Not able to import CA certificate to use for OpenVPN Client
-
I perfectly understand now - why pfSense refuses this import.
because it is obvious, that my CA.cert does not fulfill the correct specification of a CA cert. - So now - until I get the other side to correct all this stuff - I am just curious if I can make some workaround to use this ca.crt like the OpenVPN Client under windows does
.... -
Another Info:
prior to opening this issue here I also tried to import the <ca>.crt into my Windows 10 '"Trusted Root Certification Authorities Store". This only because I suspected this cert to be somehow incorrect ;-). Windows does also accept this without warning!
So I already assumed the pfSense Software to be 'too strict' on this checking. But Its not up to me to judge who is doing it right or wrong here in this case ;-). -
remote-cert-tls server
ns-cert-type was deprecated long time ago..
Compress lz4?
Yeah that is not what I would call a current or secure setup..
-
@johnpoz said in Not able to import CA certificate to use for OpenVPN Client:
Yeah that is not what I would call a current or secure setup..
Yeah ok, but that's not the issue here, or is it? If the setup is not good/secure enough to be allowed to work we should file a bug with OpenVPN for that. But fact is I can connect with current version of OpenVPN but I can't with pfSense ...
-
Not a bug that you setup an insecure config..
Be it that the windows doesn't validate its actually a CA cert.. Have never tested that - but doesn't even look like your verify that..
The client should validate that CA is a CA and that your client cert was issued/signed by it..
I would have to do some testing on what exactly happens if you use some none CA tagged cert in windows client. But pfsense isn't going to let you install cert into the cert manager unless its actually marked as a CA..
I would suggest you get with whoever setup this openvpn instance to fix their shit ;) And compression is not secure.. What version of openvpn are you even using? Lets see the log of this connection..
You should see a verify at min.
exampleNov 10 06:12:04 openvpn 50634 VERIFY OK: depth=1, CN=OpenVPN CA -
I use OPENVPN GUI 11.20.0.0/2.5.0 and I get a Verify in the Log:

-
You only get the 1 verify.. You should see a verify for the server cert and the ca..
I would be curious to see who issued the cert your using.. Does it list the other cert as the issuing?
Can you verify it with the CA cert you have - example
C:\test>openssl verify -CAfile HomeCA.crt sg4860.crt sg4860.crt: OK -
@johnpoz said in Not able to import CA certificate to use for OpenVPN Client:
But pfsense isn't going to let you install cert into the cert manager unless its actually marked as a CA..
Thx, I got it :-) (some hours ago ;-) )!
Only question I have remaining is about a possible workaround. If there is none - ok, fine with me.....
-
Thats how opemnssl verifies the clients cert:
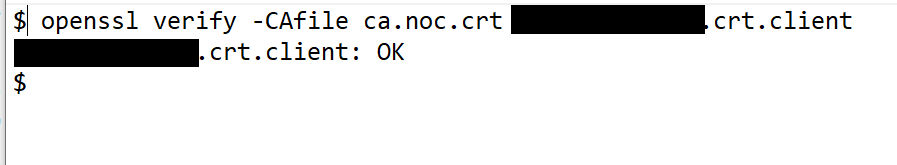
and yes, the ca is the issuer of the client cert. I already mentioned that I checked this with means of windows cert viewer. So to mee it all looks good - only thing missing is this one flag on the CA cert......
-
So the cert they created, just isn't marked as CA, but it was used to sign the the cert.. That is on the creator of the certs to fix.. Your just doing selfsigned..
As to a work around - I do not know how to import a cert into the cert manager as a CA, when it has not been marked as a CA
When they are creating the cert they are going to use as their CA, they need to set
basicConstraints=CA:true -
@johnpoz said in Not able to import CA certificate to use for OpenVPN Client:
basicConstraints=CA:true
Ok, thx. for that info. I will forward this....
-
I also mentioned this bug fix in my first message because I thought - then - that there is a distinction between 'usable' (-> make new signed certificates from this ca with help of pfSense and the provided private key for it) and 'trusted only' (chek if used as root for other certs). Then it could make sense only to check this "CA bit" if you also enter a private key on import ...
@RobertK66 said in Not able to import CA certificate to use for OpenVPN Client:
It seems that this issue: https://redmine.pfsense.org/issues/7885 introduced a check that my ca does not pass! But why is this? It's a valid cert and it was used to create my client/server certs ( I do not need it as a 'usable CA' as the bug report askes for to be checked when importing CAs).
Is there some other way I can import my CA as 'trusted CA' only and not as 'usable Ca'!?... but as I learned now. Every CA has to set its "basicConstraints=CA:true" to be accepted as CA. Thx. again for clarifying that.
-
I can't vouch that it wouldn't break anything but you could just edit the system_camanager.php page and comment out the validation check https://github.com/pfsense/pfsense/blob/master/src/usr/local/www/system_camanager.php#L171
Then import it. I don't recall if it's checked before use in OpenVPN frontend or backend so there may be some other similar checks to edit.
But the real fix is to use a proper cert. Just because OpenVPN/OpenSSL allows it today doesn't mean it always will.