Zombie Default deny rule IPv6
-
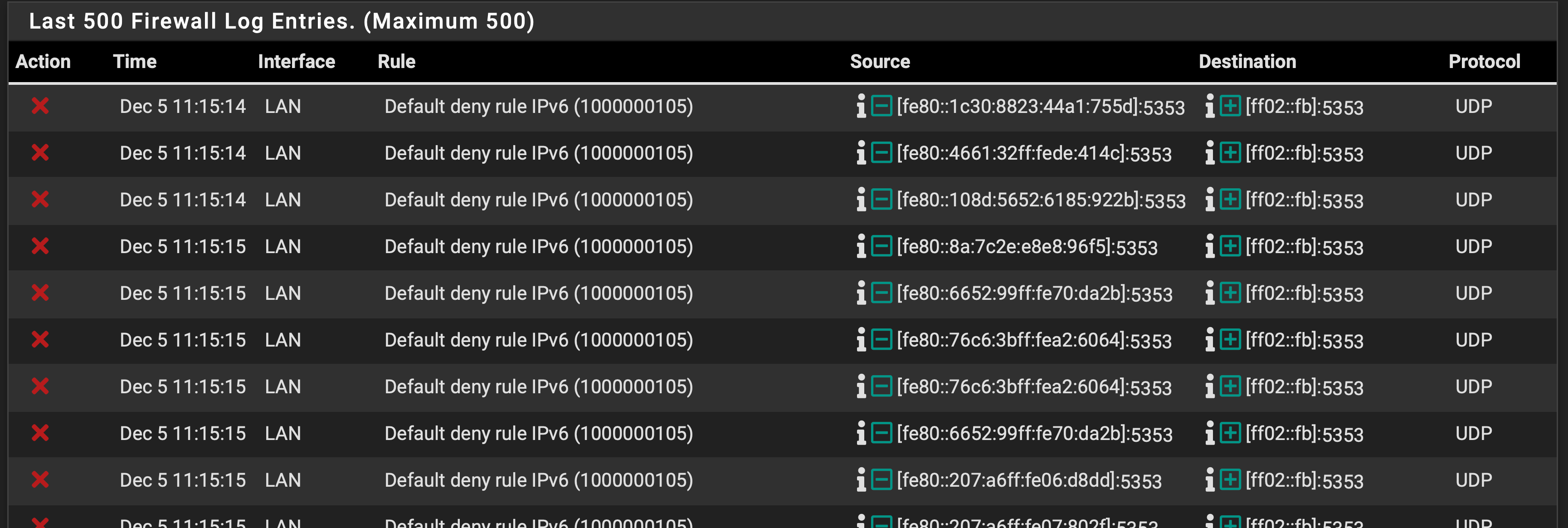
Can't kill it or stop it from stuffing the firewall log.
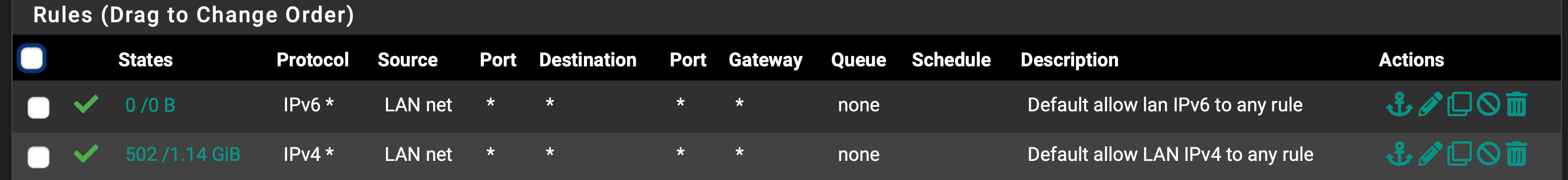
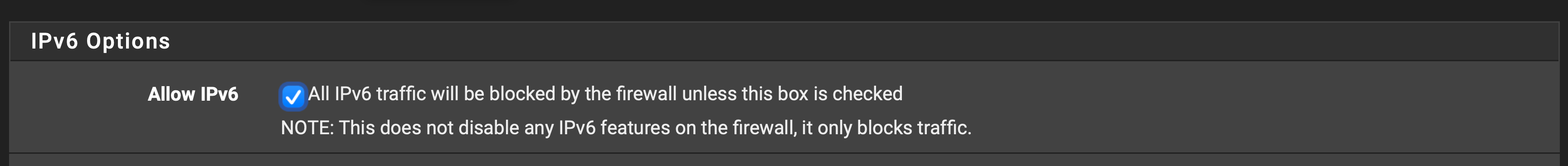
Have the all IPv6 button checked in System/Advanced/Networking. Have a rule to pass all IPv6 traffic in my LAN firewall. It's all mDNS traffic on port 5353, but can't make it stop. I do not have IPv6 on for wan, so this is all internal. Not sure how long this has been going on, just happened to check earlier this week. Updated to the latest 2.5 snapshot today and the issue persist.
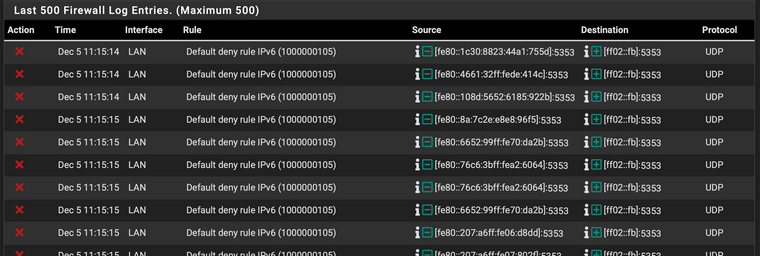
With some googlefu, found a few older things online where turning off then back on the all IPv6 button in System/Advanced/Networking seemed to work for some, but no such luck for me.
-
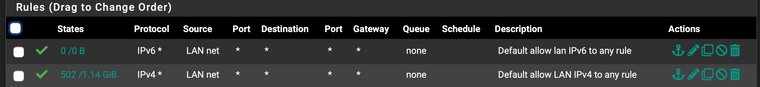
What are your specific rules which pass IPv6 on your LAN? Odds are they don't cover this. Either because you used something like "LAN Net" which doesn't include link-local, or because packets may have some other property which doesn't make them match (like IP options).
I suspect the former in this case. Read other reports such as https://redmine.pfsense.org/issues/9168 for details.
-
Try this one :
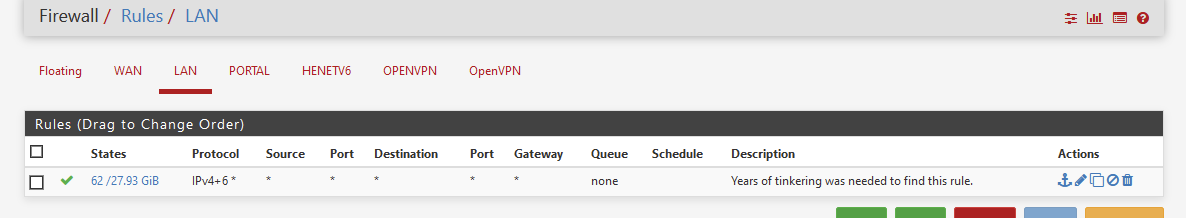
It works.
Normally, these :
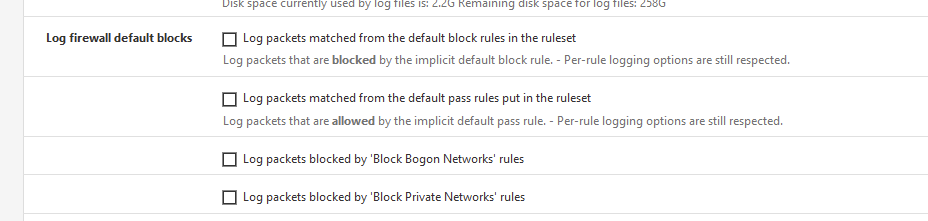
are unchecked, as you don't want to know who's knocking on the door.
Those who can and should enter, have the key (your rules).
Because you have some of them checked, you saw the issue : packets hit the default block rule. -
You don't need a source of
*as that's a bit dangerous.You could just add a rule to pass from
fe80::/10to*and fromLAN netto*.Or be more specific:
- Block IPv6
fe80::/10toff00::/8with "Allow IP options" checked, and without log checked, description "Ignore link local multicast traffic" - Block IPv6
fe80::/10tofe80::/10with "Allow IP options" checked, and without log checked, description "Ignore other link local traffic" - Pass
LAN Netto*
That way if something unusual comes along, like a link-local address erroneously trying to contact something outside multicast or link local, it would still be logged since you may want to track down the misbehaving client.
If there are services on the firewall you want to expose via link-local addresses, you can add explicit pass rules for them. Most/all things that required for basic IPv6 operation are passed automatically and not subject to the LAN rules.
- Block IPv6
-
Adopted :
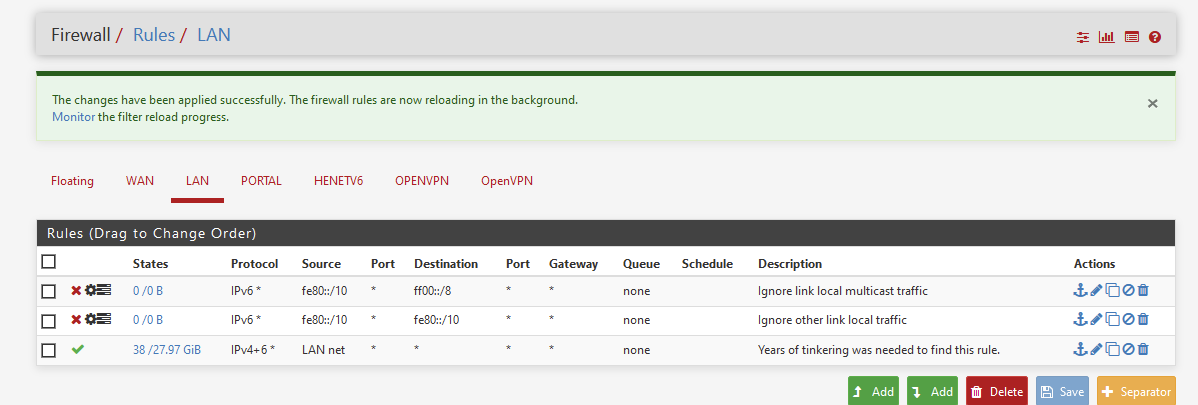
Made the first to to log for a while, just to see what they do - if something is done / rules apply.
-
Another note, if you do install something like Avahi on purpose that needs to receive IPv6 multicast on the firewall, then you would need to set that multicast rule to pass, or to create one that would at least pass to that same source/destination with whatever port(s) it needs on there (e.g.
5353) -
@jimp Yep, I'm using Avahi, how did you know ? ;)
But, mine is there so Captive portal user can 'find' our printers, so they can print something like a plain ticket or whatever.
Knowing that the captive portal is IPv4-only land, I don't need that extra rule.