openVPN different sites same WAN IPs (tricky homeBrew)
-
Ticky homeBrew Situation.
The Provider Modem only allows to open a port for openVPN (1194 UDP&TCP)
The pfS Box gets a 10.0.0.0/24 for its WAN-IF. LAN and openVPN IP Ranges can be set at will :)The goal is to connect all 3 purple / yellow / green with eacht other.
The Problem if it is one ... that there is no way (cuz not wanted by the provider) to change the 10.0.0.0/24 range.dyndns and an port forwarding for openVPN is working and supported by the ISP (and working afaik)
before i start wasting time of trying to get a connection road warrior Style and hittin walls, maybe someone can help here pointin some problems to not run into.
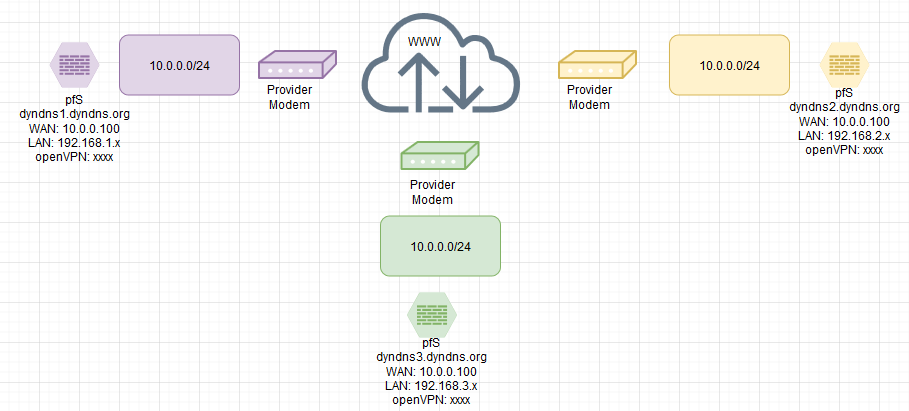
If i m gettin this right, the pfs should set up an on demand openVPN tunnel to another site (purple / grenn / yellow)
Oh and yes changing the ISP (Provider) is not possible.
thx in advance
brNP -
From your drawing 10.0.0.0/24 looks more like a transfer network and not the WAN IP. The WAN IP would be the red circle.
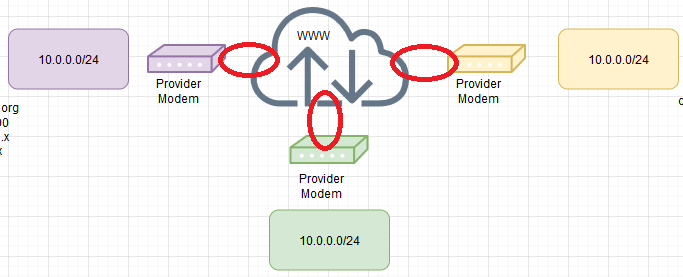
As long as you have one site with a Internet routable IP address you can run a hub-and-spoke OpenVPN, for full mesh you need all Sites with a routable IP address.-Rico
-
i thought that i have to put more info in the grap ... here we go
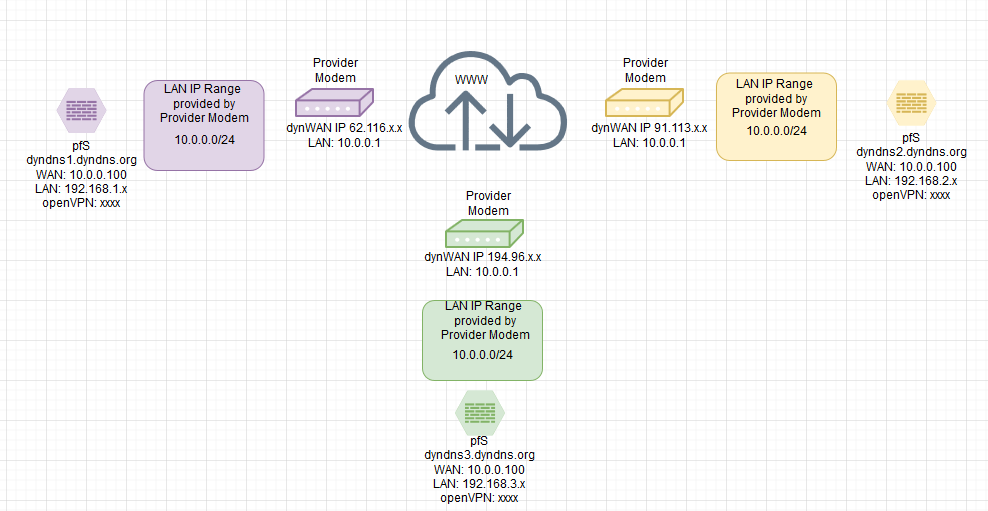
each Modem gets a IP from the ISP
purple ... 62.116.x.y
yellow ... 91.113.x.y
green ... 194.96.x.ythose IPs are gonna change every 8 hours (therefore the dyndns accoounts)
the pfS box is connected to the modem and receives the 10.0.0.100 (this Range is not changeable, yes it might be possible to get something like purpe .. 10.0.0.10 yellow 10.0.0.20 green 10.0.0.30)If I'm gettin you right, as log as my openVPN IP adress Range is differnt for each color (purple yellow green) i wont run into any problems ?
br NP
-
@noplan said in openVPN different sites same WAN IPs (tricky homeBrew):
LAN and openVPN IP Ranges can be set at will :)
...
The goal is to connect all 3 purple / yellow / green with eacht other.
...
dyndns and an port forwarding for openVPN is working and supported by the ISP (and working afaik)Those 3 statements are normally all you need to have. So to recap that:
- WAN IPs are private and set to a 10/8 subnet
- LAN can be defined (by you?) so to NOT overlap with each other
- OpenVPN is reachable via internet in all 3 locations(?) via port forwarding
So if you can connect via OpenVPN to all 3 locations correctly AND can define the LANs as per your plan (I'd suggest using more space in between like 192.168.10/20/30.x but OK), that's all you need.
As long as the 3 pfSense instances can connect to each other in any way you want (star, hub/spoke, any2any...) via a tunnel setup, I see no problem in connecting the 3 locations. As they only communicate via their LAN IP ranges and they are separated from each other, the routing should be fine. And if you set up the ranges more along the CIDR ranges, you can even simplify your routing via OpenVPN further.
But to give an example: Site A would reach Site B and C via routes 192.168.2.x/24 (ovpns2) and 192.168.3.x/24 (ovpns3) given that both are connected via a site2site tunnel to A. WAN and WAN IP is only interesting in Site2Site tunnel setup but there you'd only have to use the "server" site (e.g. Site A) and perhaps if you'd want direct comms from B to C another tunnel between them.
Just a small hint at last: use the site with the biggest bandwith as "main site"/server site. If you don't have one really bigger site, take one with static IP. Makes Client->Server site2site VPN setup easier then relying on DynDNS.
-
Don't put any hosts in one of the 10.0.0.0/24 networks and you'll be fine.
@noplan said in openVPN different sites same WAN IPs (tricky homeBrew):
those IPs are gonna change every 8 hours
Nasty stuff, means the pipe goes down during working hours?!
-Rico
-
@noplan said in openVPN different sites same WAN IPs (tricky homeBrew):
those IPs are gonna change every 8 hours (therefore the dyndns accoounts)
WTF? That's against any regulation I'm aware of.
-

-Rico
-
8 hours yes i dont know why but thats what the log files say
i hope its not worse and configured als on demand connect ... oh boy we got some crazy stuff here ;)when the pipe goes down there will be the next issuse how to bring the tunnel up again
(watchdog ? )there is no other way than dyndns (at the moment)
as far as i got the memo the 10.0.0.0/24 network is only used by the Provider Modem and the WAN interface of the pfS box.
i'll give it a try tomorrow to set up openVPN Server on each color ;)
not thinkin thaht this will be fun ;) -
OpenVPN tries to (re)connect infinite by default.
-Rico
-
@Rico
oh yesss ... thanks -
You need to take care about the DynDNS to update the IPs as fast as possible then.
-Rico
-
yes that will be a challenge,
i'm not sure whats a better way to go get a goDaddy DynDns or use dynDns pro accounti dont like this setup, these 8 hours .... SO NOT COOL !
-
As long as you can do DynDNS to the "real" address it's probably fine. Though depending on your budget and throughput needs it might be more stable if you had a hosted/DC/cloud/whatever type server with a static address and then all these dynamic clients connect to that. Then their address changes wouldn't matter. They'd timeout and reconnect in 60s and that's that.
-
yes i can get dyndns working with the real IP assigned by the ISP
so something like this
purple ... 62.116.x.y ... dyndns1.dyndns.org
yellow ... 91.113.x.y ... dyndns2.dyndns.org
green ... 194.96.x.y ... dyndns3.dyndns.orgthe budget in COVID times is slim to n00thing
thx for the hint with the static IP gonna look into it.