OpenVPN LAN can't talk to VPN Clients
-
Hey everyone I'm sorry if this is a stupid question but I've been trying to fix this for the past few days and no solution I've found online has worked.
To summarize what I'm trying to do, I have a pfsense box running in my apartment as my main router. I have one LAN with the IP range of x.y.z.0/24. I am currently trying to get an OpenVPN server working for my phone and laptop.
I followed a tutorial online and was able to connect to the OpenVPN server and by adding a push route command in the server config I was able to ping my LAN. (the OpenVPN server does have a different IP range that is outside of the LANs a.b.c.0/24) This is where I started to have problems, I am able to ping all of my LAN devices from my Laptop on a different network connected in using my OpenVPN but I am unable to access any of my LAN device's web interfaces. This led me down a rabbit hole where I found that none of my LAN devices can ping my OpenVPN clients. After this, I looked at my routing table on my desktop on my LAN and found none of my LAN devices have a route to my a.b.c.0/24 network. I then looked at my pfsense routing table and found that the route for a.b.c.0/24 was through a.b.c.2 as a gateway which is a client on the server, pfsense has the a.b.c.1 address. I also tried to ping the OpenVPN clients through pfsense and I was able to ping them using the default source address setting but when I set that to LAN the ping fails. The OpenVPN server was setup using the wizard and I have created a new OpenVPN server with a different IP range and the same thing happened with the new range. Also, the VPN is a remote access not a peer-to-peer I'm not sure if this could be the problem as well but from what I understand a remote access VPN should be fine for this case.
Sorry for the long post I just wanted to try and give as much information as I could. Thanks for any help.
-
A lot of troubles will go away if you set this in the OpenVPN server.
You will be forcing your clients to use the pfSense as default gateway , and all pfSense nets should beknown toreachable from the client.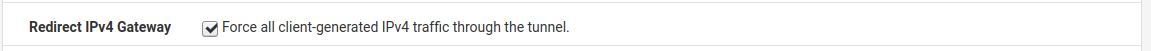
You don't need a specific route in your Lan devices to talk to your Clients, just make sure your Lan devices has the pfSense as default gateway.
You have to put some allow rules on the "Auto generated OpenVPN Group-interface" , in order to allow incomming traffic from your Clients.
If you have chosen a "random /24" as OpenVPN Client subnet , make sure you allow that in unbound DNS resolver (accesslist) , else you will not be able to use the pfsense as DNS server
/Bingo
-
Thanks @bingo600 thanks for your response I already had the Redirect IPv4 Gateway checked. The rules in the firewall for OpenVPN were auto-generated and as far as I can tell all my traffic is getting through. I am able to get internet through the VPN and I can see the LAN. I think the issue might be coming from the LAN devices not knowing how to get to the VPN clients properly but this is just my running theory.
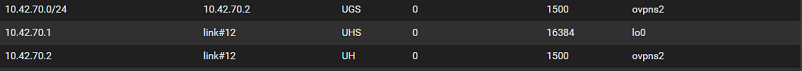
Here are the relevant routing table entries (10.42.70.0/24 is my openVPN network). I can ping 10.42.70.1 from inside the LAN but I can't ping my laptop at 10.42.70.2 from inside the LAN when it's connected to the VPN
-
@jrj2011 said in OpenVPN LAN can't talk to VPN Clients:
I can't ping my laptop at 10.42.70.2 from inside the LAN when it's connected to the VPN
Have you allowed "pings" traffic on the LAN interface , to ping the "Client net" ?
Edit:
Watch out for an active Windows Firewall , that could block stuff too -
Yes, I have a firewall rule under the LAN interface that allows any packets with the destination network of 10.42.70.0/24 (VPN Network). I can see packets hitting this rule when I ping from inside the LAN but they just time out.
-
Just to recap
You can ping from VPN Client to Lan devices , but not from Lan device tp VPN Client ?
-
Thanks for all your help your comment about the windows firewall got me to look at it a different way. Turns out during one of my previous attempts to get internet to my VPN clients (a different issue not this one) I messed with some other firewall settings and pushed all of the VPN traffic out the WAN interface which worked fine for getting my clients internet access but caused issues when I tried to access the LAN. I removed that and now with the push route command my clients are able to access the Internet and my LAN