Set it to a tagged membershipDone ...
You should now be able to ping (allow ping) your pfSense vlan 217 interface , from any port that has a vlan217 membership.Thumb rule for ports:
Untagged is for end devices using normal plain ethernet (PC , IOT etc)
Tagged is for "transport" to other devices that runs tagged multi vlan transport (ie.switches, VM-Hypervisor master interfaces etc.)/Bingo
-
I'm not a VM/Hypervisor guru.
But the Vlan tagging could also be done in ie VMware ESXi (vSwitch) , and then "just" have it present normal (virtual) ethernet interfaces to the pfSense.If you have a lot of server (host) intercommunication that (vSwitch) ought to be faster than any physical interface you can present.
I seem to remember a Max IF limitation of ?? 10 ??
With the VMNIC3 ?? , driver.I have only used pfSense w. physical boxes.
/Bingo
-
@bingo600 said in Making Best Use of Physical NICs & VLANs:
You should only have ONE dhcp server (per vlan) active at any time.
Else you risk getting overlapping leases.Actually, multiple DHCP servers are permitted. While you can configure them with non-overlapping pools, Duplicate Address Detection is supposed to be used to avoid problems.
-
 B bingo600 referenced this topic on
B bingo600 referenced this topic on
-
 B bingo600 referenced this topic on
B bingo600 referenced this topic on
-
 B bingo600 referenced this topic on
B bingo600 referenced this topic on
-
 B bingo600 referenced this topic on
B bingo600 referenced this topic on
-
 B bingo600 referenced this topic on
B bingo600 referenced this topic on
-
 B bingo600 referenced this topic on
B bingo600 referenced this topic on
-
 B bingo600 referenced this topic on
B bingo600 referenced this topic on
