pfBlockerNG-devel v3.0.0 - No longer bound by Unbound!
-
I'm trying to apply the update but the Package Reinstallation is hanging: Please wait while the update system initializes. I've waited over 30 minutes and tried rebooting the SG-1100 without success. Any ideas?
-
Thank you for the update and the effort you put into this project. This add-on is one of the main reasons I stick with pfSense.
We have a bunch of remote Sites running non-pfSense VPN Router with integrated DSL Modem. This remotes Sites are connected to our Data Centers by routed IPsec VPN, terminate on the pfSense where the DNS-Resolver with pfb enabled is hosted. Each site has a local resolver and forwards all queries for public domains to the pfSense in the Data Center over the VPN Tunnel.
@BBcan177 said in pfBlockerNG-devel v3.0.0 - No longer bound by Unbound!:
DNSBL Web Server is now bound to localhost instead of 0.0.0.0
Unfortunately this change breaks the usage of pfBlockerNG over IPsec for good. I cannot get the web server to reply to connections which come in over VPN.
Out of the box it doesn't work at all but with a custom NAT config it can be make functional.
When the Web Server is bounded on all Interfaces it was possible make this work by placing NAT Rules before the system generated rules to redirect the Traffic to the High Ports of the DNSBL VIP.rdr pass on enc0 inet proto tcp from any to 10.255.255.12 port = http -> 10.255.255.12 port 8081 rdr pass on enc0 inet proto tcp from any to 10.255.255.12 port = https -> 10.255.255.12 port 8443This was enough to get it working for Policy based VPN. If using VTIs for IPsec an addition floating rule with no state is necessary to allow the return traffic.
pass out quick on enc0 inet proto tcp from 10.255.255.12 to <net_vpn_all> port >= 1024 no state label "USER_RULE: Allow Stateless Replies from DNSBL VIP"I do understand that this is a limitation of pfSense/FreeBSD VPN and not a pfBlockerNG problem. Anyway it is possible to make the binding of Web Server to all interface or loopback a configurable option for future release?
If not - does anybody have an idea how to get this work when the service is bound to a loopback? -
@Artes
I can add this as an option in the next release as time permits.
In the meantime, you can edit the code to revert to 0.0.0.0.
Edit the file:
/usr/local/pkg/pfblockerng/pfblockerng.incAt line #1097 there is a function that builds the Lighttpd configuration file:
function pfb_create_lighttpd() {
}In that function you can change the lines with "127.0.0.1" to "0.0.0.0"
and change "::1" to "::/0" for IPv6. (haven't tested that myself, so hoping that this is the correct IPv6 address)
In the same file:
Edit line #1308:
From:
'target' => '127.0.0.1',
To:
'target' => '0.0.0.0',Edit line #1322:
From:
'target' => '::1',
To:
'target' => '::/0',Hope this works for you, Thanks for using the package, and and any support is appreciated.
-
I get to this...and then it takes forever...
[ DoH ] Downloading update [ 11/25/20 20:02:51 ] . cURL Error: 35
OpenSSL SSL_connect: SSL_ERROR_SYSCALL in connection to heuristicsecurity.com:443 Retry in 5 seconds...
. cURL Error: 35
OpenSSL SSL_connect: SSL_ERROR_SYSCALL in connection to heuristicsecurity.com:443 Retry in 5 seconds...
. cURL Error: 35
OpenSSL SSL_connect: SSL_ERROR_SYSCALL in connection to heuristicsecurity.com:443 Retry in 5 seconds...
.. unknown http status code | 0[ DNSBL_DoH - DoH ] Download FAIL [ 11/25/20 20:03:06 ]
Firewall and/or IDS (Legacy mode only) are not blocking download.Restoring previously downloaded file
No Domains Found! Ensure only domain based Feeds are used for DNSBL!
Assembling DNSBL database...... completed [ 11/25/20 20:03:19 ]
TLD:
TLD analysis.............................. completed [ 11/25/20 20:08:33 ]
TLD finalize....................... -
From the CHANGELOG :
FEEDS: Removed discontinued Heuristic Security DoH FeedRemove this URL. Use the Feeds tab to update your Groups
-
Hi,
Do we have CNAME blocking now? Thanks and as always amazing job!
-
@vjizzle
Yes its there in the DNSBL Tab with the other Unbound Python mode features. -
@BBcan177 said in pfBlockerNG-devel v3.0.0 - No longer bound by Unbound!:
Edit the file:
/usr/local/pkg/pfblockerng/pfblockerng.inc
At line #1097 there is a function that builds the Lighttpd configuration file:
function pfb_create_lighttpd() {
}Editing this function works fine for me. There is no need to edit lines #1308 and #1322 - These are for the NAT Rules and should stay as they are.
Thank you!
-
This post is deleted! -
First of all, great job on this release!
I'm currently running 3.0.0_1 with 'Unbound python mode' enabled in DNSBL.
While viewing the Reports tab I saw that the If and Source columns show 'Unknown' within the DNSBL Python alert entry's.Any suggestion how the fix this?
-
@SachaH said in pfBlockerNG-devel v3.0.0 - No longer bound by Unbound!:
Reports tab I saw that the If and Source columns show 'Unknown' within the DNSBL Python alert entry's.
https://forum.netgate.com/topic/158597/interface-and-source-is-unknown-running-devel-3-0-1/5
-
@RonpfS Thanks


-
also https://www.reddit.com/r/pfBlockerNG/comments/k1137y/reports_dnsbl_python_unknown/
-
This post is deleted! -
and https://www.patreon.com/posts/nov-update-43770381
-
Thanks BBcan177 for your great work,
For info, get yellow icon for DNSBL widget due to following error.
2020-11-27 21:33:25,736|ERROR| [pfBlockerNG]: Failed get_q_name_qinfo: in method '_get_qname', argument 1 of type 'struct query_info *' -
@HuskerDu
Do you have any of these options enabled in the DNS Resolver?DHCP Registration:
- Static DHCP
- OpenVPN Clients
If so, disable those options, clear the py_error log and Force Reload - DNSBL and see if the error returns.
-
@BBcan177
The options were removed after I've read the doc, but first launch after the install must have triggered the error.Thanks, clearing the log file solved the yellow icon "issue".
Regards,
-
with v3.0.0 load on my Firewall is significant reduced when running large Set of DNSBL Lists (~3 Million Domains).
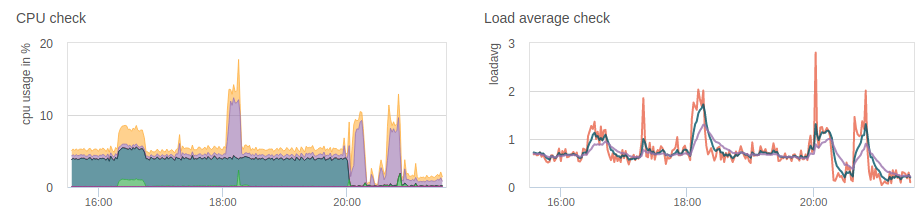
I don't see the unbound-control process spinning up every couple of seconds anymore.
Well Done

-
Thank you for your effort!
Everytime I do a RELOAD the skew on the backup CARP gets its value set to 0.
This causes the backup machine holding as CARP master when the Master machine comes online again.
I'm running 3.0.0_2