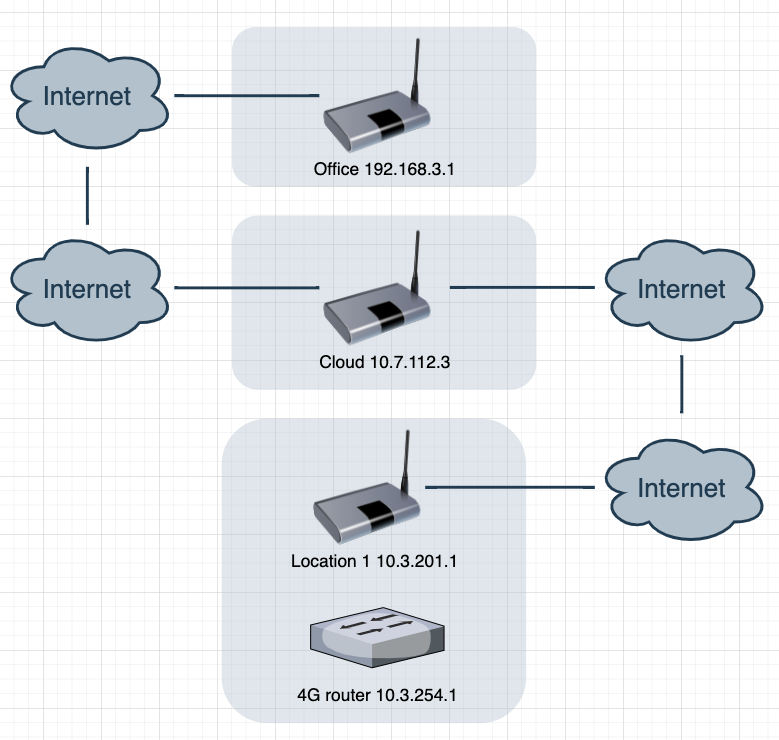
Connect trough vpn to outside 4g router
-
Add the 4g routers IP to the "Remote networks" in the OpenVPN settings at both the office and cloud, if that isn't already done.
And add an outbound NAT rule at location 1 to the interface the router is connected to like:
If the outbound NAT is in automatic mode, switch it to hybrid mode first.
source: office LAN (where you want to access it from), any if you want.
destination: the routers IP
translation: interface address -
-
Tunnel settings cloud->location1:
IPv4 Tunnel Network: 10.7.127.0/24
IPv4 Remote network(s): 10.3.0.0/16Tunnel settings location1->cloud:
IPv4 Tunnel Network: 10.7.127.0/24
IPv4 Remote network(s): 10.7.112.0/24,192.168.3.0/24When ping from pfsense cloud 10.7.112.3 -> 10.3.254.1
With source adres lan package not received
With source adres openvpn cloud-loation1 tunnel package receivedTunnel settings cloud->office:
IPv4 Tunnel Network: 10.7.128.0/24
IPv4 Remote network(s): 192.168.3.0/24Tunnel settings office->cloud:
IPv4 Tunnel Network: 10.7.128.0/24
IPv4 Remote network(s): 10.7.112.0/24,10.3.0.0/16When ping from pfsense office 192.168.3.1 -> 10.3.201.1
with source adres lan package received
When ping from pfsense office 192.168.3.1 -> 10.3.254.1
with source adres lan package not received -
@Freek_Box
Did you add the NAT rule as suggested? You may have to reboot pfSense after. -
@viragomann Can you explain more about why the nat rule should fix this problem?
-
@Freek_Box
Cause the router won't have a route to the office Lan. So he directs response packets to its default gateway which is presumably the ISPs upstream gateway.The suggested NAT rule translates the source IP in requests to the router into the pfSense interface IP which is in its own subnet, so no route needed and he directs response packets back to pfSense.
-
So like this?
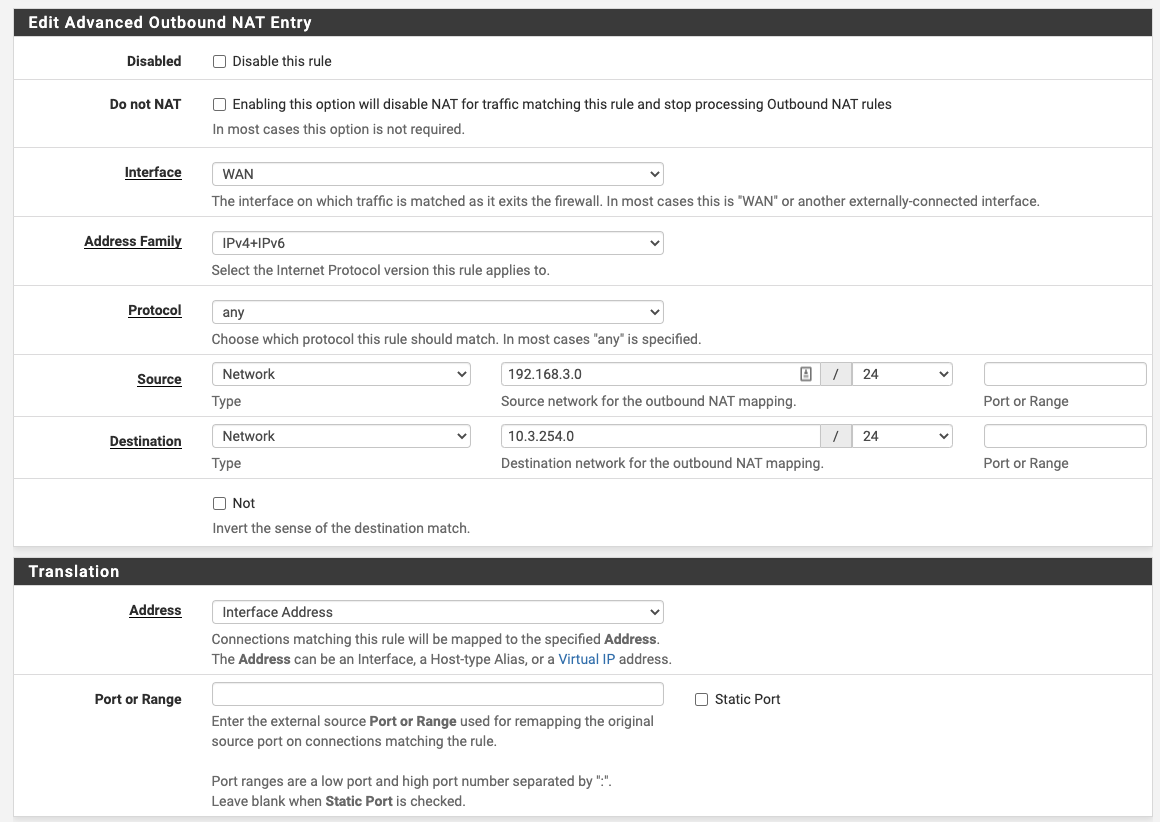
-
@Freek_Box
At interface you have to select that one which the router is connected to. Don't know, if this is WAN.
The other options will be okay. -
@viragomann Wouws this indeed fixed the problem!!
So the 4g router also has openvpn on it I could also do a tunnel from cloud to 4g router.
If you can choose what would you advice to do this option with the nat rule or a different vpn tunnel for the 4g router?
-
@freek_box
If your onlay goal is to access the router itself for maintenance I would go with the existing VPN and the NAT.
However, if you set up the router as OpenVPN client which is connecting to the cloud you can have a backup connection in case the main internet goes down. But you will need a route on the 4g router to the LAN behind pfSense.
Another option is to set up a second VPN on pfSense itself using the 4g as gateway. This way it may be easier to configure a failover for both directions.